Executive Summary
Unit 42 stopped monitoring this threat as well as updating this brief on March 11, 2025. Please refer to Ivanti's Security Advisory for the latest information.
On Jan. 8, 2025, Ivanti released a security advisory for two vulnerabilities (CVE-2025-0282 and CVE-2025-0283) in its Connect Secure, Policy Secure and ZTA gateway products. This threat brief provides attack details that we observed in a recent incident response engagement to provide actionable intelligence to the community. These details can be used to further detect current attacks noted in the wild using CVE-2025-0282.
These Ivanti products are all appliances that facilitate remote connections into a network. As such, they are outward-facing assets that attackers could target to infiltrate a network.
CVE-2025-0282 is a stack-based buffer overflow in Ivanti Connect Secure before version 22.7R2.5, Ivanti Policy Secure before version 22.7R1.2 and Ivanti Neurons for ZTA gateways before version 22.7R2.3 that allows a remote unauthenticated attacker to achieve remote code execution. This vulnerability has been assigned a critical CVSS score of 9.0.
CVE-2025-0283 is a stack-based buffer overflow in Ivanti Connect Secure before version 22.7R2.5, Ivanti Policy Secure before version 22.7R1.2 and Ivanti Neurons for ZTA gateways before version 22.7R2.3 that allows a local authenticated attacker to escalate their privileges. This vulnerability has been assigned a high CVSS score of 7.0.
On the same day of Ivanti’s advisory, Mandiant disclosed its findings of attacks in the wild using the CVE-2025-0282 remote code execution vulnerability.
On January 10, Watchtowr Labs also provided analysis of the exploited vulnerability. On January 12, Watchtowr provided a walkthrough and on January 16 they published a proof of concept (PoC).
Palo Alto Networks customers receive protections from and mitigations for CVE-2025-0282 and CVE-2025-0283 in the following products and services:
Cortex Xpanse has the ability to identify exposed Connect Secure, Policy Secure and ZTA gateway products on the public internet and escalate these findings to defenders.
Palo Alto Networks also recommends applying the appropriate updates to the affected Ivanti appliances as described in their security advisory.
The Unit 42 Incident Response team can also be engaged to help with a compromise or to provide a proactive assessment to lower your risk.
| Related Unit 42 Topics | CVE-2025-0282, CVE-2025-0283 |
Details of the CVE-2025-0282 Vulnerability
CVE-2025-0282 is a buffer overflow vulnerability that can be exploited by an unauthenticated attacker. Because the affected appliances are outward-facing and on the edge of the network, attackers could scan for and directly target them.
If the appliance is vulnerable, an attacker can exploit it by sending a specially crafted request. If the exploit is successful, the attacker can gain a foothold into the internal network behind the appliance. This would be an initial foothold for an attacker to laterally move into the network behind the affected Ivanti appliance.
Details of the CVE-2025-0283 Vulnerability
CVE-2025-0283 is a stack-based buffer overflow that allows a local authenticated attacker to escalate privileges. There are no reports of attackers using the CVE-2025-0283 privilege escalation vulnerability at this time.
Current Scope of the Attack Against CVE-2025-0282
There are limited reports of attackers using the CVE-2025-0282 remote code execution vulnerability to gain access into affected systems.
We have observed specific tools, tactics and procedures with this attack, many of which align with third-party reporting. We currently track this activity as cluster CL-UNK-0979. While overlaps exist between our observations and activity reported by Mandiant as UNC5337, we do not yet have enough evidence to confirm whether this activity is by the same threat actor group.
The attacks in the activity cluster CL-UNK-0979 consist of four phases:
- Initial access
- Credential harvesting and lateral movement
- Defense evasion
- Persistence
Initial Access
Our telemetry reveals a threat actor potentially exploited the CVE-2025-0282 zero-day, pre-authentication remote code execution vulnerability in a public-facing Ivanti Connect Secure (ICS) VPN appliance in late December 2024.
While we were unable to recover evidence showing the specific exploit, we did observe several instances of the error below in the appliance's debug.log file in the days leading up to the threat actor dropping malware on the Ivanti appliance:
vc0 0 ifttls tnctransport.cc:1198 - Invalid IFT packet received from unauthenticated client. IP : <REDACTED>
We observed both Tor and Nord VPN infrastructure generating the above log message. Third-party reporting suggests exploitation of CVE-2025-0282 involves a vulnerability in how IFT (also known as IF-T) connections are handled. The consistent IFT errors suggest that attackers made a number of attempts to exploit this vulnerability.
Credential Harvesting and Lateral Movement
Attackers leveraged a custom Perl script named ldap.pl to harvest credentials from the Ivanti appliance, which they likely used to move laterally into the victim environment. Attackers used Remote Desktop Protocol (RDP) to move laterally to additional systems and deployed a simple memory dumping tool named package.dll to potentially dump LSASS memory for credential harvesting.
Defense Evasion
Post-exploitation, attackers engaged in anti-forensic activities including deleting critical log files to cover up their actions. Specifically, a recovered debug log file only showed a specific period of time after the initial intrusion, suggesting they had removed other log entries.
Additionally, the Ivanti appliance's /var/cores directory was empty, and the following files had been deleted:
- /data/runtime/logs/log.events.vc0
- /data/var/dlogs/debuglog
Persistence
The threat actor attempted to leverage a tunneler named SPAWNMOLE, an SSH backdoor named SPAWNSNAIL and a log tampering utility named SPAWNSLOTH as described by Mandiant for persistence on the Ivanti appliance. Pivoting into the environment, the attackers leveraged a service named DcomSrv and a scheduled task named /mail for persistence for the backdoor.
Post-Exploitation Tooling
To better understand the CL-UNK-0979 activity cluster, we examined the following tools used in the attacks:
- The custom Perl script named ldap.pl
- The memory dumping tool named package.dll
- A backdoor established through DLL side loading using files named vixDiskLib.dll and deelevator64.dll
Custom Perl Script: Ldap.pl
The attackers used a custom Perl script named ldap.pl, which appears designed to collect and decrypt passwords from the Ivanti appliance. The redacted Perl script is shown below in Figure 1.
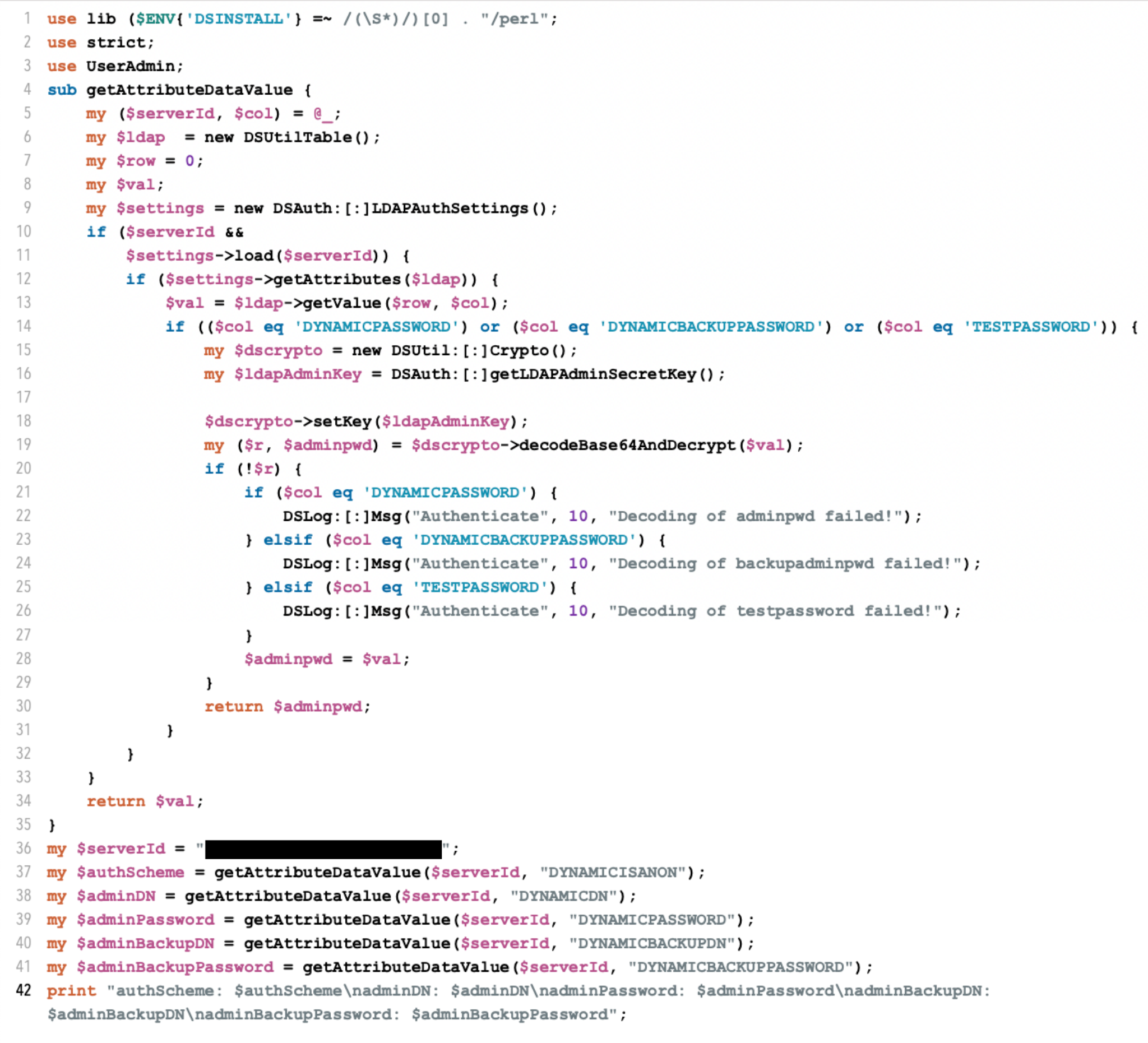
Simple Memory Dumping Tool: Package.dll
After moving laterally from the Ivanti appliance via RDP to a Windows host, attackers then used the legitimate build tool for Visual Studio named MSBuild.exe as a living off the land binary (LOLBIN) technique to create a likely memory dumping tool named package.dll. We observed a Windows Shortcut named msbuild.lnk likely used to launch MSBuild.exe to compile and run application code we found in a file on the system named mini.xml.
Soon after MSBuild.exe was executed, a file was created at C:\Users\Public\Music\package.dll on the targeted system. This file creates a full memory dump at C:\Users\Public\Downloads\VM.txt and XOR encodes it with a key 0x27. While we did not observe how this tool was used, attackers could have used it to access the LSASS process memory for credential harvesting.
Backdoor Through DLL Side Loading: VixDiskLib.dll and Deelevator64.dll
We observed the attackers leveraging a backdoor through DLL sideloading. The malicious DLL files were named deelevator64.dll and vixDiskLib.dll, and they were loaded by legitimate Windows executable files named DeElevate64.exe and vmdisk.exe respectively.
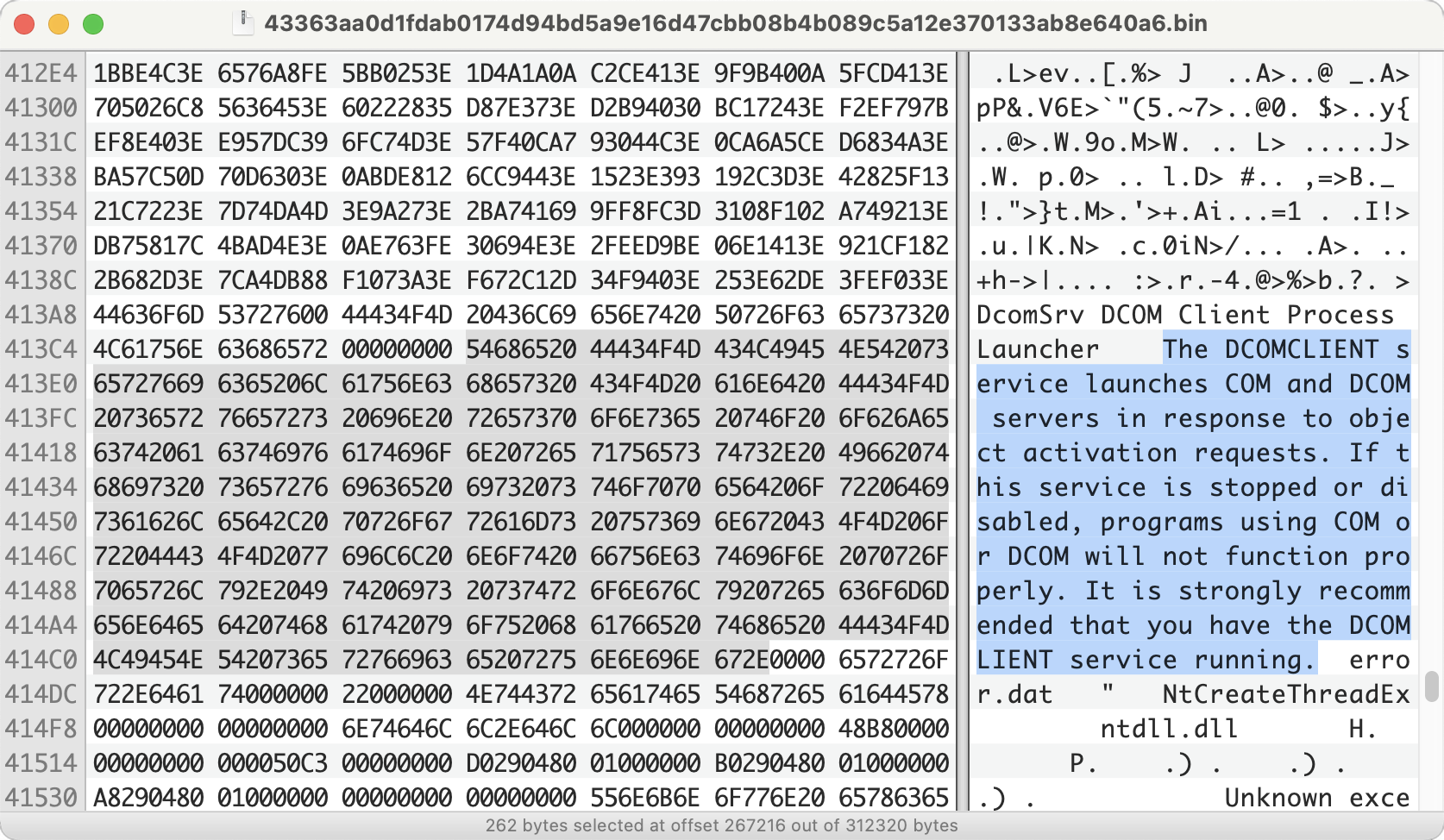
The malware file named vixDiskLib.dll creates a service named DcomSrv. A description of the service embedded in the code from the file is shown below in Figure 2. Note how the term DCOMCLIENT is misspelled the second time as DCOMLIENT. This is an indicator for this particular binary.
The DCOMCLIENT service launches COM and DCOM servers in response to object activation requests. If this service is stopped or disabled, programs using COM or DCOM will not function properly. It is strongly recommended that you have the DCOMLIENT service running.
Attackers set up a scheduled task named /mail for persistence to run DeElevate64.exe to sideload deelevator64.dll.
These malicious DLL files load other files located in the same directory:.
- vixDiskLib.dll loads a file named error.dat
- deelevator64.dll loads a file named temp.log
We were unable to recover error.dat or temp.log, inhibiting our ability to fully analyze this malware.
The error.dat or temp.log files will be mapped to memory and decrypted. Then the sample will spawn svchost.exe in a suspended state to attempt process hollowing to load the decrypted payload into memory. We observed the injected processes beaconing to C2 IP addresses at 168.100.8[.]144 and 193.149.180[.]128.
Interim Guidance
Ivanti has provided a security update in its security advisory to mitigate these RCE and privilege escalation vulnerabilities. Ivanti has also advised that activity targeting CVE-2025-0282 has been specifically observed on their Connect Secure appliances and not on Policy Secure or ZTA gateways to this point.
Ivanti was alerted to the exploitation activities via its Integrity Checker Tool (ICT). This allowed Ivanti to quickly develop a patch to mitigate the vulnerability.
Ivanti recommends applying its patch to mitigate these vulnerabilities as well as continually monitoring its ICT for suspicious activities.
Conclusion
Based on the topology of the affected Ivanti appliances and the possibility of an impending PoC for this vulnerability, we highly recommend following Ivanti’s patch and guidance provided in its security advisory. We will continue to monitor for further attacks using this vulnerability and will provide updated indicators of compromise as necessary.
Palo Alto Networks customers are better protected by our products, as listed below. We will update this threat brief as more relevant information becomes available.
Palo Alto Networks Product Protections for Ivanti CVE-2025-0282
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
Next-Generation Firewalls and Prisma Access With Advanced Threat Prevention
Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block attacks via the following Threat Prevention signature: 95948.
Cloud-Delivered Security Services for the Next-Generation Firewall
- The Advanced WildFire machine-learning models and analysis techniques have been reviewed and updated in light of the IoCs shared in this research.
- Advanced URL Filtering and Advanced DNS Security identify known identify known IP addresses associated with this activity as malicious.
Cortex Xpanse
Cortex Xpanse has the ability to identify exposed Connect Secure, Policy Secure and ZTA gateway products on the public internet and escalate these findings to defenders. Customers can enable alerting on this risk by ensuring that the “Insecure Pulse Secure Pulse Connect Secure VPN” Attack Surface Rule is enabled. Identified findings can either be viewed in the Threat Response Center or in the incident view of Expander. These findings are also available for Cortex XSIAM customers who have purchased the ASM module.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
We have shared our findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
| Indicator | Data | Note |
| IPV4 | 185.219.141[.]95 | Nord VPN node observed in debug log file |
| IPV4 | 185.195.71[.]244 | Tor exit node observed in debug log file |
| IPV4 | 193.149.180[.]128 | C2 address |
| IPV4 | 168.100.8[.]144 | C2 address |
| SHA256 | 7144B8C77D261985205AE2621EB6242F43D6244E18B8D01D05048337346B6EFD | ldap.pl file |
| SHA256 | AAE291AC5767CFE93676DACB67BA50C98D8FD520F5821FB050FD63E38B000B18 | Potential SPAWNMOLE malware |
| SHA256 | 366635c00b8e6f749a4d948574a0f1e7b4c842ca443176de27af45debbc14f71 | Potential SPAWNSNAIL malware |
| SHA256 | 3526af9189533470bc0e90d54bafb0db7bda784be82a372ce112e361f7c7b104 | Potential SPAWNSLOTH malware |
| SHA256 | 43363AA0D1FDAB0174D94BD5A9E16D47CBB08B4B089C5A12E370133AB8E640A6 | vixDisklib.dll |
| SHA256 | 1dc0a3a5904ec35103538a018ef069fbe95b0a3c26cb0ff9ba0d1c268d1aaf98 | package.dll |
| SHA256 | f9ca95119b32a18491e3cc28c7020ee00f6e7a45ae089c876d87252e754e5a2e | error.dat |
| SHA256 | 723711ccbb3eaf1daea3d5b00aa6aaee48a359be395d9500d8a56609ec5238e9 | msbuild.lnk |
| SHA256 | 75a3d53c1d63ecb338d4b2d6f5b3d980b0caceb77808ed81ab73b49138cc0a26 | mini.xml |
| SHA256 | a6b24fcef2e018c9ef634aa21e26a74ff94ea508a8b132fad38d48f5ab10fcd3 | deelevator64.dll |
| HOSTNAME | DESKTOP-1JIMIV3 | Remote computer name seen accessing compromised accounts |
Updated Jan. 17, 2025, at 6:08 a.m. PT to expand product protections coverage information.












 Get updates from Unit 42
Get updates from Unit 42