Summary

Unit 42 recently discovered a new Android malware family we named “HenBox” masquerading as a variety of legitimate Android apps. We chose the name “HenBox” based on metadata found in most of the malicious apps such as package names and signer detail. HenBox masquerades as apps such as VPN and Android system apps and often installs legitimate versions of these apps along with HenBox to trick users into thinking they downloaded the legitimate app. While some of the legitimate apps HenBox use as decoys can be found on Google Play, HenBox apps themselves have only been found on third-party (non-Google Play) app stores.
HenBox appears to primarily target the Uyghurs – a minority Turkic ethnic group that is primarily Muslim and lives mainly in the Xinjiang Uyghur Autonomous Region in North West China. It also targets devices made by Chinese manufacturer Xiaomi and those running MIUI, an operating system based on Google Android made by Xiaomi. Smartphones are the dominant form of internet access in the region and Xinjiang was recently above the national average of internet users in China. The result is a large online population who have been the subject of numerous cyber-attacks in the past.
Once installed, HenBox steals information from the devices from a myriad of sources, including many mainstream chat, communication, and social media apps. The stolen information includes personal and device information. Of note, in addition to tracking the compromised device’s location, HenBox also harvests all outgoing phone numbers with an “86” prefix, which is the country code for the People’s Republic of China (PRC). It can also access the phone’s cameras and microphone.
HenBox has ties to infrastructure used in targeted attacks with a focus on politics in South East Asia. These attackers have used additional malware families in previous activity dating to at least 2015 that include PlugX, Zupdax, 9002, and Poison Ivy. This also aligns with HenBox’s timeline, as in total we have identified almost 200 HenBox samples, with the oldest dating to 2015. Most of the samples we found date from the last half of 2017, fewer samples date from 2016, and a handful date back to 2015. In 2018, we have already observed a small but consistent number of samples. We believe this indicates a fairly sustained campaign that has gained momentum over recent months.
HenBox Enters the Uyghur App Store
In May 2016, a HenBox app was downloaded from uyghurapps[.]net. Specifically, the app was an Android Package (APK) file that will be discussed in more detail shortly. The domain name, language of the site and app content hosted suggest this site is a third-party app store for whom the intended users are the Uyghurs. Such app stores are so-called because they are not officially supported by Android, nor are they provided by Google, unlike the Play Store. Third-party app stores are ubiquitous in China for a number of reasons including: evermore powerful Chinese Original Equipment Manufacturers (OEM), a lack of an official Chinese Google Play app store, and a growing smartphone market.
The HenBox app downloaded in May 2016 was masquerading as the DroidVPN app. At the time of writing, the content served at the given URL on uyghurapps[.]net, is now a legitimate version of the DroidVPN app, and looks as shown in Figure 1 below.
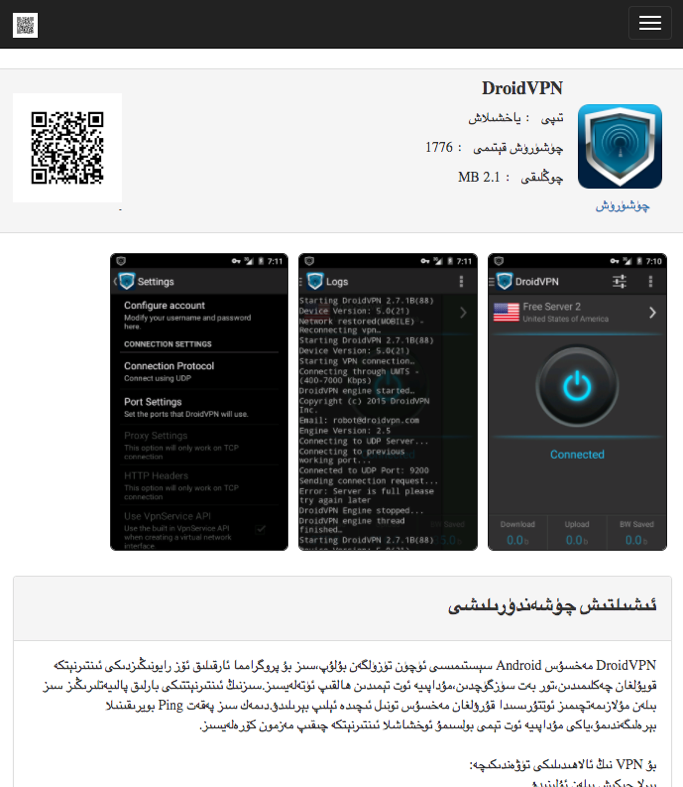
Figure 1 Uyghurapps[.]net app store showing the current DroidVPN app
Virtual Private Network (VPN) tools allow connections to remote private networks, increasing the security and privacy of the user’s communications. According to the DroidVPN app description, it “helps bypass regional internet restrictions, web filtering and firewalls by tunneling traffic over ICMP.” Some features may require devices to be rooted to function and according to some 3rd party app stores, unconditional rooting is required, which has additional security implications for the device.
We have not been able to ascertain how the DroidVPN app on the uyghurapps[.]net app store was replaced with the malicious HenBox app; however, some indicators point to the server running an outdated version of Apache Web Server on a Windows 32-Bit operating system. In light of this, we believe an attack against unpatched vulnerabilities is a reasonable conjecture for how the server was compromised.
The HenBox app downloaded in May 2016, as described in Table 1 below, masquerades as a legitimate version of the DroidVPN app by using the same app name “DroidVPN” and the same iconography used when displaying the app in Android’s launcher view, as highlighted in Figure 2 below Table 1.
| APK SHA256 | Size (bytes) | First Seen | App Package name |
App name |
| 0589bed1e3b3d6234c30061be3be1cc6685d786ab3a892a8d4dae8e2d7ed92f7 | 2,740,860 | May 2016 | com.android.henbox | DroidVPN |
Table 1 Details of the HenBox DroidVPN app on the uyghurapps[.]net app store
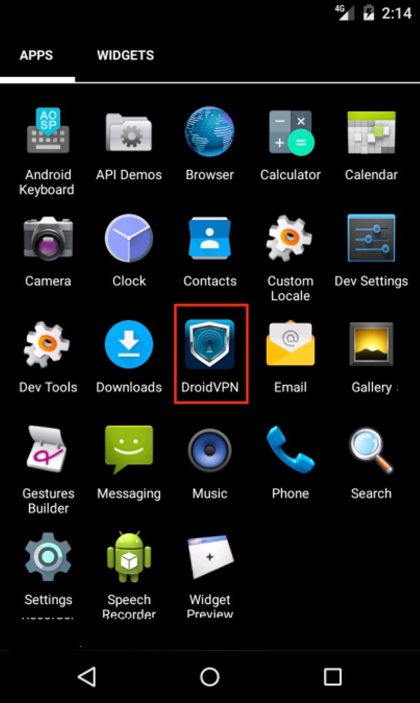
Figure 2 HenBox app installed, purporting to be DroidVPN
Depending on the language setting on the device, and for this particular variant of HenBox, the installed HenBox app may have the name “Backup” but uses the same DroidVPN logo. Other variants use other names and logos, as described later.
Given the DroidVPN look and feel being used by this variant of HenBox, it’s highly likely the uyghurapps[.]net page for DroidVPN remained identical when serving either HenBox or DroidVPN apps, just that the legitimate APK file had been replaced with HenBox for an unknown period of time.
In addition to the look and feel of DroidVPN, this HenBox variant also contained a legitimate DroidVPN app within its APK package as an asset, which could be compared to a resource item within a Windows Portable Executable (PE) file. Once the HenBox app is installed and launched, it launches an install process for the embedded app as a decoy to other malicious behaviors occurring in the background, and to satisfy the victim with the app they were requesting, assuming they requested to download a particular app, such as DroidVPN.
The version of the legitimate DroidVPN embedded inside this HenBox variant is the same version of DroidVPN available for download from uyghurapps[.]net, at the time of writing. It’s worth noting, newer versions of the DroidVPN app are available on Google Play, as well as in some other third-party app stores, which could indicate uyghurapps[.]net is not awfully well maintained or updated to the latest apps available.
At the time of writing, to our knowledge no other third-party app stores, nor the official Google Play store, were or are hosting this malicious HenBox variant masquerading as DroidVPN.
The Right App at the Right Time
The malicious HenBox and embedded DroidVPN app combination is one instance of the type of legitimate apps the attackers choose to mimic to compromise their victims. These threat actors frequently offer malicious apps purporting to be legitimate apps that are broadly used or important to a targeted population. It’s worth noting however, about one-third of the HenBox apps contained embedded APK objects that did not refer to legitimate apps. Some were only 3 bytes long, containing strings such as “ddd” and “333”, or were otherwise corrupted.
Beyond the previously mentioned DroidVPN example, other viable embedded apps we found include apps currently available on Google Play, as well as many third-party app stores. Table 2 below lists some of these apps with their respective metadata.
| # | Parent APK SHA256 | First Seen | Package names (parent APK) [embedded APK] |
APK App names (parent APK) [embedded APK] |
| 1 | fa5a76e86abb26e48a f0b312f056d24000bc 969835c40b3f98e5ca 7e301b5bee |
April 2016 | (com.android.henbox) [com.ziipin.software] |
(Uyghurche Kirguzguch) [Emojicon] |
| 2 | 1749df47cf37c09a92 b6a56b64b136f15ec 59c4f55ec835b1e569 c88e1c6e684 |
May 2017 | (cn.android.setting) [com.apps.amaq] |
(设置 (Backup)) [Amaq Agency] |
| 3 | 4d437d1ac29b1762c c47f8094a05ab73141 d03f9ce0256d200fc6 91c41d1b6e7 |
June 2017 | (cn.android.setting) [com.example.ourplayer] |
(islamawazi) [islamawazi] |
Table 2 Example HenBox variants containing embedded apps
Sample 1 marks the first HenBox sample we saw embedding a legitimate app within its assets to be dropped and installed on the victim device as a decoy. The legitimate app in question was a Uyghur language keyboard app targeted at native speakers of the Uyghur language and their smartphones.
Sample 2, has the package name cn.android.setting masquerading as Android’s Settings app, which has a similar package name (com.android.settings). This variant of HenBox also used the common green Android figure as the app logo and was named 设置 (“Backup” in English). This variant’s app name, along with many others, is written in Chinese and describes the app as a backup tool. Please see the IOCs section for all app and package name combinations. Interestingly, the embedded app in sample 2 is not a version of the Android Settings app but instead the “Amaq Agency” app, which reports on ISIS related news. Reports indicate fake versions of the Amaq app exist, likely in order to spy on those that use it.
A month after observing sample 2, we obtained another which used the same package name as sample 2 (cn.android.setting). However, this time the app name for both HenBox and the embedded app were identical: Islamawazi. Islamawazi is also known as the Turkistan Islamic Party or “TIP”. This organization was formerly known as the East Turkestan Islamic Party and is purported to be an Islamic extremist separatist organization founded by Uyghur jihadists. The embedded app appears to be a media player.
These examples, together with the HenBox app placed on a very specific third-party app store, point clearly to at least some of the intended targets of these malicious apps being Uyghurs, specifically those with interest in or association with terrorist groups. These threat actors appear to be choosing the right apps – those that could be popular with locals in the region, at the right time – while tensions grow in this region of China, to ensure a good victim install-base.
HenBox Roosts
HenBox has evolved over the past three years, and of the almost two hundred HenBox apps in AutoFocus, the vast majority contain several native libraries as well as other components in order to achieve their objective. Most components are obfuscated in some way, whether it be simple XOR with a single-byte key, or through the use of ZIP or Zlib compression wrapped with RC4 encryption. These components are responsible for a myriad of functions including handling decryption, network communications, gaining super-user privileges, monitoring system logs, loading additional Dalvik code files, tracking the device location and more.
The remainder of this section describes at a high-level what HenBox is capable of, and how it operates. The description is based on analysis of the sample described in Table 3 below, which was of interest given its C2 domain mefound[.]com overlaps with PlugX, Zupdax, and Poison Ivy malware families discussed in more detail later.
| SHA256 | Package Name | App Name |
| a6c7351b09a733a1b3ff8a0901c5bde fdc3b566bfcedcdf5a338c3a97c9f249b |
com.android.henbox | 备份 (Backup) |
Table 3 HenBox variant used in description
Once this variant of HenBox is installed on the victim’s device, the app can be executed in two different ways:
One method for executing HenBox is for the victim to launch the malicious app (named “Backup”, in this instance) from the launcher view on their device, as shown in Figure 3 below. This runs code in the onCreate() method of the app’s MainActivity class, which in effect is the program’s entry point. This process is defined in the app’s AndroidManifest.xml config file, as shown in the following snippet.
|
1 2 3 4 5 6 |
<activity android:excludeFromRecents="true" android:label="@string/app_name" android:name="com.android.henbox.MainActivity" android:theme="@android:style/Theme.Translucent"> <intent-filter> <action android:name="android.intent.action.MAIN"/> <category android:name="android.intent.category.LAUNCHER"/> </intent-filter> </activity> |
Figure 3 HenBox app installed and visible on Android's Launcher view
Doing so executes code checking if the device is manufactured by Xiaomi, or if Xiaomi’s fork of Android is running on the device. Under these conditions, the app continues executing and the intent of targeting Xiaomi devices and users could be inferred, however poorly written code results in execution in more environments than perhaps intended; further checks are made to ascertain whether the app is running on an emulator, perhaps to evade researcher analysis environments. Assuming these checks pass, one of the main ELF libraries is loaded that orchestrates other components and provides functionality to the app’s Dalvik code through the Java Native Interface (JNI).
HenBox checks whether this execution is its first by using Android’s shared preferences feature to persist XML key-value pair data. If it is the first execution, and if the app’s path does not contain “/system/app” (i.e. HenBox is not running as a system app), another ELF library is loaded to aid with executing super-user commands.
The second method uses intents, broadcasts, and receivers to execute HenBox code. Providing the app has registered an intent to process particular events from the system, and one of said events occurs, HenBox is effectively brought to life through external stimulus from another app on the system broadcasting a request, or the system itself broadcasting a particular event has occurred. These intents are typically defined statically in the app’s AndroidManifest.xml config file; some HenBox variants register further intents from their code at run-time. Once a matching intent is triggered, the respective Receiver code will be executed, leading to other HenBox behaviors being launched, which are described later. Table 4 below lists the intents that are statically registered in this HenBox variant’s AndroidManifest.xml config file, together with a description of what that intent does, and when it would be used. Depending on the intent triggered, one of two Receivers would be called, in this instance they are called Boot or Time but the name is somewhat immaterial.
| Receiver | Intent Name | Description |
| BootReceiver | android.intent.action.BOOT_COMPLETED | System notification that the device has finished booting. |
| android.intent.action.restart | A legacy intent used to indicate a system restart. | |
| android.intent.action.SIM_STATE_CHANGED | System notification that the SIM card has changed or been removed. | |
| android.intent.action.PACKAGE_INSTALL | System notification that the download and eventual installation of an app package is happening (this is deprecated) | |
| android.intent.action.PACKAGE_ADDED | System notification that a new app package has been installed on the device, including the name of said package. | |
| com.xiaomi.smarthome.receive_alarm | Received notifications from Xiaomi’s smart home IoT devices. | |
| TimeReceiver | android.intent.action.ACTION_TIME_CHANGED | System notification that the time was set. |
| android.intent.action.CONNECTIVITY_CHANGE | System notification that a change in network connectivity has occurred, either lost or established. Since Android version 7 (Nougat) this information is gathered using other means, perhaps inferring the devices used by potential victim run older versions of Android. |
Table 4 HenBox variant's Intents and Receivers
Most of the intents registered in the AndroidManifest.xml file, or loaded during run-time, are commonly found in malicious Android apps. What’s more interesting, and much less common, is the inclusion of the com.xiaomi.smarthome.receive_alarm intent filter. Xiaomi, a privately owned Chinese electronics and software company, is the 5th largest smart phone manufacturer in the world and also manufactures IoT devices for the home. Most devices can be controlled by Xiaomi’s “MiHome” Android app, which is available on Google Play with between 1,000,000 and 5,000,000 downloads.
Given the nature of connected devices in smart homes, it’s highly likely many of these devices, and indeed the controller app itself, communicate with one another sending status notifications, alerts and so on. Such notifications would be received by the MiHome app or any other, such as HenBox, so long as they register their intent to do so. This could essentially allow for external devices to act as a trigger to execute the malicious HenBox code, or perhaps afford additional data HenBox can collect and exfiltrate.
Either method to load HenBox ultimately results in an instance of a service being launched. This service hides the app from plain sight and loads another ELF library to gather environmental information about the device, such as running processes and apps, and details about device hardware, primarily through parsing system logs and querying running processes. The service continues by loading an ELF, created by Baidu, which is capable of tracking the device location before setting up a monitor to harvest phone numbers associated with outgoing calls for those numbers with a country code “+86” prefix, which relates to the People’s Republic of China.
Further assets are decrypted and deployed, including another Dalvik DEX code file, which has various capabilities including registering itself as the incoming SMS handler for the device to intercept SMS messages, loading another ELF library that includes a version of BusyBox - a package containing various stripped-down Unix tools useful for administering such systems – and, interestingly, is capable of turning off the sound played when the device’s cameras take pictures.
The Android permissions requested by HenBox, as defined in the apps’ AndroidManifest.xml files, range from accessing location and network settings to messages, call, and contact data. HenBox can also access sensors such as the device camera(s) and the microphone.
Beyond the Android app itself, other components such as the aforementioned ELF libraries have additional data-stealing capabilities. One ELF library, libloc4d.so, handles amongst other things the loading of the app-decoded ELF library file “sux”, as well as handling connectivity to the C2.
The sux library appears to be a customized super user (su) tool that includes code from the com.koushikdutta.superuser app and carries the equivalent of a super user (su) binary in order to run privileged commands on the system. The primary goal of sux appears to be steal messages and other data from popular messaging and social media apps specified within the HenBox sample. A similar tool, with the same filename, has been discussed in previous research but the SpyDealer malware appears unrelated to HenBox. More likely, this is a case of common attack tools being re-used between different threat actor groups.
This particular HenBox variant, as listed in Table 3 above, harvests data from two popular messaging and social media apps: Voxer Walkie Talkie Messenger (com.rebelvox.voxer) and Tencent’s WeChat (com.tencent.mm). These types of apps tend to store their data in databases and, as an example, HenBox accesses Voxer’s database from the file “/data/data/com.rebelvox.voxer/databases/rv.db”. Once opened, HenBox runs the following query to gather message information.
|
1 2 3 4 5 6 |
select messages.timestamp ,messages.sender,messages.body,profiles .first || profiles .last,profiles.profile_username from messages,conversations left join profiles on messages.sender=profiles.username where messages.thread_id=conversations .thread_id |
Not long after this variant was public, newer variants of HenBox were seen, and some had significant increases in the number of targeted apps. Table 5 describes the latest variant seen in AutoFocus.
| SHA256 | Package Name | App Name | First Seen |
| 07994c9f2eeeede199dd6b4e760fce3 71f03f3cc4307e6551c18d2fbd024a24f |
com.android.henbox | 备份 (Backup) | January 3rd 2018 |
Table 5 Recent HenBox variant with updated functionality
Table 6 contains an updated list of targeted apps from which this newer variant of HenBox is capable of harvesting data. Interestingly, the two communication apps described above as being targeted by the HenBox variant listed in Table 3 do not appear in this updated list.
| Package Name | App Name |
| com.whatsapp | WhatsApp Messenger |
| com.pugna.magiccall | n/a |
| org.telegram.messenger | Telegram |
| com.facebook.katana | |
| com.twitter.android | |
| jp.naver.line.android | LINE: Free Calls & Messages |
| com.instanza.cocovoice | Coco |
| com.beetalk | BeeTalk |
| com.gtomato.talkbox | TalkBox Voice Messenger - PTT |
| com.viber.voip | Viber Messenger |
| com.immomo.momo | MOMO陌陌 |
| com.facebook.orca | Messenger – Text and Video Chat for Free |
| com.skype.rover | Skype; 3rd party stores only |
Table 6 Targeted apps from a newer HenBox variant
Most of these apps are well established and available on Google Play, however, com.skype.rover appears to be available only on third-party app stores. The same is likely to be the case for com.pugna.magiccall but this is unknown currently.
It’s clear to see that the capabilities of HenBox are very comprehensive, both in terms of an Android app with its native libraries and given the amount of data it can glean from a victim. Such data includes contact and location information, phone and message activity, the ability to record from the microphone, camera, and other sensors as well as the capability to access data from many popular messaging and social media apps.
Infrastructure
While investigating HenBox we discovered infrastructure ties to other malware families associated with targeted attacks against Windows users – notable overlaps included PlugX, Zupdax, 9002, and Poison Ivy. The overall image of these ties is below in Figure 5 and paints a picture of an adversary with at least 5 malware families in their toolbox dating back to at least 2015.
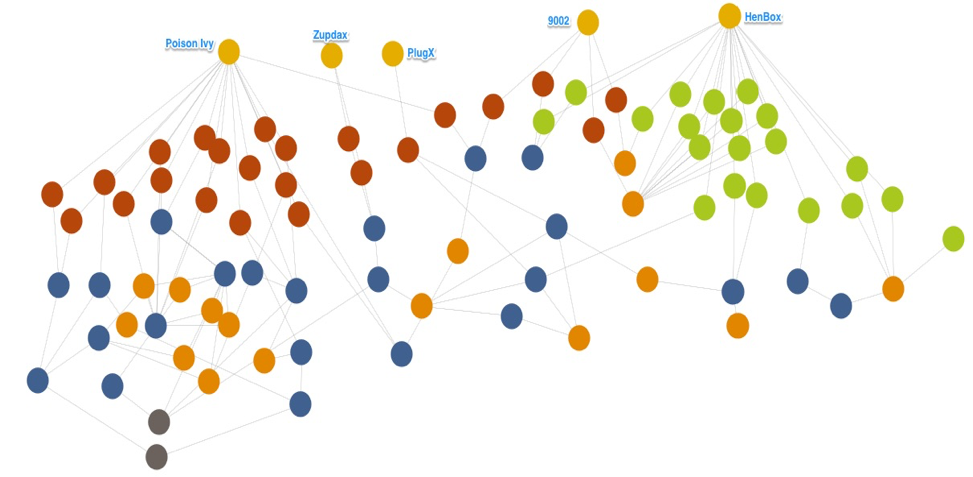
Figure 5. HenBox and related malware and C2s
The overlap between the HenBox and 9002 malware families Unit 42 has seen involves three shared C2s between several samples; the first IP below is used for more than half of the HenBox samples we have seen to date:
- 47.90.81[.]23
- 222.139.212[.]16
- lala513.gicp[.]net
The overlaps between the Henbox, PlugX, Zupdax, and Poison Ivy malware families involves a web of shared C2s and IP resolutions centered around the below:
- 59.188.196[.]172
- cdncool[.]com (and third-levels of this domain)
- www3.mefound[.]com
- www5.zyns[.]com
- w3.changeip[.]org
Ties to previous activity
The registrant of cdncool[.]com also registered six other domains. To date, Unit 42 has seen four of the seven (the first three in the list below, along with cdncool[.]com) used in malicious activity and it is reasonable to assume the remaining three are or were intended to serve the same purpose.
- tcpdo[.]net
- adminsysteminfo[.]com
- md5c[.]net
- linkdatax[.]com
- csip6[.]biz
- adminloader[.]com
Unit 42 published a blog in July 2016 about 9002 malware being delivered using a combination of shortened links and a file hosted on Google Drive. The spear phishing emails had Myanmar political-themed lures and, if the 9002 C2 server responded, the Trojan sent system specific information along with the string “jackhex”. “jackhex” has also been part of a C2 for what is likely related Poison Ivy activity detailed below, along with additional infrastructure ties.
The C2 for the aforementioned 9002 sample was logitechwkgame[.]com, which resolved to the IP address 222.239.91[.]30. At the same time, the domain admin.nslookupdns[.]com also resolved to the same IP address, suggesting that these two domains are associated with the same threat actors. In addition, admin.nslookupdns[.]com was a C2 for Poison Ivy samples associated with attacks on Myanmar and other Asian countries discussed in a blog published by Arbor Networks in April 2016. Another tie between the activity is the C2 jackhex.md5c[.]net, which was also used as a Poison Ivy C2 in the Arbor Networks blog. “jackhex” is not a common word or phrase and, as noted above, was also seen in the beacon activity with the previously discussed 9002 sample. Finally, since publishing the 9002 blog, Unit 42 has also seen the aforementioned 9002 C2 used as a Poison Ivy C2 with a Myanmar political-themed lure.
In our 9002 blog we noted some additional infrastructure used either as C2s for related Poison Ivy samples, or domain registrant overlap with those C2 domains. When we published that blog Unit 42 hadn’t seen any of the three registrants overlap domains used in malicious activity. Since then, we have seen Poison Ivy samples using third-levels of querlyurl[.]com, lending further credence the remaining two domains, gooledriveservice[.]com and appupdatemoremagic[.]com are or were intended for malicious use. While we do not have complete targeting, information associated with these Poison Ivy samples, several of the decoy files were in Chinese and appear to be part of a 2016 campaign targeting organizations in Taiwan with political-themed lures.
Conclusion
Typically masquerading as legitimate Android system apps, and sometimes embedding legitimate apps within them, the primary goal of the malicious HenBox appears to be to spy on those who install them. Using similar traits, such as copycat iconography and app or package names, victims are likely socially engineered into installing the malicious apps, especially when available on so-called third-party (i.e. non-Google Play) app stores which often have fewer security and vetting procedures for the apps they host. It’s possible, as with other Android malware, that some apps may also be available on forums, file-sharing sites or even sent to victims as email attachments, and we were only able to determine the delivery mechanism for a handful of the apps we have been able to find.
The hosting locations seen for some HenBox samples, together with the nature of some embedded apps including: those targeted at extremist groups, those who use VPN or other privacy-enabling apps, and those who speak the Uyghur language, highlights the victim profile the threat actors were seeking to attack. The targets and capabilities of HenBox, in addition to the ties to previous activity using four different Windows malware families with political-themed lures against several different South East Asian countries, indicates this activity likely represents an at least three-year-old espionage campaign.
Palo Alto Networks customers are protected by:
AutoFocus customers can investigate this activity using the following tag. To date we believe HenBox is not a shared tool, however, the remainder of malware used by these attackers is shared amongst multiple groups:
Android Hygiene
Update: Keep installed apps updated. Much like patching Operating System and application files on PCs, Android and apps developed for the platform also receive security updates from Google and app developers to remove vulnerabilities and improve features, including security.
Review: App permissions to see what the app is potentially capable of. This can be quite technical, but many permissions are named intuitively describing if they intend to access contacts, messages, or sensors, such as the device microphone or camera. If you the permission seem over the top compared to the described functionality, then don’t install. Also read the app and developer reviews to evaluate their trustworthiness.
Avoid: Third-party app stores that may host pirated versions of paid apps from the Google Play app store, often such apps include unwanted extra features that can access your sensitive data or perform malicious behaviors. Also avoid rooting devices, if possible, as apps could misuse this power.
IOCs
Most recent samples first:
| sha256 | apk_package_name | apk_app_name | apk_app_name_en |
| 446734590904c5c44978e4646bbbc629d98236c16e29940b32100c1400aebc88 | com.android.henbox | 备份 | Backup |
| ea0786bfe145d8c763684a2fdf2eb878da29c1b6ae5aacd1a428c9ffead4bad8 | com.android.vivibox | 备份服务 | Backup service |
| 16bb6ff97999b838a40b66146ff4c39b9c95906f062c6fe1e3077e6e30171a4d | com.android.vivibox | 备份 | Backup |
| 0fa384198ae9550e008e97fa38e8a56c4398fc91e12eddba713966bfed107130 | com.android.henbox | 备份 | Backup |
| e835e4907c9ff07a3a8281530552eaed97d9dea5b182d24a8db56335bad5213d | com.android.cicibox | 备份服务 | Backup service |
| 9192602e5a3488c322025991ca7abcbdc8f916e08f279004a94cec8eb9f220b4 | com.android.vivibox | 备份 | Backup |
| 9b57ab06650a137a5962b85ca9ae719e9c3956d68938a6a2425dffe8d152941a | com.android.webbox | 备份服务 | Backup service |
| 7bf0e70fb4ffca19880fecdeb7e7e5d0fb4681064a98c71056cbb29c80ed6119 | com.android.henbox | 备份 | Backup |
| 51cfc1a658e63624706a6bb2ed2baa63c588e7ce499bd116a3d5752743fefb54 | com.android.henbox | 备份 | Backup |
| 3417899195780c8186356d49bc53b600b3b0e49aae83d9aeb27e518b6964be04 | com.android.henbox | 备份 | Backup |
| f0fd8c5f4487df7592e5b7fa02f19f23d3ad43f5aaab84257cc560bf5ea76f1e | com.android.henbox | 备份 | Backup |
| a6c1da9559d72563848802ed14a7421515009c2a0ffb85aab74c6e42584c222d | com.android.cicibox | 备份服务 | Backup service |
| bf0ab0362ee39191587921b75ab92bf6da12e377dbfdf4f7a053c1217841bdfc | com.android.vivibox | 备份服务 | Backup service |
| f5abd5e7e325f16df3e96ff55a19ebf524f40f9ade76003355eb1d68bc084006 | com.android.vivibox | 备份 | Backup |
| 201eca94a9e8023d021a2b4a1517c4e46cd01e3be323bc46660c1c6f42aa6abf | com.android.henbox | 备份 | Backup |
| 7b7887d4ad7cab0c53d6f8557bbdf616985f3434ba536a5683f6fba604151d04 | com.android.henbox | 备份 | Backup |
| 4eb768b52b687de49c7da8845bbd7671e2e076fe64bf23596a409108ef3fbbbc | com.android.henbox | 备份 | Backup |
| a7cfae9b12542b293d8265770a10946d422736d6f716af17f7b963603e422c51 | com.jrzheng.supervpn.view | SuperVPN | SuperVPN |
| 3c2109adf469bfc6c320ac824355f97a2b0f5ff01891d1affcd1a5b017c97195 | com.android.webbox | 备份服务 | Backup service |
| 2a7e456d2700ba13af48efdcf1f699bf51b6901a3ba5c80c009aaaca86235e5d | com.android.henbox | 备份 | Backup |
| 3d525435cbd88b4f1f97e32e2c6accf7855f4cc576ecbd87ad05a05ddd2d2f79 | com.android.vivibox | 备份服务 | Backup service |
| 5a999904b2f03263a11bcc077ad179333b431fb9e6e8090f371d975ba188e55e | com.android.cicibox | 备份服务 | Backup service |
| 4d1e37e5840e8a4d5ae0f60cf33c593f595af200fbf998c3af809fd0c225c475 | com.android.henbox | 备份 | Backup |
| 3cce965887d4677069cb9160d7c7c122087a5f434e095a9f0848c3e838bca9f5 | com.android.henbox | 备份 | Backup |
| 8095cf4f6aec1983bd9f81ca85c1b27415e200b315f757613afb4f0334c99f0b | com.android.henbox | 备份 | Backup |
| b098be6fd1859ee70ef123c59d5e2a1db435f990c9378b41af0c005f76ba24f2 | com.android.henbox | 备份 | Backup |
| 56c1e23b12e83573440019084b9ce39f8f5ddd9d6de51edaf1f83e020fc648a0 | com.android.cicibox | 备份服务 | Backup service |
| 75fef2a0f05ae2ad971b01041fd3ed5ceacce306d78930bc2eba190c39799bc7 | com.android.henbox | 备份 | Backup |
| a3deca8203792d4b34242e8f5d0f7e2e3d054f08d74885ab7ff6f3a6f4b2578a | com.android.henbox | 备份 | Backup |
| 77b6e8cd1e6de9ee22bf0e9d735089ae24134ab955f0975d4febc9ed6b60af38 | com.android.henbox | 备份 | Backup |
| 9f8909b1615aaa0fed38ad27162ccf3437e2eaa59cb0c990261c866f075c4113 | com.android.henbox | 备份 | Backup |
| 7ffc1afd5749e7731f4161a6348205555e5892f1bd3446b6d0c5e7bbaa5917e3 | com.android.henbox | 备份 | Backup |
| a1644194faac76a1d49fd96b875a3f9026993e9f21f6dbc50dc59aeb5e7dac4b | com.android.henbox | 备份 | Backup |
| 2e4aa7777ba449071b90c0c13b803ddf6c6f10576eb9806acde6c3d1391db463 | com.android.henbox | 备份 | Backup |
| af2d44e36cc28727e29b0d9aecb4b17534a195faacbf4192ce1483a9bde65edc | com.android.henbox | 备份 | Backup |
| 5010236b481d8d2ebc45ee95154f10ffbb317eced86401486f63276520049896 | com.android.henbox | 备份 | Backup |
| 8de4e886b69046c2942e26d8b2f436695ca27060f6a74c797c620502f87887c9 | com.android.henbox | 备份 | Backup |
| fed084773542120fe77b880fc136bd20979cddc286b75b651d01aa6e32234b2d | com.android.henbox | 备份 | Backup |
| 43ce0c3e63de64f032ea7d4ca77c4b40b86d57e1d237f771b21c1f9c8f41eafb | com.android.henbox | 备份 | Backup |
| 6e1812f7bf313552bc60b6be5b46bdfd44582775e3cb19cf6a231a903aec508b | com.android.henbox | 备份 | Backup |
| 7774432c67f3d3688a1a1b21edc0a73d9d47990cc1f132663b0010ff4bbd6e87 | com.android.henbox | 备份 | Backup |
| 59ca2754279d9cba40334c35907e2e1fc6fd2888b2c180e5b0b8d73accbb40f2 | com.android.henbox | 备份 | Backup |
| 2c5934db000a2838d42cf705453e29d16f4d4bb462fa65e134ce78b4266cefee | com.android.henbox | 备份 | Backup |
| e326501a0fb15bf19ac135f501b84caa2587d1fb2cad9e034f1756898686dab4 | com.android.henbox | 备份 | Backup |
| 14f715228acff7d8bad057e4bf996635d76ab41ae25ca8a3f90196caeb241446 | com.android.henbox | 备份 | Backup |
| 2be931f008a9ea62aa35091eb9a5629824e81499ce7a5219101ccd39a02ecdec | com.android.henbox | 备份 | Backup |
| 51db059a833377666f92f64ae1e926b83da8821876c66949e320b55c1a929ff8 | com.android.henbox | 备份 | Backup |
| dee79253deaaa57af0fddb2c8ec5d4cc0546dfe3c1d05c2916a44a37eef3d9f8 | com.android.henbox | 备份 | Backup |
| ec2e060ac633978b9b700aa95784255b9796f4fb51c188b1c79d5947df07bf98 | com.android.henbox | 备份 | Backup |
| a6c7351b09a733a1b3ff8a0901c5bdefdc3b566bfcedcdf5a338c3a97c9f249b | com.android.henbox | 备份 | Backup |
| ae5598ccb3f2f31d2ec967808988a47d6ce4d1cd5e6808d1194ee93c6400039c | com.android.henbox | 备份 | Backup |
| 6f5e7f6ca2f25667d5fe55d7e8ec1b816d6db8b31cb28dff43b4f2f73d70ecdb | com.android.henbox | 备份 | Backup |
| 4cbb5a0d9b6f64dc9d8dd9aaac5651649e24b2cd7248eb9db32191102559ab9c | com.android.henbox | 备份 | Backup |
| c375aad52c292b4d5c4efb02a33e2325a27f27158bb13c048f533a2a9d0837fb | com.android.henbox | 备份 | Backup |
| 779b09c61951818e5afb47c369fe9b5fa7b7f6139f589f14b3042b2ac96809d8 | com.android.henbox | 备份 | Backup |
| 7ba216b88f84c9a0ce90ca5500ddc2e80100b23ef3784d133b69870768f1e3bc | com.android.henbox | 备份 | Backup |
| 077239b3bedaa850b82204fdd42e5e45fedc3dfc2f6da5aab04d768370e990fa | com.android.henbox | 备份 | Backup |
| be548c26d0863b812948a16f982e96557319346fad897f67dc7873108203fdce | com.android.henbox | 备份 | Backup |
| 54366ee485b43cea10624d62247a48b12c1ce35c49295491f7fbb6323c68da7b | com.android.henbox | 备份 | Backup |
| 51714b8f34db94cbd8916374af4d8e63b56ef41fa819d2d697f1a3975a32960e | com.android.henbox | 备份 | Backup |
| 48f38b671847bfba3810b74d1d815c2bb4cc94392b98e1f59f95e748eb410465 | com.android.henbox | 备份 | Backup |
| d0e58c3e9d881f875532d1bb8bee63e4ac8728458708361f754db97fba6be22e | com.android.henbox | 备份 | Backup |
| 8b78f469f3eda0cb02cfbf5598f0a7449cb63b7181d7fd5037ebb9cb8aff30a4 | com.android.henbox | 备份 | Backup |
| 49556e972a35c9d592bf64ab37056f6da356b2061c1ce269d9c3af73978756d9 | com.android.henbox | 备份 | Backup |
| 1d4dadae0c696fde2fef99eb99188509dc0d5fbac7ee07d4f0d5a92dcc922ad7 | com.android.henbox | 备份 | Backup |
| 3c62d00a9740c49cf01fb7635260ff71e0ac44cf80da749ca4101869120f2233 | com.android.henbox | 备份 | Backup |
| 993692d5540c40614f4da430cf4cea64a7e0e7f950452abae19bf608afdf20a6 | com.android.henbox | 备份 | Backup |
| 3e026154767b6a101d3a852946e9eb3ed1c96662490afe9b601469a8459e325b | com.android.henbox | 备份 | Backup |
| 6a518d29232d3f68aa5c78df4a8d212f924e03379dc2be0a388b3118779fe583 | com.android.henbox | 备份 | Backup |
| 70512a566f33c636ad071d18e82db89f9531a6133be89b7d3f18fc9f7730b078 | com.android.henbox | 备份 | Backup |
| 53238af90efd8531686432245c516db04cd163584a811d6e5835a42fe738fbab | com.android.henbox | 备份 | Backup |
| 2f2277898f34a91a365f1a090d72678768c5e420c8350f340cc4b4602cd8a710 | com.android.henbox | 备份 | Backup |
| b48edd2270b1aeb014291eb3ac2aaa1d4b7ee4694965d0de2c0978b2feae946d | com.android.henbox | 备份 | Backup |
| 45e7dc9c0e33d4754384365a60604c66d72356a994cbed8e8eab8796cf1579e2 | com.android.henbox | 备份 | Backup |
| a1e465d905434d5dae3bb7acb7c148ef8ed0d341a6d9121d09adbc126cc3a907 | com.android.henbox | 备份 | Backup |
| 4d437d1ac29b1762cc47f8094a05ab73141d03f9ce0256d200fc691c41d1b6e7 | cn.android.setting | islamawazi | islamawazi |
| d29646f2c665ef91c360e24242c634ee9051d4ab01cb8f87265088e47f41d690 | com.android.henbox | 备份 | Backup |
| 2345a56d61e052af3265ee0fae47b22f1551ede4eee45bca30ad5fb9fac7a922 | com.android.henbox | 备份 | Backup |
| 44388ec38ee36177d6804d778ee554b2d063db3b88d7480eca6587ff68a15982 | com.android.henbox | 备份 | Backup |
| 286bd20f3ea944703c8c87e66708d6b32046a640863afba7f3c4c72dc28d37d1 | cn.android.seting | 设置 | Setup |
| 7f28caeaa484496f85c80580cd88671961149aae2295c8777becb2970455504c | com.android.henbox | 备份 | Backup |
| 89ef65813bccb8197da4af68ba8f9e8e123f3aad4ed41736f8039ad2c6817a25 | com.android.henbox | 备份 | Backup |
| 1749df47cf37c09a92b6a56b64b136f15ec59c4f55ec835b1e569c88e1c6e684 | cn.android.setting | 设置 | Setup |
| 5f16c23f92a10de59efc9a081e0c79458faa3fabb24a1356dbfff7cea8611a3e | com.android.henbox | 备份 | Backup |
| 66eec9ffa2906e56656e649d5b632526e829d7142a75cd27a006bf82775e8c45 | com.android.henbox | 备份 | Backup |
| a728c653b9c7be4b058eff329afb826db755fdddc4e10ba67191816db7dbeac0 | cn.android.setting | 爱奇艺 | IQIYI |
| c4ee98d58d38f6109d843955277f1a37bfb138a14113c6cb38bcb6eb857d4977 | cn.android.setting | 设置 | Setup |
| 577ed81e07b62d9c363c505271d1f2a81592a69e1a60a82fbe8fff16e7d3419d | cn.android.setting | 设置 | Setup |
| b8f785a6581bf438b1947e498b8f2255607440347d8f8b5cb31f3b98427330e6 | cn.android.setting | 设置 | Setup |
| 5a3c44a6e8c8e02e69caa430f41ec80b94740d099bbcfbf39cf08280fc6e16bb | com.android.henbox | WJ VPN | WJ VPN |
| 184e5cbebef4ee591351cfaa1130d57419f70eb95c6387cb8ec837bd2beb14d6 | com.android.henbox | 备份 | Backup |
| efa3cd45e576ef8ab22d40fc9814456d06a6eeeaeada829c16122a39cb101dbf | com.android.henbox | 备份 | Backup |
| 9d85be32b54398a14abe988d98386a38ce2d35fff91caf1be367f7e4b510b054 | com.android.henbox | 备份 | Backup |
| a8ea1140a739b2aeeb838d7fe2c073cb834bce46db22071022bd181a59422af1 | com.android.henbox | 备份 | Backup |
| 80a35bcbce326d05dd74ed05560db41a0f9471c4922fc9fe88d0b1a94c3cb1ae | cn.android.setting | 设置 | Setup |
| 0e31575bf0001d818d87aa134e728f62e7f2d27ff9437897303eb8ae1962a865 | cn.android.setting | 设置 | Setup |
| d3dd162e7dee6022826e7fef23cb84f17a948d2761013a09943f165f378197e0 | cn.android.setting | 设置 | Setup |
| 3b345ffe7fac9aef0c9e0be3f01e8f9e1f3e0442849cc0e3f979b9866465b6bc | cn.android.setting | 设置 | Setup |
| 0a4f38a83abbbab3a039be95862df7848f28513baa1da52a74a9e6a31f63c9b7 | com.android.henbox | 备份 | Backup |
| a267176bdc1779b19fde2e38f5f062478e8cf173582e38a26538512d64d85ecd | cn.android.setting | 设置 | Setup |
| 7603126f04e9e7cff828aabc060349d6dfbd76e795df7b0e798b3b0914ad13a0 | com.android.henbox | 备份 | Backup |
| 1da0e30b4b2ad2626a3f069f0f50f81d29b789d41385db26d7c84da3af02cd1c | com.android.henbox | 备份 | Backup |
| ddea532ef46abb9bfa77acdbd38155d9a92381f777fe4c797967203578aa0966 | com.android.henbox | 备份 | Backup |
| a89bdb4fd54b9488fd6f2685a4dcfa1c106d4ac9f9fb8f8992e557e306184f1a | com.android.henbox | 备份 | Backup |
| b0bbcee232f27a1b366f8a7ed1d2c3056f9a67fa70e42c1fa7cfb7c778df8cb5 | cn.android.setting | 设置 | Setup |
| bf16b9f012e1a0724f95a0e61a8748be3c9fc3fe3bb5a82bf3efd9b8211591fb | cn.android.setting | 设置 | Setup |
| ad5a6b9ca0389c458dde73a456404634eec473cf5833914c7466af41e23b6ea9 | cn.android.setting | 设置 | Setup |
| a5d9efae12c9e5913156b5415581678748bdeed25a5767438afadc869d25e0d4 | cn.android.setting | 设置 | Setup |
| b5598c4a26f3b4a143a413c46935f0506afd7e400ecf4c6ca05595e83d8dc2c7 | cn.android.setting | 设置 | Setup |
| 4f6173659e2c23835228f2e05daacecb618c099878d0028dd9a52b9682de2ac4 | cn.android.setting | 无秘 | No secret |
| 7d8a47cda9367ee31ebf58dd226afc583b34a73476ed5ff1b2b3f2460cd4c339 | cn.android.setting | uyhl | uyhl |
| b34b09d7b4bee3125ea9b27c128c4239c78d3be95d9d5dff73c68e479353db5b | cn.android.setting | 设置 | Setup |
| b3413e09ceecc305187d08007ea86f654a451952807e37b8f2dcd14a8127042a | cn.android.setting | 设置 | Setup |
| 718bab91ba29791a494c31783b64ce1fe3d78bcdd6a6f909588e198fbea3b3cf | cn.android.setting | 设置 | Setup |
| de9d1c68ef9df6dd72455f50d1cdffd76e24a501bbbaa3cacc4aedb74b2f743d | cn.android.setting | 探探 | Explore |
| 55e65d1fba82a21b0ee52435be890279cf7ae747abba7f448a6547ba2ed9666e | cn.android.setting | 设置 | Setup |
| 801d54f829668487c2ed28dc56beb6f156a6100a3be12805e1104fb9f68f6a00 | cn.android.setting | 设置 | Setup |
| 3ffa8ef36934420b08e4139385400da774f61cabe000557ff025af650f2964bb | cn.android.setting | 设置 | Setup |
| 8b4e60160089b6af71e3c555c4bdaa9344b76a5f0dfd1ecc3a6e8c23f0940b2a | cn.android.setting | 0 | |
| b779a7a05c226a14c2f4bad1f22c493a2a9de8b988b01602fbe60d1f6dc2ba8c | cn.android.setting | 0 | |
| 4a8c5194183f2a5b593654a29213c6f705f083ddbbff10a0bb1e7695c66a0f89 | cn.android.setting | 0 | |
| 775c2dbf6dd7423bd098b216bd6dcf11104e885e451fa95ae64dc18fb54a34c7 | cn.android.setting | 0 | |
| 228d1c80a92641c6ba9c9d1e68146e9bb66f02605135c2603db3ace692cc05f2 | cn.android.setting | 0 | |
| 4ecf03a1eaa0255340a41e48728be1d50dab724b72f9096a1f537fa578e76d17 | cn.android.setting | 0 | |
| 8a28fed36cf0d8640c7086770614e33d3788200bc7b0b408873873cd17e31653 | com.android.henbox | 0 | |
| 35b1f11a97dd5c05c87328e2ed4ae5776b84d3ce6cf4cdbc2faa1865dab2e09b | cn.android.setting | 0 | |
| bb91d7bbea783bacd57a92691ebcbb449d9606f2f3bbb77538ec751a8b01d8a9 | com.android.henbox | 0 | |
| 011509bb9cde31c0b45c49747ff150abcfa66d283ff986f167bf564bacfded4d | com.android.henbox | 0 | |
| da6d75e996b0bafad782d87c809269ef5ccfa62c938039790333f0f2b4ecafe3 | cn.android.setting | 0 | |
| eb31fc24f727bc6f25b7a90dc86c127099384398b7182ae52d3fe23950e9ed8c | com.android.henbox | 0 | |
| 6d441e6b75fa0ea1880937d7c94dbd1caaa210915d386dfb5a01ca22fd813d28 | com.android.henbox | 0 | |
| c153ed3b2ae96cb2ec55294f89180302f89e9dbca6a192eec7bd4f3591b8252e | cn.android.seting | 0 | |
| 2510aa8736c5462e8784f1cf494716bb923f97645899c73c56ead1ff58b35499 | cn.android.setting | 0 | |
| 0bfbbca56718b5bae7e21613a9884ea80db53aa1eca9cacf5a793e52f6a724e7 | com.android.henbox | 0 | |
| e9da842ccf4a681226577c26e2becea079080a4b6838171c06bb358db132bc5e | cn.android.setting | 0 | |
| 20fcff9826373d50abe813d3cb0272bf7b65617196cd4ac8d4646b8fd3256bea | cn.android.setting | 0 | |
| 0387baebb2b0c678e46e7291325e91118c53a3206d73c1145c082b10cf6a65f1 | cn.android.setting | 0 | |
| 0efaf91842a7e45562e97bda369efa6e14f98bf9d63782ec9c323fa246da549a | cn.android.setting | 0 | |
| cdbd4b98625c4766cbf72f69ce951faf49a13394ea85e7a23188e70a209609be | cn.android.seting | 0 | |
| d4ef4bdea69a248f9792211c4d52882ad6262f7223fc1aa9f328abe50412669f | cn.android.setting | 0 | |
| 3db36dc3b21dbd0a9037cda21606d37c1a1dd493346e00e36231a252a14446d6 | cn.android.setting | 0 | |
| 92c5fdf61b378e5252b0eb70a5cfd7af2d27c915aece48e32b9c2ba04a5fa5b3 | cn.android.setting | 0 | |
| 740a54e1f89cb321d13396987fd26d52c6c66c49894283c6d9889156e063ecb3 | com.android.henbox | 0 | |
| 7f76f102ab233528ce3cb111ae3b026cf16b3233c6bf3002de8a0daea3ebc0d7 | com.android.henbox | 0 | |
| 153794e424eceaba48e28e7f3333ab0c9c7addeda1c5de7835b191f5f25e4e34 | com.android.henbox | 备份 | Backup |
| a1bf2f3fcac9d1aae94eb7a6dc37be00185e102e504032f4ffa391ddbd4bd353 | com.android.henbox | 0 | |
| 444e73bd1020d08dc2901a041d675db1060815914024855daeddbc201e3ad4ee | com.android.henbox | 0 | |
| f88c84156d8e9fdec6f5c400135277ecd03e4b1d95e7d3b6f5b8c8a77eeb055f | cn.android.setting | 0 | |
| 2782265ddd3a0d94d4f2622366b3401002dcfe1a9b99b7cbf6d5e824ff14d728 | com.android.henbox | 0 | |
| efff4243b6143c937509f52dbe7c4e40ceb2eb226f7cc1c96d8cf9f287668e37 | cn.android.setting | 设置 | Setup |
| 000473f7168ebda3de054a126352af81b61dd0be462ae9b3c7ccc0bc5cea7986 | cn.android.setting | 0 | |
| 6f0de72ee2df4206102c1ff93955fef07cee84a1ba280ef3eda3db9a7eafb22e | cn.android.setting | 0 | |
| 2f7aa05b16d870d34feb1faa62bbfb9c5cffd4a52ea094c66657887b7c7046d4 | cn.android.setting | 0 | |
| 198ff17259ad377fae62ca49daaed0d9313831d5a12b16a79dd54045eb6909b8 | cn.android.setting | 0 | |
| 88c08e7084d4e0db14fc5fec6c906ff89e68b54df09096d49573b1906dd1ecd2 | cn.android.setting | 0 | |
| 5fff623781636b2af95327293f246e0d83b90012f067a8c9e6c2b5869e606465 | cn.android.setting | 0 | |
| a26802ebe8ad4dc076becbc18b32a825cf057ff2059a0742ece86afe6fcb496c | com.android.henbox | 0 | |
| e0427ca401d68c347ef14f65a94735f76238f59710d99c4097e51da23cbb2a6d | cn.android.setting | 0 | |
| cf36fb6f2d4029876f50d6a1eb9eafb13eb0bc6a57e179172ffe67a305f33c41 | cn.android.setting | 0 | |
| d68070f75341ce070b11a4ecda28d80a85303fa102fb4cb84c3dcbf97863bcc5 | cn.android.setting | 0 | |
| 60adc526a1bfa8df150c25016d220544671a62820493b66a8467436181b8d224 | cn.android.setting | 0 | |
| 0589bed1e3b3d6234c30061be3be1cc6685d786ab3a892a8d4dae8e2d7ed92f7 | com.android.henbox | DroidVPN | DroidVPN |
| f28761f897e3a0e1dcdb0a993076a1cc48a1b17361d3f401aa917406332a79f1 | 0 | ||
| fa5a76e86abb26e48af0b312f056d24000bc969835c40b3f98e5ca7e301b5bee | com.android.henbox | Uyghurche Kirguzguch | Uyghurche Kirguzguch |
| 5808df07cedf15451ab0984e9c60b077602de258319d48cf88b0cc4ca7bb57a0 | 0 | ||
| b0e0d35649d6e5405d051580d0c2a7ca5d3eb58f38bd51d0b8b7b98813256ea1 | 0 | ||
| 2db13b0cdede04b1b050744114e6c849e5e527b37bcd22984b265dff874dd411 | 0 | ||
| c6117397a54a1c2fda6efe40b1a209c14834f9ecb82136e06174c16644a59657 | 0 | ||
| ed35dab84aa4de72e782aef8cead90688d5c664de878207488828ed16902e828 | 0 | ||
| 2a7ab147d9e7c7f5349f5f929a2f955fb03b376d29d02d5a41d5e6da31d7cdcf | 0 | ||
| f3d04a7f77498acec86efc8d372c4d6eac591d8030f0a867ab856074e4da1fe6 | 0 |
Poison Ivy
d3d5a43a2a4f054d41acf6d5f5c1d4d87c7027d880172c3167eaa19f99db43db
dfcff48fb7ad43940c46430a4cd28d52564ea9b6e40a23ff4324da919a5fb783
12759f7fd01ffdea97954be5404d7e43a3941a7388129e7b6ace85f56b500cd8
26c0349af2b5ffebd01d86eff16a0158bb3ceba9ecb04a0c0bd442bc5736328d
ac8fc264c7ec3cf70836e1bb21f9a20174b04ad49731b8797d7d8bb95cb353e2
3d714e1c02c4baf37008fb2537b02c0c1f524fa49263f3400f97f9ef12f2c907
58246d040c79c2a75729511f09b09ae709fbfbaa0bad6e72751a586f7b37ec5e
c9be192a5acfc3b416dbd3fa800fa63851b3440d4187961978b33cef21aeaaeb
98f16b65b8acd4610077edd92dcb090e3d97f427dbb621827096071ed333b7b4
7cdd37ef4a45afa1b85c87f2a778cf8a7482f7beeee5178856d2f4acfa841135
c9be192a5acfc3b416dbd3fa800fa63851b3440d4187961978b33cef21aeaaeb
14e2e6bbcc68650bfd7c1eb374401eb606c7417dfae7bebb4bf86909e2ff524d
6a5998faa2be7d8b44f23cd5e02c9e3fa4a22bdba32e4663780aa035bddef239
b45e4ac7a790a7c6364cd93e371e548756f621028380c850059954340c0f13dc
b82785a6d488798c43f9dba0dd3f6cf8a4b03b308203452f641456dde09bedd8
PlugX
45c64508382f41056bed1a6d95927225791fe8fcd8ee9a9a133968b93c19e39f
9002
b2966c2702285d2cad851bae72fe22136d7975a2a50b43a855447703146c63f0
1b168603010e5179d001f78e47176296776938dde2351ca2250f2977eff043d0
C11b963e2df167766e32b14fb05fd71409092092db93b310a953e1d0e9ec9bc3
Zupdax
ce0a078d12698cfca9c4a00dcb6cb2425956538f271e6a151a0e646677ed4ae9
ffc3f886d142c5df35b8eb1c2aee77e553a74657b6054e596e8347b4f0c0975e
Domains and IPs
60.191.57[.]35
47.90.81[.]23
222.139.212[.]16
59.188.196[.]172
222.239.91[.]30
work.andphocen[.]com
andphocen[.]com
w3.ezua[.]com
lala513.gicp[.]net
logitechwkgame[.]com
www5.zyns[.]com
www3.mefound[.]com
w3.changeip[.]org
admin.nslookupdns[.]com
cdncool[.]com
dns.cdncool[.]com
tcpdo[.]net
3w.tcpdo[.]net
md5c[.]net
jackhex.md5c[.]net
up.outhmail[.]com
outhmail[.]com
queryurl[.]com
update.queryurl[.]com
re.queryurl[.]com
mail.queryurl[.]com
adminsysteminfo[.]com
info.adminsysteminfo[.]com












 Get updates from Unit 42
Get updates from Unit 42