Executive Summary
On March 28, 2024, Red Hat Linux announced CVE-2024-3094 with a critical CVSS score of 10. This vulnerability is a result of a supply chain compromise impacting the versions 5.6.0 and 5.6.1 of XZ Utils. XZ Utils is data compression software included in major Linux distributions. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has advised people to downgrade to an uncompromised XZ Utils version (earlier than 5.6.0).
The newly disclosed vulnerability has been assigned the following CVE:
| CVE Number | Description | CVSS Severity |
| CVE-2024-3094 | Malicious code was discovered in the upstream tarballs of xz, starting with version 5.6.0. Through a series of complex obfuscations, the liblzma build process extracts a prebuilt object file from a disguised test file existing in the source code, which is then used to modify specific functions in the liblzma code. This results in a modified liblzma library that can be used by any software linked against this library, intercepting and modifying the data interaction with this library. | 10.0 Critical |
Palo Alto Networks customers are better protected from and can implement mitigations for CVE-2024-3094 in the following ways:
- The Next-Generation Firewall with cloud-delivered security services including Advanced WildFire detects the compromised versions described in this report as malicious, as well as features known to be associated with the backdoors.
- Cortex XDR and XSIAM help protect against post-exploitation activities using the multi-layer protection approach. Cortex customers using the Host Insights module can detect if the vulnerability exists on protected devices.
- Prisma Cloud has out-of-the-box detection capabilities in place that will help prevent the launch of images with CVE-2024-3094.
- The Unit 42 Managed Threat Hunting team is monitoring attempted malicious activities against our customers. The XQL queries shared in that section below can also be used by Cortex XDR customers to search for affected versions of XZ Utils.
- The Unit 42 Incident Response team can also be engaged to help with a compromise or to provide a proactive assessment to lower your risk.
Details of CVE-2024-3094
On March 28, 2024, Red Hat Linux announced CVE-2024-3094 with a critical CVSS score of 10. This vulnerability is a result of a supply chain compromise impacting the latest versions of XZ tools and libraries. XZ Utils is data compression software included in major Linux distributions.
Versions 5.6.0 and 5.6.1 of the libraries contain malicious code that modifies functions during the liblzma build process. Liblzma is a data compression library.
This malicious code results in a compromised liblzma library, which may modify or intercept data from other applications that leverage the library. Under certain conditions this code may allow unauthorized access to affected systems.
A security researcher, Andres Freund, found the malicious code when he saw failing ssh logins using high CPU loads. When researching the cause of the high CPU utilization he then also noticed slower logins which led to further exploration and discovery of the vulnerability.
Affected Versions and Mitigation Actions
All major Linux distros recommend either reverting back to versions built prior to the inclusion of XZ Utils 5.6.0 and 5.6.1 or migrating to updated releases.
Please check the notification page for your specific distribution for additional updates and guidance.
| Distro | Affected Version |
| Red Hat | Fedora Linux 40 and Fedora Rawhide |
| Debian | No Debian stable versions are known to be affected.
Compromised packages were part of the Debian testing, unstable and experimental distributions, with versions ranging from 5.5.1alpha-0.1 (uploaded on 2024-02-01), up to and including 5.6.1-1. |
| Kali | The impact of this vulnerability affected Kali between March 26-29. If you updated your Kali installation on or after March 26, it is crucial to apply the latest updates today to address this issue. However, if you did not update your Kali installation before March 26, you are not affected by this backdoor vulnerability. |
| OpenSUSE | OpenSUSE Tumbleweed and OpenSUSE Micro OS between March 7th and March 28th 2024. |
| Alpine | 5.6 versions prior to 5.6.1-r2 |
| Arch |
|
Additionally, HomeBrew package manager is forcing downgrades to 5.4.6. They do not believe Homebrew’s builds were compromised but are taking this action as a precaution.
Amazon has stated that Amazon Linux customers are not affected by this issue, and no action is required.
Conclusion
Unit 42 will continue to monitor the situation and will update this post as more information becomes available.
Unit 42 Managed Threat Hunting Queries
The Unit 42 Managed Threat Hunting team continues to track any attempted malicious activities across relevant Linux distributions used by our customers, using Cortex XDR and the XQL queries below. Cortex XDR customers can also use these XQL queries to search for affected versions of XZ Utils.
|
1 2 3 4 |
//This query searches for XZ Utils versions 5.6.0 or 5.6.1, requires the Host Insights module. config case_sensitive = false | preset = host_inventory_applications | filter (application_name contains "XZ-UTILS" AND version = "5.6.0") OR (application_name contains "XZ-UTILS" AND version = "5.6.1") |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
//This query aims to identify hosts running XZ Utils versions 5.6.0 or 5.6.1 that have received inbound SSH connections from external ip addresses, requires the Host Insights module. config case_sensitive = false | preset = host_inventory_applications | filter (application_name contains "xz-util" AND version = "5.6.0") OR (application_name contains "xz-util" AND version = "5.6.1") | fields endpoint_name, application_name, version | join type = left ( dataset = xdr_data | filter agent_os_type = ENUM.AGENT_OS_LINUX | filter event_type = ENUM.NETWORK | filter actor_process_image_name in ("ssh", "sshd") | filter action_remote_ip != null | alter Ip_Address = action_remote_ip | alter IP_Address_Private = if (incidr(Ip_Address, "10.0.0.0/8") = true, "TRUE", if (incidr(Ip_Address, "127.0.0.0/8") = true, "TRUE", if (incidr(Ip_Address, "169.254.0.0/16") = true, "TRUE", if (incidr(Ip_Address, "172.16.0.0/12") = true, "TRUE", if (incidr(Ip_Address, "192.168.0.0/16") = true, "TRUE", if (incidr6(Ip_Address, "fe80::/64") = true, "TRUE", if (incidr6(Ip_Address, "::/128") = true, "TRUE", if (incidr6(Ip_Address, "::1/128") = true, "TRUE", if (incidr6(Ip_Address, "fc00::/7") = true, "TRUE", "FALSE"))))))))) | filter (IP_Address_Private != "TRUE") | fields agent_hostname, actor_process_image_name, Ip_Address ) as ssh_network ssh_network.agent_hostname = endpoint_name |dedup endpoint_name |
Palo Alto Networks Product Protections for the XZ Util Vulnerability
Based on the information presently known, Palo Alto Networks products and cloud services do not contain affected XZ software packages and are not impacted by these issues. Read our informational bulletin for more details.
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Advanced WildFire
The Next-Generation Firewall with cloud-delivered security services including Advanced WildFire detects the compromised versions described in this report as malicious, as well as features known to be associated with the backdoors.
Cortex XDR and XSIAM
Cortex XDR and XSIAM agents help protect against post-exploitation activities using the multi-layer protection approach. Cortex customers using the Host Insights module can detect if the vulnerability exists on protected devices.
XDR customers can find and upgrade software vulnerable to this issue centrally from the XDR console. Our InfoSec SOC team used the following XQL query to find vulnerable versions of XZ on our endpoints:
|
1 2 3 4 5 |
dataset = xdr_data |alter CMD = arrayindex(regextract(action_file_path, "(.*\/xz\/5.6[.1|.0]+)"),0) |filter CMD != null |fields action_file_path,actor_effective_username, CMD, agent_hostname, action_username, causality_actor_effective_username |dedup agent_hostname,CMD,actor_effective_username |
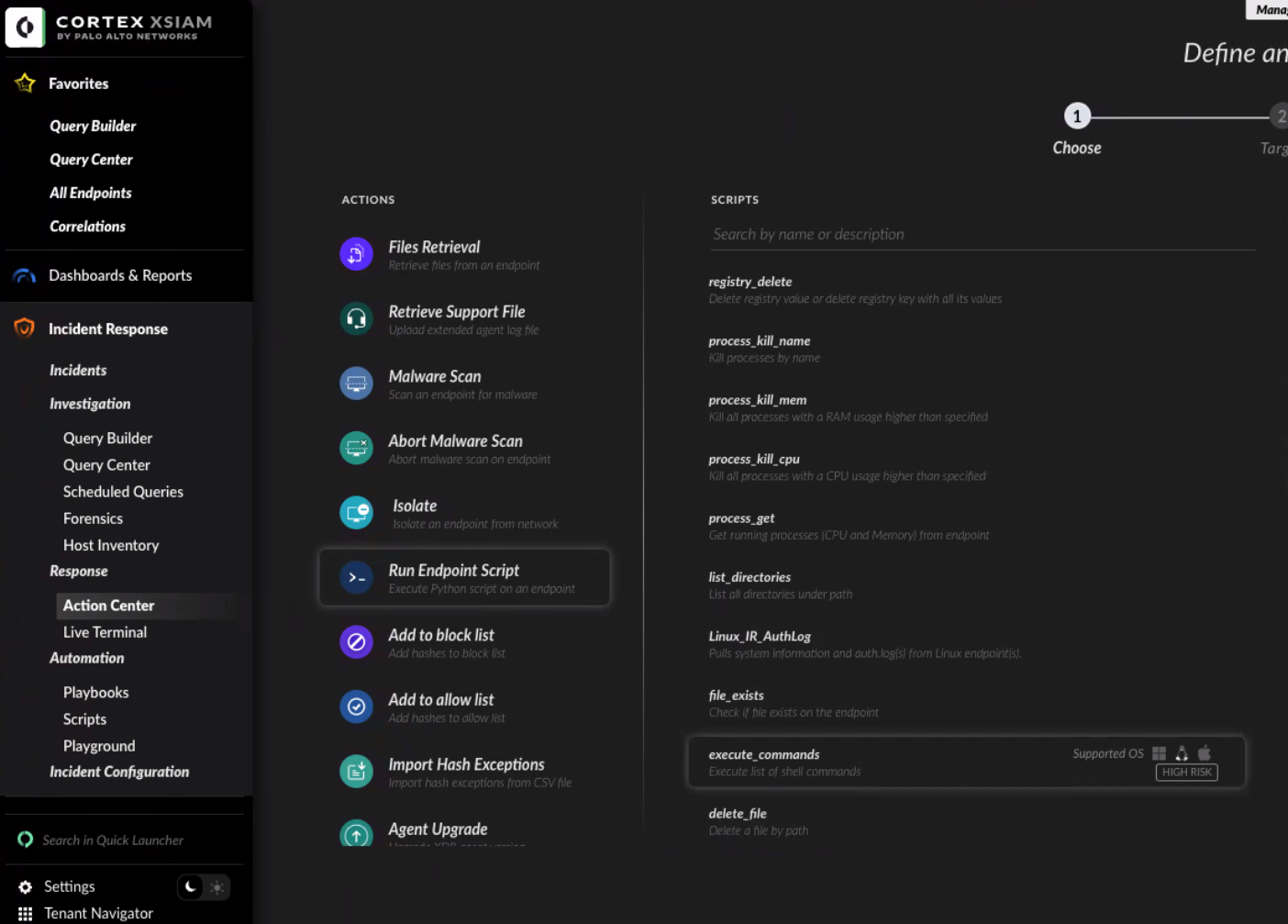
Once you review the results, if you identify installations of software that need to be updated, you can execute an endpoint script on a particular software package. For example, to upgrade a vulnerable HomeBrew installation on a list of Macs to the latest version (with the downgraded, safe, version of XZ) you can execute the following commands via XDR on your endpoints.
The menu options to follow are: Incident Response → Action Center → Run Endpoint Script → Execute Commands.
|
1 |
/usr/bin/sudo -u $( echo "show State:/Users/ConsoleUser" | /usr/sbin/scutil | /usr/bin/awk '/Name :/ && ! /loginwindow/ { print $3 }' ) /usr/local/bin/brew upgrade xz |
Prisma Cloud
Prisma Cloud has out-of-the-box detection capabilities in place that will help prevent the launch of images with CVE-2024-3094. Prisma Cloud’s agentless approach provides you with a comprehensive lifecycle overview from Code Repository to Cloud and simplified filter options that enable you to identify vulnerable hosts, high privilege access and potential exposure to the internet. Additionally, its defender component or pipeline integration offer real-time insights and protection capabilities, enabling you to prevent the launch of images with the CVE or detect and prevent anomalous behavior. Our researchers validated this capability relative to this CVE by committing a Dockerfile and then triggering a CI/CD pipeline to build and deploy the Docker image.
Additional Resources
- Find and Fix XZ Utils in Just a Few Clicks – Prisma Cloud Blog, Palo Alto Networks
- Reported Supply Chain Compromise Affecting XZ Utils Data Compression Library, CVE-2024-3094 – Cybersecurity and Infrastructure Security Agency (CISA)
- NVD - CVE-2024-3094 – NIST
- Brew install xz installs the outdated version 5.4.6 instead of 5.6.1 – Homebrew, Discussion #5243 on GitHub
- Urgent security alert for Fedora Linux 40 and Fedora Rawhide users — Red Hat
- Debian Security Advisory DSA-5649: 1xz-utils security update – Debian
- Kali Linux: "As of the information we have …" – infosec.exchange on Mastodon
- OpenSUSE - Open Build Service Request 1163302 – Open Build Service
- CVE-2024-3094 – Alpine Security Tracker
- News: The xz package has been backdoored – Arch Linux
Updated March 31, 2024, at 9:30 a.m. PT to add an additional XQL query and additional details about Cortex XDR protections.
Updated March 31, 2024, at 7:15 p.m. PT to add a link to additional info about Host Insights.
Updated April 1, 2024, at 8:15 a.m. PT to add info on Advanced WildFire protections.
Updated April 2, 2024, at 10 a.m. PT to add a link to the Palo Alto Networks Product Security Assurance team's assessment that PANW products and cloud services are not impacted by these issues.
Updated April 3, 2024, at 1:45 p.m. PT to expand Cortex XDR product protection information on endpoints.
Updated April 11, 2024, at 12:45 p.m. PT to add to Additional Resources section.












 Get updates from Unit 42
Get updates from Unit 42