This post is also available in: 日本語 (Japanese)
Executive Summary
On March 14, 2023, Microsoft released a patch for CVE-2023-23397. CVE-2023-23397 is a vulnerability in the Windows Microsoft Outlook client that can be exploited by sending a specially crafted email that triggers automatically when it is processed by the Outlook client. No user interaction is required to trigger the exploit.
Exploitation of the vulnerability will leak the targeted user’s Net-NTLMv2 hashes. This could then be used to conduct relay attacks to other systems that support NTLMv2, allowing the threat actor to authenticate as the targeted user.
Relay attacks are much more effective when the threat actor already has a foothold into the targeted network. This is because Windows New Technology LAN Manager (NTLM) authentication is commonly used within an Active Directory (AD) environment and not for services exposed to the Internet. Therefore, relaying leaked hashes remotely should be much less common.
Remote attacks will rely on cracking weak underlying credentials of the leaked Net-NTLMv2 hashes and using the cracked, cleartext credentials to manually log into externally exposed services the targeted user has access to.
The vulnerability affects all versions of Outlook for Windows. Outlook for Android, iOS, Mac, and Windows users who use Outlook on the web (formerly known as Outlook Web Application) without using the Outlook client are not affected.
| Related Unit 42 Topics | CVE-2023-23397, Threat Brief |
Details of the Vulnerability
CVE-2023-23397 is a vulnerability in Microsoft Outlook that allows a threat actor to craft a message (.msg) file with a custom PidLidReminderFileParameter property that contains a Universal Naming Convention (UNC) path pointing to an attacker controlled Server Message Block (SMB) server. The PidLidReminderFileParameter allows the message sender to set a custom notification sound for items such as meeting notifications.
Connections to the threat actor-controlled SMB server will leak the Net-NTLMv2 hashes of the targeted user. The threat actor can then use the hashes to conduct a relay attack to authenticate with other servers that support NTLMv2 authentication, or they can attempt to crack the hashes to obtain the underlying cleartext credentials.
Upon receiving this malicious message, Outlook adds an asynchronous task to play the scheduled reminder through HrAsyncPlayReminderSound, as shown in Figure 1. When playing the reminder, it will eventually call SearchPathW with the supplied file path of the sound reminder file. This triggers the SMB connection.
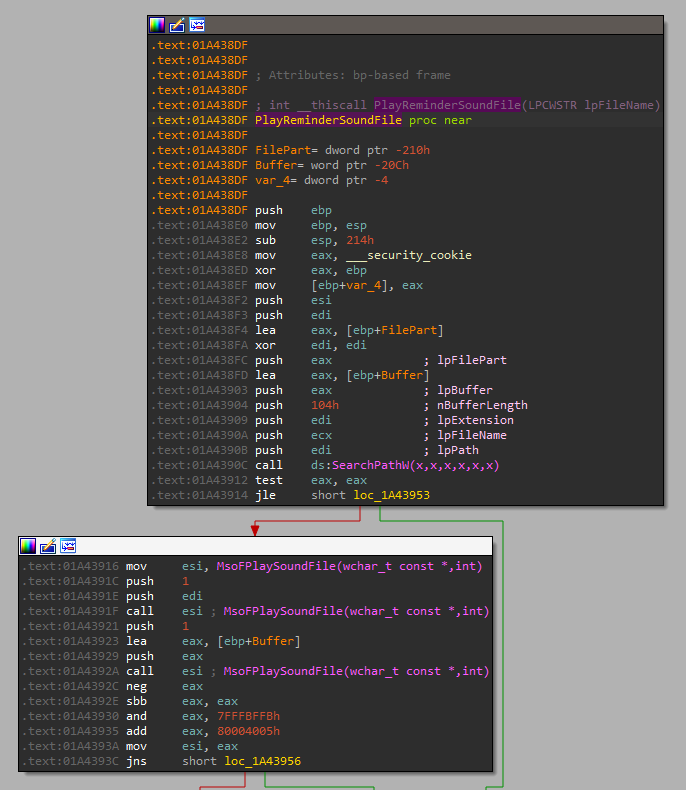
The patched code calls IsFileZoneLocalIntranetOrTrusted on the file path. This function checks if the file path is part of the device's local intranet or a trusted domain, and it should not allow external connections. This patch might be insufficient, as it still allows an internal connection if an attacker already has access to the internal network.
The vulnerability affects all versions of Outlook for Windows. Outlook for Android, iOS, Mac, and Windows users who use Outlook on the web (formerly known as Outlook Web Application) without using the Outlook client are not affected. The attack only requires that the targeted user receive the message. No user interaction is required to trigger the exploit.
If the threat actor has already established a foothold on the internal network, exploitation of CVE-2023-23397 is trivial and NTLMv2 relay attacks will likely allow for effective lateral movement within the environment as well privilege escalation.
Remote exploitation is technically possible, but should be much more difficult unless the underlying credentials are weak and are easily cracked. This is because conducting NTLM relay attacks require access to servers that support NTLMv2 authentication. We are not currently aware of any external services that support NTLMv2 authentication, and Microsoft recommends denying incoming NTLM traffic to the domain for this very reason.
Outlook for Web (previously known as Outlook Web Application) does not support NTLM authentication. However, it does support Active Directory Federated Services (AD FS). According to Microsoft, “it is possible that a federated identity provider may be susceptible.”
Current Scope of the Attack
Microsoft has stated that they have traced evidence of potential exploitation of this vulnerability back to April 2022. At this point, observed attacks have been limited to threat actors attributed to Russia targeting Ukrainian infrastructure.
Interim Guidance
Microsoft provided guidance to aid organizations in hunting for indicators of compromise or failed exploitation attempts. Microsoft’s guidance also provided mitigation measures for organizations that might not be able to implement the patch.
Microsoft has provided a script to hunt for messages where the PidLidReminderFileParameter parameter is set. They also provided guidance on hunting for outbound SMB connections, WebDAV connection attempts, and review of Exchange Server and SMBClient logs for evidence of suspicious activity.
Microsoft’s mitigation strategy, for those who cannot patch, includes adding privileged accounts to the Protected Users Group and blocking outbound SMB connections. Cortex XDR and XSIAM customers should upgrade to XDR Agent version 8.0, use a content version higher than 910-49200, and enable the Advanced API monitoring feature to get reporting capabilities.
Unit 42 Managed Threat Hunting Queries
The Unit 42 Managed Threat Hunting team continues to track any attempts to exploit these CVEs across our customers, using Cortex XDR and the XQL queries below. Cortex XDR customers can also use these XQL queries to search for signs of exploitation.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
// Description: WebDAV connection attempt to public IP address. // Note: False positives may result from legitimate activities. config case_sensitive = false | dataset = xdr_data | filter event_type = PROCESS and actor_process_image_name = "svchost.exe" and action_process_image_name = "rundll32.exe" and action_process_image_command_line contains "davsetcookie" | alter webdav_address = arrayindex(regextract(action_process_image_command_line, ":\/\/(.*?)[ \/]"), 0) | alter webdav_address_is_ip = if(webdav_address ~= "^((25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.){3}(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)$", "true", "false") | filter webdav_address_is_ip = "true" | filter incidr(webdav_address, "10.0.0.0/8") != true and incidr(webdav_address, "192.168.0.0/16") != true and incidr(webdav_address, "172.16.0.0/12") != true | fields actor_process_image_name, action_process_image_command_line, webdav_address, webdav_address_is_ip |
Conclusion
Palo Alto Networks highly recommends applying Microsoft’s patch for the Outlook client software. If you can’t apply the patch, follow Microsoft's guidance to protect your organization until patching is convenient. Palo Alto Networks and Unit 42 will continue to monitor the situation for updated information, release of proof-of-concept code and evidence of more widespread exploitation.
Palo Alto Networks Product Protections for CVE-2023-23397
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Next-Generation Firewalls and Prisma Access With Advanced Threat Prevention
Next-Generation Firewalls (PA-Series, VM-Series, and CN-Series) and Prisma Access with the Advanced Threat Prevention subscription can automatically block sessions related to CVE-2023-23397 using Threat ID 93584 (Application and Threat content update 8687).
Cortex XSOAR
The Cortex XSOAR CVE-2023-23397 - Microsoft Outlook EoP (Elevation of Privilege) pack includes an automated playbook that helps collect indicators, identify suspicious emails and process them. It also uses Microsoft's PowerShell hunting script, which allows for locating and deleting suspicious emails. The playbook also provides the mitigations and workarounds published for this vulnerability.
Cortex XDR and XSIAM
Cortex XDR running agent version 8.0, with content version 910-49200, and with Advanced API Monitoring enabled, detects the exploitation of CVE-2023-23397 by monitoring the behavior of outlook.exe process. Every time a reminder is played with a sound file path from UNC, an alert will be triggered, with details of the remote path.
Prisma Cloud
The Windows Outlook Client is an end user application and not an application associated with cloud or container operations. It is not recommended to run a Windows Outlook Client in a cloud or container environment. Any occurrence of a Windows Outlook Client operating within a cloud or container environment should be considered extremely suspicious.
Prisma Cloud does not detect CVE-2023-23397 vulnerabilities, however Prisma Cloud can detect the occurrence of a Windows Outlook Client running within cloud or container environments.
Indicators of Compromise
The following indicators were provided by Microsoft.
Several malicious samples have been uploaded to VirusTotal and a signature has been created that identifies potentially malicious messages associated with exploitation of CVE-2023-23397. VirusTotal subscribers can review those results.
Known IP addresses associated with exploitation of this vulnerability in the above VirusTotal results are listed below. Note: These IP addresses were assessed by Microsoft Threat Intelligence to be compromised infrastructure.
- 101.255.119[.]42
- 213.32.252[.]221
- 168.205.200[.]55
- 185.132.17[.]160
- 69.162.253[.]21
- 113.160.234[.]229
- 181.209.99[.]204
- 82.196.113[.]102
- 85.195.206[.]7
- 61.14.68[.]33












 Get updates from Unit 42
Get updates from Unit 42