Unit 42 released details about a vulnerability that affects Android devices running operating systems older than 8.0 Oreo. The vulnerability leaves Android users at risk of falling victim to an Android Toast Overlay attack. Patches are available that fix this vulnerability, so Android users should get the latest updates as soon as possible.
How it Works
The vulnerability affects the Toast feature on Android devices, an Android feature that allows display messages and notifications of other applications to “pop up,” and allows an attacker to employ an overlay attack.
An overlay attack happens when an attacker places a window over a legitimate application on the device. Users will interact with the window, thinking they are performing their intended function, but they are actually engaging with the attackers overlay window and executing the attacker’s desired function. You can see an example of how this would work in Figure 1.
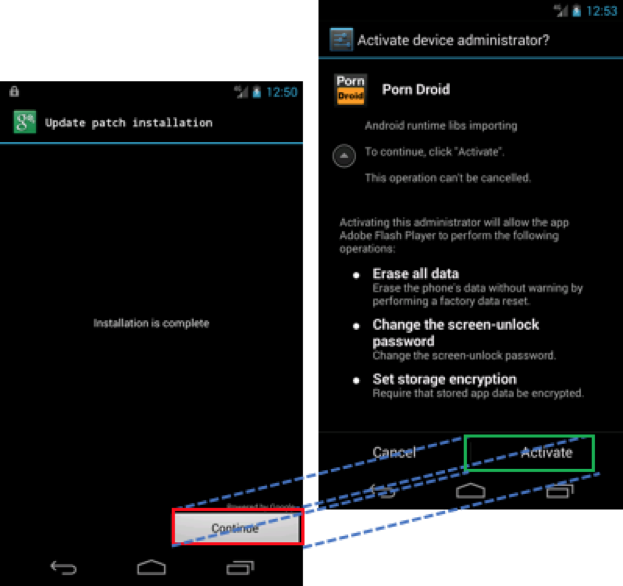
Figure 1: Bogus patch installer overlying malware requesting administrative permissions
This interaction can install malware or malicious software on the device, grant malware full administrative privileges or lock the user out and render the device unusable.
In the past successful overlay attacks were typically dependent on two conditions:
- The malicious application must be downloaded from Google Play.
- The malicious application must explicitly request permissions from the user to enable the “draw on top” functionality, allowing the application to display something on the window even if the application is not in the foreground.
However, with this particular vulnerability, these conditions are no longer required for a successful attack. This means that attackers can use this vulnerability in apps users get from places other than Google Play. And when they install these malicious apps, they don’t have to ask for the “draw on top” permission.
How to Defend Against It
Keeping devices updated is a general security best practice. The Android Toast Overlay attack specifically targets outdated devices using versions prior to 8.0. In order to defend against the Android Toast Overlay attack, update all Android devices to the latest version. Additionally, avoid downloading malicious applications by only downloading from the Google Play store is another best practice you should always follow.












 Get updates from Unit 42
Get updates from Unit 42