This post is also available in: 日本語 (Japanese)
Put yourself in the shoes of an attacker: Your objective is to infiltrate an organization, deploy ransomware and get paid. It is your job to launch the most effective, lowest cost attack possible, which also delivers the highest return. When adversaries balance the equation of effort versus potential reward, they are increasingly turning toward automated tools, like exploit kits (EKs), to help them achieve their malicious goals at massive scale. In short, EKs allow a malicious actor to silently exploit vulnerabilities in a browser-based application, deliver a malware payload, and operationalize the attack using rental-based EK infrastructure.
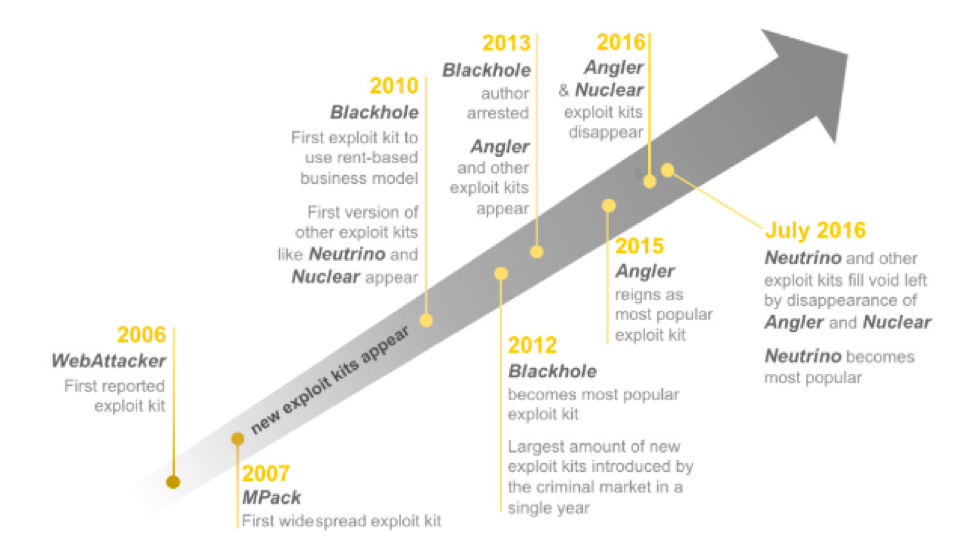
Before we look forward, it is important to understand the history of exploit kits and how they’ve become one of the most prevalent and effective methods of breaching an organization today. The popularity of EKs dates back to 2006, when the first documented case appeared; but it really took off in 2010 with the introduction of the Blackhole EK and its associated software-as-a-service (SaaS) based business model. Now, instead of setting up malicious infrastructure, compromising websites, identifying vulnerability exploits, and delivering malware, malicious actors could outsource nearly the entire attack flow to an expert. This is cyberattacking for the masses, with a modern and simple-to-use interface to match.
Over time, network defenders identify and take down prevalent exploit kits, as we saw with the disappearance of Blackhole after the arrest of its author; but there is always another one ready to take over the mantle and reap the profits. In recent years, we have seen an explosion in the scale of EK usage against organizations, especially as they have been increasingly used to deliver ransomware payloads. In fact, according to research by the Palo Alto Networks Unit 42 threat intelligence team, “Exploit kits are now, on average, about twice as expensive as they were two years ago.” We expect this trend to continue, with malicious actors continuing to leverage the automation, scale and silent malware delivery offered by exploit kits.
As organizations build their prevention infrastructure, they should consider how their security controls can identify and prevent this significant threat across the network, cloud and endpoint. Learn more about the past, present and future of exploit kits, and how to prevent them:
- Download Unit 42’s report: Exploit Kits: Getting in by Any Means Necessary
- Register for the upcoming “Exploit Kits: Getting in by Any Means Necessary” webinar on December 7 at 10 a.m. PT.











 Get updates from Unit 42
Get updates from Unit 42