This post is the first in a series by Unit 42 covering the cybercrime underground. Cybercrime persists as an epidemic that continues to worsen every year, with associated impacts and losses steadily growing. In this series, we'll explore actors, motivations, and the current threat landscape.

Some of what contributes to the growth of the cybercrime underground is the convenience, speed, and anonymity the Internet provides to enable online crimes. Advances in the sophistication of cyberattacks over the past decade closely correlate with two major evolutions:
- Lowered Cost of Entry: The ease and availability of tools and training to conduct such attacks, allowing individuals with lower skillsets to successfully thrive in the cybercrime industry.
- Increased Business Acumen: The refinement of full attack lifecycle processes and support structures that rival some of the most innovative legitimate business models, enabling more efficient and effective operations coupled with robust commodity markets.
With the ever-changing cybercrime threat landscape, it is important to understand its current state, observe trends, and anticipate likely paths of evolution. Before we go any further, let’s establish some definitions related to the cybercrime underground.
Definitions
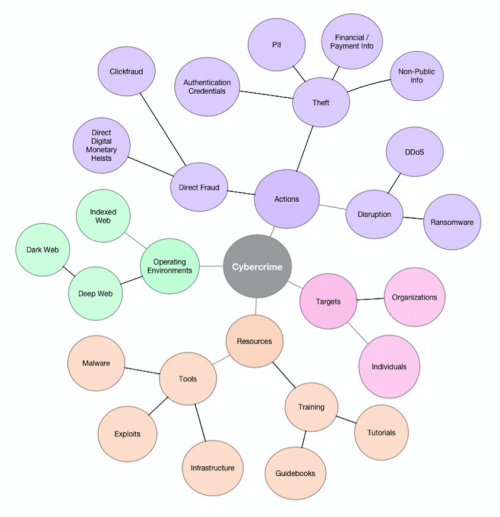
Cybercrime: Any crime that involves the use of computers to victimize an individual or organization for financial gain.
Indexed Web: All Internet search engine accessible and indexed sites. This is the web that most of the world knows and uses every day, and includes commercial / retail, social media, news, consumer service, and other publicly known sites.
Deep Web: Sites that make indexing by Internet search engines problematic, due to access control, dynamic content, or other prerequisite mechanisms (e.g., encryption or specialized software). In general, these sites are not accessible to standard web search engine crawlers that perform indexing. This class of sites is also sometimes referred to as the Invisible Web, Hidden Web, or Deepnet.
Dark Web: A subset of Deep Web sites that requires special software (e.g., TOR) to reach. Related infrastructure hosts criminal content such as stolen information and access to premium malware and exploits, and supports other categories of activity, such as illegal pornography, drug trade, prostitution, human trafficking, and terrorist operations. A number of these sites are transient, only up for a short time or constantly changing addresses in an attempt to minimize the risk of exposure to government agencies, law enforcement and security researchers.
Cybercrime underground: Online forums where information, tools (malware, exploits), and services are bought and sold in support of cybercrime objectives. Composite sites exist on the Indexed Web, Deep Web, and Dark Web in varying contexts.
Figure 1 High level chart connecting the different attributes of cybercrime
Impacts
Cybercrime has broad impacts to both organizations and individuals. The losses from cybercrime can range from theft of intellectual property to costs incurred due to a result of a breach. A high level overview of the impacts can be broken down into direct and indirect losses:
Direct Losses
- Loss of control over owned or entrusted:
- PII data
- Financial information
- Electronic Health Records (EHRs)
- Intellectual property
- Trade secrets
- Direct financial fraud
- Service disruptions or restriction of access to data (e.g., ransomware).
Indirect Losses
- Costs supporting recovery from a breach, such as incident response, investigation services, and remediation
- Reputational damage
- Legal and regulatory penalties related to the loss of records (e.g., PII, health, financial, etc.)
- Near term business revenue loss
- Longer term financial and economic consequences
Products, Services and Actor Roles
The cybercrime underground maintains its own economy of commoditized products and services. Related financial transactions have boomed with the broad adoption and accessibility of anonymous cryptocurrencies such as Bitcoin, which is commonly used by malicious actors amongst themselves as well as for accepting payments from victims (e.g., ransomware).
Products can be broken down into two main categories: information and resources. Sellers of these products benefit from the quick payouts of discrete (and sometimes one-time) transactions. Buyers benefit from what is often a professional level product that can be applied immediately to malicious actor operations “out of the box.” Information products include commodities such as:
- Stolen personally identifiable information (PII): Including everything from mass email lists used by spammers to full identity theft packages to commit financial fraud
- Exfiltrated organizational information: Including intellectual capital / property, non-public internal data, and internal operational details
- Harvested authentication credentials: Stolen username and password combinations continue to present a significant risk these days, especially when those credentials are re-used across multiple sites
- Pilfered financial / payment data: Unauthorized withdrawals from accounts or charges against credit lines continue to plague account holders
Resource products include elements such as:
- Access to feature-rich malware: Malware across varying capabilities (e.g., information stealers, remote administration tools – RATs, ransomware, purpose built utilities) that demonstrate consistent results and avoid source code leakage can generate significant revenue for associated authors and distributors
- Purchase of system or software exploits: While many white hats elect to support bug bounty initiatives by vendors, there remains a lucrative underground market for reliable, un-patched exploits
- Transfer of control for previously compromised machines: This usually applies to always-on servers that can then be used as attack platforms or sold for the information they store, although the service model for this element is more popular these days
- Malicious actor training: Guidebooks or tutorials on effective tool usage or specific Tactics, Techniques, and Procedures (TTPs)
Services can be thought of as "lease" versions of the resource-based – and even some of the information-based – products described above, where access to a product is promised at a set rate for an agreed upon period of time. Providing services appeals to many actors due to the recurrent cost model and opportunity to collect higher profits over a longer period of service. Malicious actors using these services benefit from assurances on availability and performance (e.g., timely feature, exploitation, and evasion updates). Such services include the following:
- Distributed Denial of Service (DDoS): Botnet powered attacks that affect the availability of targeted servers and capabilities
- Exploit Kits (EKs): Typically, monthly rate for access to the exploit toolkit allowing for customized end payloads
- Infrastructure rental: Hosting services for attack platforms; malware update, configuration, and command and control (C2); and other attack lifecycle functions. Of special note: BulletProof Hosting Services (BPHSs) providers play a critical role in the cybercrime world as they allow cyber criminals to thrive and operate their malicious services without the risk of easily being taken down by law enforcement. Some of the key reasons that BPHS providers have been successful in their operations include: the appearance of legitimate businesses, strategic geographic distribution of servers in countries with accommodating cyber laws, high redundancy to minimize the risk of operational disruption, and professional level support services
- Money laundering: Transfer (“money muling”) of illegally obtained funds through accounts and mechanisms in money haven countries remains a key service
As a high-level, malicious actor motivation, cybercrime is simply an extension of traditional criminal activity, focused on the theft of personal and account information and/or establishment of leverage over a target to achieve illicit monetary gain. The cybercrime ecosystem relies on a number of key roles that are also shared across other top-level motivations. A description of these roles can be found in Part 2 of a prior Unit 42 blog series: Adversaries and Their Motivations.
Coming Up…
Subsequent posts in this blog series will focus on different aspects of the cybercrime underground, including associated tools, services, techniques, and actors.












 Get updates from Unit 42
Get updates from Unit 42