This post is also available in: 日本語 (Japanese)
Executive Summary
Our Unit 42 research team routinely evaluates the data from our Email Link Analysis (ELINK) system. In examining the data it collects, which are URLs extracted from emails or submitted by API, we can identify patterns and trends which help us discern prevalent web threats. This blog is the fourth (4th quarter of 2018) installment in a series of posts tracking web-based threats throughout the year, specifically statistics pertaining to malicious URLs, domains, exploit kits, CVEs, and now, phishing scams.
The key findings in this quarter’s report in summary are:
- After Q4 saw an increase in malicious URLs, ending a trend of decreasing malicious URLs starting in Q1 and continuing through Q3.
- For the first time in our tracking, the United States is not the number one country for malicious URLs: it fell to number two with France taking number one.
- The number of domains hosting malware continued the drop we saw in Q3.
- The United States once again is number one in malicious domains hosting malware.
- There was no change in the top three vulnerabilities under attack this quarter: CVE-2018-8174, CVE-2016-0189, CVE-2014-6332
- It’s also notable that these three have been the top three for three quarters now. And two of these (CVE-2016-0189, CVE-2014-6332), have been in the top three for a full year now.
- The US was number one for phishing URL distribution and phishing domains, accounting for 56% and 40% of the volume respectively.
- Microsoft account holders and customers were the number one target for phishers. Overall, technology company account holders and customers were the primary target for phishers, though DHL and Bank of America customers and account holders were also in the top ten for this quarter.
Malicious URLs/Domains
Malicious URLs
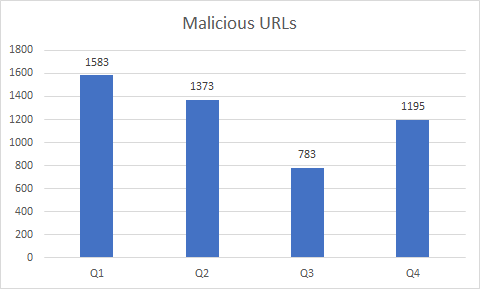
Based on the data from our ELINK system during Q4, we noticed a comeback in malicious URL links that were extracted from our data feed and analyzed. There were 1195 malicious URLs recorded during Q4, which is around 37% more than the previous quarter. The 3rd quarter of 2018 capped at 783 malicious URLs, which as you can see in Figure 1 is quite low compared to the rest of the year.
Figure 1. Malicious URLs from Q1 to Q4 2018
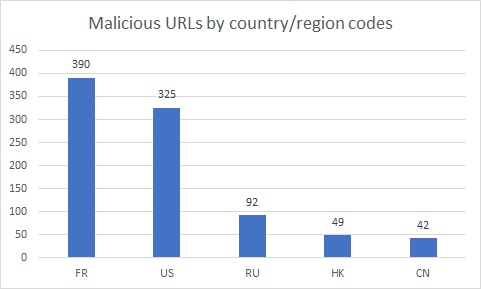
These malicious URLs have also been broken down by country/region codes. Out of the 1195 URLs, France placed highest with 390 malicious URLs. It’s the first time the United States hasn’t ranked #1 on the list. The United Kingdom, which appears in the top 5 list from Q3, plummeted to only 7 malicious URL in Q4. Please keep in mind these statistics are formulated from our ELINK system data sets, they represent a sample set of overall numbers in the wild.
Figure 2. Top 5 malicious URL hosting country/region from Q4 2018
Malicious Domains Hosting Malware
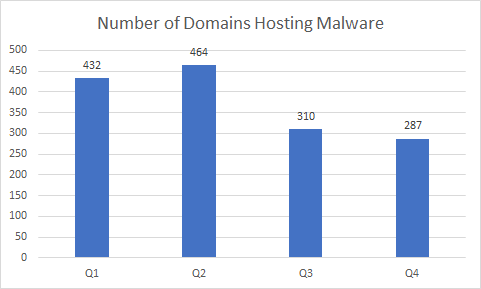
Although we observed a resurgence in malicious URL numbers, the number of domains hosting malware decreased from last quarter. From 310 malicious domains in Q3 to 287 in Q4, as seen in Figure 3 below.
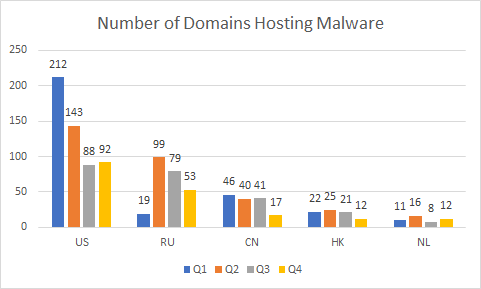
Figure 3. Malicious domains from Q1 to Q4 2018
While monitoring the domain hosting data, a pattern has emerged. Since the beginning of 2018, not only has the United States ranked #1 throughout the year, but the same 5 country/regions have remained at the top of our quarterly chart: United States, Russia, China, Hong Kong, and the Netherlands. These results may not seem surprising, especially the top 3, but it’s always interesting to see the movement of numbers throughout the quarters, these are detailed in Figure 4 below.
Figure 4. Malicious domains in 2018
The recorded CVEs in use have not changed much since the beginning of 2018. The top 3 vulnerabilities in Q4 are the same as in Q2 and Q3. Table 1 shows the rundown of the most common CVEs since Q1.
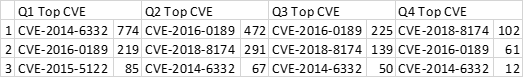 Table 1. Most triggered CVEs Q1 to Q4 2018
Table 1. Most triggered CVEs Q1 to Q4 2018
Most of the currently exploited CVEs are not new. In fact, although they didn’t make the top 3 list, the exploitation of three, over ten year old CVEs are still showing up in our data. Below is an overview of the CVEs that have been triggered in our ELINK system.
- CVE-2008-1309: The RealAudioObjects.RealAudio ActiveX control in rmoc3260.dll in RealNetworks RealPlayer Enterprise, RealPlayer 10, RealPlayer 10.5 before build 6.0.12.1675, and RealPlayer 11 before 11.0.3 build 6.0.14.806 does not properly manage memory for the (1) Console or (2) Controls property, which allows remote attackers to execute arbitrary code or cause a denial of service (browser crash) via a series of assignments of long string values, which triggers an overwrite of freed heap memory.
- CVE-2008-1472: Stack-based buffer overflow in the ListCtrl ActiveX Control (ListCtrl.ocx), as used in multiple CA products including BrightStor ARCserve Backup R11.5, Desktop Management Suite r11.1 through r11.2, and Unicenter products r11.1 through r11.2, allows remote attackers to execute arbitrary code or cause a denial of service (crash) via a long argument to the AddColumn method.
- CVE-2008-4844: Use-after-free vulnerability in the CRecordInstance::TransferToDestination function in mshtml.dll in Microsoft Internet Explorer 5.01, 6, 6 SP1, and 7 allows remote attackers to execute arbitrary code via DSO bindings involving (1) an XML Island, (2) XML DSOs, or (3) Tabular Data Control (TDC) in a crafted HTML or XML document, as demonstrated by nested SPAN or MARQUEE elements, and exploited in the wild in December 2008.
Phishing
ELINK started to support phishing detection at the end of Q3. Below are phishing detections from ELINK in Q4 2018.
URLs
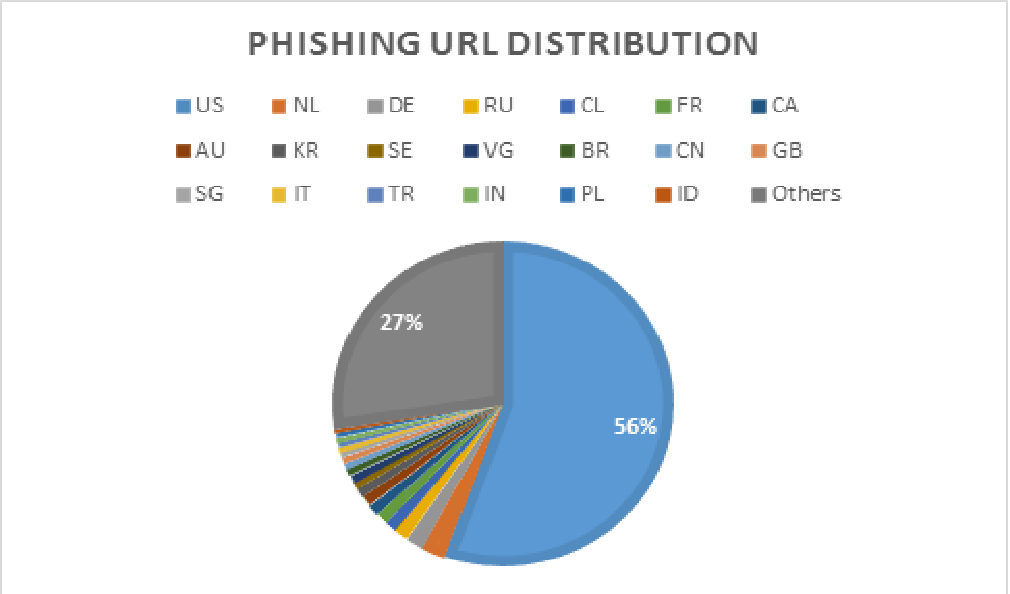
In Q4 2018, we observed 212,818 phishing URLs in total. More than half of them are hosted in the US, followed by the Netherlands, Germany, Russian, and Chile. France, which ranked #1 in our malicious URLs hosting country/region, ranked 6th in hosting phishing URLs. Figure 5 shows a breakdown of the top 20 hosting countries/regions for Phishing URLs.
Figure 5. Phishing URL distribution
Domains
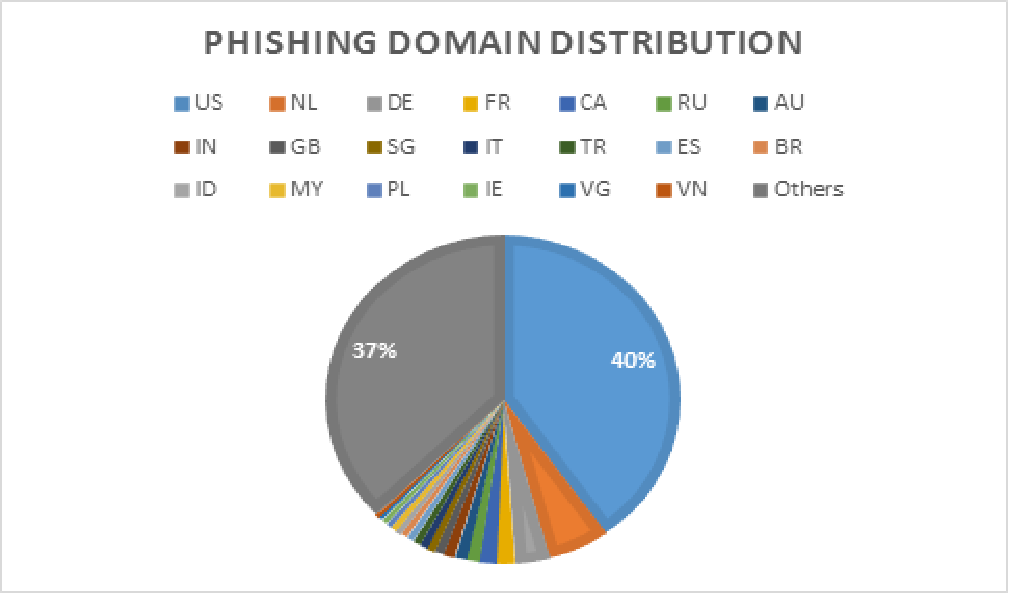
All 212,818 phishing URLs were hosted by 20,990 domains. Out of all the phishing domains monitored, a prominent 40% were hosted in United States. The top 5 countries/regions for hosting phishing domains are as follows: United States, Netherlands, Germany, France, and Canada. More details are in Figure 6 below.
Figure 6. Phishing domain distribution
Targets
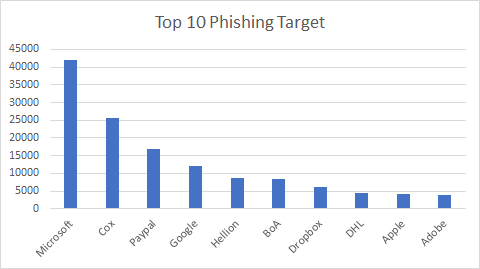
There is no doubt that phishing campaigns are rampantly spreading, ELINK captured 200 times more phishing URLs than malicious URLs. You may be curious what well-known entities these phishing scams are intended for. It may not be surprising that Microsoft is the overriding phishing target, considering there are multiple popular products/services from Microsoft, such as OneDrive, Outlook, and Office 365. Bank of America (BoA) is the only bank present in the top 10 list, with Chase second in the bank category ranking in at 15th place. More details of the top 10 phishing targets are in Figure 7 below.
Figure 7. Phishing target distribution
Case Study
The Fallout Exploit Kit, using CVE-2018-8174, is still the most active EK in Q4. A new campaign called “FindMyName” was found to deliver multiple new Azorult (data stealing/downloading malware) variants through CVE-2018-8174 (which we noted above is the number one targeted vulnerability this quarter). In this campaign several attack chains, that originated from different URLs, had the same final landing pages on the same domain (findmyname[.]pw). These new Azorult variants use advanced obfuscation techniques, such as API flooding and control flow flattening to evade anti-virus products. In addition, the samples we captured support stealing sensitive information in more browsers, applications, and cryptocurrency wallets than previous versions. We disclosed more details in this blog.
Conclusion
Looking at this quarter’s trends, we see a comeback in malicious URLs globally due to a surprisingly upsurge in France. Meanwhile, the United States remained the top hosting country/region for malicious domains.
While our ELINK system indicates 10-year-old vulnerabilities still being exploited, most of the vulnerabilities showing up were discovered within the last 5 years. There is no zero-day vulnerability attack observed this quarter, keep your software and system updated can prevent a majority of them. WildFire and PANDB both have full coverage of these malwares.
Compared to malicious URLs, the number of phishing URLs is substantially larger. They are not based on any vulnerability of software or system but based on humans being the weakest link in cybersecurity. WildFire and PANDB both have full coverage of these phishing URLs.












 Get updates from Unit 42
Get updates from Unit 42