Last year, Unit 42 reported a number of Google play apps infected with malicious IFrames in this report. Recently, we found similar cases on Google Play. However, this time, there are 145 Google Play apps infected by malicious Microsoft Windows executable files instead of malicious IFrames. We have reported our findings to Google Security Team and all infected apps have been removed from Google Play.
Notably, the infected APK files do not pose any threat to Android devices, as these embedded Windows executable binaries can only run on Windows systems: they are inert and ineffective on the Android platform. The fact that these APK files are infected indicates that the developers are creating the software on compromised Windows systems that are infected with malware. This type of infection is a threat to the software supply chain, as compromising software developers has proven to be an effective tactic for wide scale attacks. Examples include, KeRanger, XcodeGhost, and NotPetya.
Most of the infected apps were released to Google Play between October 2017 and November 2017, which means these apps have been in Google Play for more than half a year. Among these infected apps, several have more than 1,000 installations and 4-star ratings.
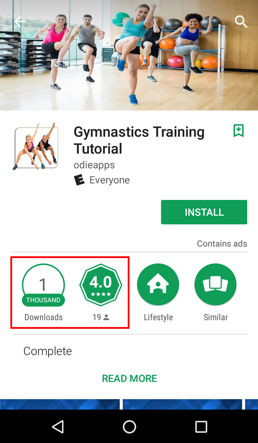
Figure 1: An infected app with 1000+ downloads and 4.0 rating
Interestingly, we saw a mixture of infected and non-infected apps from the same developers. We believe the reason might be that developers used different development environment for different apps.
Some of the infected apps include “Learn to Draw Clothing”, an app teaching people how to draw and design clothing; “Modification Trail”, an app showing images of trail bike modification ideas; “Gymnastics Training Tutorial”, an app letting people find healthy ideas for gymnastic moves.
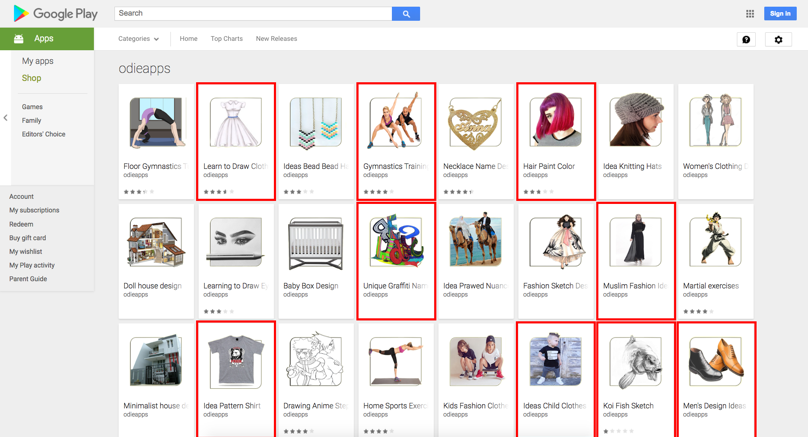
Figure 2: Apps from one developer (marked) are infected with Windows keylogger
Among these infected apps, one APK file may contain multiple malicious PE files at different locations, with different file names. However, there are mainly two PE files embedded across all of the infected apps.
According to the analysis results from WildFire, one PE file has infected 142 APK files including those apps on Google Play. The second PE file infected 21 APK files. 15 APK samples of them have both PE files mentioned above inside. Among these infected APK bundles, we found a number of other malicious PE files inside. These developers’ machines may be seriously infected by various malware families.
After investigating all those malicious PE files, we found that there is one PE file which infects most of the Android apps, and the malicious activity of that PE file is key logging. On a Windows system, this key logger attempts to log keystrokes, which can include sensitive information like credit card numbers, social security numbers and passwords. Besides, these files fake their names to make their appearance look legitimate. Such names include “Android.exe”, “my music.exe”, “COPY_DOKKEP.exe”, “js.exe”, “gallery.exe”, “images.exe”, “msn.exe” and “css.exe”.
During Palo Alto Networks’ WildFire analysis, the malicious PE files have the following suspicious activities when executed on a Windows system:
- Creates executable and hidden files in Windows system folders, including copying itself
- Changes Windows registry to auto-start themselves after restarting
- Attempts to sleep for a long period
- Has suspicious network connection activities to IP address 87.98.185.184 via port 8829
Potential Damage and Mitigation
The malicious PE files cannot directly run on the Android hosts. However, if the APK file is unpacked on a Windows machine and the PE files are accidentally executed, or the developers also issue Windows-based software, or if the developers are infected with malicious files runnable on Android platforms, the situation will go much worse.
Customers of Palo Alto Networks are protected by our WildFire and Traps for Android. WildFire is able to automatically detect these infected apps. Traps for Android protects Android devices, it automatically intercepts malicious apps installed on the device by leveraging WildFire and protect the device from malicious apps by blocking the app and notifying the user.
The development environment is a critical part of the software development life cycle. We should always try to secure it first. Otherwise other security countermeasures could just be attempts in vain.
Acknowledgements
We would like to thank Ryan Olson from Palo Alto Networks for their assistance during the analysis.
Appendix
PE files found in the infected apps:
9af18bd1bc68e0f49f8935a8cf662729cc1cec773f0237188762cebe75d48521
bdfabde9e45693a218e0391005f32e3546dedd0bc757cea2012ad42afdbe2f06
cadee0451947759cae1c94545ca910486e504c6544f6e60ba0a176b31df44abf
11ada55cc9dfcbafe969510b0711b110a8991b5deca2f296b895969958a66559
138f338653c82b86ea94829058a0e0bc18940903f6d7a01a7f0c2ba47f68e7e2
99074b45b20f794c35b72dbd6af2380497b8b482814822d88ca9c1c5cf83a400
57b345f635bf77f5b0da01248a1b798cbd8deb2c66306303ca595f3ccfaa8fbe
e355275030efa1ddb8bc233095c189a9cc6586ba241a1c4b7a9fe1875945bbf7
355c640a0cd3793f0e6ed96dd8175afe32d6bae7a8f8d1f1496167e5f2191195
88bdf6e443300988e160204778d859fb5a0dca775876ff8b079a4eb886ad4372
78c91a6071e73e7b0ebd10ff7a4a62d3412fe0f281e4ac064eeedbf707b15b22
524c780f3f35c5c9dd1bd935affe312f89ff851d51f9df21e78730134d4e7c50
cb09e6e28e2e0e3c031d99cb122ca767a23ecea1a2e98cb6d8bcf6ff7e61151e
b0442ad97086c4850133dcc72746f877cbbdb0b037374e598e231f8728dcda0c
07b07b74743364451876dca12531cdd515feff6264745be49add094388537685
edfadee37e5dd0e045d211ba9b09c2ac0f267790ac4ef8d7f9beced25d94c1fc
493d95c5222a86d581110d7c38b62a4e2015bf782ddac04c5a7e576a0955a727
5889a05fc1f161fe23ec9e3dfeb35ac225621f3c5c7019df7afa14aefdb96235
78f936fd6a8cabc39c727976ab9c2c6ceeb5be690186e2a729f59adaad7b3f4c
7268ea040b7ca1ab79d3f1eac279cf4cbc072c706b70672eba8d84387f76b3bf
688d39cfa1f581e841a896963b83081960844cdf06d3c71e7eab2746e498d5b1
df74876a564d38bf8fd3275fd0a429ee74c3f67b2e78f59d97c2ec8a7143bd9a
The following infected APK files were found on Google Play.
| SHA256 | App Name | Package Name |
| 1896ed8d12f5a7c3046acd929e64cc97e8acb020e40c1b3a2001b30003f50883 | Baby Room | com.KamarBaYi.odieapps |
| 290b7f930361d06e8f8c93aa9f97405d6b4b9fef7f9ac13c3c73c8966cf0e83a | Motor Trail | com.MotorTraiL.odieapps |
| b2fec79084611ad8abed3354399b2e759e903ec15976b9d10ac05e548964a1e9 | Tattoo Name | com.TatToNaMa.odieapps |
| b828b870a317693a0ae0544b9d0ffddcf6442da4d1979f6f8ccafcbe5c96d1e3 | Car garage | coml.GaRaSiMobiL.odieapps |
| 86661a4a611484f8db2593bfae241db9b53274a1736ec668335f878ed24795e4 | Japanese Garden | com.TaMaNJapanG.odieapps |
| 79e77835c9690ca0bc6d376659dd15f50e396bbc573fcc7293d458d8002f6a60 | Koi fish | com.IkanKoI.odieapps |
| 91bb8594e118338f38de22e96e89cc5e11d619da3ec3dc0ecada13720111a588 | House Terrace | com.TeRaSRumaH.odieapps |
| c41a8edaa85344e48a75843447358ea7a092fe1061bca79ac535abf467112eda | Skirt Design | com.DesainRokK.odieapps |
| 52d9df500ae7684d58c2bf65fb6852da1440e79b07a049f72585ccf8665e9d64 | Yoga Meditation | com.MeditasiYoga.odieapps |
| 21fce35139cfdf1145855987b6e3306adf26c3b60ba59b1c364a3d7d44bc5285 | Shoe rack | com.RaKSepatU.odieapps |
| 4739a7d1317fee0a7a885a00468d9749bb7da5c5f1696408deaa736fa2aab6e9 | Unique T-shirt | com.KaoSUniK.odieapps |
| bc49cec1896f7f4542ff8712da8475bf5e55abe7558918c260492467eb03ef6f | Mens Shoes | com.SepatuPriA.odieapps |
| 7345975ca29d16e3b55309e84f6249990878482ed55e597269fdd0cb77a290ff | TV RuanG TaMu | com.TVRuanGTaMu.odieapps |
| ecb04d5359949bfbbc64fd7bedd8fde3a5b9703784fea8d758a3a643117165b0 | Idea Glasses | com.IdeaKacamata.odieapps |
| a21f4e9536dcbcd810fbfcdff8f6cce5b6338f1d5df7ba45abd1a5f4ed8dca76 | Fashion Muslim | com.FashioNMusLiM.odieapps |
| 41386181f9e7dc8085d6a117607cd79346744d925e5d2ca67759742fbac47e51 | Bracelet | com.GelangTut.odieapps |
| fceda65ea8624af018c072c60ed5fcb8b6bb00832fb63559e819463d2ba9db4e | Clothing Drawing | com.BusanaMenggambar.odieapps |
| c5b24cf5d348a6fe3ad543f70379c7d9fa60a8e9bac03d6ea387fcdbcbbca932 | Minimalist Kitchen | com.DapuRMiniMaLis.odieapps |
| c36e7566e2e92898162006b9922d9d8f450867224b67d2346f70d7e76b1cbae6 | Nail Art | com.SeNiKuKu.odieapps |
| 0039f9b2faac6146bddc2831fdfa6a03327f77d3954a1a27ab66e6b0b5952a3a | Ice cream stick | com.StikEzKriM.odieapps |
| a8687cb35ee453958dc1757608505f3c5a7f137909f517acb7a850316d0e87b4 | Roof | com.AtapRumaH.odieapps |
| 7da49a0122444b2087a582d142c82375541544fd765f29b9b3f7728e598b54e0 | Children Clothes | com.BusanaAnaK.odieapps |
| 7312c5ba59f89350b13fe93107233a06c79a68eedff0eb082ef7a5f24bec76e2 | Home Ceiling | com.PlaFoNRumaH.odieapps |
| bf00efc96cf3ecdd3069afbbfae53aeb79910848721fe50d64410760790f1a27 | PoLa BaJu | com.PoLaBaJU.odieapps |
| 892f883d3588ee952888cccb4bb9bb33092f1be924d981e69595a758daca8c86 | Living room | com.RuanGTaMu.odieapps |
| 5a1693d255e5f487214fd1cd46c0cff8d5375903459c7f87ae17f636fa470e32 | Bookshelf | com.RakBuKu.odieapps |
| 906cd586d8f7388c1fbb0581b926aa4b2dc5534d460cc3ba011198d26a1dfe16 | Knitted Baby | com.RajutanBayI.odieapps |
| 96bd87c8bd8772b1f11b3e4771889b4d2d81739cd2ef7494a3ff54fc28e711f6 | Hair Paint | com.CaTRambuT.odieapps |
| 54380fa8c12f6333a22fd0c728e615e92470565e96c7b39ae2f1d7e30584fc31 | Wall Decoration | com.DekoraSiDinding.odieapps |
| b6671808dbc226c11697c54d000b6a30213478c141d96aa4c3d52fa5243cff16 | Painting Mahendi | com.MelukisMehndi.odieapps |
| 525c515e3e8c0d6007ab79f05a64c42951b440db4ab12f397218efa9692faa84 | Bodybuilder | com.Binaragawan.odieapps |
| 399058e95153600a471d94309a6c3e87f3851647fb003f6d4289fa5b5df389a4 | Couple shirts | com.KaosCouple.odieapps |
| 44066a23057ee93bed27737e8f444150c29c68b14bc9b21419f549188e436103 | Unique Graffiti | com.GrafitiUniK.odieapps |
| 1fcd61a10c170d259fca12e52d1930018adafad5613551b5bbb14987de1c7cfd | Paper flower | com.BungaKerTas.odieapps |
| 0b85488788f7f83e879f41591d674b50d4daafb60094918391d98f143ba54ddc | Night gown | com.BaJuTiDuR.odieapps |
| cb11dd259fa4fc0c1b4ee878cfb3c2df2a0a6ecab83276e33185ba7ce45c46ba | Wardrobe Ideas | com.IdeLeMaRi.odieapps |
| 4091c8acea954fffd22be4c0675c440cf1fe4620d6659b8d23d8d3a2fc815e20 | Dining table | com.MejaMakaN.odieapps |
| 9412ca41b7c9aebaeef05fe5c45bf5c5d998e5da44d5a7a495f5ba06c00feea0 | Gymnastics | com.LatiHaNSeNaM.odieapps |
| 761032267b9659cd04676fce55e602a87e43cb4c75c58fa61486cc73da0016c6 | Use Child | com.PakaiAnAnak.odieapps |
| 14bffba23e2bf4a61b4a54f1ef5027225290eab7f10d4c663570629e456cf51e | Window Design | com.DesainJenDeLa.odieapps |
| 5dca7151c50ce88102b1fc5c0dd984c57202ad7c67f25be231d64cf1d52da437 | Hijab StyLe | com.HijabStyLe.odieapps |
| 3350f4eb55c2f00c1ba0380044a1a6670a4eddc5cbabf903f2ad2e266eab58d2 | Wing Chun | com.TeknikWingChuni.xsadroid |
| c99a6e7e5d066076bacfad9142e3cf01855525782d638ccfe9ce7cd57d11ca5c | Fencing Technique | com.TeknikAnggar.xsadroid |












 Get updates from Unit 42
Get updates from Unit 42