Emotet and Trickbot are information stealers targeting Windows-based computers, and they are best known as banking malware. Each are typically distributed through separate distinct malicious spam (malspam) campaigns. However, we occasionally see both types of malware retrieved during a single infection chain. This Emotet+Trickbot combination doubles the danger for any vulnerable Windows host.
As 2018 progresses, Trickbot is still sent through its own malspam campaigns, but we continue to find examples of Trickbot using Emotet as an alternate distribution method. Most writeups about Emotet and Trickbot focus on individual malware characteristics, and they do little to paint a complete picture of a successful infection chain.
This blog post examines Emotet malspam so far in 2018, and we take a closer look at a Emotet infection traffic featuring Trickbot.
Similarities
Although Emotet and Trickbot are from different malware families, they have some similarities. Both are information stealers that can load additional modules for functions like spamming or worm-based propagation. And for the last year or so, both have been distributed through malspam using Microsoft Word documents as the initial infection vector.
Emotet
Emotet was first reported in the summer of 2014 as banking malware, but has since evolved. By 2017, various sources reported Emotet acting as a loader for other malware like Dridex. One source reported Emotet loading Trickbot, so this most recent combination is not without precedent.
In 2018, Emotet infection traffic usually revealed the IcedID banking Trojan or Zeus Panda Banker as the follow-up malware. In June 2018, I started posting examples of Emotet infection traffic with Trickbot as its follow-up malware. We have also seen spambot malware as the follow-up malware, where the infected Windows host sends out more Emotet malspam.
An Emotet infection currently starts with a malicious macro in a Word document. Macros are disabled by default in Microsoft Office. If a user ignores security warnings and enables macros macros on a vulnerable Windows host, the malicious Word document starts an infection chain. These macro are designed to retrieve Emotet malware from compromised servers to infect a victm's computer.
Malspam pushing Emotet uses one of the two standard methods to deliver the initial Word document:
- Victims retrieve the initial Word document from a link in the email .
- The Word document is directly attached to a recipient's email without any links.
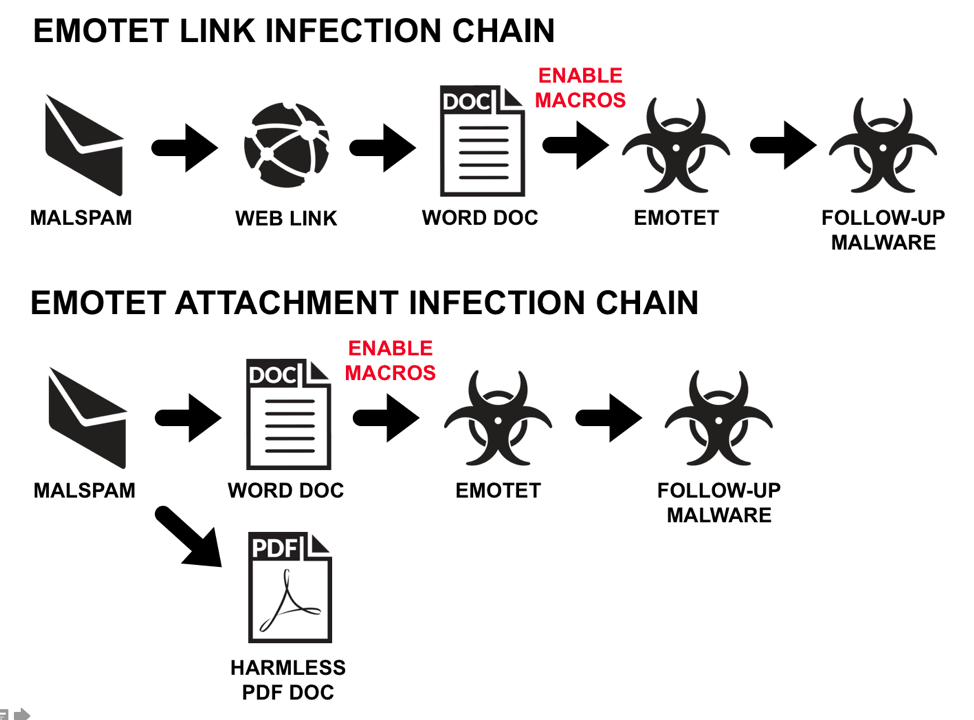
Figure 1: Emotet infection chains so far in 2018.
Trickbot
Trickbot first appeared in the fall of 2016 and was initially described as the successor to Dyreza, another credential stealer. Trickbot is a modular malware with additional functions like an email spammer. Its most notable function is lateral movement. By July 2017, Trickbot added an SMB-based worm propagation module, but had not yet included an exploit.
Since June 2018, I have posted examples of Trickbot infection traffic with SMB propagation on malware-traffic-analysis.net, showing Trickbot moving from an infected Windows client to a vulnerable Active Directory (AD) domain controller. Trickbot's lateral movement over SMB is distinctly different than WannaCry's implementation of EternalBlue noted in 2017, so this method of SMB propagation appears to be based on a different exploit developed by Trickbot authors.
Trickbot normally has its own malspam-based distribution channel, but now Trickbot attackers are also using Emotet for their infections.
Emotet Distribution
On the week starting Monday, June 11th 2018, we saw a great deal of IRS-themed malspam pushing Emotet to recipients in the United States. IRS was not the only theme, but it was by far the most prominent. In the days leading up to July 4th 2018, we also saw Independence Day-themed malspam pushing Emotet to recipients in the United States.
The following are some examples of spoofed senders and subject lines we have seen for recent malspam pushing Emotet since June 11th, 2018.
Spoofed senders:
- From: [various spoofed sender names and email addresses]
- From: Internal Revenue Service <[spoofed email address]>
- From: Internal Revenue Service Online <[spoofed email address]>
- From: Internal Revenue Service Online Center <[spoofed email address]>
- From: IRS <[spoofed email address]>
- From: IRS <irsonline@treasury.gov> <[spoofed email address]>
- From: IRS <Press@treasury.gov> <[spoofed email address]>
- From: IRS <Transcript@treasury.gov> <[spoofed email address]>
- From: IRS Online Center <[spoofed email address]>
- From: IRS.gov <[spoofed email address]>
- From: Intuit <[spoofed email address]>
- From: Intuit Online Payroll Support Team <[spoofed email address]>
- From: Intuit Payroll <[spoofed email address]>
- From: Intuit Payroll Services <[spoofed email address]>
Subject lines:
- Subject: 4th of July congratulation
- Subject: 4th of July eCard
- Subject: 4th of July Greeting eCard
- Subject: Happy 4th of July Greeting Message
- Subject: Record of Account Transcript from June 14, 2018
- Subject: Tax Account Transcript from June 14, 2018
- Subject: The Fourth of July wishes
- Subject: Verification of Non-filing Letter
- Subject: Verification of Non-filing Letter from 06/15/2018
- Subject: Wage and Income Transcript
- Subject: 0335363294
- Subject: 2142 Payroll Summary
- Subject: 3291 Payroll Summary
- Subject: ACCOUNT#94895547-Milan Marsic
- Subject: Engr. Abdul Rauf Invoice 8288592
- Subject: Invoice 897614 from Patrick Bingham
- Subject: Invoices Overdue
- Subject: IRS Record of Account Transcript
- Subject: IRS Record of Account Transcript from 06/14/2018
- Subject: IRS Record of Account Transcript from 06/15/2018
- Subject: IRS Record of Account Transcript from June 14, 2018
- Subject: IRS Record of Account Transcript from June 15, 2018
- Subject: IRS Tax Return Transcript from 06/12/2018
- Subject: IRS Tax Return Transcript from June 11, 2018
- Subject: IRS Tax Account Transcript
- Subject: IRS Tax Account Transcript from 06/15/2018
- Subject: IRS Tax Account Transcript from June 15, 2018
- Subject: IRS Tax Return Transcript
- Subject: IRS Verification of Non-filing Letter
- Subject: IRS Verification of Non-filing Letter from 06/11/2018
- Subject: IRS Verification of Non-filing Letter from 06/12/2018
- Subject: IRS Verification of Non-filing Letter from June 11, 2018
- Subject: IRS Verification of Non-filing Letter from June 14, 2018
- Subject: IRS Wage and Income Transcript
- Subject: IRS Wage and Income Transcript from 06/14/2018
- Subject: IRS Wage and Income Transcript from June 11, 2018
- Subject: IRS Wage and Income Transcript from June 15, 2018
- Subject: New Invoice / WM2708 / RP# 09648
- Subject: New Payroll Co.
- Subject: NYPXV7-16497063849
- Subject: Pay Invoice
- Subject: Payment
- Subject: Payroll Tax Payment
- Subject: Scott Crowe The 4th of July Greeting eCard
Each of these emails has had either an attached Word document or a link to download the Word document.
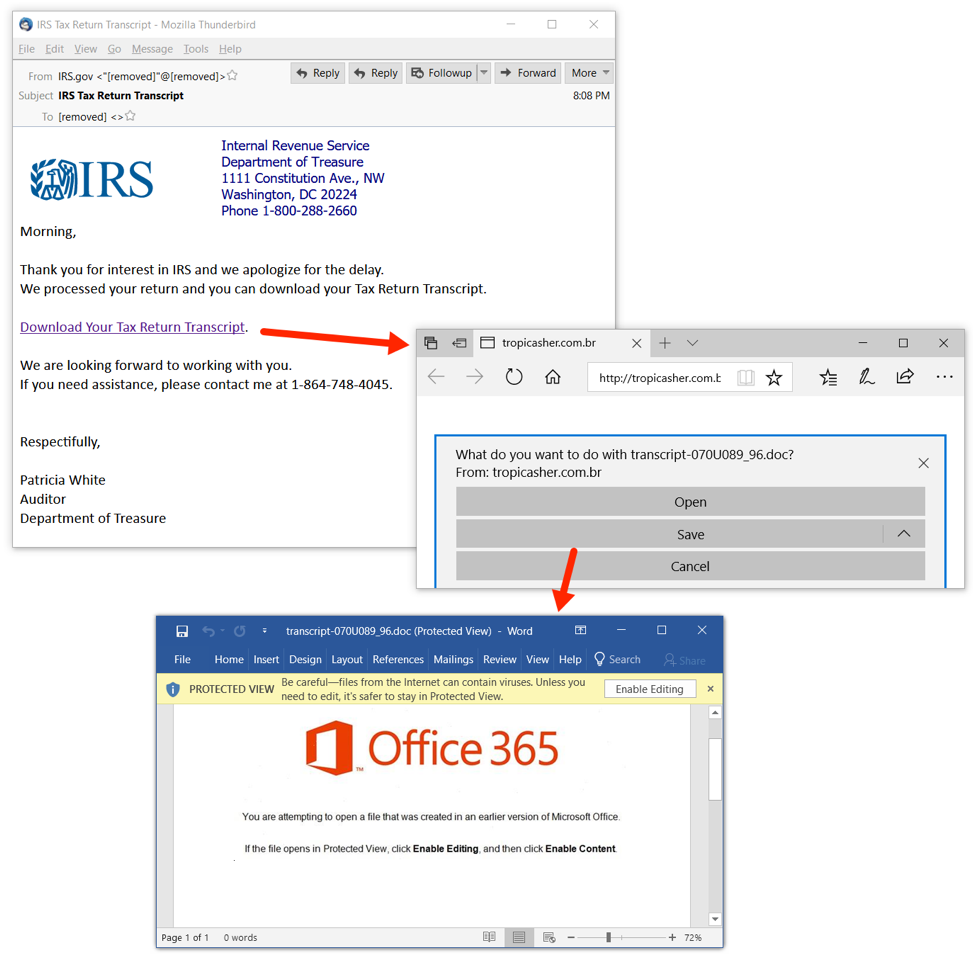
Figure 2: Emotet Word document distributed through a link in the malspam.
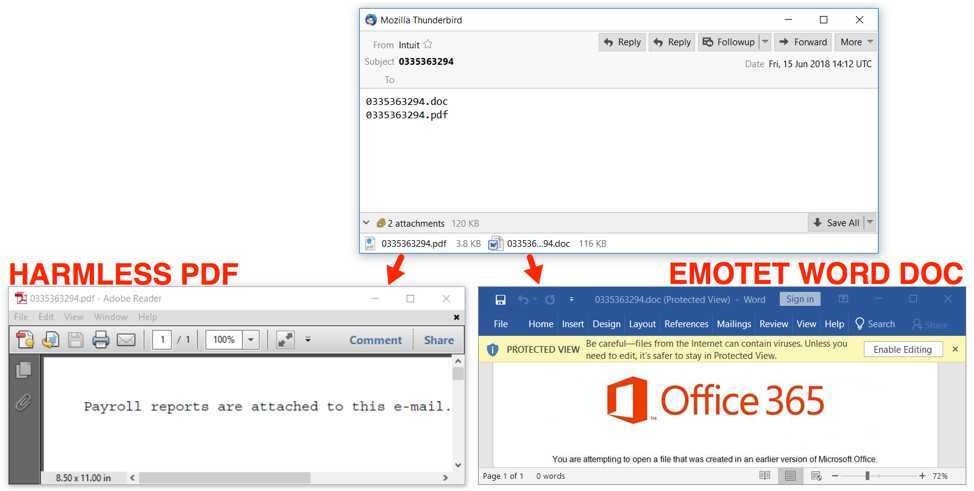
Figure 3: Emotet Word document distributed as an attached file.
Emotet Levels Jump Drastically Starting in May 2018
Autofocus shows an increasing trend in Emotet malspam during the past year, with a very sharp jump in Emotet Word documents beginning in May 2018. Below are graphs for verified hits on Emotet from links or as attachments. Link hits are the number of times we verified requests for URLs to download an Emotet Word document. Attachment hits are the number of emails seen with an Emotet Word document attached to the message.
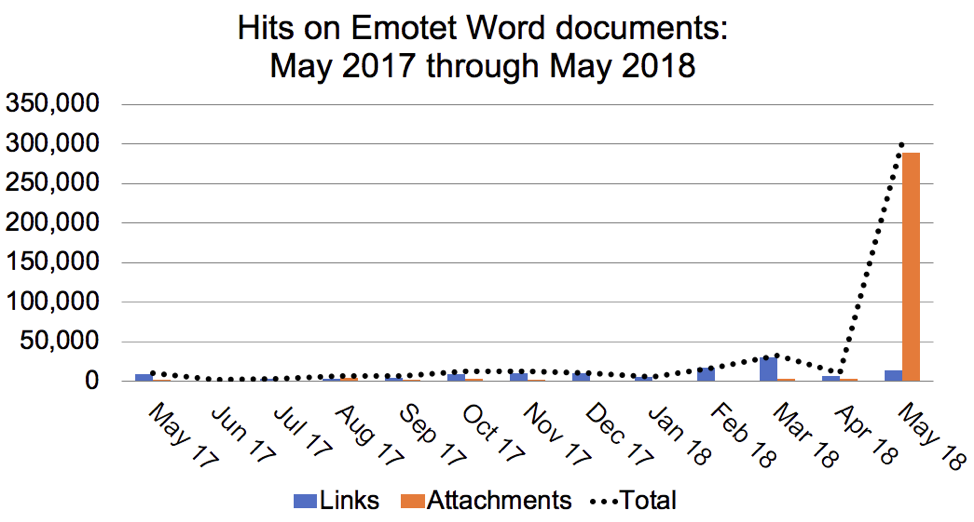
Figure 4: Hits for Emotet Word documents from May 2017 through May 2018.
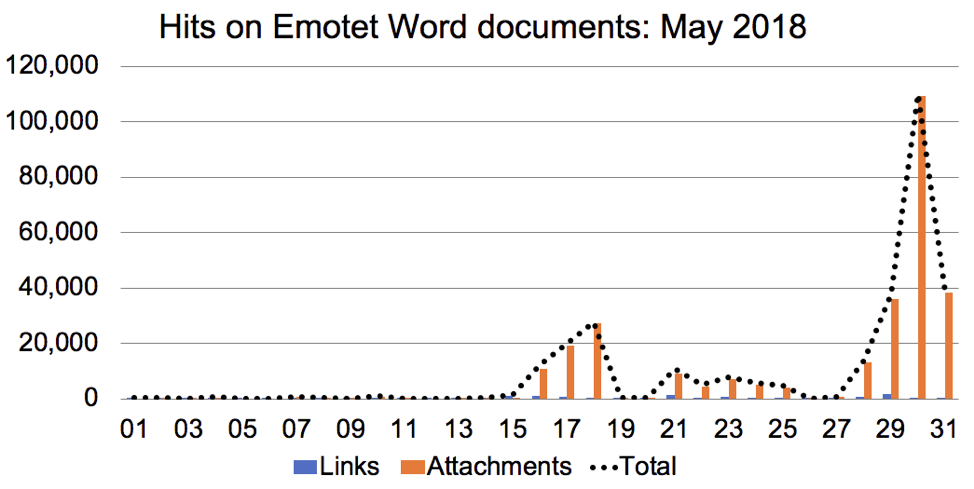
Figure 5: Hits for Emotet Word documents in May 2018.
Emotet Infection in an Active Directory Environment
My blog post from malware-traffic-analysis.net on June 15th 2018 provides an example of infection traffic from Emotet malspam. This analysis was done in an Active Directory (AD) environment with a domain controller running an unpatched version Windows Server 2008 R2. The Windows client was running an unpatched version of Windows Professional 7 Service Pack 1.
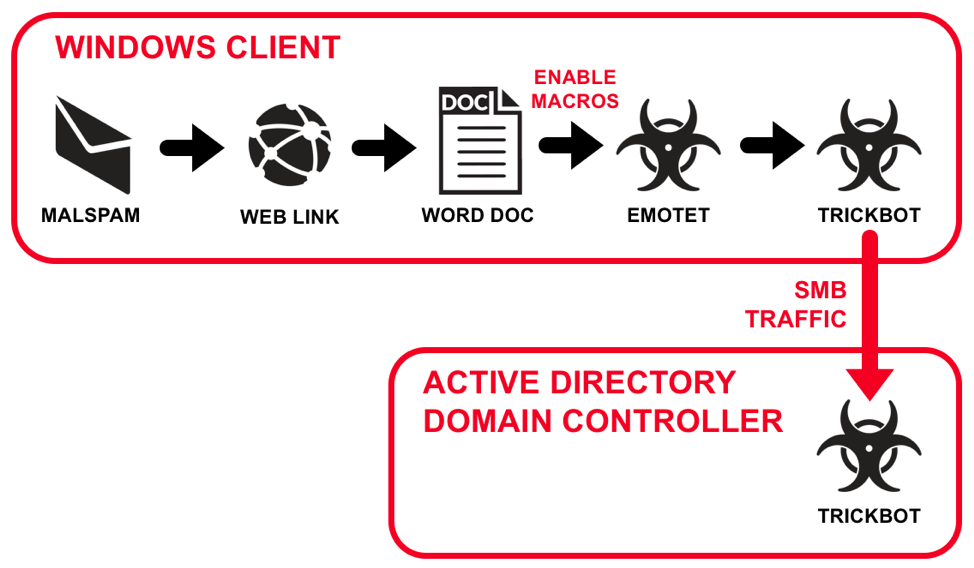
Figure 6: A successful Emotet + Trickbot infection chain in an AD environment.
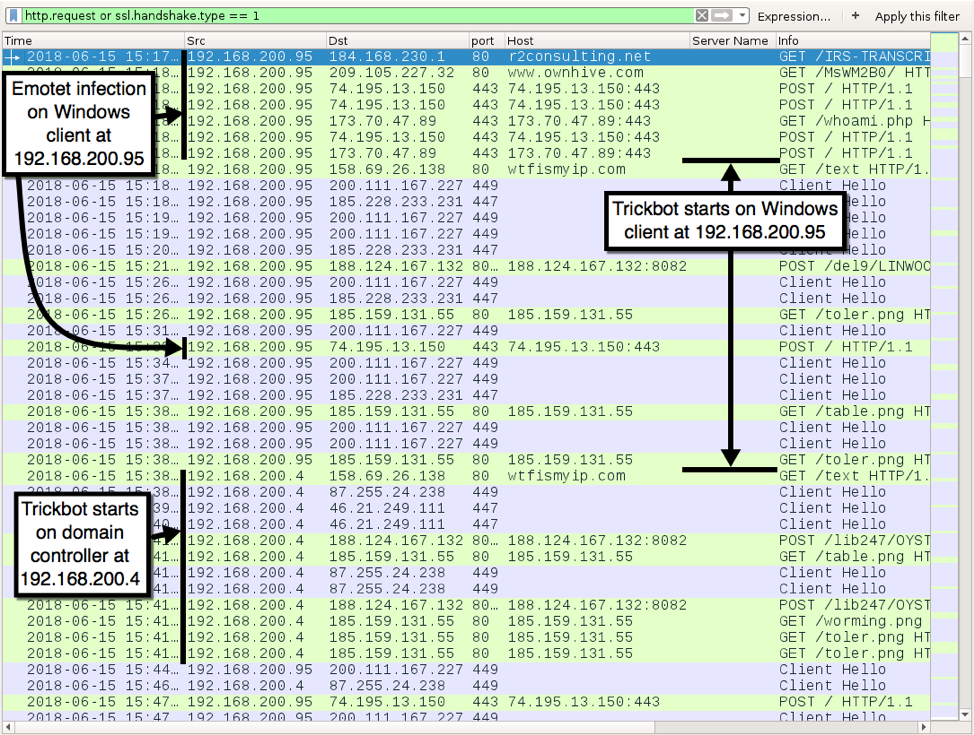
Figure 7: Traffic from the infection filtered in Wireshark.
Figure 7 shows the initial infection traffic from Emotet on a Windows client at 192.168.200.95, followed by Trickbot infection traffic on the same host.
Trickbot propagated from the Windows client to the vulnerable domain controller on 192.168.200.4 via SMB. Approximately 20 minutes later, the vulnerable AD domain controller shows signs of a Trickbot infection.
Figure 8 shows traffic where Trickbot was sent to the domain controller at 192.168.200.4.
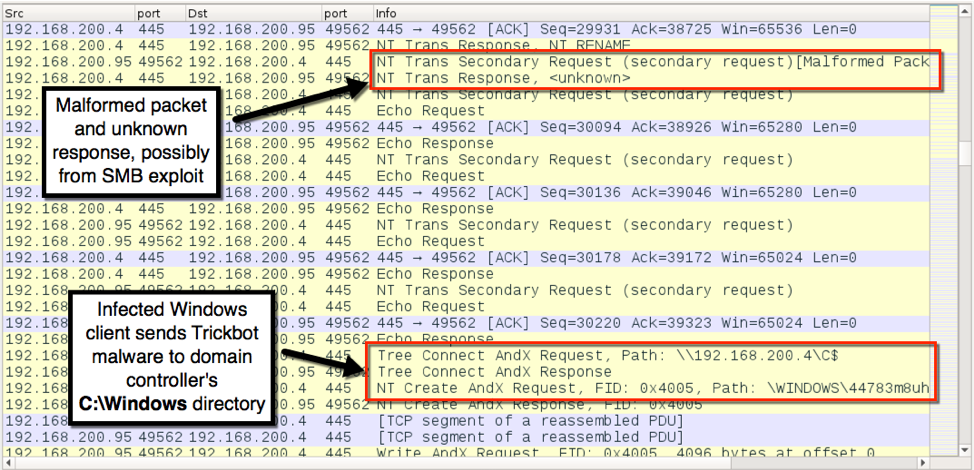
Figure 8: SMB traffic in Wireshark where Trickbot was sent to the domain controller.
Conclusion
This activity combines the increasing amount of mass distribution for Emotet with the lateral movement capabilities of Trickbot. An Emotet+Trickbot combination represents a more potent infection, and it doubles the danger for any vulnerable Windows host.
Organizations with decent spam filtering, proper system administration, and up-to-date Windows hosts have a much lower risk of infection. Palo Alto Networks customers are further protected from this threat. Our threat prevention platform detects both Emotet and Trickbot malware. AutoFocus users can track this activity using the Emotet and Trickbot tags.
We will continue to investigate this activity for applicable indicators to further inform the community and enhance our threat prevention platform.
Appendix A
Hits for Emotet Word documents from May 2017 through May 2018:
Month/Year: Links - Attachments - Total
- May 2017: 8,423 - 1,421 - 9,844
- Jun 2017: 1,154 - 173 - 1,327
- Jul 2017: 2,868 - 390 - 3,258
- Aug 2017: 3,273 - 3,803 - 7,076
- Sep 2017: 4,650 - 2,211 - 6,861
- Oct 2017: 9,289 - 3,407 - 12,696
- Nov 2017: 10,676 - 1,737 - 12,413
- Dec 2017: 10,499 - 217 - 10,716
- Jan 2018: 5,287 - 2 - 5,289
- Feb 2018: 16,637 - 265 - 16,902
- Mar 2018: 29,801 - 2,680 - 32,481
- Apr 2018: 6,138 - 3,533 - 9,671
- May 2018: 13,150 - 289,308 - 302,458
Appendix B
Hits for Emotet Word documents in May 2018:
Date: Links - Attachments - Total
- 2018-05-01: 383 - 0 - 383
- 2018-05-02: 45 - 437 - 482
- 2018-05-03: 43 - 150 - 193
- 2018-05-04: 41 - 604 - 645
- 2018-05-05: 38 - 0 - 38
- 2018-05-06: 36 - 0 - 36
- 2018-05-07: 218 - 711 - 929
- 2018-05-08: 476 - 9 - 485
- 2018-05-09: 65 - 1 - 66
- 2018-05-10: 155 - 957 - 1,112
- 2018-05-11: 47 - 25 - 72
- 2018-05-12: 26 - 0 - 26
- 2018-05-13: 45 - 5 - 50
- 2018-05-14: 350 - 19 - 369
- 2018-05-15: 1,274 - 325 - 1,599
- 2018-05-16: 1,119 - 10,929 - 12,048
- 2018-05-17: 746 - 19,311 - 20,057
- 2018-05-18: 386 - 27,437 - 27,823
- 2018-05-19: 61 - 270 - 331
- 2018-05-20: 60 - 234 - 294
- 2018-05-21: 1,632 - 9,098 - 10,730
- 2018-05-22: 381 - 4,656 - 5,037
- 2018-05-23: 920 - 7,050 - 7,970
- 2018-05-24: 536 - 5,169 - 5,705
- 2018-05-25: 481 - 4,206 - 4,687
- 2018-05-26: 78 - 134 - 212
- 2018-05-27: 171 - 743 - 914
- 2018-05-28: 734 - 13,105 - 13,839
- 2018-05-29: 1,678 - 35,909 - 37,587
- 2018-05-30: 566 - 109,409 - 109,975
- 2018-05-31: 359 - 38,405 - 38,764
- Totals: 13,150 - 289,308 - 302,458












 Get updates from Unit 42
Get updates from Unit 42