Executive Summary
RedLine Stealer is information-stealing malware that harvests login credentials and other sensitive data from a victim's Windows host. This Wireshark quiz uses a packet capture (pcap) that “crosses a line” separating normal traffic from malicious activity. The malicious activity in this pcap is a RedLine Stealer infection from July 2023. Our pcap provides experience analyzing RedLine traffic, and we can determine what specific data was stolen from an infected Windows computer.
Anyone can participate in this quiz. To get the most benefit, participants should be familiar with Wireshark. This quiz also requires a basic understanding of IPv4 traffic. To help people gain this knowledge, we have a series of Wireshark tutorials available.
Palo Alto Networks customers receive protection from RedLine Stealer and other malware through Cortex XDR and our Next-Generation Firewall (NGFW) with Cloud-Delivered Security Services (CDSS) that includes WildFire and Advanced Threat Prevention.
| Related Unit 42 Topics | pcap, RedLine, RedLine Stealer, Wireshark, Wireshark Tutorial |
Scenario
Traffic for this quiz occurred in an Active Directory (AD) environment during July 2023. Details of the local area network (LAN) environment for the pcap follow.
Local Area Network (LAN) Details
- LAN segment range: 10.7.10[.]0/24 (10.7.10[.]1 through 10.7.10[.]255)
- Domain: coolweathercoat[.]com
- Domain controller IP address: 10.7.10[.]9
- Domain controller hostname: WIN-S3WT6LGQFVX
- LAN segment gateway: 10.7.10[.]1
- LAN segment broadcast address: 10.7.10[.]255
Quiz Questions
- What is the date and time in UTC the infection started?
- What is the IP address of the infected Windows client?
- What is the MAC address of the infected Windows client?
- What is the hostname of the infected Windows client?
- What is the user account name from the infected Windows host?
- What type of information did this RedLine Stealer try to steal?
Requirements
Participants should use Wireshark to review the pcap. We encourage people to customize their Wireshark column display before reviewing the traffic. While you should personalize Wireshark according to your specific needs, we recommend starting with changes demonstrated in our Unit 42 series of tutorials and videos.
Participants should use the latest version of Wireshark if possible, due to its feature updates and bug fixes over previous versions. We do not recommend outdated Wireshark versions like 1.x and 2.x for these quizzes.
Infection traffic often contains malware or malicious code targeting Microsoft Windows. Because of this, we recommend using Wireshark in a non-Windows environment to review the pcap for this quiz. Operating systems like BSD, Linux or macOS provide an ideal environment for Wireshark when reviewing traffic from Windows-based malware like RedLine Stealer.
Accessing the Pcap
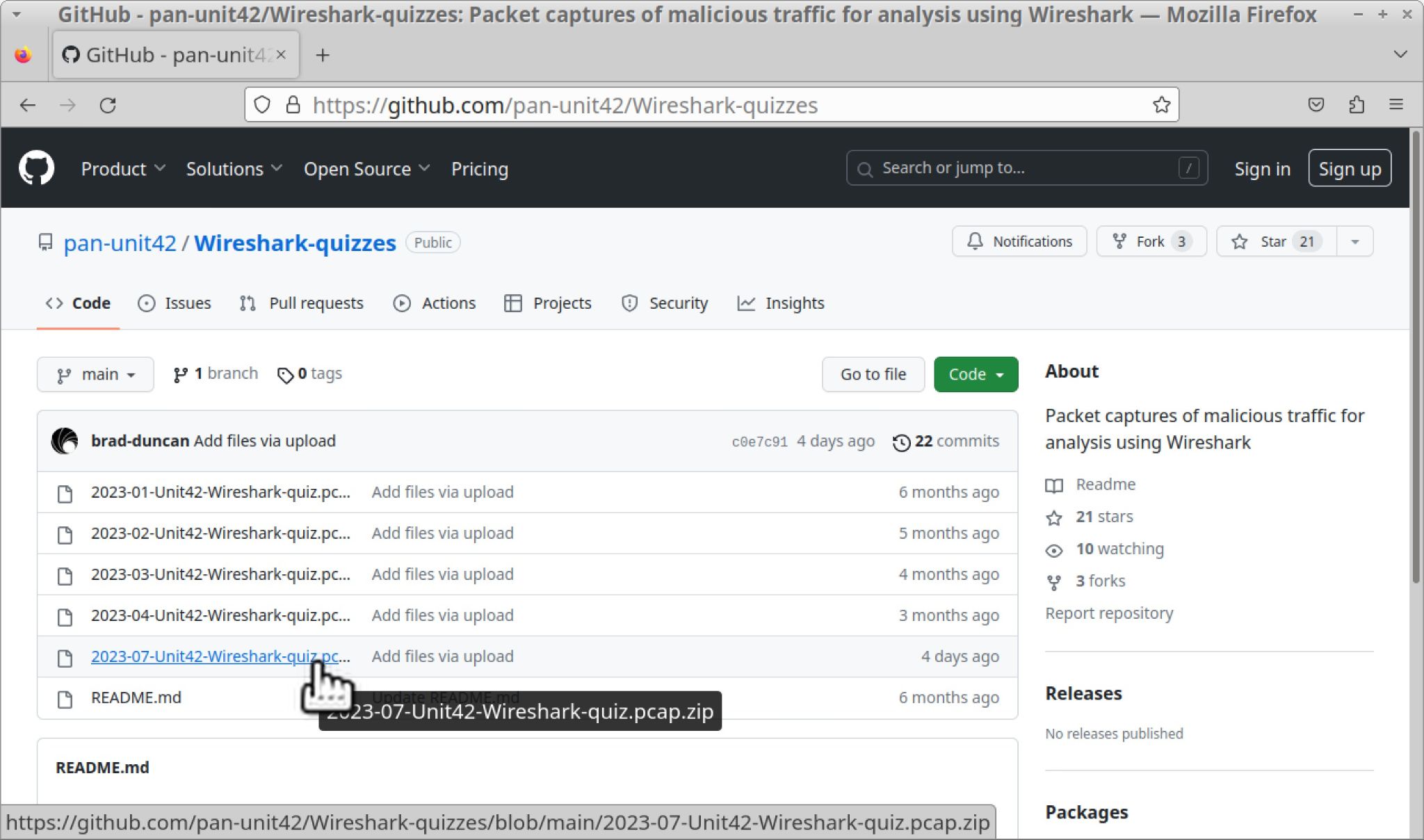
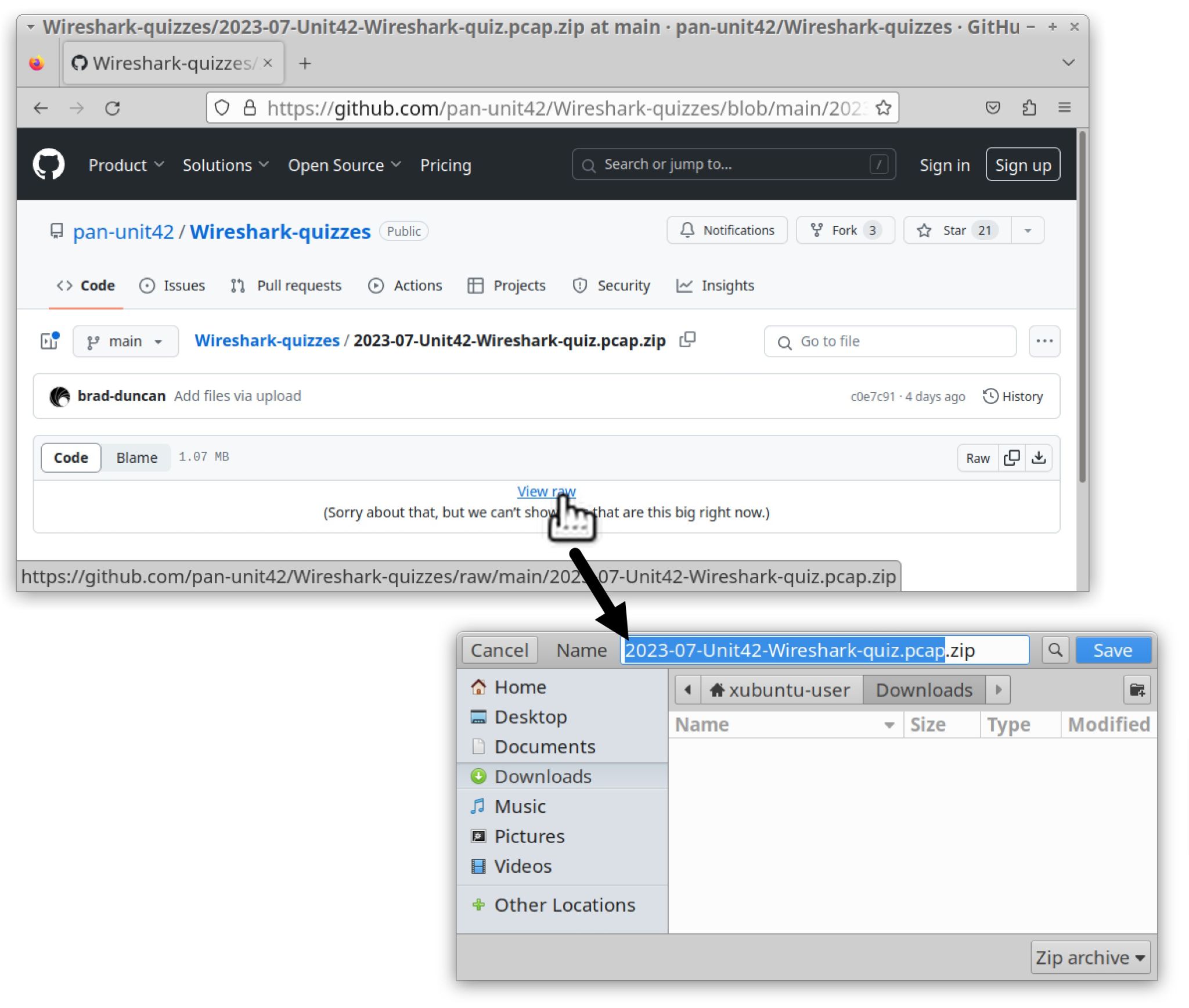
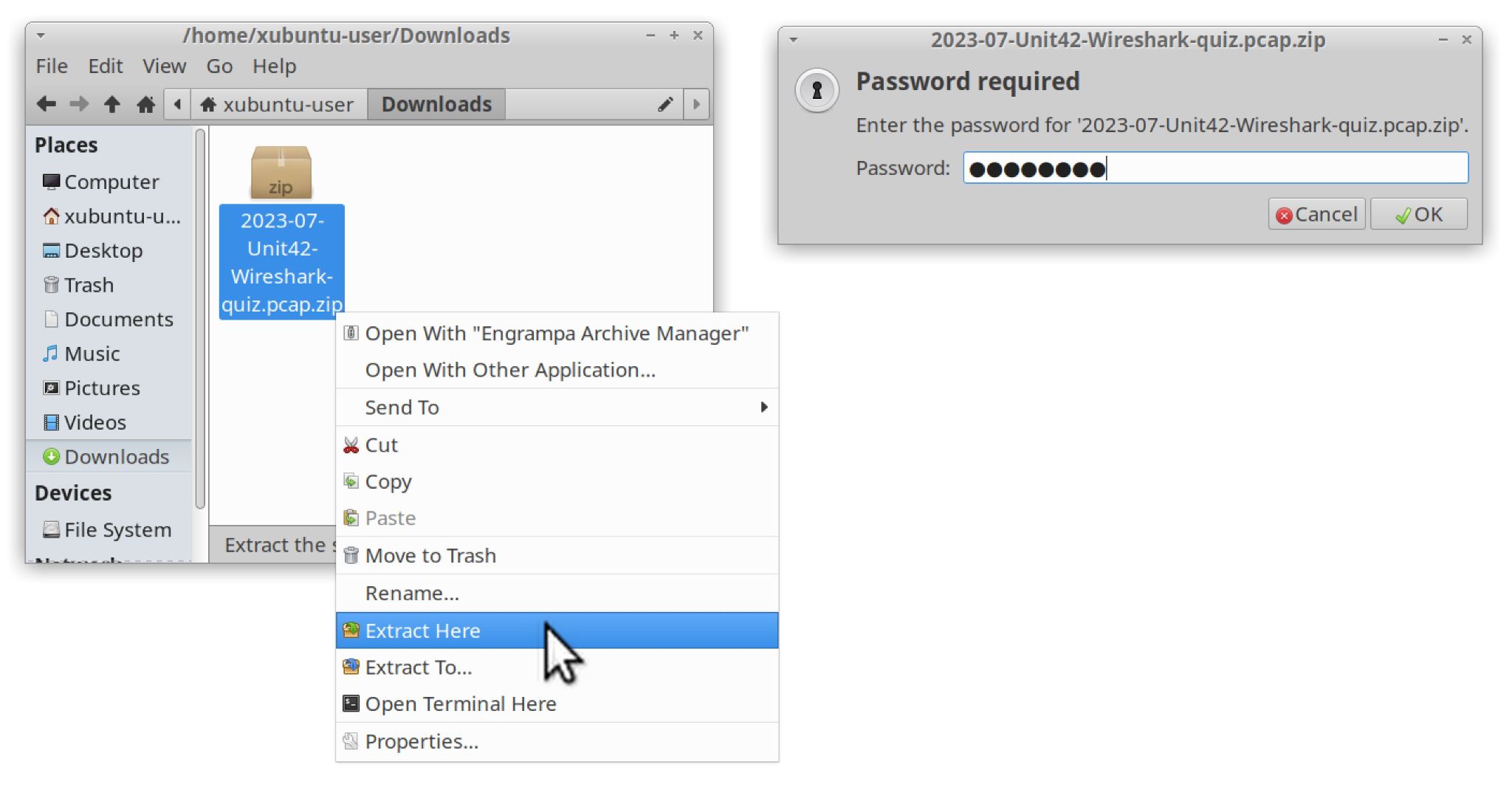
The pcap for this quiz is located in our GitHub repository as shown in Figure 1. Download the ZIP archive named 2023-07-Unit42-Wireshark-quiz.pcap.zip as shown in Figure 2. Use infected as the password to unlock the ZIP archive as shown in Figure 3.
Conclusion
RedLine Stealer is one of many information stealers within our current threat landscape. This Wireshark quiz can help participants better understand network traffic associated with a RedLine Stealer infection.
The answers to the Unit 42 Wireshark quiz for RedLine Stealer are published in a separate post.
Palo Alto Networks customers receive protection from RedLine Stealer and other malware through Cortex XDR and our NGFW with CDSS that includes WildFire and Advanced Threat Prevention.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Additional Resources
- Wireshark Tutorial: Wireshark Workshop Videos Now Available – Unit 42, Palo Alto Networks
- Unit 42 Wireshark Quiz, January 2023 – Unit 42, Palo Alto Networks
- Answers to January 2023 Unit 42 Wireshark Quiz – Unit 42, Palo Alto Networks
- Unit 42 Wireshark Quiz, February 2023 – Unit 42, Palo Alto Networks
- Answers to February 2023 Unit 42 Wireshark Quiz – Unit 42, Palo Alto Networks
- Finding Gozi: Unit 42 Wireshark Quiz, March 2023 – Unit 42, Palo Alto Networks
- Finding Gozi: Answers to Unit 42 Wireshark Quiz, March 2023 – Unit 42, Palo Alto Networks
- Cold as Ice: Unit 42 Wireshark Quiz for IcedID – Unit 42, Palo Alto Networks
- Cold as Ice: Answers to Unit 42 Wireshark Quiz for IcedID – Unit 42, Palo Alto Networks
- RedLine Stealer: Answers to Unit 42 Wireshark Quiz – Unit 42, Palo Alto Networks
- New Redline Password Stealer Malware – Proofpoint Threat Insight, March 2020
- 2023-03-02: Rig EK --> malware loader --> Redline Stealer – malware-traffic-analysis.net
- Malicious AI Tool Ads Used to Deliver Redline Stealer – Trend Micro Research, May 2023
- Do Not Cross The 'RedLine' Stealer: Detections and Analysis – Splunk Threat Research Team, June 2023








 Get updates from Unit 42
Get updates from Unit 42