Executive Summary
Our Email Link Analysis (ELINK) system is routinely reviewed by our Unit 42 research team. In examining the data it collects, patterns and trends are discovered which helps us discern prevalent web threats. This blog is the third (3rd quarter of 2018) in a series of posts tracking web-based threats throughout the year, specifically statistics pertaining to malicious URLs, domains, exploit kits, and CVEs.
During Quarter 3 (Q3), July – September, a notable shift occurred with the malicious URL and domain data; there was a significant drop in the number of malicious URLs as well as a drop in malicious domains that will be discussed below. In addition, we will be covering an interesting malicious Flash SWF that exploits CVE-2015-5119.
URLs
Based on our analysis of data from Q3 of 2018, we’ve observed a reduction in malicious URLs. The total number dropped around 40% from Q2. As you can see below in Figure 1, Q1 had the highest number of malicious URLs thus far, coming in at 1583. The total for Q2 was much less with 1373 seen, making Q3, with 783 recorded malicious URLs, an overall sizable drop.
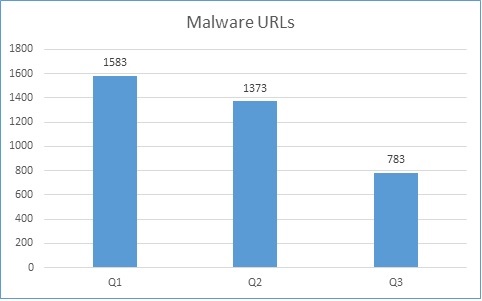 Figure 1. Malware URLs from Q1 to Q3 2018
Figure 1. Malware URLs from Q1 to Q3 2018
These malicious URLs have also been broken down by countries. Out of the 783 URLs, the United States still dominates the top 5 list of hosting countries with 331 malicious URLs recorded as shown below in Figure 2. The top three are consistent in ranking with our Q2 analysis that can be seen here.
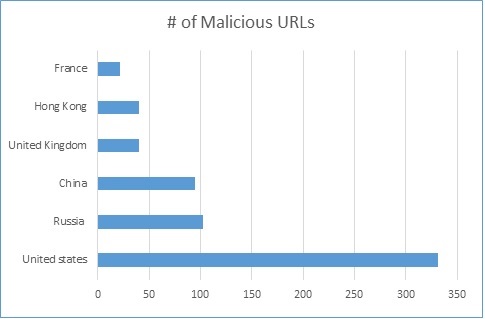 Figure 2. Top 5 malicious URL hosting countries from Q3 2018
Figure 2. Top 5 malicious URL hosting countries from Q3 2018
Domains
Although not as drastic of a decline in numbers as malicious URLs, the number of malware hosting domains has also decreased from last quarter. From 464 malware hosting domains in Q2 to 310 in Q3 as seen in Figure 3 below.
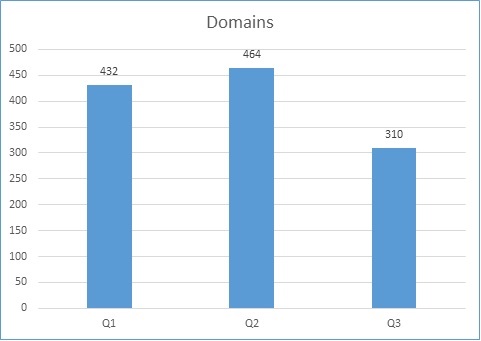 Figure 3. Malware domains from Q1 to Q3 2018
Figure 3. Malware domains from Q1 to Q3 2018
In monitoring the domain hosting data, a pattern has emerged. Since the beginning of the year, the same top 5 countries are present: United States, Russia, China, Hong Kong, and the Netherlands. These results may not seem surprising, especially the top 3, but it’s always interesting to see the movement of numbers throughout the quarters which are detailed in Figure 4 below.
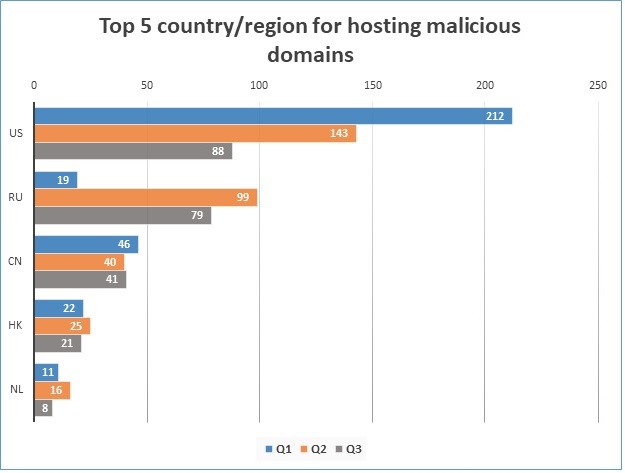 Figure 4. Malware domains in Q1 2018
Figure 4. Malware domains in Q1 2018
Exploit Kits
Unlike Q2, we did not observe a major difference between the distribution of two major exploit kit families we are tracking, Grandsoft/Sundown/Rig and Kaixin. In Q2, we noticed a clear geographic distribution between the two families. Kaixin was heavily seen in China and Grandsoft/Sundown/Rig in the US. However, from the data in Q3, the boundary between the two exploit kits is ambiguous. In Q3 there is a shift, more Kaixin exploit kits are hosted in US.
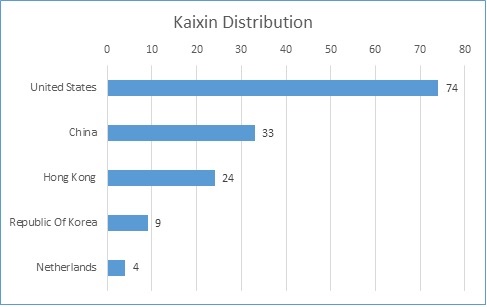 Figure 5. Kaixin EK distribution.
Figure 5. Kaixin EK distribution.
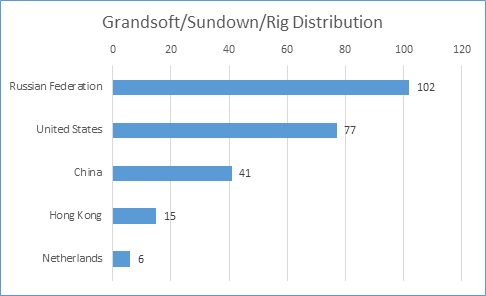 Figure 6. Grandsoft/Sundown/Rig EK distribution.
Figure 6. Grandsoft/Sundown/Rig EK distribution.
In addition to the two major exploit kit families, two samples of Terror EK and nine samples of Fallout EK were found in Q3.
Vulnerabilities
The recorded CVEs have not changed much since the beginning of 2018. The top 3 vulnerabilities in Q3 are the same as in Q2. Table 1 shows the rundown of the most common CVEs since Q1.
| Q1 Top CVE | Q1 top Trigger | Q2 Top CVE | Q2 top Trigger | Q3 Top CVE | Q3 top Trigger | |
| 1 | CVE-2014-6332 | 774 | CVE-2016-0189 | 472 | CVE-2016-0189 | 225 |
| 2 | CVE-2016-0189 | 219 | CVE-2018-8174 | 291 | CVE-2018-8174 | 139 |
| 3 | CVE-2015-5122 | 85 | CVE-2014-6332 | 67 | CVE-2014-6332 | 50 |
Table 1. Most triggered CVE Q1 to Q3 2018
Most of the currently exploited CVEs are not new. In fact, although they didn’t make the top 3 list, the exploitation of a decade old CVEs are still showing up in our data. Below is an overview of the CVEs that have been triggered in our ELINK system.
CVE-2008-1309: The RealAudioObjects.RealAudio ActiveX control in rmoc3260.dll in RealNetworks RealPlayer Enterprise, RealPlayer 10, RealPlayer 10.5 before build 6.0.12.1675, and RealPlayer 11 before 11.0.3 build 6.0.14.806 does not properly manage memory for the (1) Console or (2) Controls property, which allows remote attackers to execute arbitrary code or cause a denial of service (browser crash) via a series of assignments of long string values, which triggers an overwrite of freed heap memory.
CVE-2008-1472: Stack-based buffer overflow in the ListCtrl ActiveX Control (ListCtrl.ocx), as used in multiple CA products including BrightStor ARCserve Backup R11.5, Desktop Management Suite r11.1 through r11.2, and Unicenter products r11.1 through r11.2, allows remote attackers to execute arbitrary code or cause a denial of service (crash) via a long argument to the AddColumn method.
CVE-2008-4844: Use-after-free vulnerability in the CRecordInstance::TransferToDestination function in mshtml.dll in Microsoft Internet Explorer 5.01, 6, 6 SP1, and 7 allows remote attackers to execute arbitrary code via DSO bindings involving (1) an XML Island, (2) XML DSOs, or (3) Tabular Data Control (TDC) in a crafted HTML or XML document, as demonstrated by nested SPAN or MARQUEE elements, and exploited in the wild in December 2008.
CVE-2009-0075:Microsoft Internet Explorer 7 does not properly handle errors during attempted access to deleted objects, which allows remote attackers to execute arbitrary code via a crafted HTML document, related to CFunctionPointer and the appending of document objects, aka "Uninitialized Memory Corruption Vulnerability."
CVE-2010-0806:Use-after-free vulnerability in the Peer Objects component (aka iepeers.dll) in Microsoft Internet Explorer 6, 6 SP1, and 7 allows remote attackers to execute arbitrary code via vectors involving access to an invalid pointer after the deletion of an object, as exploited in the wild in March 2010, aka "Uninitialized Memory Corruption Vulnerability."
CVE-2010-3973: The WMITools ActiveX control in WBEMSingleView.ocx 1.50.1131.0 in Microsoft WMI Administrative Tools 1.1 and earlier in Microsoft Windows XP SP2 and SP3 allows remote attackers to execute arbitrary code via a crafted argument to the AddContextRef method, possibly an untrusted pointer dereference, aka "Microsoft WMITools ActiveX Control Vulnerability."
CVE-2012-1889:Microsoft XML Core Services 3.0, 4.0, 5.0, and 6.0 accesses uninitialized memory locations, which allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site.
CVE-2014-6332:OleAut32.dll in OLE in Microsoft Windows Server 2003 SP2, Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8, Windows 8.1, Windows Server 2012 Gold and R2, and Windows RT Gold and 8.1 allows remote attackers to execute arbitrary code via a crafted web site, as demonstrated by an array-redimensioning attempt that triggers improper handling of a size value in the SafeArrayDimen function, aka "Windows OLE Automation Array Remote Code Execution Vulnerability."
CVE-2016-0189:The Microsoft (1) JScript 5.8 and (2) VBScript 5.7 and 5.8 engines, as used in Internet Explorer 9 through 11 and other products, allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site, aka "Scripting Engine Memory Corruption Vulnerability," a different vulnerability than CVE-2016-0187.
CVE-2018-8174:A remote code execution vulnerability exists in the way that the VBScript engine handles objects in memory, aka "Windows VBScript Engine Remote Code Execution Vulnerability." This affects Windows 7, Windows Server 2012 R2, Windows RT 8.1, Windows Server 2008, Windows Server 2012, Windows 8.1, Windows Server 2016, Windows Server 2008 R2, Windows 10, Windows 10 Servers.
CVE-2015-5119 Exploit Still Used in the Wild
The vulnerability CVE-2015-5119 was found in the Hacking Team leak in 2015. This critical vulnerability in Adobe Flash Player can allow remote attackers to execute arbitrary code. In Q3, we detected a malicious Flash file utilizing vulnerability CVE-2015-5119 in the wild.
Exploit Framework
On August 27th, 2018, our ELINK system found a URL in a porn site embedded with a malicious Flash file that takes advantage of CVE-2015-5119. It’s interesting to point out how the attacker weaponized this exploit in the wild.
The exploit code takes advantage of the vulnerability by assigning a large number to one of the vector objects. Through the corrupted vector object, the attacker has Read&Write privileges to modify the entire process memory. This is typically the first step for attackers when hijacking the control flow. Next, by calling the native Flash function, the exploit code assigns the memory permission to Read Write Execute (RWE) as shown in Figure 9. Finally, the exploit code changes the content of the stack and eventually hijacks the control flow.
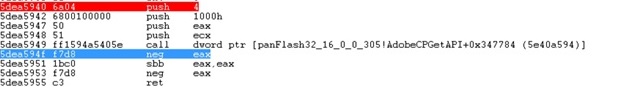 Figure 7. Exploit code changed shellcode memory permission
Figure 7. Exploit code changed shellcode memory permission
After the Adobe Flash Player is fully controlled, the exploit code executes the real shellcode for the last stage of the exploit.
The shellcode is highly obfuscated for thwarting the process of reverse engineering. After the shellcode loads specified libraries, it creates a thread to connect the C2 with the specified user agent which then verifies the response from the C2. The shellcode extracts the XOR key from the C2 response and decrypts all the C2 content as a new shellcode. At this point, it would be possible for remote attackers to fully control the victim’s machine by executing the shellcode from the C2.
Conclusion
Looking at this quarter’s trends, we see a surprising drop in malicious URLs globally. Meanwhile, the United States remained the top hosting country for malicious sites and exploit kits.
While our ELINK system indicates 10-year-old vulnerabilities still being exploited, most of the vulnerabilities showing up were discovered within the last 5 years.
In Q3, the United States based domains hosting the Kaixin exploit kit almost doubled from Q2. This significant change was surprising considering the total number of domains drastically dropped. It also reveals the geographic division for the various exploit kits are ambiguous.
Next quarter, we’ll return to review this quarter’s statics and trends against the latest data from ELINK to help better understand the threat trends in the wild.












 Get updates from Unit 42
Get updates from Unit 42