This post is also available in: 日本語 (Japanese)
Today we identified a new tool actively being used by the Locky ransomware family to evade detection and potentially infect endpoints. Unit 42 identified slight changes in Locky detonations through the AutoFocus threat intelligence service, correlating global data to discover a new tool being used to pack multiple ransomware families. Adversaries are constantly seeking new techniques to bypass security controls, and based on data from AutoFocus, this represents a widespread update to their tradecraft.
In our analysis, multiple malware samples stood out due to what seemed like obfuscated API calls coming from a dictionary of embedded terms to resolve system functions and hide their true capabilities from commonly used static analysis tools.
(Oddly named variables passed to API calls)
Tampering with the API calls takes away the ability to classify based on key names, thus increasing the likelihood that the malware will go undetected. This, however, is where it gets interesting, as it appears this was just the first in a series of misdirections designed to throw off analysts.
When looking at the new samples, the import tables for libraries to load on execution would differ significantly and not actually be used at all during execution. This prevented any sort of meaningful detection by import hashing. Additionally, looking at the executable version information showed varying information per sample but a clear pattern that can be used for future identification.
| LegalCopyright | Copyright \xa9 2017 |
| InternalName | Phoneticist |
| FileVersion | 218, 158, 104, 112 |
| CompanyName | Cyber Power Systems Inc. |
| ProductName | Nesting Punk |
| ProductVersion | 221, 202, 46, 180 |
| FileDescription | Skittles |
| LegalCopyright | Copyright \xa9 2015 |
| InternalName | Grated |
| FileVersion | 82, 233, 256, 103 |
| CompanyName | SafeNet Inc. |
| ProductName | Geomagnetic Espadrilles |
| ProductVersion | 176, 194, 91, 229 |
| FileDescription | Connectivity |
Within each sample of malware we found different embedded strings, some used and some unused.
(Word list)
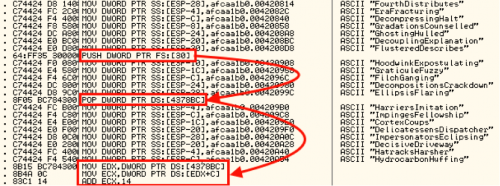
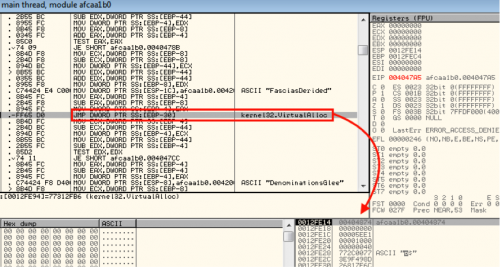
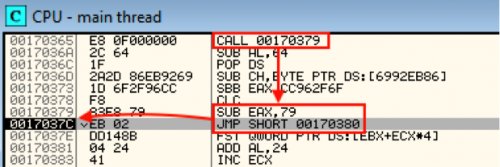
Upon closer inspection, it appears that the author uses a lot of the terms to generate noise and pointless instructions in an attempt to make analysis more difficult. In the below picture, highlighted in red, is where this sample begins to get serious about unpacking and walks the PEB structure to identify the base address of kernel32.dll.
(Start of the PEB walk)
On every run, it advances forward one DWORD and eventually compares a value that is XOR’d against 0x958B9963 to see if it’s found kernel32.dll.
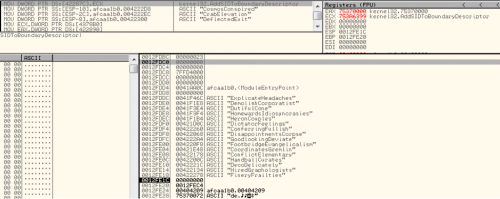
(Upon finding the intended target DLL it saves it into a register)
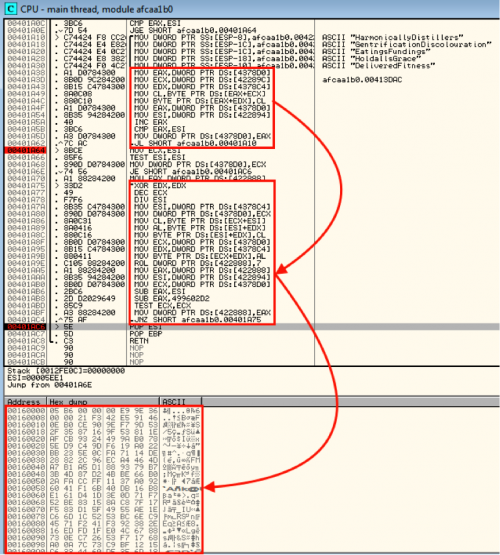
Now that it has the base address for kernel32.dll, it begins to enumerate functions, continually changing the variables on the stack during this process to further misdirect their intentions.
(Function iteration)
(Finding the target)
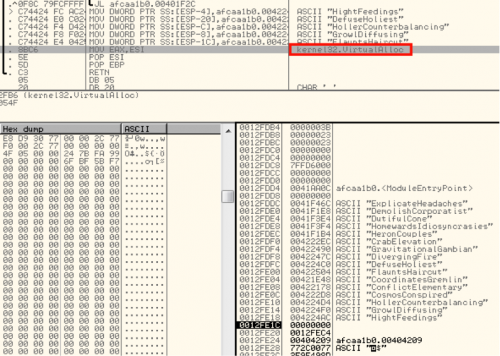
Once it identifies the location of the VirtualAlloc function within kernel32, it begins to position the necessary variables to call on the stack while continuing to try and hide within the noise. As shown below, once the stack is setup, it does a direct JMP to VirtualAlloc, providing a return address that eventually leads to a couple of decoding routines.
(JMP to VirtualAlloc to allocate space for the encoded data)
(Decoding data into allocated space)
Once finished with this phase, the malware shifts execution into the newly decoded data and continues to modify itself through multiple iterations.
(Self-modifying its code at run-time)
Recall from the beginning of this post that abnormal arguments passed to API calls were the first clue something had changed. In this phase, you can follow the self-modification to the next set of red herrings before it gets down to business again.
(Code continues to JMP to new offsets, modifying all subsequent instructions)
(JMP after JMP, with one actual instruction hidden deep within)
This will eventually lead to a call for LoadLibraryA with bogus names that do not map, which end-up failing and return a NULL result effectively serving no purpose but to confuse.
![]()
(More red herrings)
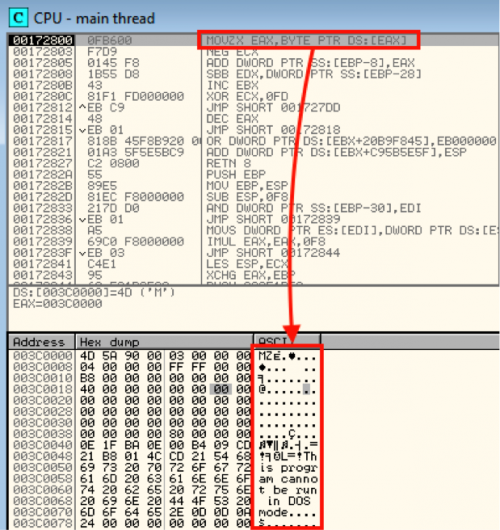
Once this all completes, it will allocate another region of memory and then copy over and decode the actual malware, similar to the above process.
(The final payload of the packer)
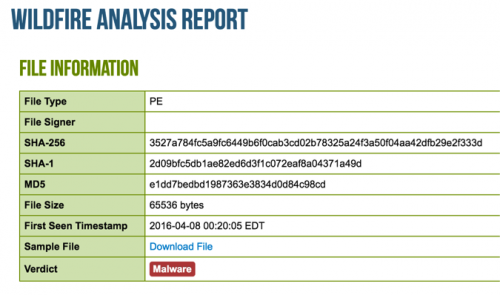
When we extract the payload, we can validate that it is indeed Locky and accurately gets detected.
Palo Alto Networks has identified this technique being picked up recently by the Locky ransomware, but we have also identified samples of TeslaCrypt and Andromeda malware families, dating back to March 14, 2016, that exhibit the technique. It is important to note that this obfuscation can be detected by dynamic analysis, which is used in combination with static analysis by WildFire service to protect Palo Alto Networks customers from this threat.
WildFire is able to detect this new packing technique being utilized across the malware families described in this post, as well as detect each family after unpacking. Users of AutoFocus can find more information on impacted malware families with the Locky, TeslaCrypt and Andromeda tags.
We observe Locky exhibiting this technique:
4b9a525a80cdba0d827b52d1e19c0b74e055b9afacfa2910dd32230826f91a7a
7fe3c82165fa2fad745c337325eaa99bbbc1ca7b89479a52d64af7813b47e1e4
d958c6f0a5208a6040e06ab71decbed47f3ac7e8235a13c918a0b68eb5ae5748
6715765a36d6e6cb6f2e8b159e21d914aa0bdf433f2ece3032535e9ea0382f80
38774f2381c0d62b522604e66d42d4b320b6a10a229f25c129e96ad6d62c57c1
afcaa1b0e7864a3e471b5d6ffb66816d2def62c363aa0d8a23cdf96684d4960d
5d29dbf3f854457b71a502d4487d620986924582f5c8997ef9f55c6ba038b6b5
64d51aaf4abe4e87013056277277f05c55c6554d2a7005374f254983ac846c4d
127c4c0437af192ad9b216b7dc3daf7b8b20e04f39559487ff5bf6d29e7b624d
24e330f05b3fd86761969037cfd384a044b81c05bd3626b2d74dbacb2d18972b
00fba93cee17df9d76475c4a07ecbc4663917990d5175284f4ec9fd5e9de9314
94cfc072d57250f5da4409682bab75f655ac70bf384885b008b785357e0cc256
85e22edb58902c1c087103f1be083f3fbdd1f6b2737efb32b229c92eb1fbf30f
a83824d43c04893a3c0563f4bc8ca9adde5ad2d4f8b9eddd7e8521f3c36be0e0
c7d9b7e3cc672d0bb588d247b5860527d8e48eb0ae642ab4454ff12cb921d8e3
9fec0efb432f7ab3dc68c2e9913492d5e640084eb2e94226837a896dc1a3ea8e
We observe TeslaCrypt exhibiting this technique:
9651d0cbca5c0affc47229c33be182b67e7bfbc09d08fd2d1c3eb2185bb29cdf
9fff99c289db327d2ed6b65c199c3424f85b013ecb9826a47f368841386f1f42
8b30a779db7a22a48ec923c2e0f2277be777ebb196487d15872e2df4a3742fda
e08fec9f5a41f47c66531755a6f229b1066d475abf3f36d87f8901358b475c26
d7cacf0b6c8ed4f0dfb0666e9fb7cc0bfe44da540db0ac613b920229681d2d9a
b00ce6a6107f0ace12878c3636fd42494bc387ba494f87c094c3597eb1dd4943
ae006b6c9d03e3e5ee0a98cf82fa517ac361f04d66ebf98029e12569e1f467be
e12617985ebb160e6e6e02ecaad83adfda37df66722002f63fd0804f45f7ff09
c2d4f240122354a6db5edc428dba1b6d6540dc10818d5561128690d57388c508
84b5d49183870ec8adaea182bdcb857e503720a4e656ad580397ec98bc7bc6cf
af5bc5a9d2dc6f0c5e6321a7b760867d7c52f6701212e1ac0ad667dd5bee94b3
bb002ddcc4ef252d0d9457f5e91589933ee99ee9142656a8b37e02be7b90742f
ad6bfc0b940aa142ec925b54ff3feabbfab60751034a102f8a7a5ee84f5eda51
bbd8a4b1d60547638c67c325a3ce1b449758146c3e3a49731c3ddaf8f987c0d3
8ca7583fc45500e4f02955022350c9b64c1ce774eeca2d7684fe0118d2f469ff
99a3457f10de4b4e33fd65ec341e0f4cc543a1c076c2f3eefca8d41ef56c93b7
83427ffa553f49bb627045c609b5d4e505f7129616cccce9958f61c084985676
961ac867a29c0afe193aedc279d95a08872e524e8ac1b6d62f83644ba1db5692
8d342e16a1ab0b33c666e86b03f9580f25be2eb1067d590a8c21545f9e5247a7
b76dde85793d4f8ea23957f9cf9fac790c18968429aab3a9024cefcead7db309
b3f8a863a7ab9d14510e83424a1a4b8ace18d7e0997102ed6731880aad9859bf
a70a192bbe3fd9126b138d16bb70ee2f941756be8b695f450355e1fa1aaa05aa
7f862e66f96764eff67d06ee7edfb086e5c871720681c5d7caed7df2c9734f8c
d9934d3cf498e08fe39bfb070545b010b1888f85716db9aca7f5b20134a7437a
a677620dfe3676d80cbb655e5a28eab477256a1023418c225002e6cd2e886e3f
8e8ce12b7d5efd2315ea11516d17f503772d306b106713a505d7bdfc658ff564
8f53da2f01194680b7ec2fa848b7e3d438f4bf1d3cef72e6b4094b00a1a877cc
9b0939fa4c00061cb9588ae8d30679fe92d46e38f48af6c7bad1317c5e93d2e0
8537361d63e80f5479ad8e36c61c2f8dc798eff9bc364ef4f4e74bee035f1820
8f8a91dc0b525da0aa81ceda682aaf4580300f3c2fb63da545646a1c2f088bf1
e0449abe02aa3ec49f98e900685d0bab920fdab5012588a7892f4b992fa86b28
b27336bf97cc72499336ba3c5f0ba8134d6aeb95225a17342379bea74e9dc758
b3fe8b423dfb28b0b505259efc28e567c4b2adeae550d0fd214dbf4368806f1a
db0654584870e3c7e701cd8a35b8267728db0dacaa9c411cf18e335ae062196e
7d7f02a051696bc706cc9b07b115a11c89093ccb22a37fc27b825486e7ff0a0d
97c6d884eb61dba0f0798464351d69ce24b528b24f68e668e81af52582a9a0ab
af20e170ae290df4f0b34909c51d18e0ea1ce6fea47adb29d858df42d4d50750
86ed651308c6c04d4ad2b2eecae31637a70f0d9b6d2fb04726f3bd07fbc5ad4a
7aed6b832bb58adebeb560ce532840edfeee65d8e18c1a0be61b264cf74c1e47
93d16b2b5a3fefa578ffec2f2bd2e3b818702b0988a6bd14050e485fcef5cf06
a670f6fc15074e1fd79b26fee28d48eebce25fe6608b00dc23e1386dacca9442
ab035382f8dfe6fc13374d1e9cc92ebf3d44e32e1d757485568545f92dae5005
d70c74726a8ab6c4dd2ee530795267a409f0504ed1384537241f5bc0fd77d65d
ac4b81c115787ea2724a48a6ccd36ea11f62336fe4cac01d7b8e6dd05c318b69
cba3f4d1b73b5be52a4a79de875b1fda7d6cb58c0b6782f9a03e0562940eab7d
ad970a3a893b5b67f4b805606bb3ea04f0552e2cda6adaa38a4ebfa323a67838
add5534feeee9fdeb962d2bf55baddda8854d9e3b43103cc2007d6a75860774a
dd2998e204f7179c550728c77ed05290bde36dd897d851ce323b6b84800bfe80
c0f1da5ef339a0f47734704ea77611a43232fad5819ae9dab04178380e38aec3
7fa1ed71fda8accb83ca520957c985019b7e43947b4bee47c8d71a826cd50035
bdf819317a9e7fe8d5c1b337625230391a91f30449979b9b786f43f5c840d485
52ddbadeb560819500f031406ed629ea53f7ccdb0feccb43968fa3be668c45a1
58dabaefe317881362df1e13d190505285c38a0e2fe353d2784defde4c709f92
75336c9de17b7444ac5220360b5a0766d3898d81eb77ba01cd2bbef95975797b
0712e38624f0cf75f79245326108b754efbc318545ef8e1c685b3306369d2384
70a443f84aae5e88824df72d39f797b7aa5ba00aa82940f16c23d1b5bcee5cce
356b11753cde7d628406f61580bc823300bc4b954eb79c0766224bd4b8dad05f
2d44dd2dd4d4d5ef835ce8a1cde4a45ab39119196a6fe26ab4c9ee8a3b790228
1dcdc62763c4d77f8ea9d64eca310fceb74194efb8700b365028862b44d7e8df
76a3883da15069287c8972099fc922477e41f3160599eb86de4ad9377a3f43ed
3af0c37ab942960fc642665e36644a5cc0ac2d0e779172bc1d5233cb3ecff710
3efd082e3aed3a42d7a16825201153928787cfd6438e7a5f5ecddc9c15efdaf1
288a00387f76046c1598f21bb54dcfbc6a499499f4117c39e7645c54d350c130
25e233b41022d6fa9a3fcb5c723229065a499ea77a4f4eb6e33d185b131e27d0
6345af00608caadb29b82ed03674a6e889a3c33e6b76e1434052ca5e65e64c7d
42ab4fdff74592bf0097efda55b0f0529d6579dd8c83e9fb79d81dd8f4d76376
01c814fa5b67317b083e87c0e94bfb78333d4841f24d3d95ecb992700542b87f
794b32f5d08cf7f7e9faff39707c0652f35a5cf1992135e8930863d9bcac4f0f
464e8d4903536ea7f99c7bf8ddabf3ffe568e11e490dbd773c4fae5e552fd311
3d4c955e9a5d2aafbb359b5ebefa8173f73862600809204a969bc4b1b30fe27d
05cc2952f76d3d273ed3eb97dcd537c82cc1afdec44817712cd088a40bbe7003
6400a149d316df356f9d1ad490e69f3d6eacadfa4b835ea180b50b5a9023a267
58b50c39b70c9b55aa6ac34a548f9c076034e75ff08885e2cb44cc1a1a7187de
416c5e3cc4771a78317249eb8745dcf16081d9126c5f6b7a4ebf750f512c64b7
100049de5895a7f96204f86aaae14d5f271d8e4c3cd918a51efe30103f33e7b2
0a1f05a1aa720ad600aedc0cbc0c19f662159075447c188c2642f5b64f63da7f
79cb69fef2f0ef73f26e4cfcbb3f959f0f85f6a1de52d2c3202cbe00aea75d41
500a371e28cc97fa29e649a082c8eae7a64cedee8b17505a088977dbf9dce68e
3c573e5994285957e8d12376b7187173945a6395b2bc59197492c70a2e3382e2
61ee0172985612fb1e85c6707671cda79dacb982cf4a15851b6c655f5799b884
783e77cca5a20da0285c472d334b3da47995c2c838f67eacb220491e6459b0cd
1d975e692a7596e37ce5ef812b420fd6915f2461fec7f460413e018e4cd3a03c
37b154bb5dc1aeda58972fef4380da2f0d63c8c358cb4e2b36f9f177dc0afc4f
620be6db60593855d9a190b3a05e6d4d3103879b0d3eee75056dfec1d169ddbf
34275d0fb73575447c5016a519ccf0bed9ca292ab4a2f1908226521d0594a139
69b7b58065ea977e66c9adf161a7c70d35533d97e9d8c6ea5957e01869077402
5e03297fea99d6d397a1298724e49aa0390e3c0686be5028ca5c923a66d12b20
415e27f3b6e4cd02a77d656a852c8de9a1dc911f5b1c51e0c2d50c356832838f
6f90dd4223c979615f55b7a6a6c88370052b96cc4309cde2048a00d8fab60b17
50978d98135917773ba1117bff918ac66a30a4dce742c645dbd68c1b8f02a281
001261336f0190c366f05cc20a5c01062d5f25cddf98019e0674c28b86c4227e
357a241a37ee9578174872084a3a3a25ca03074878986d55617ae9ba216e2a39
3a892a2b223e90cc9017c5245e0a7b32c902056ab5f1ffc1ac5fc18f788a35cd
68fd79b623b1dec65ad10691ac8cb4877c000faa022de809c48f5a419d1eff6e
0255f33108708f136034ca2fce1496cf37b3d9ebf4bda9a7c00ceb44a6c1955f
4aca6fa3401813f88d9111079a0d81af128093c12b8519e3fd4def47a81d4710
77ce4ba2a605e22b8699eef874d075fb585d259ed6cade2e503e6dbf58020aa0
65a92ba86259e051cbb721ff5b13cd89cc9b76845f531180afe2feb416635cd1
4ba6b18edc0099936dbfc444fd2b089271a398bf03d78372456ac7f631ccee36
6d4be5072e052e4c4aa1b59da379a8e4e01fe166d5ce6084cf86448bfe2370d0
2a9e9e279b6bae67efe101614cbf7ca00b10cd2ad1f713c07b393861bdb9a3f1
3f2eb88bc86235f47470cf741f0adef5016492e99956ec87b5ab2896e0dd5ca2
4132ab07b9273a1ed5d4ca979500e7cb541c33029775f7be795f94f43980e5ea
78741b5bbe94903ce22a9db5fb578fd3af4f2cad48142480a1354d156943a4fd
0ed6bbbb6f372723be1ed38e2bacd8f7d81a96b71d11ba0f46071c14e628016b
4630cb47542259b71e006560ce9a88244b1be6256ee1f2f4767e1e1e47618430
5dd1c647b4cbe9700809bfd35ae4537573659324c8f1ace006b4fac481e16148
213661084774b4352fcd644617462bf7c0ccf21838e15dd081b3cf0cfbb11144
0914e974e20c187a43807e91b95621e5ad0c14c54f6958546a60d84c0c777d29
We observe Andromeda exhibiting this technique:
9b84c2ef77b3c645bb643ee79de02a8a77eb81d79874cd6606edccd56314235b
a87c12714badd54395e075d3c695397044a8a4aee740dd4f9657df524803b1ed
b193f37721919e75e617173962e47153c05e303598e637764c837b3ac0a710d8
c9a81f89d566683e540914df1cb1541ae69ed734f3d0c7e7ba81c0ad9de947f6
88e661f55cbd241fce827df7de9c6eb5bd36bfb6dfe25a49dc0c88de167c0c8e
cfd76af3f5df83b3b94bced9644f85b8496a6dd58227c4af24632e184cd814d2
e2b36fc0e35c27723fdf623916368101af37543d63c6bcf0de737cec24d1e2e6
b855a01cfce787a505cdd5785c4f511ea7fbc1fb6a9e27d60677cc033e505de3
db5db710abf26674254383cdb7c4fc7c1308418b667341bf4a439541db71b427
d5dfc305cf41d744d21aeb8432d286aa9288a26563f358306602cf809863d92c
8ba8132621d462feb6f649a8f24506570c604acb5f5d607b7f6a675475db4f06
bebc5dd62e0680b1f56a6b4e41231857da2842ace224bf88cc1c5365538a8fa9
14f805e9f8ebd2b81ee4ee3c6a2e4b960039d8d99d13cf87d0da692947a02c91
20928d79dccb0338a113529cc1652892e79f560b98b52909ec2037a6088a7fdf
3fc9253bb1deac49b9889fb9cd1a90238239bd4e2db4d693ab99f29d08f029d3
678f2a8b9bfa585f42429ed452f2a9c39266fc10f5bdc4decd0bdc2613601c8f
78deed3fc6ccfa8bc6116c02d763a22a76e80bbfdce263158c366945d73af1c2
5392b97ef98462d31e1c07bc064dafac254f246ebb7131e364a9ec82b5b48b20
0594deb0b33ebb816fb27d4f0bf4d3ee7fce2146489cc152bd0894226840ef0c
2bec223894f14670c737b1f7ab766790cc9bf7490354d1e17ffb7e9defcaeb3a
33669080a8e8ae2ba43fd13887d3ee5cd9d686187c7d3ba82eb1da2b538fd63f
7a82a933650600bab70a85ff329a52329f5fadf64c05a86d1122298e1aaa9081
74bbceabb3ec583f7b92d55d0556aa1d0c0f302485649045bd2667b4959f62cc











 Get updates from Unit 42
Get updates from Unit 42