The Asprox/Kuluoz malware family has a special place in our hearts at Palo Alto Networks. This botnet-related Trojan malware has evolved from its 2007 roots into a simple and yet robust mass e-mail phishing threat that is the origin of a significant percentage of Internet spam today. This post further explores trends for this malware family, based on October 2014 data from our WildFire platform.
Some Background
The modern Kuluoz is known for the following:
- High distribution volume through geolocation-associated spam e-mail templates
- Use of e-mail attachments and Web links that masquerade as document or media files
- Modular design, promoting extensibility
- Distinct, default botnet node roles of spam generator for continued botnet propagation, downloader of additional malware and distributor of generalized commercial spam
- Platform-specific malware delivery based on user agent detection
Themes for Kuluoz propagation spam have ranged across legal notices (e.g., court order), package delivery messages (e.g., FedEx, UPS, DHL), voicemail service notifications (e.g., WhatsApp), general current events (e.g., 2014 polar vortex), and online deals (e.g., free pizza from Pizza Hut) – to name a few.
October 2014 Analysis
Figure 1 depicts October 2014 WildFire sessions (individual occurrences) that were flagged as Kuluoz, broken out by day.
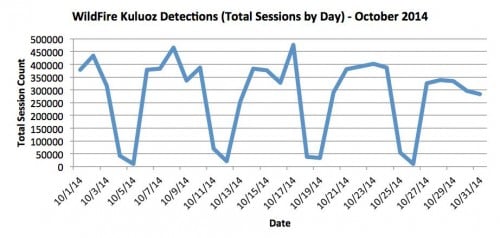
Figure 1: WildFire-detected Kuluoz sessions, by day, for October 2014
An interesting pattern emerges for significant session count valleys spaced roughly seven days apart, which are followed by major peaks two to five days out. These valleys correspond with weekends, while the peaks occur mid-week. This makes sense in the context of the standard business workweek and the broad swath of enterprises included in Kuluoz targeting.
Figure 2 displays WildFire unique Kuluoz sample counts (based on SHA256 hash) for the same period.
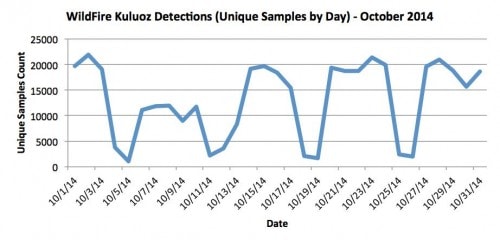
Figure 2: Unique WildFire-detected Kuluoz samples, by day, for October 2014
This second figure matches the general valleys and peaks trend for total sessions detected by WildFire. Note that this figure does not represent new/never-seen-before sample detections, but instead represents all unique Kuluoz samples detected for a given day. Kuluoz employs low-effort but effective methods of altering binaries enough to evade detection by hash alone, which significantly increases unique sample counts when comparing standard binary hashes. Accordingly, the above figure demonstrates the cumulative effect and possible escalation in unique Kuluoz sample generation, a trend previously noted by FireEye in June.
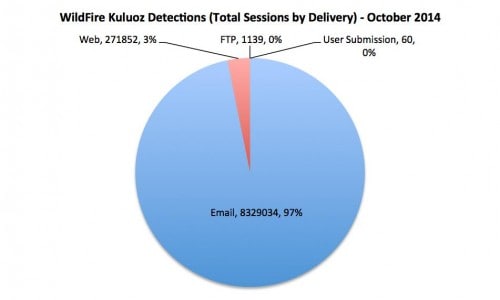
Closer inspection of WildFire session delivery/receipt for Kuluoz reveals the expected leader: e-mail/webmail (Figure 3).
Figure 3: WildFire-detected Kuluoz delivery/receipt for October 2014
Most of the remaining sessions were delivered via the Web, which includes cloud and file sharing services. A relatively small number of Kuluoz sessions leveraged File Transfer Protocol (FTP). Finally, WildFire also received a number of Kuluoz samples through user submission.
Over 98% of WildFire-detected Kuluoz filenames for October 2014 employed one of the following six themes, ordered by prevalence:
- Notice to Appear in Court
- Delta Airline Ticketing
- Purchase Order / Invoice / Shipping
- Voicemail Message
- Starbucks eGift
- Pizza Hut Coupon
Conclusion
Kuluoz continues to thrive, employing various social engineering pressure tactics to successfully propagate and serve as a bridge for other malware families.
Thorough mitigation of this threat includes several layers:
- User awareness: Awareness and training for users is a good idea to reduce the impact of any type of e-mail phishing. A number of Kuluoz variants require extra steps to be performed by a user (e.g., unzipping of a ZIP archive and then running a malicious binary). Encourage users to be wary of unexpected/unsolicited e-mails, especially those that employ any sort of pressure tactic and/or leverage the themes cited above.
- Protocol monitoring and control: Visibility into the protocols used by Kuluoz for delivery and Command and Control (HTTP, SMTP, IMAP, FTP) with structured and clearly defined response actions (most of which can and should be automated) prevent or reduce associated impacts. Palo Alto Networks Next Generation Firewall solutions offer this level of granular application monitoring and control.
- Automated analysis: Automation of static and dynamic analysis for unknown samples addresses the natural gap between the development of a variant for a threat and its coverage through signature-based technology. Anti-virus and other security control related signatures fall short. Solutions such as Palo Alto Networks WildFire platform allow for enterprises to identify new and emerging threats that remain unknown to other security controls in the environment.
- Intelligence fusion: Leveraging actionable intelligence is a cornerstone of Computer Network Defense (CND) operations. Threats such as Kuluoz rely heavily on embedded initial Command and Control (C2) communications to fully realize the potential of its role(s) within the botnet. Up-to-date feeds on malicious domains, IPs, file signatures and hashes, as well as integration of intelligence gleaned from automated solutions in the environment, enable robust security solutions that empower network defenders.












 Get updates from Unit 42
Get updates from Unit 42