This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers observed interesting attack trends from August-October 2020. Despite a surge in scanner activities and HTTP directory traversal exploitation attempts, CVE-2012-2311 and CVE-2012-1823, which were the most commonly exploited vulnerabilities in the wild in early summer 2020, are no longer at the top of that list. Several new critical exploits, including but not limited to CVE-2020-17496 and CVE-2020-25213, have emerged and were being utilized at a constant and concerning rate as of fall 2020. To complicate matters, malicious actors are well aware that new exploits aren’t always needed to get the job done. Based on observations of malicious traffic for the designated three months, weaponized ThinkPHP vulnerabilities like CVE-2018-20062 and CVE-2019-9082 had become attackers’ new favorite method of exploit.
In the following sections, we dive deep into exploit analysis, attack origin and attack category distribution, in addition to the spiking activities of scanners and HTTP directory traversal attacks.
While cybercriminals will never cease their malicious activities, Palo Alto Networks customers are protected from the attacks discussed here by the Next-Generation Firewall.
Data Collection
By leveraging Palo Alto Networks Next-Generation Firewalls as sensors on the perimeter, Unit 42 researchers have been able to isolate malicious activities from benign traffic from August-October 2020. The malicious traffic is then further processed based on metrics such as IP addresses, ports and timestamps. This ensures the uniqueness of each attack session and thus eliminates potential data skews. The researchers then correlate the refined data with other attributes to infer attack trends over time and get a picture of the threat landscape.
How Severe Were the Attacks?
Out of 3,092,127 verified attack sessions observed, there were 656 unique threat triggers.
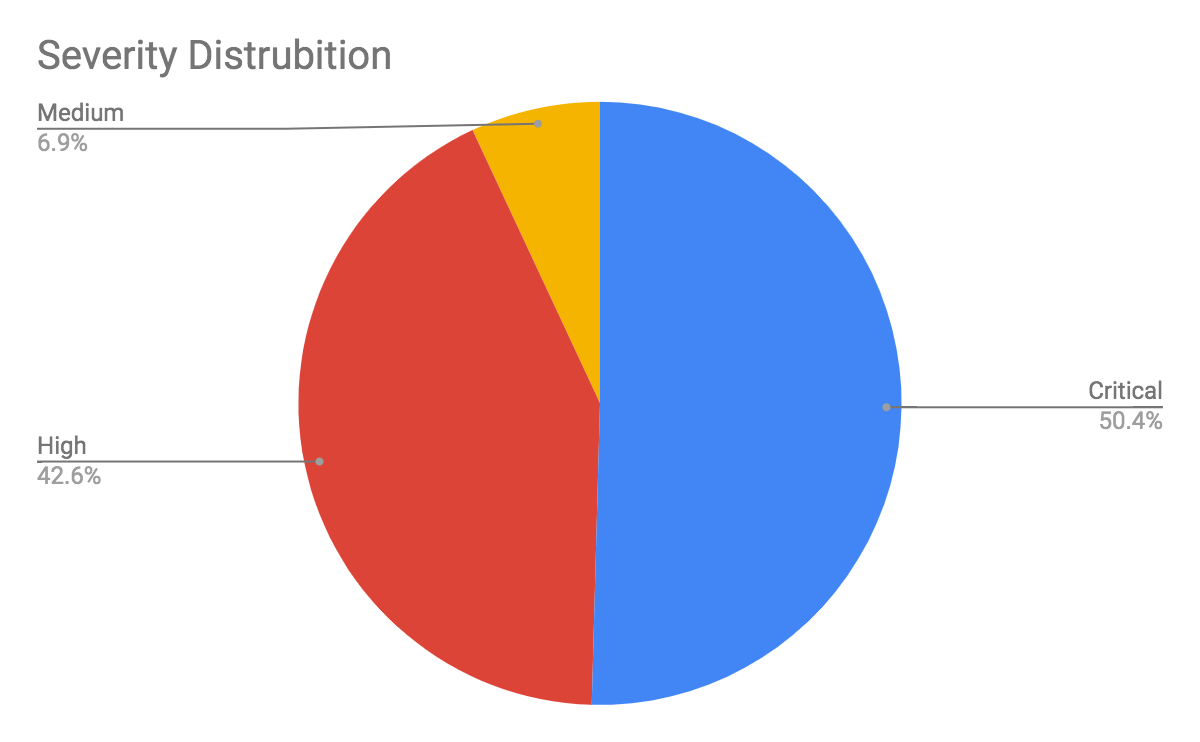
We only consider exploitable vulnerabilities with a severity rating above medium (based on the CVSS v3 Score) as a verified attack. Table 1 shows the session count and ratio of attacks with different vulnerability severities.
| Severity | Session Count | Ratio |
| Critical | 1,559,512 | 50.4% |
| High | 1,317,901 | 42.6% |
| Medium | 214,714 | 6.9% |
Table 1. Attack severity distribution ratio in August-October 2020
Exploiting vulnerabilities with high and critical severity levels is trending upward, as shown in Table 1. Not only are these exploits destructive in nature, they are also crucial to weaponizing vulnerabilities against popular products that are already part of the ecosystem. In the next section, we highlight the top five attacks that we believe are noteworthy in terms of exploitability and impact.
Latest Attack Analysis
Out of all severe attacks that we monitored, the following five exploits are the most intriguing to us. These exploits received a lot of media coverage because they had already been exploited in the wild before a patch was made available or were abused soon after the announcement of the security advisory. In addition to this attention, the reasons these exploits are in the top five attacks category are their critical severity level and their overall prevalence in 2020. These are indications that attackers are quick and efficient in adapting new tools and tactics to compromise their targets of interest. We rate the exploits below as the top five recent vulnerabilities that we captured in the wild, based on 80,528 incidents which are related to new attacks from August-October.
1. vBulletin Remote Code Execution Vulnerability
- CVE Number: CVE-2020-17496
- Severity: Critical
We captured malicious sessions related to vBulletin Remote Code Execution Vulnerability. The vendor is widely used and the severity is critical. We published research on CVE-2020-17496 in September 2020.
2. WordPress File Manager Plugin Remote Code Execution Vulnerability
- CVE Number: CVE-2020-25213
- Severity: Critical
WordPress has a remote code execution vulnerability in the wp-file-manager plugin, which can write arbitrary PHP code into a specific directory.
3. Nette Code Injection Vulnerability
- CVE Number: CVE-2020-15227
- Severity: Critical
Nette is a PHP/Composer MVC framework. It is vulnerable to code injection attacks with specific URL parameters. This vulnerability is critical, which will lead to remote code execution.
4. Artica Web Proxy SQL Injection Vulnerability
- CVE Number: CVE-2020-17506
- Severity: Critical
Artica Web Proxy is a firewall software that is vulnerable to a SQL injection of the api key parameter in fw.login.php. The vulnerability can be used to bypass Artica and gain administrator privileges through SQL injection vulnerability.
5. Oracle WebLogic Server Remote Code Execution Vulnerability
- CVE Number: CVE-2020-14882; CVE-2020-14883; CVE-2020-14750
- Severity: Critical
Oracle WebLogic Server has a remote code execution vulnerability, which could lead to critical security issues. This flaw has a low attack complexity and is highlighted as “easily exploitable.”
Overall Attack Analysis
The following exploits, shown in Table 2, were the most popular from August-October 2020 in terms of volume.
| CVE Number | Vulnerability | |
| 1 | CVE-2017-9841 | PHPUnit Remote Code Execution Vulnerability |
| 2 | CVE-2019-9082 | ThinkPHP Remote Code Execution Vulnerability |
| 3 | CVE-2019-12725 | Zeroshell Remote Command Execution Vulnerability |
| 4 | CVE-2019-16759 | vBulletin Remote Code Execution Vulnerability |
| 5 | CVE-2018-19986, CVE-2019-19597 | D-Link Remote Command Execution Vulnerability |
| 6 | CVE-2018-10561, CVE-2018-10562 | GPON Home Routers Remote Code Execution Vulnerability |
| 7 | CVE-2020-17496 | vBulletin Remote Code Execution Vulnerability |
| 8 | CVE-2018-20062 | ThinkPHP Remote Code Execution Vulnerability |
| 9 | CVE-2018-7600 | Drupal Core Remote Code Execution Vulnerability |
| 10 | CVE-2020-15415, CVE-2020-14472, CVE-2020-8515 | DrayTek Vigor Remote Command Injection Vulnerability |
Table 2. Top CVEs in August-October 2020
1. PHPUnit Remote Code Execution Vulnerability
- CVE-2017-9841
Exposure of the /vendor endpoint allows remote attackers to gain arbitrary PHP code execution on the target. This vulnerability affects all 4.x versions before 4.8.28 and 5.x versions before 5.6.3.
2. ThinkPHP Remote Code Execution Vulnerability
- CVE-2019-9082
There’s a remote code execution vulnerability in the ThinkPHP framework due to the lack of validation of the input. The ThinkPHP framework with versions < 3.2.4 suffers from a remote command execution vulnerability due to insufficient check of the controller name in the URL.
3. Zeroshell Remote Command Execution Vulnerability
- CVE-2019-12725
There’s a remote code execution vulnerability in ZeroShell version 3.9.0. By wrapping the payload in new-line characters and placing the resulting payload in the x590type HTTP parameter, the attacker can achieve arbitrary code execution on the victim’s machine.
4. vBulletin Remote Code Execution Vulnerability
- CVE-2019-16759
vBulletin version 5.0.0 through 5.5.4 is susceptible to remote command execution due to lack of validation of the HTTP parameter widgetConfig[code].
5. D-Link Remote Command Execution Vulnerability
- CVE-2018-19986
Both D-Link DIR-818LW Rev.A 2.05.B03 and DIR-822 B1 202KRb06 devices are susceptible to a command injection vulnerability due to insufficient validation of the HTTP parameter RemotePort. An attacker can inject shell metacharacters and achieve arbitrary command execution.
- CVE-2019-19597
There’s a remote command execution vulnerability in D-Link DAP-1860 devices due to insufficient input sanitization in the HNAP_Auth HTTP header value. An attack can inject shell metacharacters and achieve arbitrary code execution.
6. GPON Home Routers Remote Code Execution Vulnerability
- CVE-2018-10561
The vulnerable versions of Dasan GPON routers are susceptible to authentication bypass because they don’t properly handle the URL. This vulnerability is often used in conjunction with CVE-2018-10562 to maximize the impact.
- CVE-2018-10562
There is a command injection vulnerability in Dasan GPON routers. The vulnerable versions don’t sanitize the dest_host parameter, resulting in dire consequences. The router saves ping results in /tmp and lurks the user to revisit it.
7. vBulletin Remote Code Execution Vulnerability
- CVE-2020-17496
There is a remote command execution vulnerability in vBulletin 5.5.4 through 5.6.2 via crafted subWidgets data in an ajax/render/widget_tabbedcontainer_tab_panel request.
NOTE: This issue exists because of an incomplete fix for CVE-2019-16759.
8. ThinkPHP Remote Code Execution Vulnerability
- CVE-2018-20062
A specifically crafted value in the filter HTTP parameter can result in arbitrary code execution in the ThinkPHP framework. This bug affects versions <= 5.0.23.
9. Drupal Core Remote Code Execution Vulnerability
- CVE-2018-7600
Drupal allows remote attackers to execute arbitrary code due to an issue that affects multiple subsystems. It is caused by module misconfigurations.
10. DrayTek Vigor Remote Command Injection Vulnerability
- CVE-2020-15415
On DrayTek Vigor3900, Vigor2960 and Vigor300B devices before 1.5.1, shell metacharacters via cgi-bin/mainfunction.cgi/cvmcfgupload allow remote command execution in a filename when the text/x-python-script content type is used.
- CVE-2020-14472
There are some command injection vulnerabilities in the mainfunction.cgi file on Draytek Vigor3900, Vigor2960 and Vigor 300B devices before 1.5.1.1.
- CVE-2020-8515
DrayTek Vigor2960 1.3.1_Beta, Vigor3900 1.4.4_Beta, Vigor300B 1.3.3_Beta, 1.4.2.1_Beta and 1.4.4_Beta allow remote code execution as root via shell metacharacters to the cgi-bin/mainfunction.cgi URI without authentication.
In addition to vulnerabilities with specific CVE numbers assigned, we also capture other vulnerabilities that occur with high frequency. Below are the top five:
- ThinkCMF local file inclusion vulnerability.
There’s a file inclusion vulnerability in ThinkCMF that can also result in remote code execution. This bug affects ThinkCMF with versions <= 2.2.3.
- D-Link DSL-2750B OS command injection vulnerability.
D-Link DSL-2750B router is susceptible to a command injection vulnerability, which Mirai and its variants often abuse for infection and propagation.
- MVPower DVR unauthenticated command execution vulnerability.
Mirai and its variants are found to exploit this command execution vulnerability in MVPower DVR devices for the purpose of infection.
- Zyxel EMG2926 router command injection vulnerability.
A lack of parameter validation in Zyxel EMG2926 routers results in a remote command vulnerability. It’s also one of the vulnerabilities being exploited by Mirai malware.
- Netgear DGN Device remote command execution.
It’s an unauthenticated remote command execution resulting from the lack of input sanitization in syscmd function of setup.cgi. This vulnerability exists in Netgear DGN devices DGN1000 (for those with firmware version < 1.1.00.48) and DGN2200 v1.
Attack Category Distribution
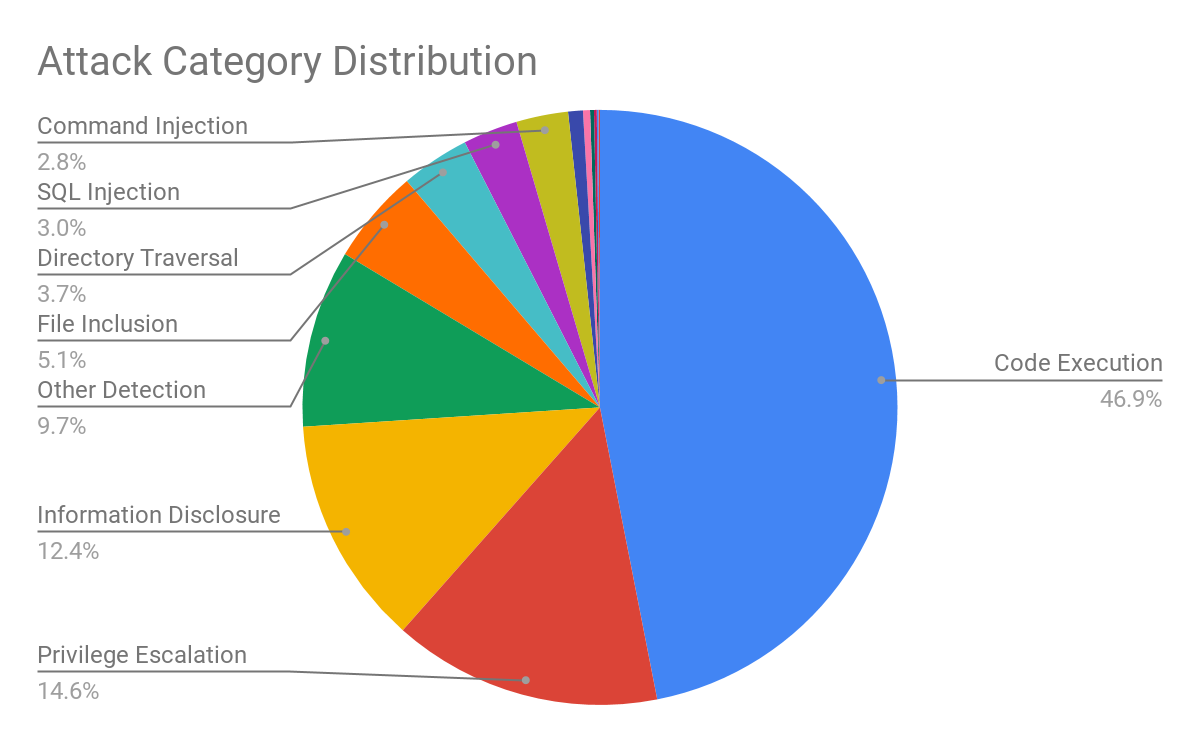
Figure 2 shows the attack category distribution. As we would like to know the details on exploitability and accessibility, we calculate the triggers by classifying the attack category. 46.9% of the attacks are code execution, which means this category still represents high-risk exposure to the network. 14.6% of the attacks can be considered privilege escalation and 12.4% are information disclosure attacks, which means the attackers are continuously attempting to gain greater access and establish an exploit chain leading to more powerful attacks such as code execution.
HTTP Directory Traversal Attacks
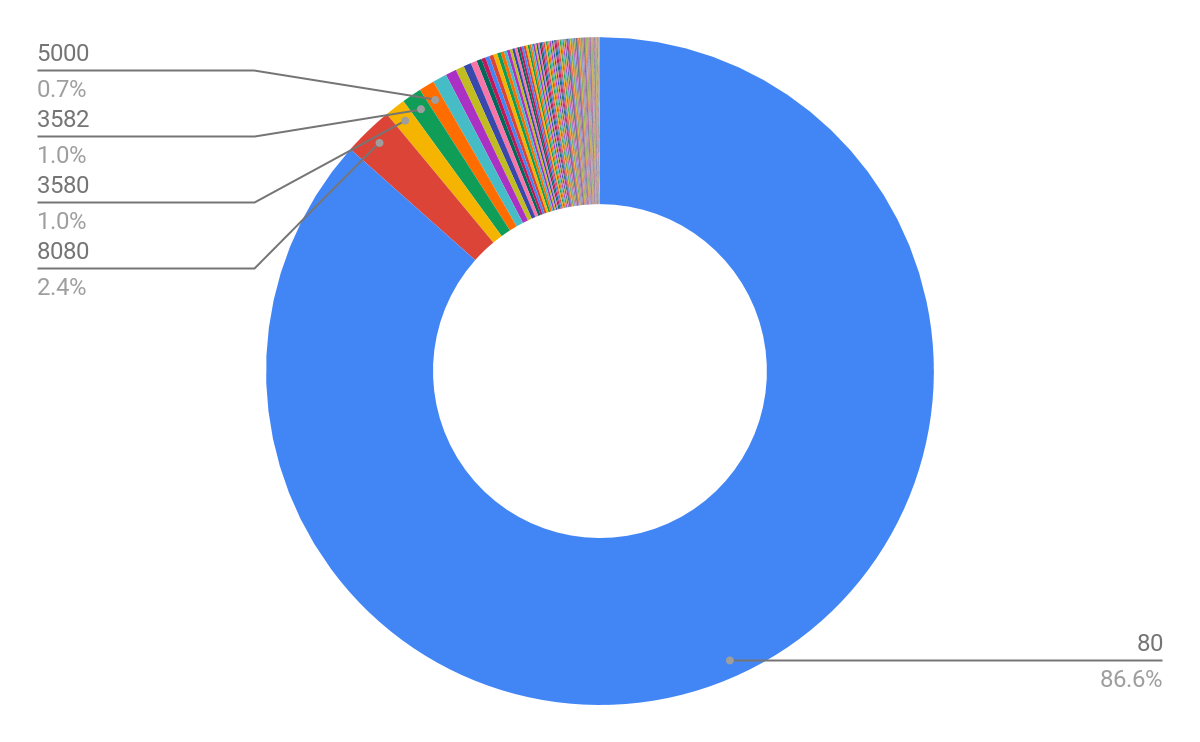
In contrast to what was observed in early summer 2020, we identified large-volume attack attempts (~500K) that exploit HTTP directory traversal vulnerabilities. Although this type of attack is one of the most commonly seen malicious behaviors in network traffic, such high volume is still rare to observe in the real world.
We first listed the top 10 destination ports attacked by the directory traversal. Most of the exploitation attempts are targeting the widely used HTTP port numbers 80 (86.6%) and 8080 (2.4%).
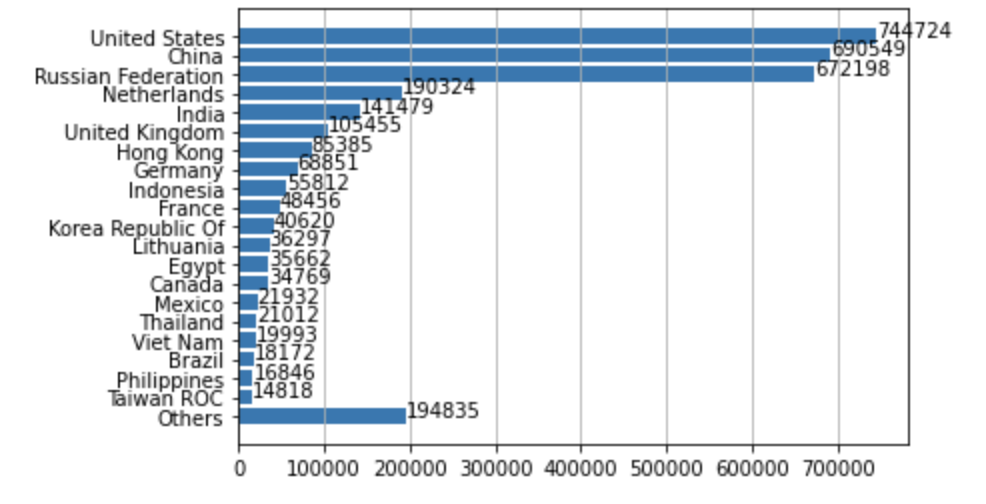
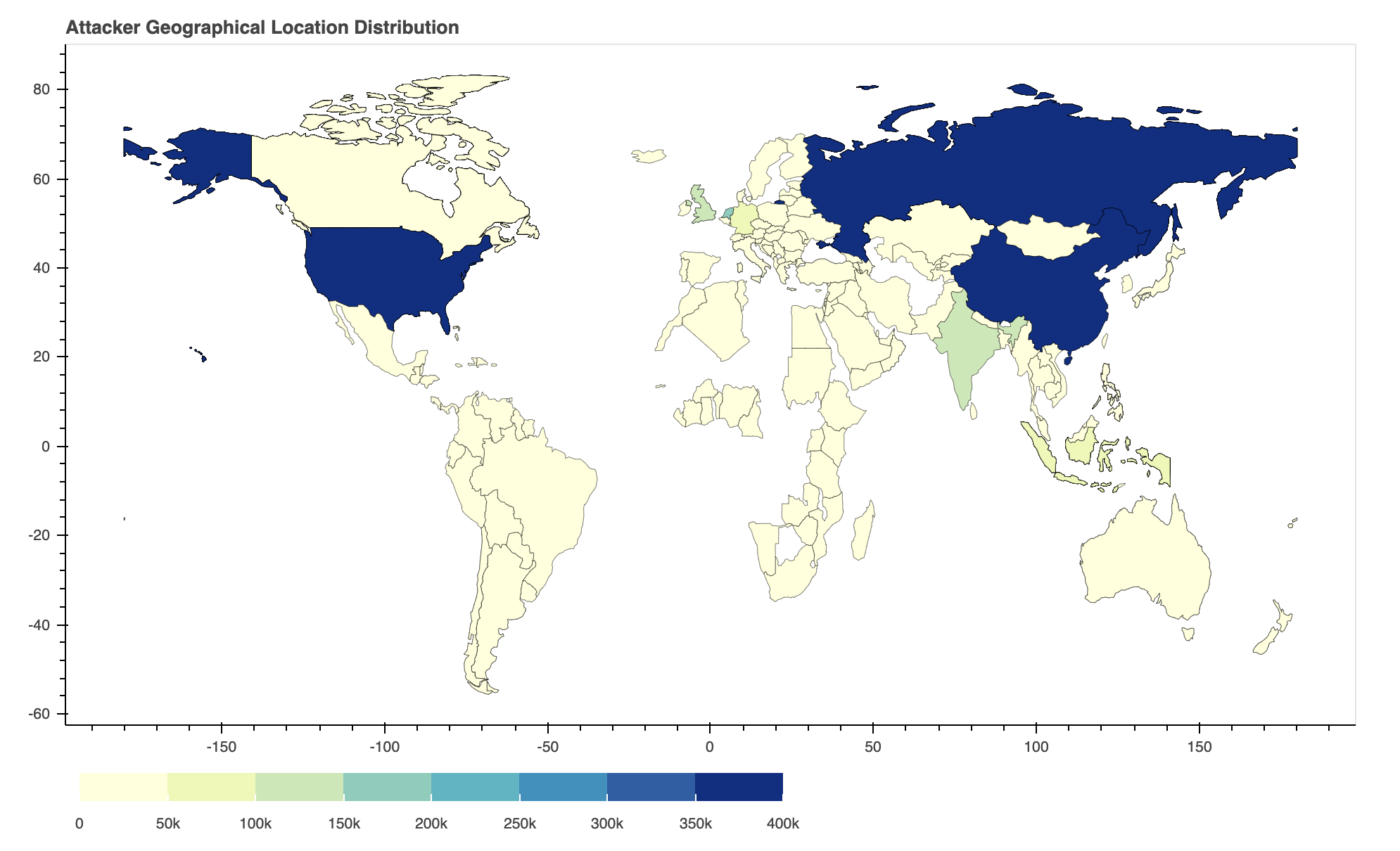
Where Did the Attacks Originate?
After identifying the region from which each network attack originated, we discovered that, by far, the largest number of them originated from the United States, followed by China and Russia. This may be in part due to the large population of the United States, China and Russia, as well as the high amounts of internet use in those regions.
Conclusion
Taken together, our data shows that attackers prioritize exploits that are both severe and easily deployed, likely in search of high-impact, low-effort attacks. While they keep ready-made weaponized exploits handy, attackers will make a concerted effort to update their arsenal whenever information about newly released vulnerabilities and the associated proofs-of-concept become available. This underscores the need for organizations to promptly patch their systems and implement security best practices.
Mitigations include:
- Run a Best Practice Assessment to identify where your configuration could be altered to improve your security posture.
- Continuously update your Next-Generation Firewalls with the latest Palo Alto Networks Threat Prevention contents (e.g versions 8366-6505 and above).












 Get updates from Unit 42
Get updates from Unit 42