Executive Summary
Security professionals occasionally use Wireshark to review packet captures (pcaps) of malware-generated network traffic. To more efficiently review this type of activity, we suggest users customize their Wireshark installation.
In our previous tutorial, we customized Wireshark's column display. This tutorial introduces display filter expressions useful to review pcaps of malicious network traffic from infected Windows hosts.
This blog is the second in a series of Wireshark tutorials that provide customization options helpful for investigating malicious network traffic. It was first published in January 2019 and has been updated for 2023.
The pcaps in this tutorial contain traffic generated by Windows-based malware. Palo Alto Networks customers receive protection from these threats through Cortex XDR and our Next-Generation Firewall with Cloud-Delivered Security Services that include WildFire and Advanced Threat Prevention.
| Related Unit 42 Topics | pcap, Wireshark, Wireshark Tutorial |
Requirements and Supporting Material
This tutorial requires readers to have reviewed and understand our previous Wireshark tutorial. Requirements also include using a recent version of Wireshark, at least version 3.6.2 or later. This tutorial uses Wireshark version 4.0.7 with a customized column display from the previous tutorial. As always, we recommend using the most recent version of Wireshark available for your environment.
Our requirements also include a basic knowledge of network traffic. Part of this knowledge is understanding the three-way handshake used for TCP connections. Furthermore, some of the pcaps for this tutorial contain malicious content from Windows-based infections, so we recommend using Wireshark in a non-Windows environment like BSD, Linux or macOS.
The five pcap files used in this tutorial are contained in a password-protected ZIP archive hosted at our GitHub repository. Download the ZIP file named Wireshark-tutorial-filter-expressions-5-pcaps.zip. Use infected as the password to extract the pcap files, as shown below in Figure 1.
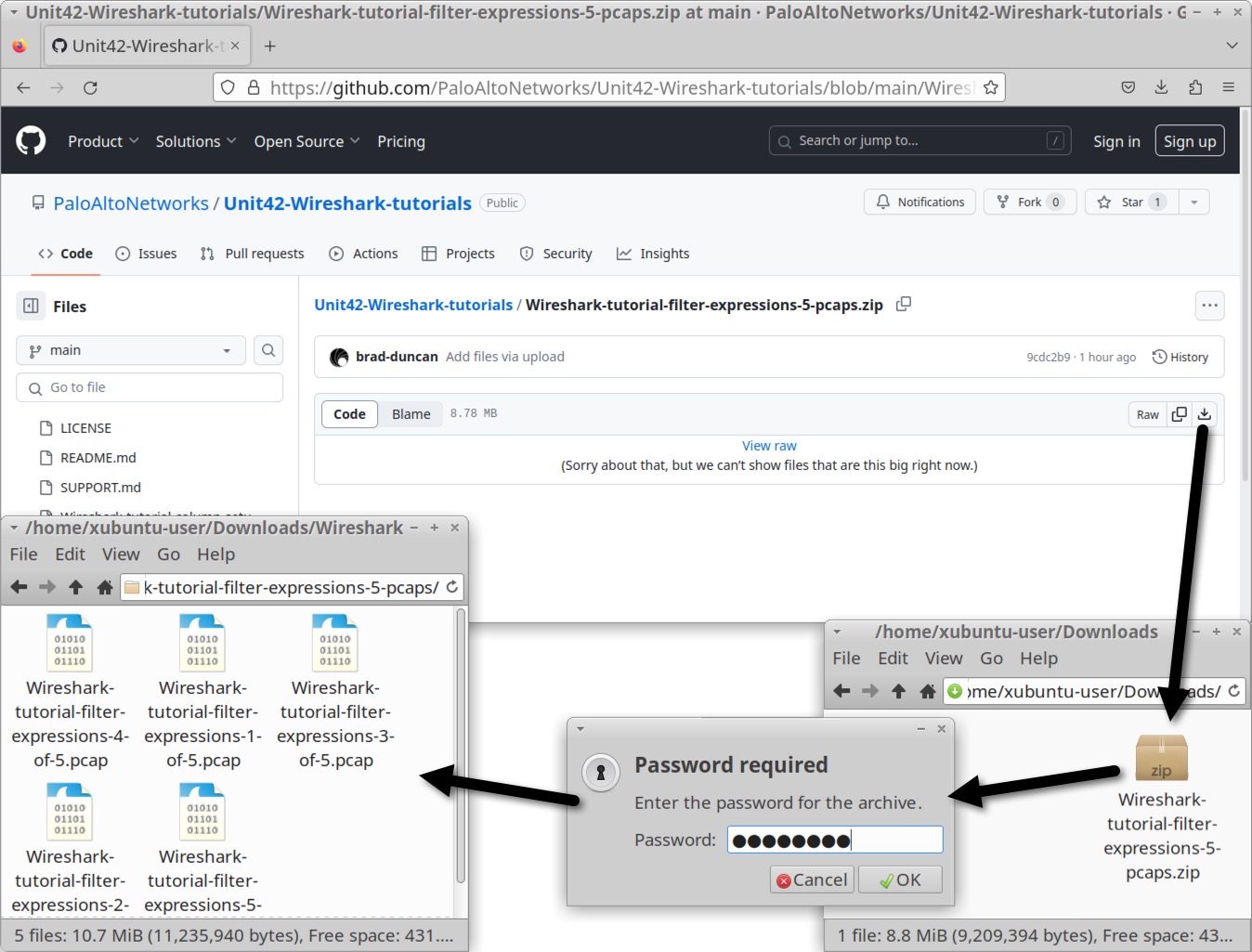
The five extracted pcap files for this tutorial are:
- Wireshark-tutorial-filter-expressions-1-of-5.pcap
- Wireshark-tutorial-filter-expressions-2-of-5.pcap
- Wireshark-tutorial-filter-expressions-3-of-5.pcap
- Wireshark-tutorial-filter-expressions-4-of-5.pcap
- Wireshark-tutorial-filter-expressions-5-of-5.pcap
Before continuing, we should ensure we are using a personal Wireshark profile, not the default.
Profile Check
During this tutorial, we save Wireshark filter expressions as filter buttons. Like the column changes from our previous tutorial, filter buttons will also be saved to your current Wireshark profile. The name of the personal profile from our previous tutorial is “Customized.”
To ensure you are using a personal profile, check the right side of the status bar, which shows the name of your current profile. You can also select “Configuration Profiles…” under the Edit menu to verify. Both options are shown below in Figure 2, revealing the customized profile name from our previous tutorial.
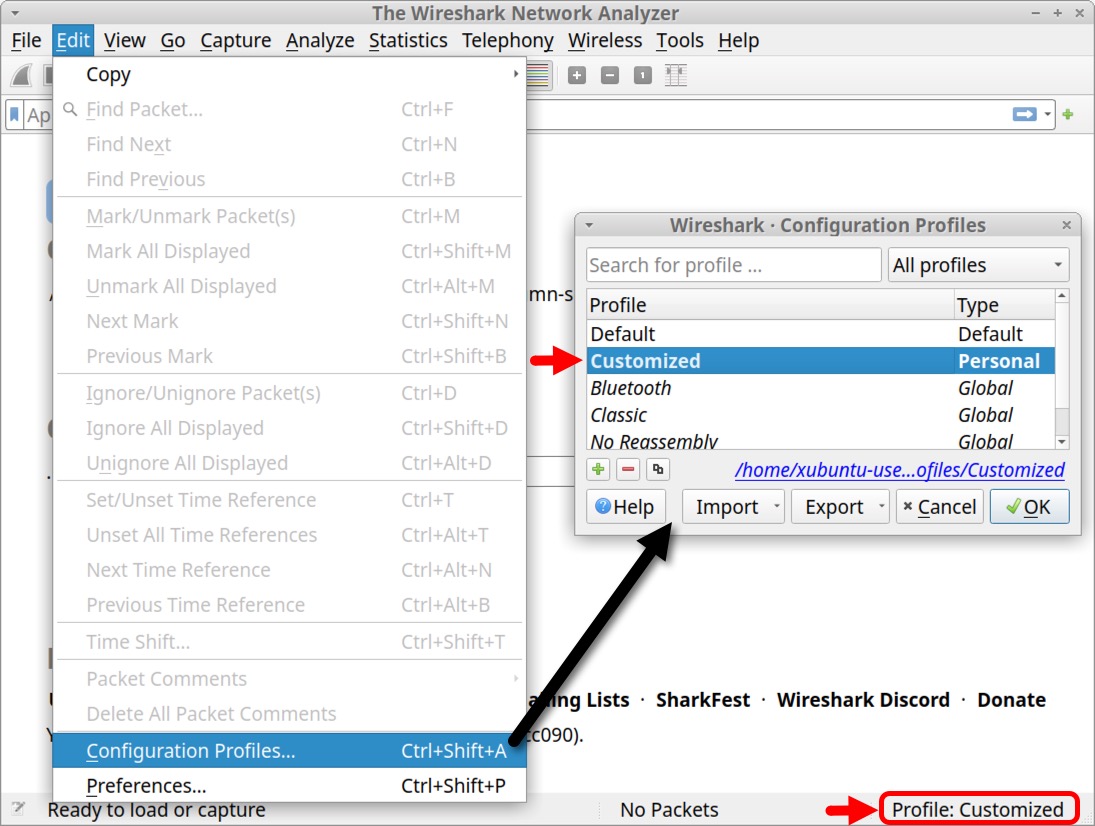
After confirming use of a personal profile, we can examine the Wireshark display filter.
The Wireshark Display Filter
In Wireshark's default configuration, the display filter is a bar located immediately above the column display. This is where we type expressions to filter our view of Ethernet frames, IP packets or TCP segments from a pcap. When typing in the display filter bar, Wireshark offers a list of suggestions based on the typed text, as shown below in Figure 3.
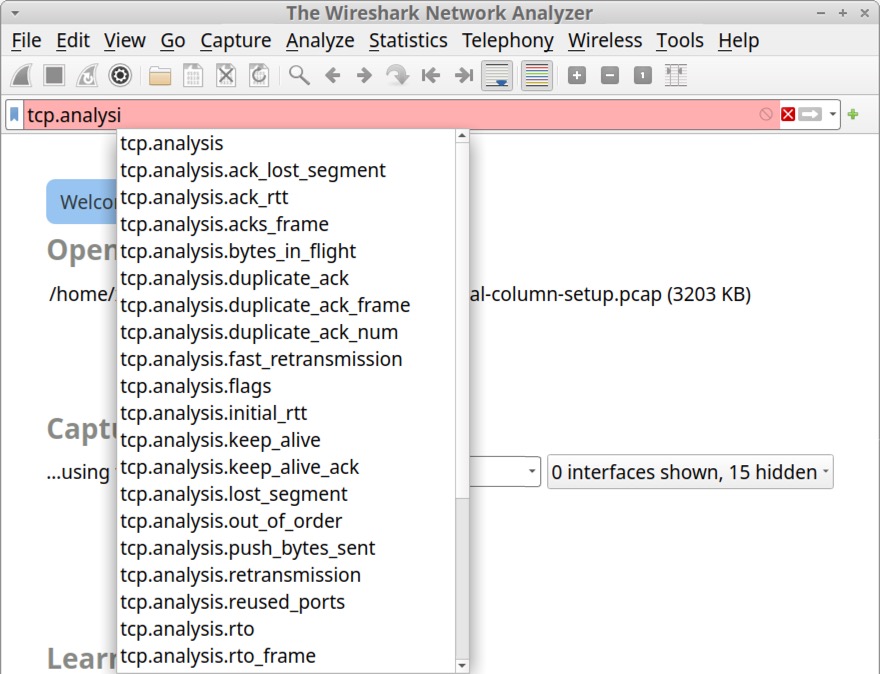
As long as the display filter bar remains red, the expression will not be accepted. Note the filter bar’s red color in Figure 3.
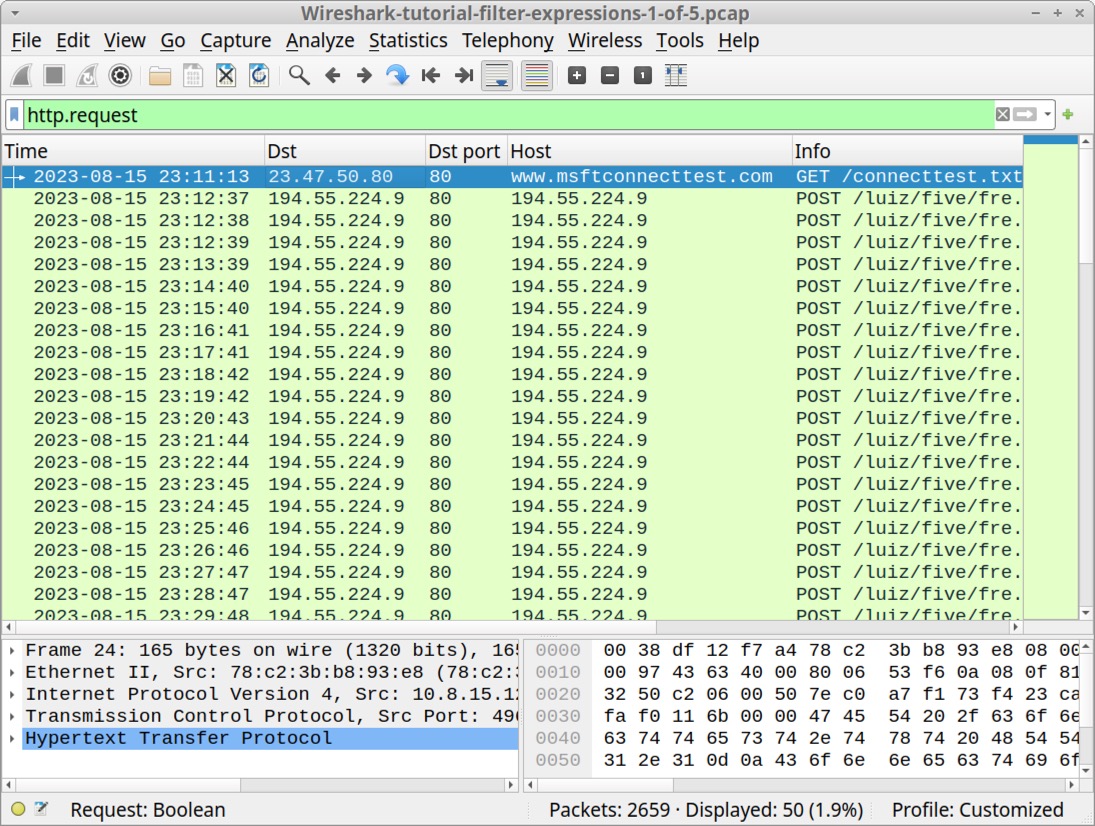
Open our first pcap named Wireshark-tutorial-filter-expressions-1-of-5.pcap in Wireshark. Type http.request in the display filter and hit Enter. If the filter bar is green, the expression has been accepted, and it should work properly, as shown below in Figure 4.
If the filter bar turns yellow, the expression is accepted, but it may not work as intended. Yellow filter bar results are more common in earlier versions of Wireshark. For example, Figure 5 shows the filter expression dns && ip.addr || http.request using Wireshark version 3.6.2. This produces a yellow result in the filter bar, with a suggested solution at the bottom in the status bar.
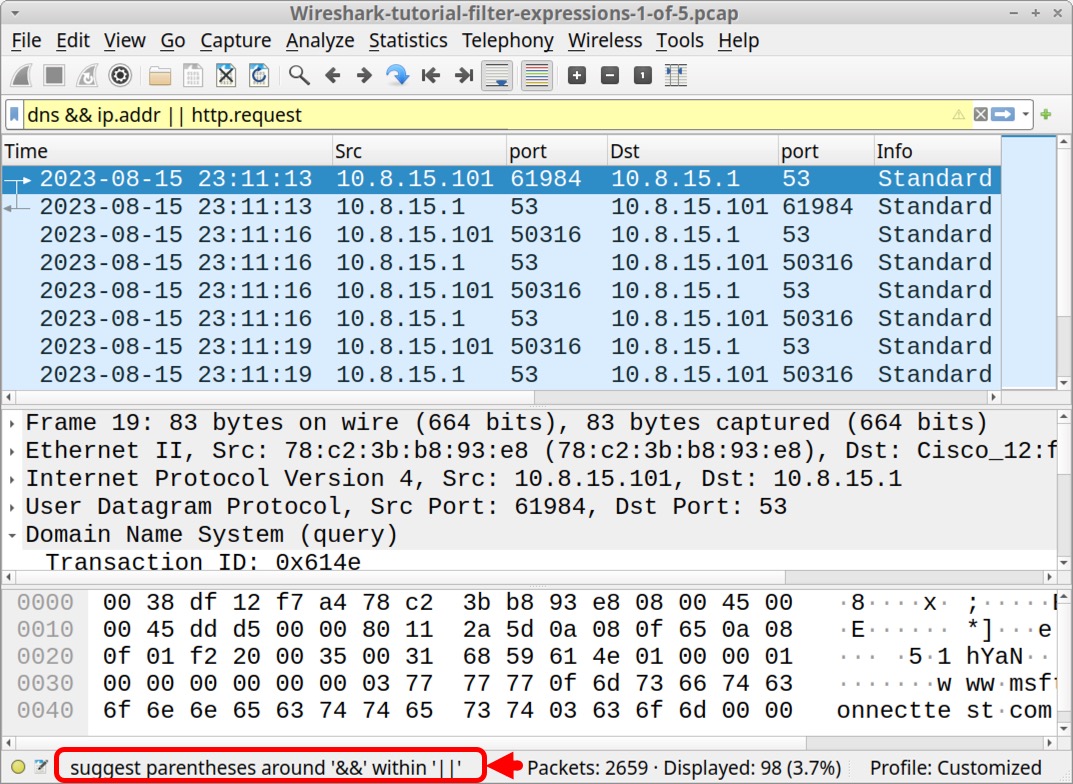
The results in Figure 5 reveal no HTTP request lines among the results in our column display. But using the same filter on the same pcap with Wireshark version 4.0.7 provides a green result and displays HTTP request lines, as shown below in Figure 6.
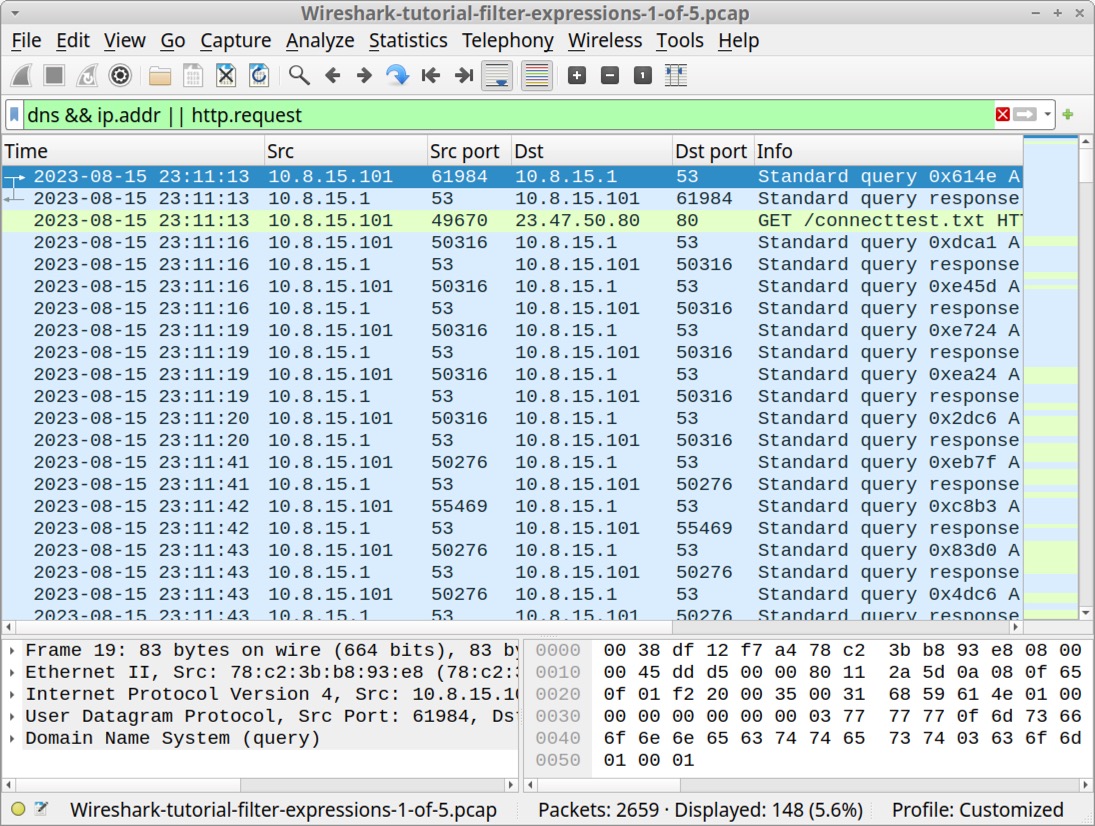
This illustrates one of the differences between Wireshark’s version 3 series and version 4. As stated earlier, we recommend using the latest version of Wireshark available for your system.
Wireshark's display filter uses Boolean expressions, so we can specify values and chain them together. Below, Table 1 lists common Boolean operators used in Wireshark filter expressions.
| Boolean Operator | Expression | Alternate Expression |
| Equals | == | eq |
| Not | ! | not |
| And | && | and |
| Or | || | or |
Table 1. Boolean functions used in Wireshark display filter expressions.
Random examples of Wireshark display filter expressions include:
- ip.addr eq 10.8.15[.]1 and dns.qry.name.len > 36
- http.request && ip.addr == 10.8.15[.]101
- http.request || http.response
- dns.qry.name contains microsoft or icmp
Filtering for Web Traffic
Our previous Wireshark tutorial used the following filter for web traffic:
http.request or tls.handshake.type eq 1
The expression http.request reveals URLs for HTTP requests, and tls.handshake.type eq 1 shows domain names used in HTTPS or SSL/TLS traffic.
For web traffic generated by Windows hosts, results from this filter include HTTP requests over UDP port 1900. This HTTP traffic is Simple Service Discovery Protocol (SSDP). SSDP is used to discover plug-and-play devices and is not associated with normal web traffic. We can exclude SSDP traffic in our results by modifying our filter expression to:
(http.request or tls.handshake.type eq 1) and !(ssdp)
While parentheses in the above filter expression are not required in Wireshark version 4, we suggest including them to ensure filter expression compatibility with older versions of Wireshark. Use this filter on our first pcap, Wireshark-tutorial-filter-expressions-1-of-5.pcap and the results should appear similar to Figure 7.
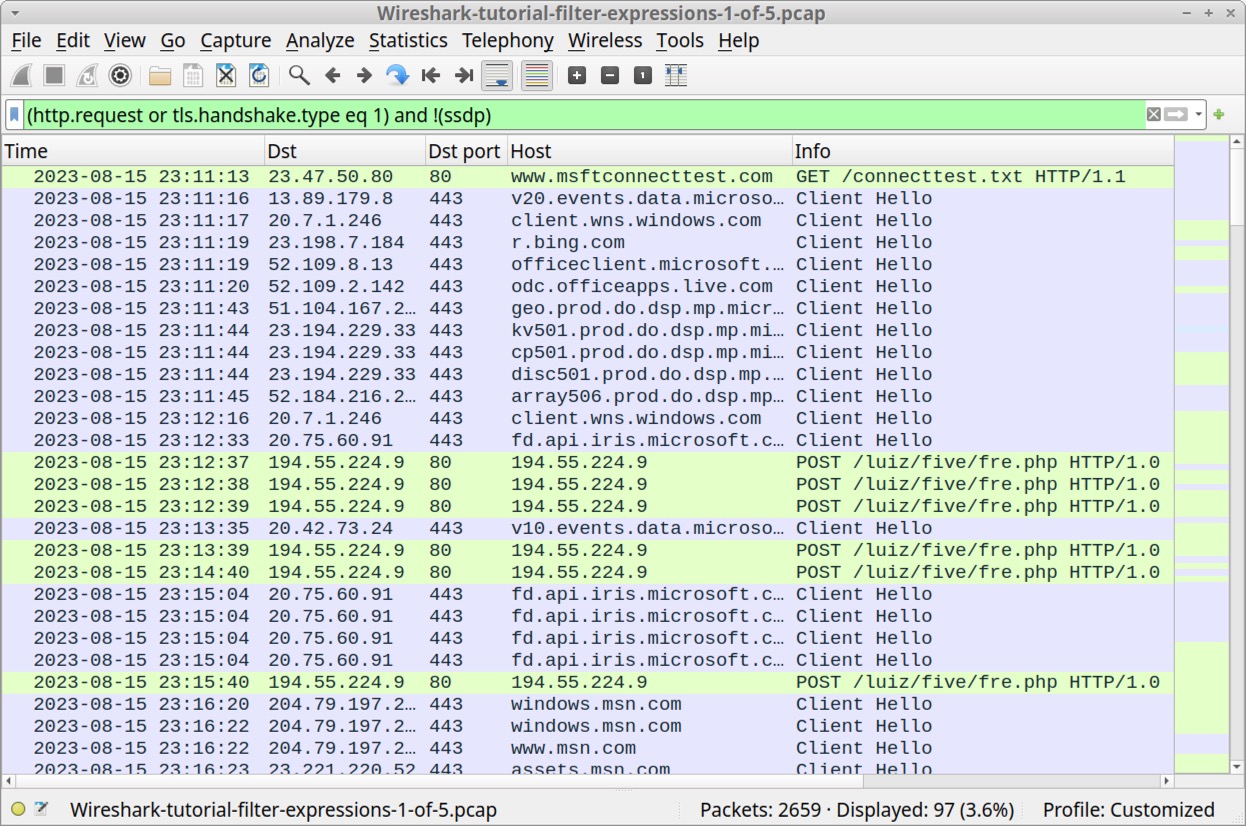
Reviewing the traffic shown in Figure 7 reveals several lines of unencrypted HTTP POST requests associated with Loki Bot malware to the URL hxxp://194.55.224[.]9/liuz/five/fre.php, which was reported to Threatfox in August 2023.
To examine the traffic, click on any of the lines for traffic to 194.55.224[.]9 to select the frame, then right-click to bring up a menu. From the menu, select “Follow” then “TCP Stream” or “HTTP Stream,” as shown below in Figure 8.
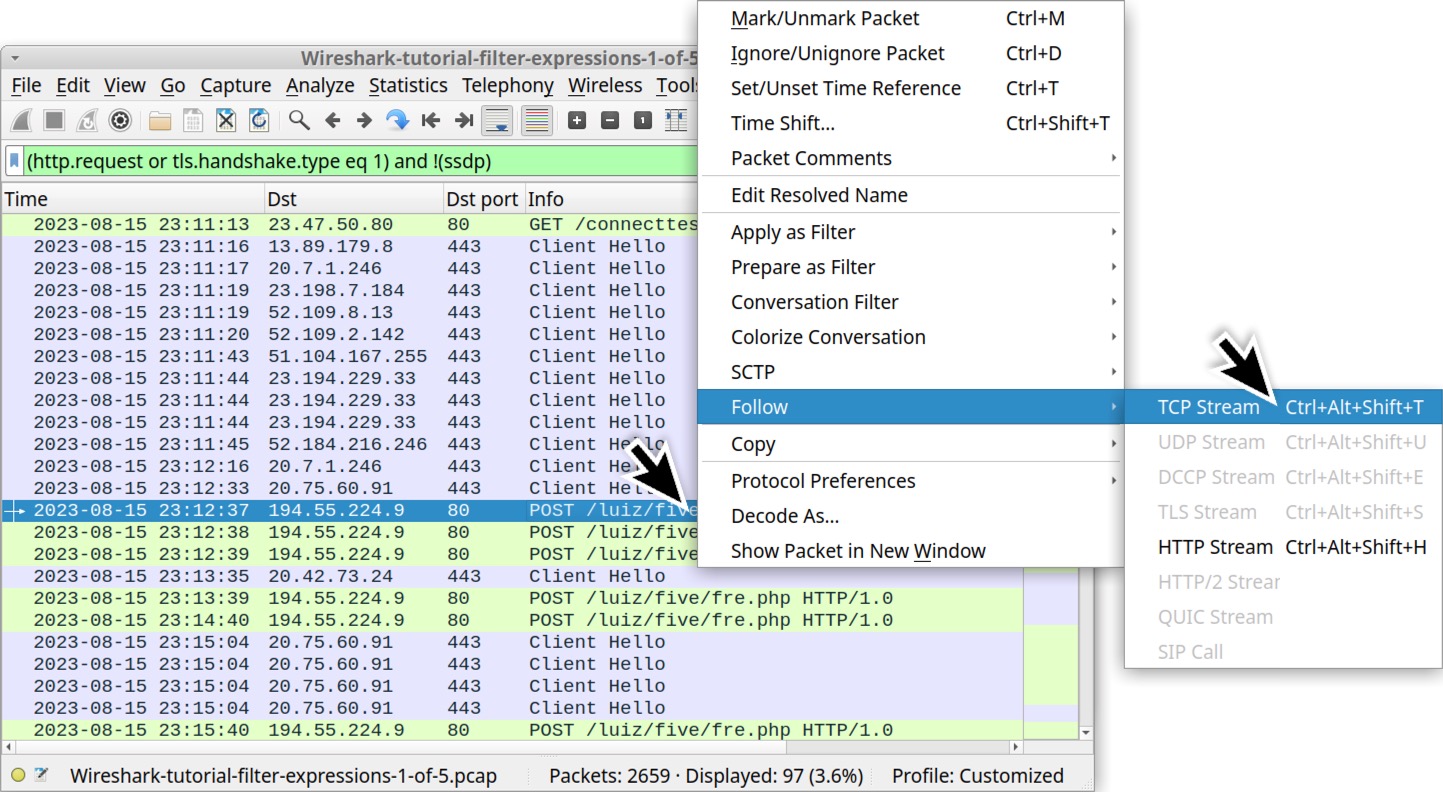
This will bring up a new window, and we can review an ASCII representation of the content of this unencrypted HTTP traffic. Review this on your own to become familiar with Loki Bot command and control (C2) traffic.
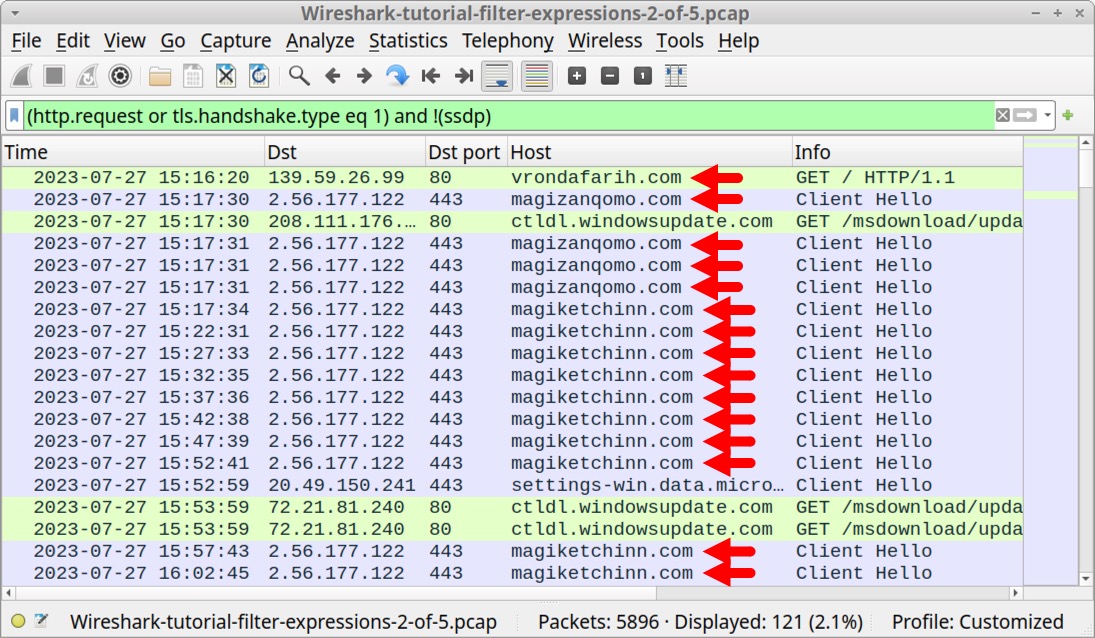
Open our second pcap Wireshark-tutorial-filter-expressions-2-of-5.pcap in Wireshark. This is traffic from a standard variant IcedID (Bokbot) infection. It contains HTTP traffic to vrondafarih[.]com and HTTPS traffic to both magiketchinn[.]com and magizanqomo[.]com. All three were identified as IcedID-related domains in July 2023.
Figure 9 shows these IcedID-associated domains in our second pcap using the basic web filter in Wireshark.
Creating Filter Buttons
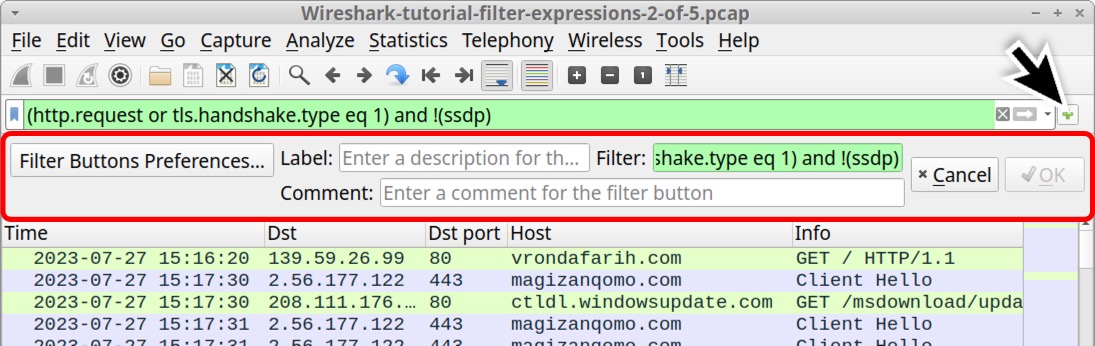
Complex filter expressions are very tedious to type in Wireshark's filter bar every time you need them. Fortunately, we can save any of our typed expressions as filter buttons.
On the right side of the Wireshark filter bar is a plus sign to add a filter button. Ensure we are still using the basic web filter shown in Figures 7, 8 and 9. After ensuring this filter has been implemented, click on the plus sign as shown below in Figure 10.
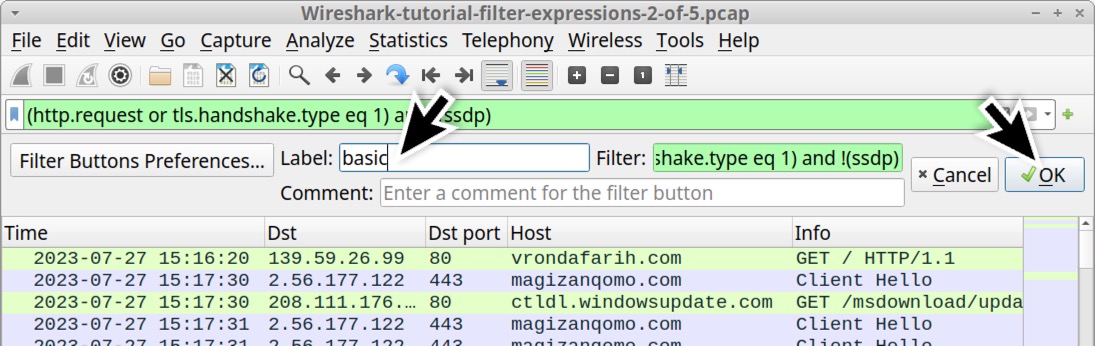
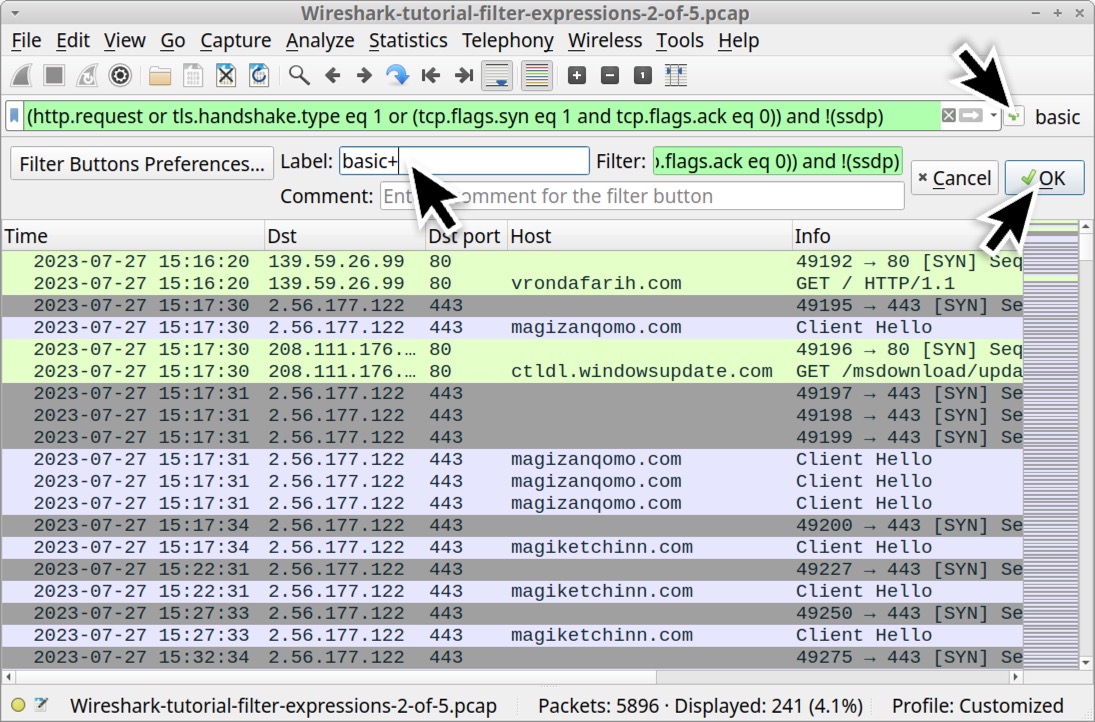
Clicking the plus sign generates a temporary panel immediately under the filter bar, as noted above in Figure 10. This panel has three fields: Label, Filter and Comment. The Filter field should contain the expression already implemented in the filter bar. Since this is our basic web filter, type basic in the Label field and click the OK button as shown below in Figure 11.
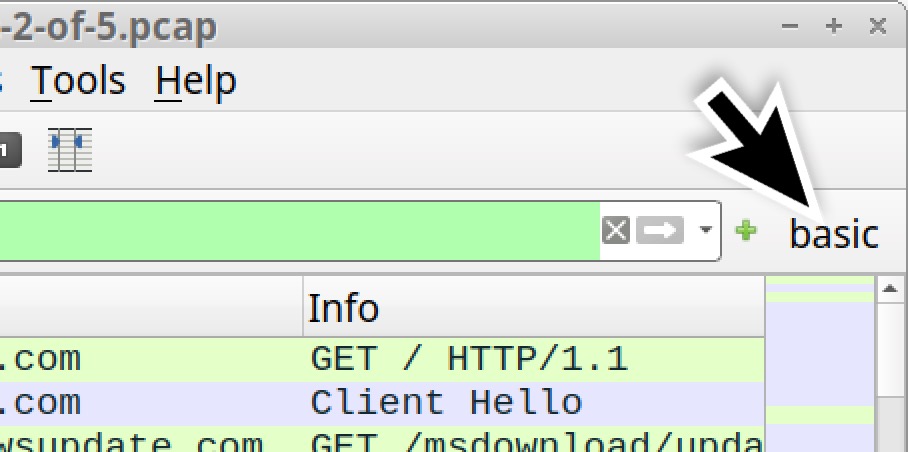
This should create a button to the right of Wireshark's filter bar labeled "basic" as shown below in Figure 12. Wireshark filter buttons have no borders and look like labels, but they function as buttons. Anytime you need this basic web filter, just left-click on it.
For this tutorial, we should create the following filter buttons listed below in Table 2.
| Button Label | Filter Expression |
| basic | basic (http.request or tls.handshake.type eq 1) and !(ssdp) |
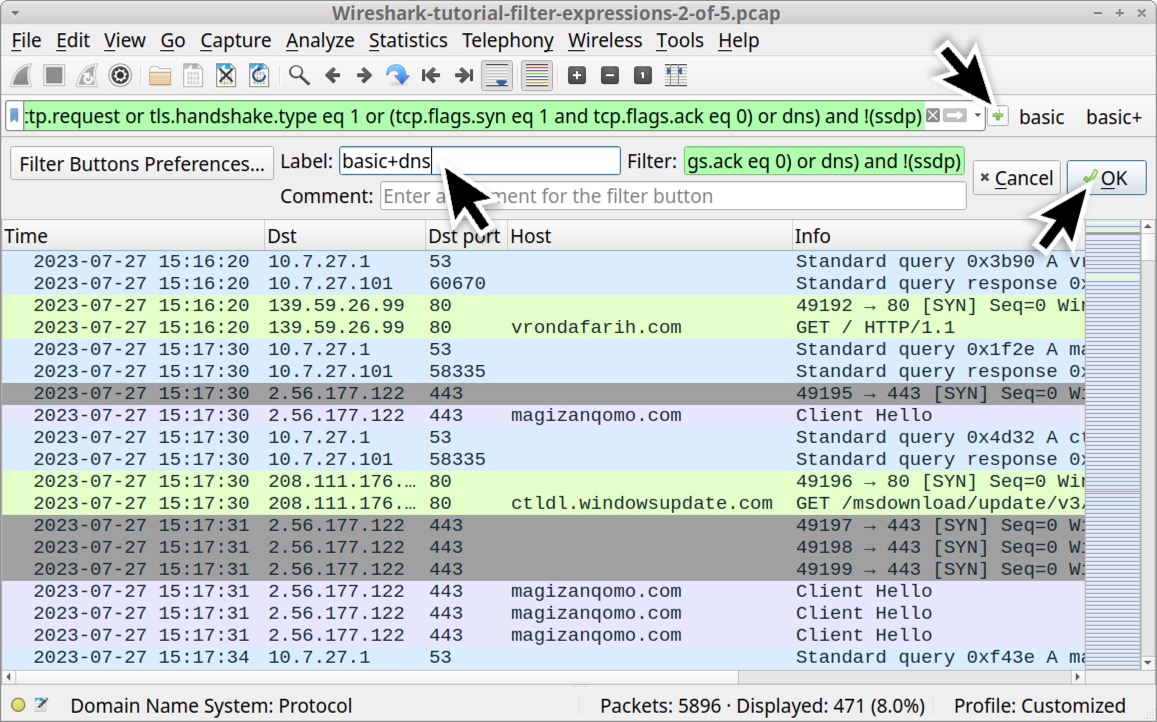
| basic+ | basic (http.request or tls.handshake.type eq 1 or (tcp.flags.syn eq 1 and tcp.flags.ack eq 0)) and !(ssdp) |
| basic+dns | basic (http.request or tls.handshake.type eq 1 or (tcp.flags.syn eq 1 and tcp.flags.ack eq 0) or dns) and !(ssdp) |
Table 2. Filter buttons to more fully investigate malicious web traffic.
When examining suspicious traffic in Wireshark, we should use a progressive method. Start simple with our basic web filter, then check for other non-web traffic using the “basic+” filter.
In Table 2, the “basic+” filter expression displays the same information as our “basic” filter, but it includes TCP segments with the SYN flag and not the ACK flag by adding or (tcp.flags.syn eq 1 and tcp.flags.ack eq 0). This displays TCP SYN segments that reveal the start of a TCP stream. With this filter, we can find non-web traffic in a pcap.
The “basic+” filter also reveals any TCP connection attempts that failed. Depending on the IP address, repeated and failed TCP connection attempts could indicate a C2 server that was off-line when the pcap was recorded.
After checking the “basic+” filter, we should review the “basic+dns” filter to check for any notable DNS activity.
In Table 2, the “basic+dns” filter expression shows the same data as our “basic+” filter, but it includes or dns. This filter reveals any DNS queries in the pcap. It is very helpful for determining domain names associated with non-web traffic.
Furthermore, if a malware sample’s C2 server is offline when the pcap was recorded, this filter could reveal one or more C2 domains associated with any failed connection attempts. Finally, this filter might reveal examples of DNS tunneling.
Add the “basic+” and “basic+dns” filters as shown below in Figure 13 and Figure 14. After adding the filter buttons, we should see all three to the right of Wireshark’s filter bar as shown below in Figure 15.
With our three newly created filter buttons in place, we can explore other types of malicious traffic.
Filtering for Non-Web Traffic
Open our third pcap Wireshark-tutorial-filter-expressions-3-of-5.pcap in Wireshark. This pcap contains post-infection traffic generated by a Remote Access Tool (RAT) malware called Ave Maria RAT (also known as Warzone RAT).
Using our basic web filter, nothing obvious stands out in the traffic. However, by using our “basic+dns” web filter and scrolling through the results, we can see things more clearly. We can find a DNS query for adaisreal.ddns[.]net that resolves to 87.121.221[.]212, then a TCP segment to that IP address with the SYN flag over TCP port 7888, as shown below in Figure 16.
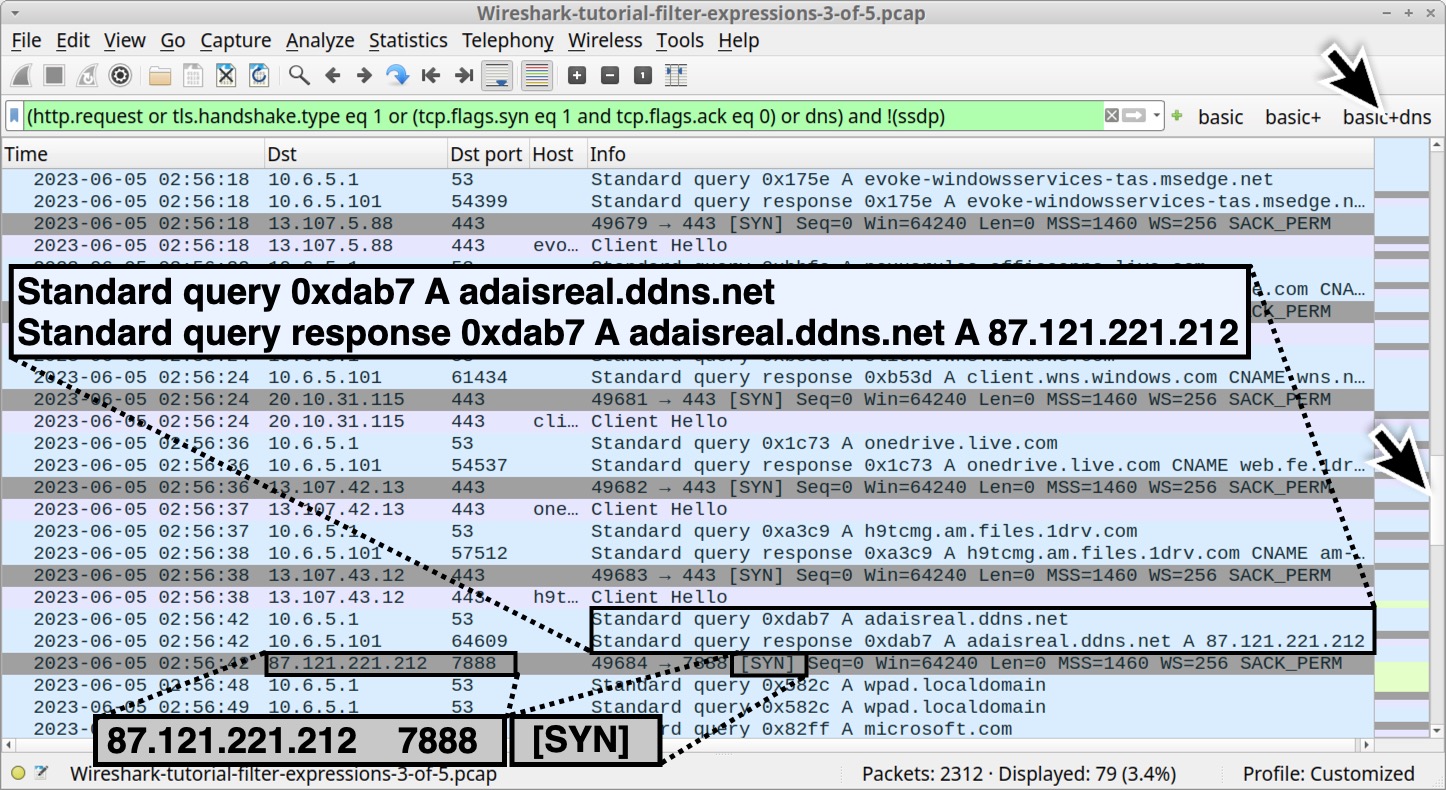
This is just one example, but different RATs and other types of malware also generate similar types of non-web traffic. Our “basic+dns” filter provides a way to search for malicious non-web activity.
Filtering for FTP Traffic
Some infection traffic uses common protocols that Wireshark can easily decode. Our fourth pcap Wireshark-tutorial-filter-expressions-4-of-5.pcap contains post-infection activity caused by a malware executable that generates FTP traffic. Our “basic+dns” filter reveals traffic over TCP port 21 and another TCP port after a DNS query to valvulasthermovalve[.]cl as shown below in Figure 17.
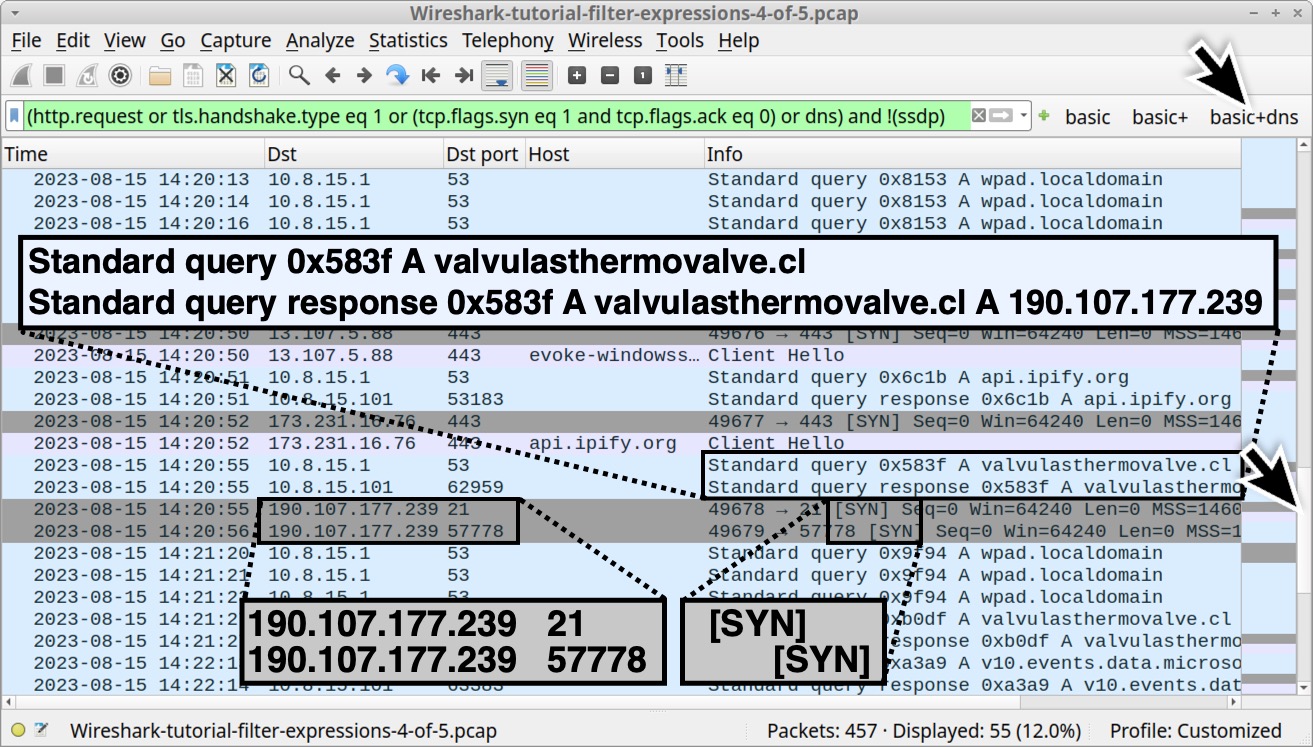
In Figure 17, we can also see HTTPS traffic to api.ipify[.]org immediately before the FTP activity. While this domain is not inherently malicious, malware often uses the service to check the IP address of an infected host.
Our “basic+dns” filter can help find unencrypted FTP traffic, but other filter expressions would better fit an FTP search. Two basic Wireshark filters for unencrypted FTP traffic are shown below in Table 3.
| Filter Expression | Description |
| ftp | FTP activity in the control channel (TCP port 21) |
| ftp-data | FTP activity in the data channel (ephemeral TCP port) |
Table 3. Basic FTP searches for Wireshark.
A general-purpose filter expression to review unencrypted FTP activity is:
ftp.request.command or (ftp-data and tcp.seq eq 1)
Type the above expression into Wireshark’s display filter bar and hit enter. The results should look similar to the screenshot in Figure 18.
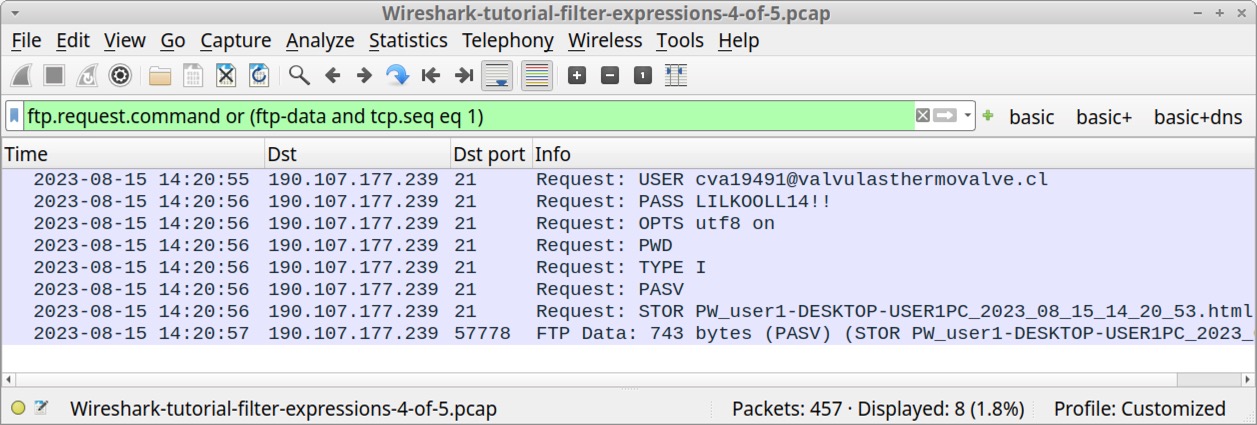
Figure 18 shows the username and password for this compromised FTP site, then a STOR command to send an HTML file to the FTP server. This represents stolen data being exfiltrated from the infected Windows host. We can follow the TCP streams to review the FTP commands and examine the stolen data. If needed, you can save this filter expression as a filter button for future use.
Filtering for Email (Spambot) Traffic
In addition to FTP, malware can use other common protocols for malicious traffic. Spambot malware can turn an infected host into a spambot designed to constantly send email messages. This is characterized by a large amount of DNS requests to various mail servers followed by SMTP traffic on TCP ports 25, 465, 587 and other ports less-commonly associated with SMTP traffic.
Our fifth pcap, Wireshark-tutorial-filter-expressions-5-of-5.pcap, contains post-infection spambot traffic. Open that pcap and type the following expression into Wireshark’s filter bar:
smtp or dns
The results should look similar to Figure 19.
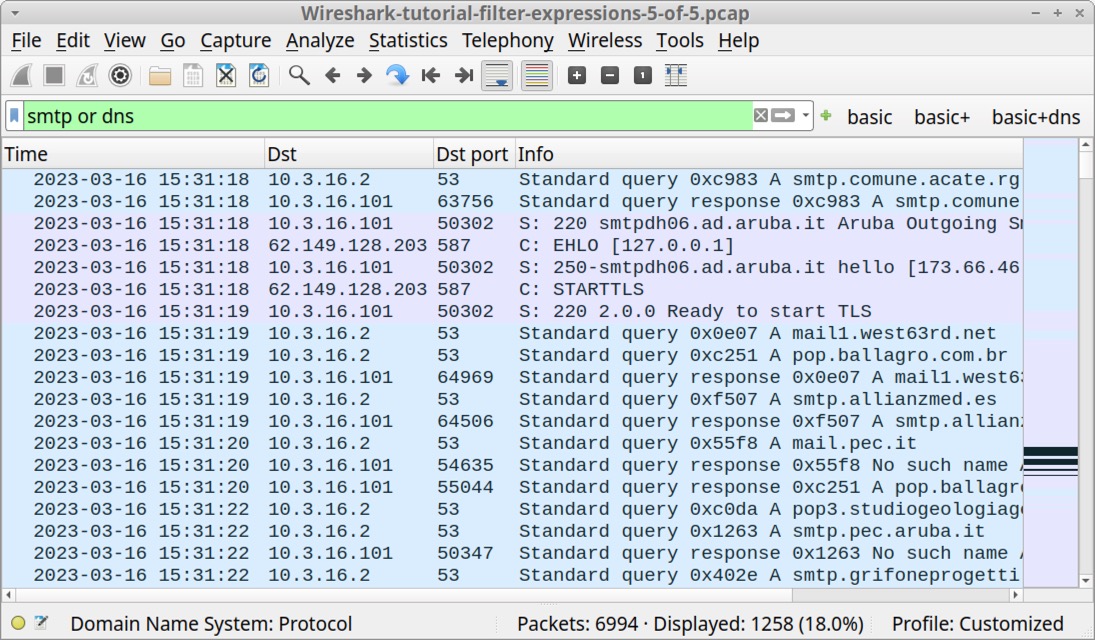
If you scroll through the results, you should find several DNS queries for various mail server domains and different SMTP statements on the far right under the “Info” column.
Now type the following filter into the filter bar:
smtp.req.command
The results shown below in Figure 20 reveal the infected host contacted several different IP addresses for mail servers in a relatively short amount of time. Note how most of these SMTP requests state STARTTLS, which establishes an encrypted tunnel after the initial SMTP connection. Most email traffic is encrypted, and most spambot activity is also encrypted.
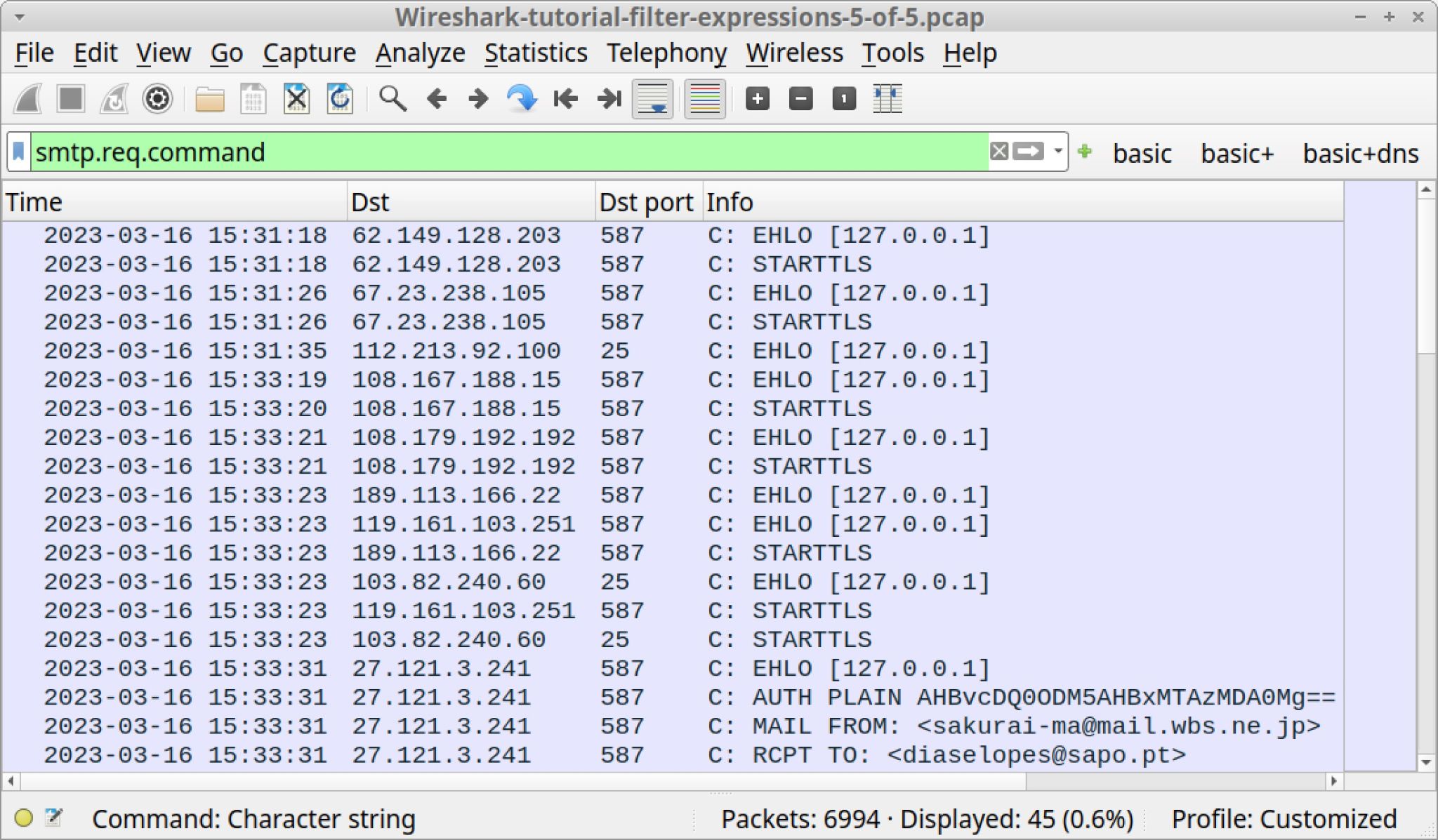
However, spambot traffic might have unencrypted email messages we can review. To find these messages, type the following expression in Wireshark’s filter bar:
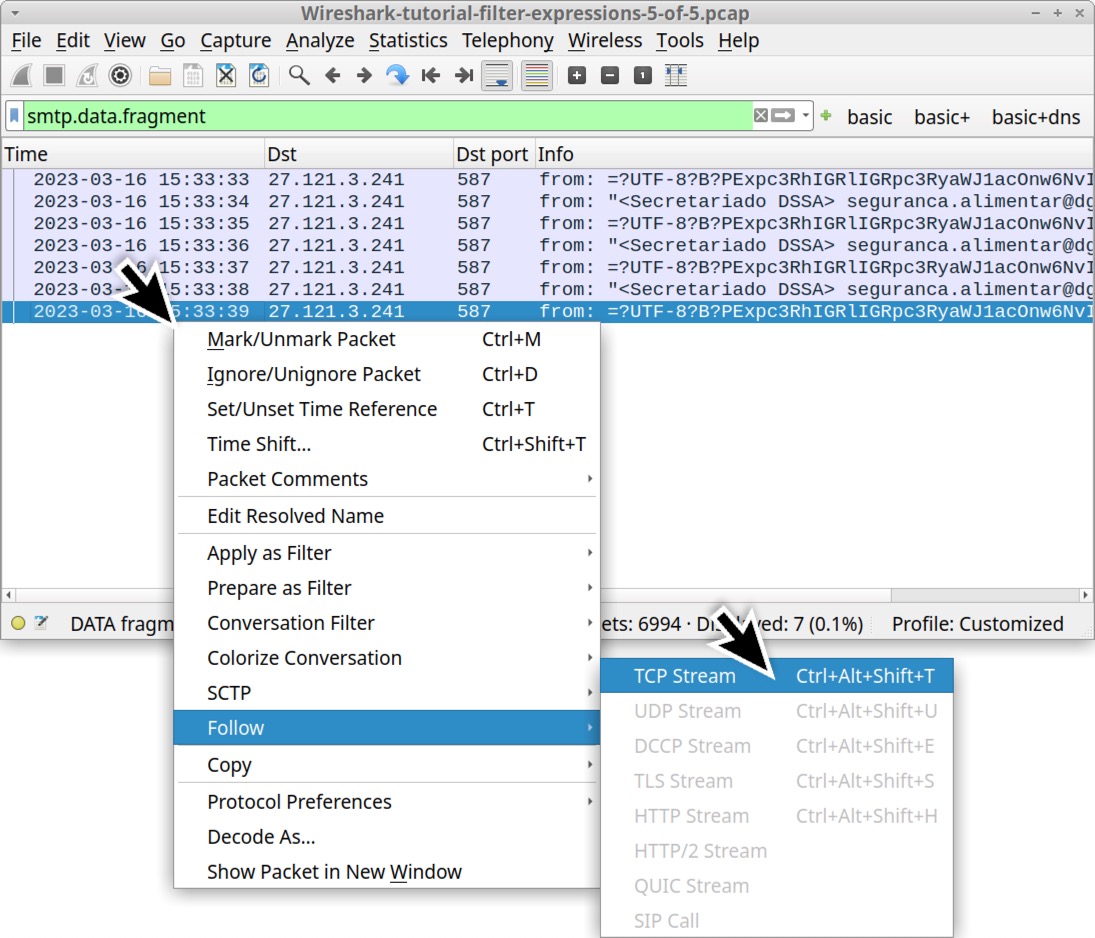
smtp.data.fragment
This should reveal seven results in the column display as shown below in Figure 21. We can follow the TCP stream for any of these to further investigate these messages.
While not extensive, these are the most common filter expressions useful for examining spambot traffic.
Conclusion
Wireshark display filter expressions are necessary to understand the contents of a pcap. When combined with an optimized column display, effective filters can immensely help security professionals investigate suspicious network activity.
Our next tutorial in this series reviews how to identify hosts and users when investigating suspicious network activity.
Pcaps used in this tutorial contain traffic generated by Windows-based malware. Palo Alto Networks customers receive protection from these threats through Cortex XDR and our Next-Generation Firewall with Cloud-Delivered Security Services that include WildFire, Advanced Threat Prevention and Advanced URL Filtering.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
The following are indicators of malicious activity from the pcaps used in this tutorial.
| URL | hxxp://194.55.224[.]9/liuz/five/fre.php |
| Description | Loki Bot C2 URL noted as early as 2023-08-15 |
| IcedID C2 domains noted on 2023-07-27: |
|
| URL | 87.121.221[.]212:7888 - tcp://adaisreal.ddns[.]net:7888/ |
| Description | C2 for Ave Maria RAT (Warzone RAT) noted as early as 2023-06-05 |
| SHA256 hash | adfa401cdfaac06df0e529bc9d54b74cea9a28d4266a49edafa5b8e04e3b3594 |
| File size | 604,672 bytes |
| Filename | unknown |
| File description | Windows executable (EXE), info stealer using FTP for data exfiltration |
| URL | 190.107.177[.]239:21 - fxp://valvulasthermovalve[.]cl/ |
| Description | Noted as early as 2023-06-07, FTP server on legitimate site used for data exfiltration, also used by the above malware sample |
| SHA256 hash | f24259e65a935722c36ab36f6e4429a1d0f04c0ac3600e4286cc717acc5b03d7 |
| File size | 134,140 bytes |
| Filename | Details-3922941.one |
| File description | OneNote file as an attachment in unencrypted spambot emails for Emotet on 2023-03-16 |
Additional Resources
-
- Wireshark Tutorial: Changing Your Column Display - Unit 42, Palo Alto Networks
- Wireshark Tutorial: Identifying Hosts and Users - Unit 42, Palo Alto Networks
- Wireshark Tutorial: Exporting Objects from a Pcap - Unit 42, Palo Alto Networks
- Wireshark Tutorial: Decrypting HTTPS Traffic - Unit 42, Palo Alto Networks
- Wireshark Tutorial: Wireshark Workshop Videos Now Available - Unit 42, Palo Alto Networks
- Full list of Wireshark Tutorials and Quizzes - Unit 42, Palo Alto Networks








 Get updates from Unit 42
Get updates from Unit 42