Last, but Not Least: Defray777
Defray777 is an elusive family of ransomware also known as Ransom X and RansomExx. Although it has recently been covered in the news as a new family, it has been in use since at least 2018 and is responsible for a number of high-profile ransomware incidents -- as detailed in the articles we linked to.
Defray777 runs entirely in memory, which is why there have been so few publicly discussed samples to date. In several recent incidents, Defray777 was loaded into memory and executed by Cobalt Strike, which was delivered by the Vatet loader.
During our research, we discovered multiple decryptors for this ransomware family, going back as early as 2018. Reviewing decryptors from 2018 until present shows that there has been consistency in the ransomware’s encryption and decryption methodology, as well as the use of Themida for packing their decryptors. Table 10 shows a list of Defray777 decryptors discovered in AutoFocus, with a list of organizations that suffered ransomware attacks. This shows that Defray777 has been consistently active since 2018.
| Date | Victim |
| 12/7/2018 | Education Organization |
| 2/4/2019 | Healthcare Organization |
| 3/1/2019 | Technology Organization |
| 3/15/2019 | Education Organization |
| 8/8/2019 | Healthcare Organization |
| 8/25/2019 | Education Organization |
| 8/28/2019 | Transportation and Logistics Organization |
| 9/3/2019 | Legal Organization |
| 9/6/2019 | Education Organization |
| 9/26/2019 | Healthcare Organization |
| 10/30/2019 | Government Organization |
| 11/1/2019 | Healthcare Organization |
| 2/4/2020 | Technology Organization |
| 2/10/2020 | Government Organization |
| 3/16/2020 | Food Organization |
| 10/17/2020 | Finance Organization |
Table 10. Defray777 ransomware attacks listed by date and victim.
We have examined several recent Defray777 samples, including one sample that was obtained directly from memory during a recent incident. Our in-depth analysis resulted in the findings outlined below.
Decrypted Strings
The string decryption process is the same as we saw with PyXie. The following strings were decrypted from a recent Defray777 sample:
| Already active [%s]
+%u (%u) files done [%s] [%u KB/s] Started (PID: %u; Workers: %u; AES-%s) [%s] Complete (+%u (%u) files done) [%s] Work time: %d:%02d:%02d Unable to get computer name CryptoGuard kernel32.dll ConvertStringSecurityDescriptorToSecurityDescriptorW advapi32.dll IsWow64Process SystemDrive KiUserExceptionDispatcher |
Table 11. Defray777 encrypted strings.
Prioritizing Defray777 on the Impacted System
While deep diving on a recovered Defray777 sample, we found that Defray777 exhibits the following notable characteristics regarding the prioritization of threads and processes:
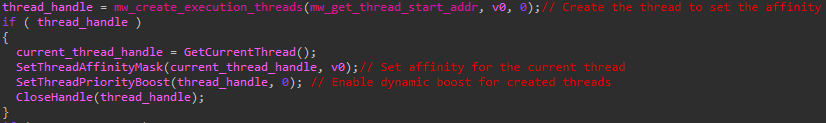
- During execution, the ransomware uses SetProcessPriorityBoost to prioritize the threads of the Defray777 process.
- Defray777 additionally focuses on creating and prioritizing threads for encryption by calling SetThreadAffinityMask and SetThreadPriorityBoost.
- Defray777 uses multithreading to improve ransomware performance.
Killing “Undesirable” Processes
As part of the execution workflow, Defray777 creates threads that will be responsible for the killing of processes that the threat actors deem to be “undesirable.” The execution continues by getting a listing of processes using CreateToolhelp32Snapshot before iterating through all active processes (with the exception of itself) and killing all “undesirable” processes. Defray777 specifically targets process that can be opened with the desired access of SYNCHRONIZE | PROCESS_QUERY_INFORMATION | PROCESS_VM_WRITE | PROCESS_VM_READ | PROCESS_VM_OPERATION | PROCESS_CREATE_THREAD.
Defray777 excludes all processes that contain the system file path in their full image path. Additionally, the ransomware will exclude the following processes from being killed during execution:
| powershell.exe | rundll32.exe |
| wefault.exe | explorer.exe |
| vmnat.exe |
Table 12. Excluded processes.
Stopping System Services
During execution, Defray777 stops the following services from running:
| Acronis VSS Provider | MSExchangeADTopology | MSSQLSERVER | SQLAgent$PRACTTICEMGT |
| AcronisAgent | MSExchangeAntispamUpdate | MSSQLServerADHelper | SQLAgent$PROD |
| AcronixAgent | MSExchangeEdgeSync | MSSQLServerADHelper100 | SQLAgent$PROFXENGAGEMENT |
| AcrSch2Svc | MSExchangeES | MSSQLServerOLAPService | SQLAgent$SBSMONITORING |
| Antivirus | MSExchangeFBA | MySQL57 | SQLAgent$SHAREPOINT |
| ARSM | MSExchangeFDS | MySQL80 | SQLAgent$SOPHOS |
| AVP | MSExchangeIS | NetMsmqActivator | SQLAgent$SQL_2008 |
| BackupExecAgentAccelerator | MSExchangeMailboxAssistants | nginx | SQLAgent$SQLEXPRESS |
| BackupExecAgentBrowser | MSExchangeMailboxReplication | ntrtscan | SQLAgent$SYSTEM_BGC |
| BackupExecDeviceMediaService | MSExchangeMailSubmission | OracleClientCache80 | SQLAgent$TPS |
| BackupExecJobEngine | MSExchangeMGMT | OracleServiceXE | SQLAgent$TPSAMA |
| BackupExecManagementService | MSExchangeMTA | OracleXETNSListener | SQLAgent$VEEAMSQL2008R2 |
| BackupExecRPCService | MSExchangeProtectedServiceHost | PDVFSService | SQLAgent$VEEAMSQL2012 |
| BackupExecVSSProvider | MSExchangeRepl | POP3Svc | SQLBrowser |
| bedbg | MSExchangeRPC | ReportServer | SQLsafe Backup Service |
| DbxSvc | MSExchangeSA | ReportServer$SQL_2008 | SQLsafe Filter Service |
| DCAgent | MSExchangeSearch | ReportServer$SYSTEM_BGC | SQLSafeOLRService |
| EhttpSrv | MSExchangeServiceHost | ReportServer$TPS | SQLSERVERAGENT |
| ekrn | MSExchangeSRS | ReportServer$TPSAMA | SQLTELEMETRY |
| Enterprise Client Service | MSExchangeThrottling | RESvc | SQLTELEMETRY$ECWDB2 |
| EPSecurityService | MSExchangeTransport | sacsvr | SQLWriter |
| EPUpdateService | MSExchangeTransportLogSearch | SamSs | SstpSvc |
| EraserSvc11710 | msftesql$PROD | SAVAdminService | svcGenericHost |
| EsgShKernel | MSOLAP$SQL_2008 | SAVService | swi_filter |
| ESHASRV | MSOLAP$SYSTEM_BGC | SDRSVC | swi_service |
| FA_Scheduler | MSOLAP$TPS | SepMasterService | swi_update |
| IISAdmin | MSOLAP$TPSAMA | ShMonitor | swi_update_64 |
| IMAP4Svc | MSSQL$BKUPEXEC | Smcinst | Symantec System Recovery |
| KAVFS | MSSQL$ECWDB2 | SmcService | TmCCSF |
| KAVFSGT | MSSQL$PRACTICEMGT | SMTPSvc | tmlisten |
| kavfsslp | MSSQL$PRACTTICEBGC | SNAC | TrueKey |
| klnagent | MSSQL$PROD | SntpService | TrueKeyScheduler |
| macmnsvc | MSSQL$PROFXENGAGEMENT | Sophos Agent | TrueKeyServiceHelper |
| masvc | MSSQL$SBSMONITORING | Sophos AutoUpdate Service | UI0Detect |
| MBAMService | MSSQL$SHAREPOINT | Sophos Clean Service | Veeam Backup Catalog Data Service |
| MBEndpointAgent | MSSQL$SOPHOS | Sophos Device Control Service | VeeamBackupSvc |
| McAfeeEngineService | MSSQL$SQL_2008 | Sophos File Scanner Service | VeeamBrokerSvc |
| McAfeeFramework | MSSQL$SQLEXPRESS | Sophos Health Service | VeeamCatalogSvc |
| McAfeeFrameworkMcAfeeFramework | MSSQL$SYSTEM_BGC | Sophos MCS Agent | VeeamCloudSvc |
| McShield | MSSQL$TPS | Sophos MCS Client | VeeamDeploymentService |
| McTaskManager | MSSQL$TPSAMA | Sophos Message Router | VeeamDeploySvc |
| mfefire | MSSQL$VEEAMSQL2008R2 | Sophos Safestore Service | VeeamEnterpriseManagerSvc |
| mfemms | MSSQL$VEEAMSQL2012 | Sophos System Protection Service | VeeamHvIntegrationSvc |
| mfevtp | MSSQLFDLauncher | Sophos Web Control Service | VeeamMountSvc |
| MMS | MSSQLFDLauncher$PROFXENGAGEMENT | sophossps | VeeamNFSSvc |
| MongoDB | MSSQLFDLauncher$SBSMONITORING | SQL Backups | VeeamRESTSvc |
| mozyprobackup | MSSQLFDLauncher$SHAREPOINT | SQLAgent$BKUPEXEC | VeeamTransportSvc |
| MsDtsServer | MSSQLFDLauncher$SQL_2008 | SQLAgent$CITRIX_METAFRAME | W3Svc |
| MsDtsServer100 | MSSQLFDLauncher$SYSTEM_BGC | SQLAgent$CXDB | wbengine |
| MsDtsServer110 | MSSQLFDLauncher$TPS | SQLAgent$ECWDB2 | WRSVC |
| MSExchangeAB | MSSQLFDLauncher$TPSAMA | SQLAgent$PRACTTICEBGC | Zoolz 2 Service |
Table 13. Services stopped by Defray777.
File Encryption
Based on a recent Defray777 sample recovered from memory, the ransomware will get a listing of all logical drives on the system using a call to GetLogicalDriveStringsW before iterating through each drive to encrypt files using the following process:
- To begin, Defray777 checks for whether the processor feature PF_XMMI64_INSTRUCTIONS_AVAILABLE is present on the impacted system.
- If enabled, Defray777 knows that SSE2 is supported and more complex mathematical operations are possible.
- Defray777 will also determine if the processor is capable of using AES-NI for improved encryption performance.
- As encryption begins, a ransom note will be created in each directory where files will be encrypted.
- The name of the ransom note will vary. However, from our research, the ransom notes most commonly contain a combination of exclamation points, the string “README,” and a reference to the victim name.
- Example: !!!_IMPACTED_Client_README_!!!.txt
- The file contents will be encrypted using an on-the-fly generated AES key that gets encrypted with RSA-4096 and stored in the file footer in a 512-byte block.
- The encrypted file will be renamed by appending an extension that consists of a unique victim identifier and a randomized eight-digit hexadecimal number.
- Example: .v1ct1m-1bc461ac
Specifically, the encryption mechanism consists of the following steps:
- Dynamically generate a 32-byte AES key.
- Encrypt the file with AES-256 in ECB mode using 16-byte blocks.
- Encrypt the AES key with RSA-4096 and append the 0x200 byte cipher text to the end of the encrypted file.
Encryption Exclusions
During the encryption process, Defray777 aims to encrypt as many files as possible without impacting the system’s core functionality. To accomplish this, Defray777 uses a set of excluded folders, files and file extensions that will not be encrypted during execution.
Excluded Folders:
| \windows\system32\ | \windows\syswow64\ | \windows\system\ |
| \windows\winsxs\ | \appdata\roaming\ | \appdata\local\ |
| \appdata\locallow\ | \all users\microsoft\ | \inetpub\logs\ |
| :\boot\ | :\perflogs\ | :\programdata\ |
| :\drivers\ | :\wsus\ | :\efstmpwp\ |
| :\$recycle.bin\ | :\EFSTMPWP\ | crypt_detect |
| cryptolocker | ransomware |
Table 14. Folders excluded from encryption by Defray777.
Excluded files:
| iconcache.db | thumbs.db | ransomware | ransom |
| debug.txt | boot.ini | desktop.ini | autorun.inf |
| ntuser.dat | ntldr | ntdetect.com | bootfont.bin |
| bootsect.bak |
Table 15. Files excluded from encryption by Defray777.
It is also important to note that Defray777 adds the name of the ransom note into the excluded files list.
Excluded extensions:
| .ani | .cab | .cpl | .cur | .diagcab |
| .diagpkg | .dll | .drv | .hlp | .icl |
| .icns | .ico | .iso | .ics | .lnk |
| .idx | .mod | .mpa | .msc | .msp |
| .msstyles | .msu | .nomedia | .ocx | .prf |
| .rtp | .scr | .shs | .spl | .sys |
| .theme | .themepack | .exe | .bat | .cmd |
| .url | .mui |
Table 16. Extensions excluded from encryption by Defray777.
Searching for Unmapped File Shares
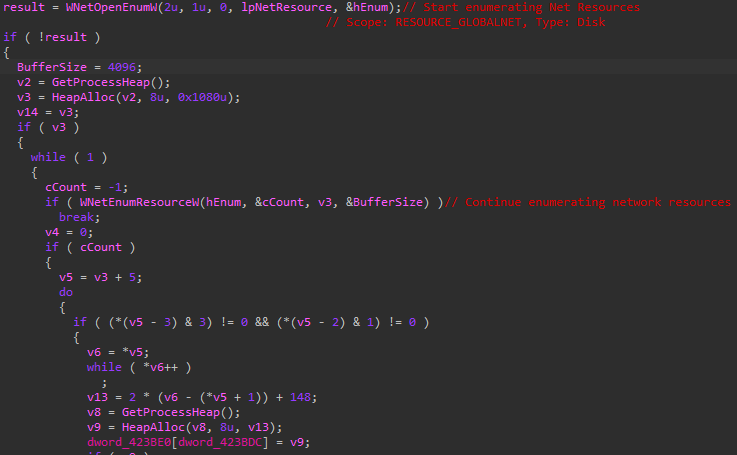
During execution, Defray777 uses WNetOpenEnumW and WNetEnumResourceW to search for file shares that may contain files that could be encrypted. This tactic has been seen amongst other ransomware variants in the wild to encrypt files that are accessible via unmapped file shares.
Anti-Forensic Measures
After all files are encrypted on the system, Defray777, like many other ransomware variants, implements common anti-forensics measures to remove as much evidence of the intrusion as possible and make it extremely difficult for the system to be recovered without a backup. Although these commands are common amongst other ransomware variants, Defray777 runs commands post-encryption, which means that when security tools alert or take action against Defray777, the files have already been encrypted.
Commands executed by Defray777:
| cipher.exe /w:[DRIVE] fsutil.exe usn deletejournal /D [DRIVE] wbadmin.exe delete catalog -quiet bcdedit.exe /set {default} recoveryenabled no bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures schtasks.exe /Change /TN "\Microsoft\Windows\SystemRestore\SR" /disable wevtutil.exe cl Application wevtutil.exe cl System wevtutil.exe cl Setup wevtutil.exe cl Security wevtutil.exe sl Security /e:false |
Table 17. Anti-forensic commands executed by Defray777.
Registry keys modified:
| \Software\Microsoft\Windows NT\CurrentVersion\SystemRestore\DisableConfig
\Software\Microsoft\Windows NT\CurrentVersion\SystemRestore\DisableSR \SOFTWARE\Policies\Microsoft\Windows NT\SystemRestore\DisableSR \SOFTWARE\Policies\Microsoft\Windows NT\SystemRestore\DisableConfig |
Table 18. Registry Keys Modified by Defray777.
Defray777’s Port to Linux
During the course of our research, we found that Defray777 ransomware has been ported over to Linux. Before Defray777, ransomware that impacted both Windows and Linux operating systems was limited to being written in Java or scripting languages such as Python. These ransomware variants would be considered cross-functional since they were written in a single language that must be installed and supported by both operating systems. Defray777’s port to Linux ensures that the ransomware has standalone executables for each platform with no external dependencies.
A ZIP archive was uploaded to a public malware repository on Oct. 17, 2020 that contained a Windows executable that was identified as a Defray777 decryptor. Additionally included in this ZIP archive was an ELF binary named decryptor64. Analysis of this binary determined it to be another Defray777 decryptor that had been ported to Linux.
Armed with the idea that there may be Linux versions of Defray777 in the wild, we began hunting in AutoFocus and quickly uncovered an ELF version of the ransomware encryptor.
Reviewing this sample further indicated that it was uploaded in August 2020. As of early October 2020, there appear to be zero detections by antivirus (AV) in VirusTotal for the Linux version of Defray777.
A deeper review of the Linux and Windows variants of Defray777 determined that the encryption and decryption processes used were nearly identical. In fact, by generating our own RSA key pair and modifying the binaries, we were able to confirm that the encryptors and decryptors for both operating systems were interchangeable.
Unlike the Windows versions, the developers didn’t seem to put any effort into protecting the Linux samples. To our surprise, the binaries we analyzed still had their symbols intact, which made reversing them quite a bit easier.
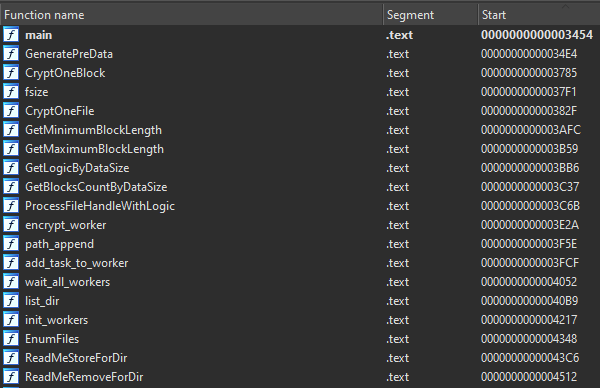
One of the biggest differences between the Windows and Linux variants is the logic that determines which files to encrypt. The Windows version will recurse the file system and encrypt anything that isn’t explicitly excluded. In contrast, the Linux variant will only encrypt directories specified in a command line argument.
Continue reading: Linking Vatet, PyXie and Defray777












 Get updates from Unit 42
Get updates from Unit 42